获取app的URLScheme
在已越狱的iPhone上,使用Filza进入app列表目录:
/private/var/containers/Bundle/Application/
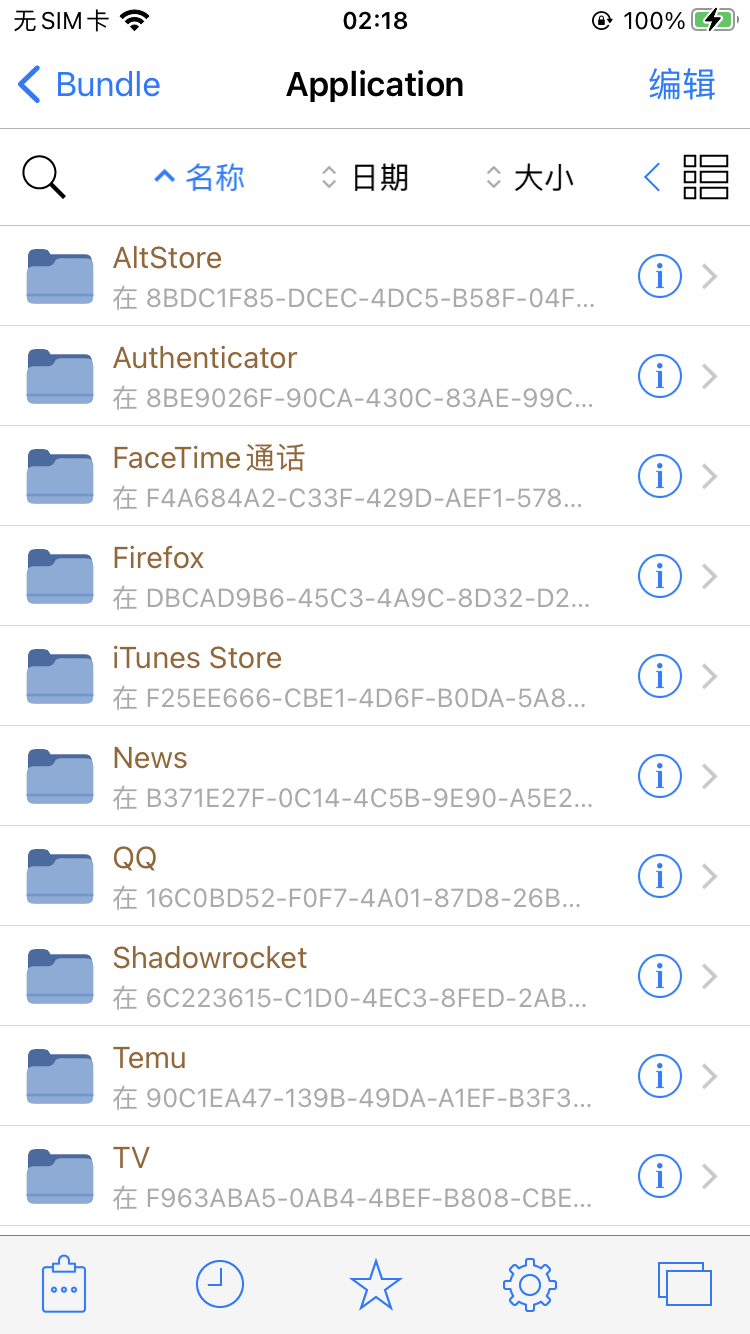
比如我要分析Microsoft Authenticator,明显对应的是这里面的“Authenticator”,那就在Filza中点击进入“Authenticator”,发现路径是/var/containers/Bundle/Application/8BE9026F-90CA-430C-83AE-99C8DD861D4D/
通过OpenSSH把整个路径文件夹下的内容拉取到PC上,之后打开其中的 xxx.app/Info.plist 这个文件,这里就是:
/private/var/containers/Bundle/Application/8BE9026F-90CA-430C-83AE-99C8DD861D4D/Microsoft Authenticator.app/Info.plist
找到URLTypes,其下URLSchemes中的数组对应的值就是这个 app 的 URL Scheme 了
<key>CFBundleURLTypes</key>
<array>
<dict>
<key>CFBundleURLSchemes</key>
<array>
<string>brooklyn-extension</string>
<string>msauth</string>
<string>ms-log-azureauthenticator</string>
<string>microsoft-authenticator</string>
<string>otpauth</string>
<string>msauthv2</string>
<string>msauthv3</string>
<string>openid</string>
<string>openid-vc</string>
<string>vcclient</string>
</array>
<key>CFBundleTypeRole</key>
<string>Editor</string>
<key>CFBundleURLName</key>
<string>com.microsoft.azureauthenticator</string>
</dict>
</array>
例如,可以通过safari访问msauth://,就能跳转到Microsoft Authenticator
常见URLScheme合集
https://gist.github.com/zhuziyi1989/3f96a73c45a87778b560e44cb551ebd2
https://gist.github.com/JamesHopbourn/046bc341e7debfd0c86e3b388d983c53
参考:https://blog.csdn.net/ShiDuQi/article/details/9791345