ifconfig ( network interfaces configuring )
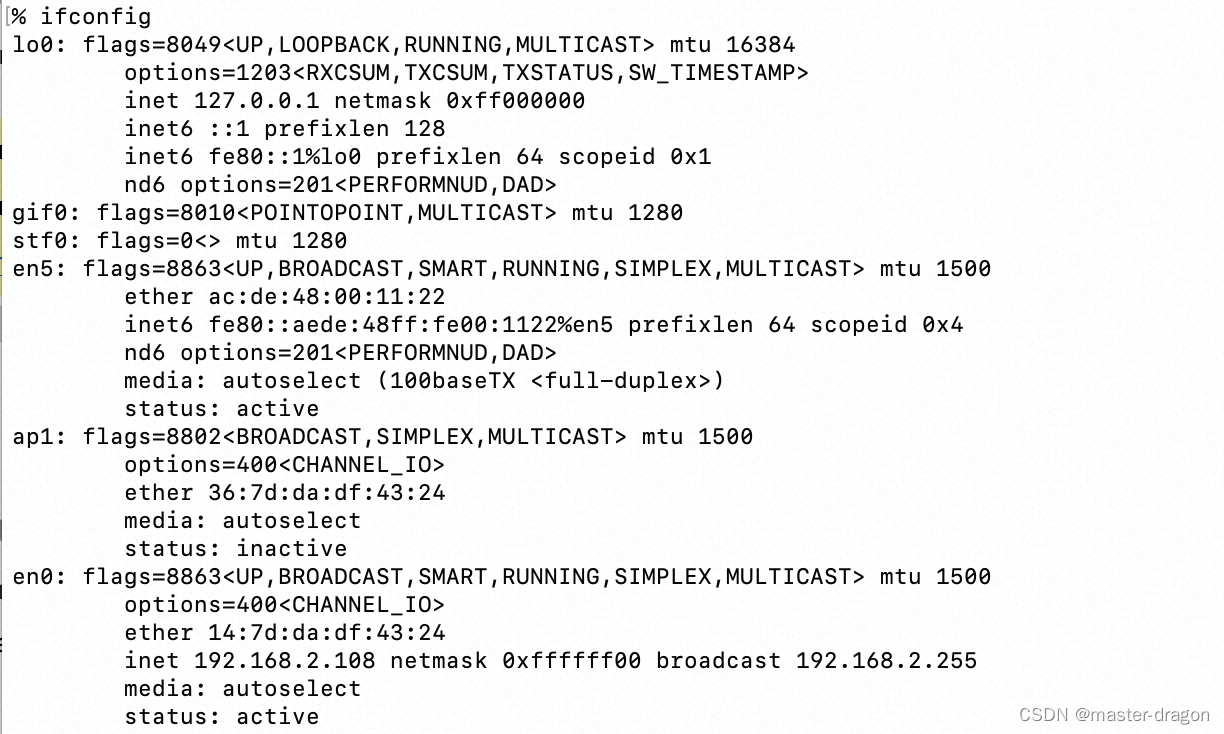
- eth0表示网卡
- UP代表网卡开启状态
- RUNNING代表网卡的网线被接上
- mtu1500: MTU(最大传输单元)是指在网络中传输数据时,单个数据包的最大长度。MTU的值越大,单个数据包的最大长度就越大,网络传输效率就越高。
- MULTICAST表示支持组播。
- ether 14:7d:da:df:43:24,mac物理地址
- inet(IP地址):192.168.2.108。netmask(掩码地址):0xffffff00。broadcast(广播地址):192.168.2.255。
- media: autoselect—— 网络媒介类型
- status: active—— 激活状态
tcpdump 命令
NAME
tcpdump - dump traffic on a network
SYNOPSIS
tcpdump [ -AbdDefhHIJKlLnNOpqStuUvxX# ] [ -B buffer_size ]
[ -c count ]
[ -C file_size ] [ -G rotate_seconds ] [ -F file ]
[ -i interface ] [ -j tstamp_type ] [ -k (metadata_arg) ]
[ -m module ] [ -M secret ]
[ --number ] [ -Q in|out|inout ]
[ -r file ] [ -V file ] [ -s snaplen ] [ -T type ] [ -w file ]
[ -W filecount ]
[ -E spi@ipaddr algo:secret,... ]
[ -y datalinktype ] [ -z postrotate-command ] [ -Z user ]
[ -Q packet-metadata-filter ] [ -Q in|out|inout ]
[ --time-stamp-precision=tstamp_precision ]
[ --immediate-mode ] [ --version ]
[ expression ]
DESCRIPTION
Tcpdump prints out a description of the contents of packets on a network interface that match the boolean
expression; the description is preceded by a time stamp, printed, by default, as hours, minutes, seconds, and
fractions of a second since midnight. It can also be run with the -w flag, which causes it to save the packet
data to a file for later analysis, and/or with the -r flag, which causes it to read from a saved packet file
rather than to read packets from a network interface. It can also be run with the -V flag, which causes it to
read a list of saved packet files. In all cases, only packets that match expression will be processed by tcp-
dump.
Tcpdump will, if not run with the -c flag, continue capturing packets until it is interrupted by a SIGINT sig-
nal (generated, for example, by typing your interrupt character, typically control-C) or a SIGTERM signal
(typically generated with the kill(1) command); if run with the -c flag, it will capture packets until it is
interrupted by a SIGINT or SIGTERM signal or the specified number of packets have been processed.
常用:
-nn,直接以 IP 及 Port Number 显示,而非主机名与服务名称。
-i,后面接要「监听」的网络接口,例如 eth0, lo, ppp0 等等的接口。
-w,如果你要将监听所得的数据包数据储存下来,用这个参数就对了。后面接文件名。
-c,监听的数据包数,如果没有这个参数, tcpdump 会持续不断的监听,
直到用户输入 [ctrl]-c 为止。
-A,数据包的内容以 ASCII 显示,通常用来捉取 WWW 的网页数据包资料。
-e,使用资料连接层 (OSI 第二层) 的 MAC 数据包数据来显示。
-q,仅列出较为简短的数据包信息,每一行的内容比较精简。
-X,可以列出十六进制 (hex) 以及 ASCII 的数据包内容,对于监听数据包内容很有用。
-r,从后面接的文件将数据包数据读出来。那个「文件」是已经存在的文件,并且这个「文件」是由 -w 所制作出来的。所欲捕获的数据内容:我们可以专门针对某些通信协议或者是 IP 来源进行数据包捕获。
vv : 输出详细的报文信息
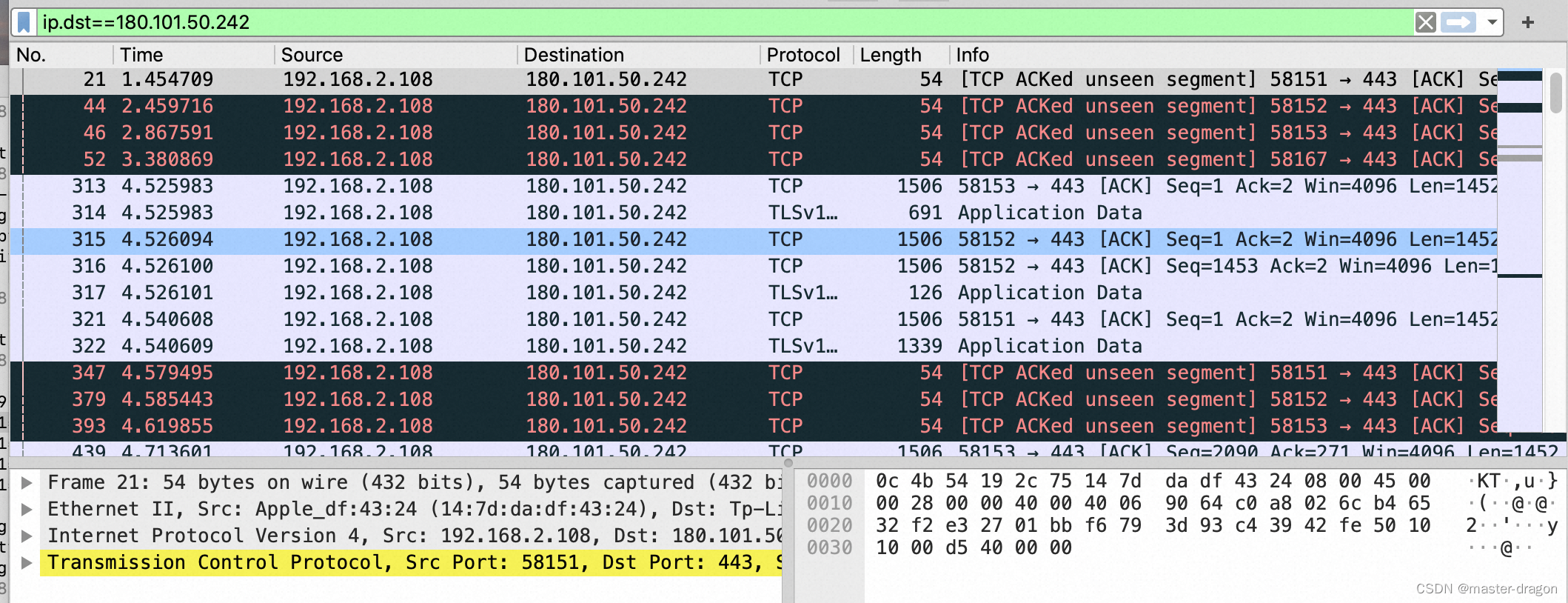
tcpdump&wireshark例子
% nslookup baidu.com
Server: 192.168.1.1
Address: 192.168.1.1#53
Non-authoritative answer:
Name: baidu.com
Address: 39.156.66.10
Name: baidu.com
Address: 110.242.68.66
tcp抓包
% sudo tcpdump -i en0 -nnvv -w tmp.cap
tcpdump: listening on en0, link-type EN10MB (Ethernet), capture size 262144 bytes
^C2415 packets captured
2415 packets received by filter
0 packets dropped by kernel
https访问百度了:

wireshark查看