1.AD域服务器操作
AD域服务器 快速配置开启winrm服务,如果没开启服务,则会报错:
2020-05-05 15:51:27,945 ERROR localAD.py 40 the specified credentials were rejected by the server
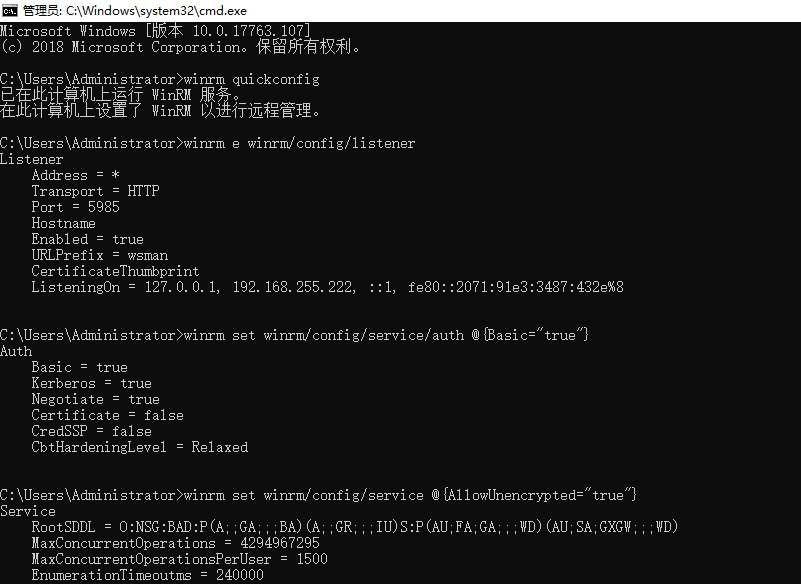
这里是AD域服务器需要配置的命令:
winrm quickconfig
winrm e winrm/config/listener
winrm set winrm/config/service/auth @{Basic="true"}
winrm set winrm/config/service @{AllowUnencrypted="true"}
winrm get winrm/config
部分截图:
2.winrm使用演示
2.1 安装pywinrm 0.4.1
这里有一个坑,pip install的是pywinrm,但是python代码导包的时候写的应该是import winrm,特别注意一下,在这里纠结了好一会。
2.2示例代码
import logging
import winrm
# 日志设置
LOG_FORMAT = "%(asctime)s %(levelname)s %(filename)s %(lineno)d %(message)s"
logging.basicConfig(filename='localAD.log', level=logging.INFO, format=LOG_FORMAT)
# 本地AD域
LDAP_IP_LOCAL = '192.168.255.222' # LDAP本地服务器IP
LDAP_ADMIN_USER_LOCAL = 'CN=Administrator,CN=Users,DC=bilibili,DC=com' # LDAP本地服务器管理员账户
LDAP_ADMIN_PWD_LOCAL = 'QQqq#123' # LDAP本地服务器管理员密码
# powershell命令,用于打开/关闭OU是否被删除的权限
cmd_list_enable_del = ["Import-Module ActiveDirectory",
"Get-ADOrganizationalUnit -filter * -Properties ProtectedFromAccidentalDeletion | where {"
"$_.ProtectedFromAccidentalDeletion -eq $true} | ft",
"Get-ADOrganizationalUnit -filter * -Properties ProtectedFromAccidentalDeletion | where {"
"$_.ProtectedFromAccidentalDeletion -eq $true} |Set-ADOrganizationalUnit "
"-ProtectedFromAccidentalDeletion $false"]
cmd_list_disable_del = ["Import-Module ActiveDirectory",
"Get-ADOrganizationalUnit -filter * -Properties ProtectedFromAccidentalDeletion | where {"
"$_.ProtectedFromAccidentalDeletion -eq $false} | ft",
"Get-ADOrganizationalUnit -filter * -Properties ProtectedFromAccidentalDeletion | where {"
"$_.ProtectedFromAccidentalDeletion -eq $false} |Set-ADOrganizationalUnit "
"-ProtectedFromAccidentalDeletion $true"]
def enable_del_ou_right(ip, user, pwd, cmd_l):
try:
win = winrm.Session('http://' + ip + ':5985/wsman', auth=(user, pwd))
for cmd in cmd_l:
ret = win.run_ps(cmd)
if ret.status_code == 0: # 调用成功
logging.info('执行命令【' + cmd + '】成功')
else:
return False
return True
except Exception as e:
logging.error(e)
if __name__ == '__main__':
# 调用ps脚本,开启OU删除权限
# modify_right_res = enable_del_ou_right(LDAP_IP_LOCAL, 'administrator', LDAP_ADMIN_PWD_LOCAL, cmd_list_enable_del)
# 关闭OU删除权限
enable_del_ou_right(LDAP_IP_LOCAL, 'administrator', LDAP_ADMIN_PWD_LOCAL, cmd_list_disable_del)
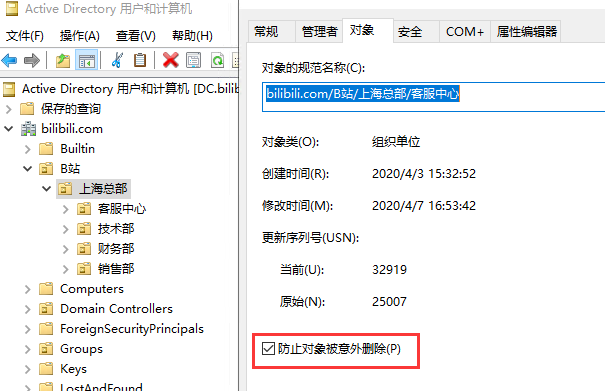
说明:关闭了OU的删除权限后,AD域中OU右键,对象中,可以看到所有OU都设置好了防止对象被意外删除:
下面是日志中记载的:
2020-05-05 15:54:41,783 INFO localAD.py 35 执行命令【Import-Module ActiveDirectory】成功
2020-05-05 15:54:44,319 INFO localAD.py 35 执行命令【Get-ADOrganizationalUnit -filter * -Properties ProtectedFromAccidentalDeletion | where {$_.ProtectedFromAccidentalDeletion -eq $false} | ft】成功
2020-05-05 15:54:45,461 INFO localAD.py 35 执行命令【Get-ADOrganizationalUnit -filter * -Properties ProtectedFromAccidentalDeletion | where {$_.ProtectedFromAccidentalDeletion -eq $false} |Set-ADOrganizationalUnit -ProtectedFromAccidentalDeletion $true】成功