节点1
ip netns add host2
ip link add veth2 type veth peer name eth0 netns host2
ip netns exec host2 ip link set lo up
ip netns exec host2 ip link set eth0 up
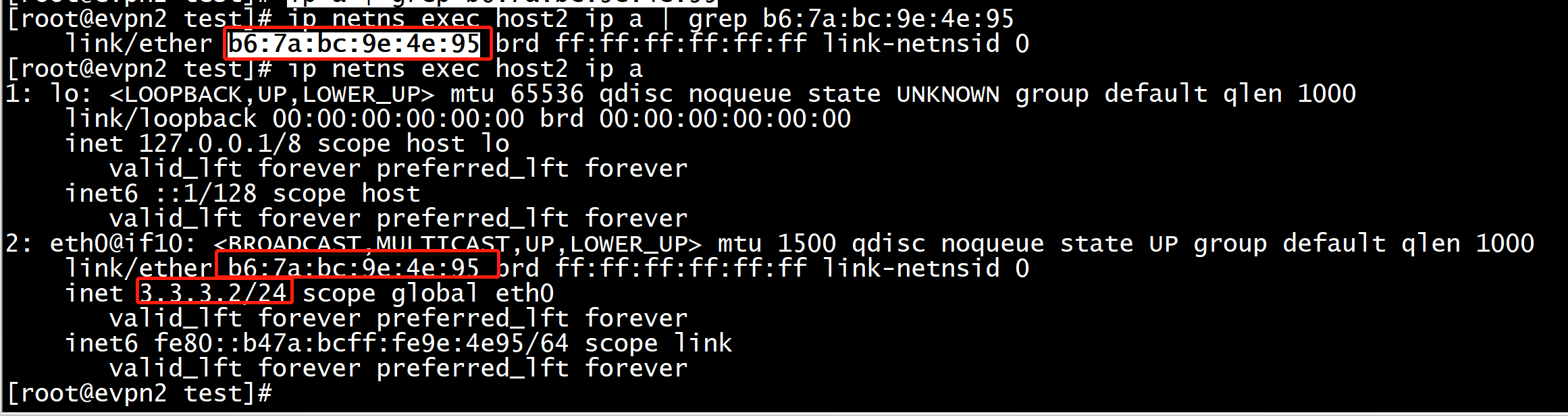
ip netns exec host2 ip addr add 3.3.3.2/24 dev eth0
ip netns exec host2 ip route add default via 3.3.3.254 dev eth0
ip link add br20 type bridge
ip link add vxlan20 type vxlan id 20 local 10.10.18.209 dstport 4789 nolearning ip link set br20 up ip link set veth2 up ip link set vxlan20 up ip link set veth2 master br20 ip link set vxlan20 master br20 ip link set dev br20 address 00:00:01:02:03:00 ip addr add 3.3.3.254/24 dev br20
vxlan20 没有加入 vrf
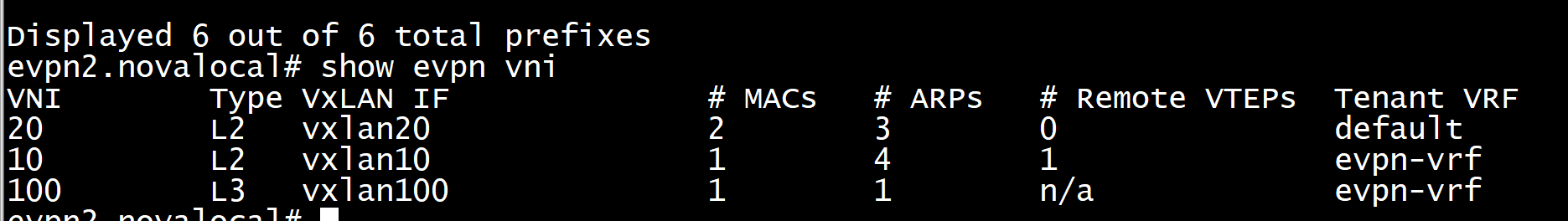
evpn2.novalocal# show ip bgp l2vpn evpn
BGP table version is 3, local router ID is 10.10.18.209
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP]
EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP] EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP] EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP] Network Next Hop Metric LocPrf Weight Path Route Distinguisher: 9.9.9.254:3 *> [5]:[0]:[24]:[9.9.9.0] 10.10.18.212 0 0 9999 i RT:9999:100 ET:8 Rmac:00:00:01:02:03:05 Route Distinguisher: 10.10.18.209:2 *> [3]:[0]:[32]:[10.10.18.209] 10.10.18.209 32768 i ET:8 RT:8888:10-----------------------------10 表示vxlan 10 Route Distinguisher: 10.10.18.209:4 *> [2]:[0]:[48]:[b6:7a:bc:9e:4e:95] 10.10.18.209 32768 i ET:8 RT:8888:20 *> [2]:[0]:[48]:[b6:7a:bc:9e:4e:95]:[128]:[fe80::b47a:bcff:fe9e:4e95] 10.10.18.209 32768 i ET:8 RT:8888:20 *> [3]:[0]:[32]:[10.10.18.209] 10.10.18.209 32768 i ET:8 RT:8888:20 -----------------------------20 是vxlan 20 Route Distinguisher: 10.10.18.212:2 *> [3]:[0]:[32]:[10.10.18.212] 10.10.18.212 0 9999 i RT:9999:10 ET:8 Displayed 6 out of 6 total prefixes
b6:7a:bc:9e:4e:95
evpn2.novalocal# show ip route ---没有2.2.2.0/24 因为br10加入了 evpn-vrf
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
K>* 0.0.0.0/0 [0/100] via 10.10.18.254, enp1s0, 1d00h18m
C>* 3.3.3.0/24 is directly connected, br20, 00:17:15
C>* 10.10.18.0/24 is directly connected, enp1s0, 1d00h18m
K>* 169.254.169.254/32 [0/100] via 10.10.18.254, enp1s0, 1d00h18m
evpn2.novalocal# show ip route vrf evpn-vrf
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
VRF evpn-vrf:
C>* 2.2.2.0/24 is directly connected, br10, 23:53:54
B>* 9.9.9.0/24 [20/0] via 10.10.18.212, br100 onlink, 03:10:16
节点1 执行ping--------无法ping 通2.2.2.3
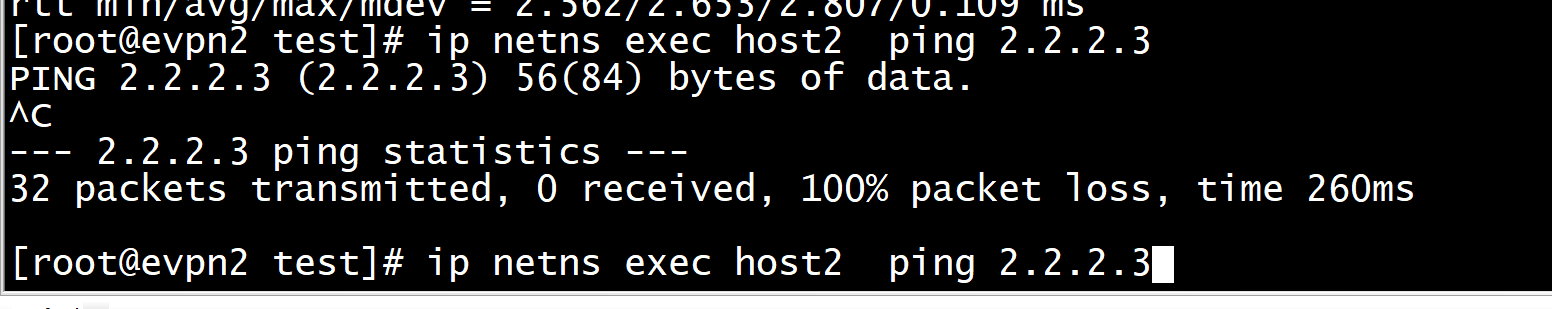
加入vrf
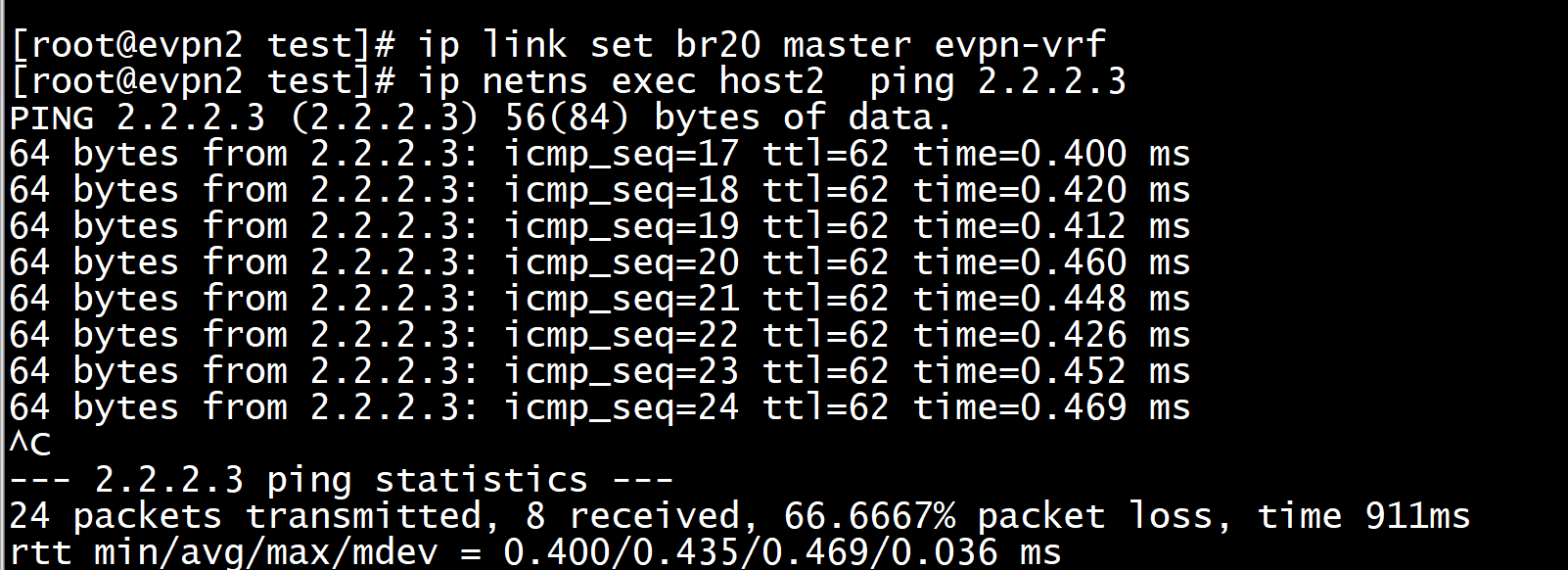
在节点2上tcpdump
[root@evpn2 test]# tcpdump -i enp1s0 -eennvv udp
tcpdump: listening on enp1s0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:38:19.275210 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 63474, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.209.39450 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x9c74!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34644, offset 0, flags [DF], proto ICMP (1), length 84)
3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 11, length 64
14:38:20.315205 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 63491, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.209.39450 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x9c74!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34681, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 12, length 64 14:38:21.355196 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 63587, offset 0, flags [none], proto UDP (17), length 134) 10.10.18.209.39450 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x9c74!] VXLAN, flags [I] (0x08), vni 100 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34700, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 13, length 64 14:38:22.395147 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 63612, offset 0, flags [none], proto UDP (17), length 134) 10.10.18.209.39450 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x9c74!] VXLAN, flags [I] (0x08), vni 100 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34804, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 14, length 64 14:38:23.435197 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 63649, offset 0, flags [none], proto UDP (17), length 134) 10.10.18.209.39450 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x9c74!] VXLAN, flags [I] (0x08), vni 100 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34861, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 15, length 64 ^C 5 packets captured 5 packets received by filter 0 packets dropped by kernel [root@evpn2 test]# tcpdump -i vxlan100 -eennvv udp tcpdump: listening on vxlan100, link-type EN10MB (Ethernet), capture size 262144 bytes ^C^C 0 packets captured 0 packets received by filter 0 packets dropped by kernel [root@evpn2 test]# tcpdump -i vxlan10 -eennvv udp tcpdump: listening on vxlan10, link-type EN10MB (Ethernet), capture size 262144 bytes ^C 0 packets captured 0 packets received by filter 0 packets dropped by kernel [root@evpn2 test]# ip link show type vxlan 7: vxlan10: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br30 state UNKNOWN mode DEFAULT group default qlen 1000 link/ether 02:20:03:9f:74:90 brd ff:ff:ff:ff:ff:ff 9: vxlan100: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br100 state UNKNOWN mode DEFAULT group default qlen 1000 link/ether e6:83:12:4c:78:fc brd ff:ff:ff:ff:ff:ff [root@evpn2 test]# tcpdump -i vxlan100 -eennvv tcpdump: listening on vxlan100, link-type EN10MB (Ethernet), capture size 262144 bytes 14:39:38.315231 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 38581, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 87, length 64 14:39:38.315292 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 24671, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.3 > 3.3.3.2: ICMP echo reply, id 16186, seq 87, length 64 14:39:39.355309 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 38603, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 88, length 64 14:39:39.355362 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 24696, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.3 > 3.3.3.2: ICMP echo reply, id 16186, seq 88, length 64 14:39:40.395201 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 38663, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 89, length 64 14:39:40.395263 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 24787, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.3 > 3.3.3.2: ICMP echo reply, id 16186, seq 89, length 64 14:39:41.435273 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 38699, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 90, length 64 14:39:41.435339 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 24823, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.3 > 3.3.3.2: ICMP echo reply, id 16186, seq 90, length 64 14:39:42.475238 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 38778, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 91, length 64 14:39:42.475302 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 24854, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.3 > 3.3.3.2: ICMP echo reply, id 16186, seq 91, length 64 14:39:43.515282 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 38798, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 92, length 64 14:39:43.515339 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 24943, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.3 > 3.3.3.2: ICMP echo reply, id 16186, seq 92, length 64 14:39:44.555265 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 38859, offset 0, flags [DF], proto ICMP (1), length 84) 3.3.3.2 > 2.2.2.3: ICMP echo request, id 16186, seq 93, length 64 14:39:44.555329 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 25042, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.3 > 3.3.3.2: ICMP echo reply, id 16186, seq 93, length 64 ^C 14 packets captured 14 packets received by filter 0 packets dropped by kernel