节点1 mp_bgp配置
evpn2.novalocal# show running-config
Building configuration...
Current configuration:
!
frr version 7.3-MyOwnFRRVersion
frr defaults traditional
hostname evpn2.novalocal
!
vrf evpn-vrf
vni 100 exit-vrf ! router bgp 8888 bgp router-id 10.10.18.209 bgp bestpath as-path multipath-relax neighbor fabric peer-group neighbor fabric remote-as external neighbor 10.10.18.212 peer-group fabric neighbor 10.10.18.212 update-source 10.10.18.209 ! address-family l2vpn evpn neighbor fabric activate advertise-all-vni exit-address-family ! router bgp 8888 vrf evpn-vrf ! address-family l2vpn evpn advertise ipv4 unicast exit-address-family ! line vty ! end
节点1 设备
#!/bin/bash
#enable forward
#sysctl -w net.ipv4.ip_forward=1
#sysctl -p
#add host1
ip netns add host1
ip link add veth1 type veth peer name eth0 netns host1
ip netns exec host1 ip link set lo up
ip netns exec host1 ip link set eth0 up
ip netns exec host1 ip addr add 2.2.2.2/24 dev eth0 ip netns exec host1 ip route add default via 2.2.2.254 dev eth0 ip link add br10 type bridge ip link add vxlan10 type vxlan id 10 local 10.10.18.209 dstport 4789 nolearning ip link set br10 up ip link set veth1 up ip link set vxlan10 up ip link set veth1 master br10 ip link set vxlan10 master br10 ip link set dev br10 address 00:00:01:02:03:10 ip addr add 2.2.2.254/24 dev br10 #add l3 vni ip link add br100 type bridge ip link add vxlan100 type vxlan id 100 local 10.10.18.209 dstport 4789 nolearning ip link set br100 up ip link set vxlan100 up ip link set vxlan100 master br100 ip link set dev br100 address 00:00:01:02:03:04 # add vrf ip link add evpn-vrf type vrf table 100 ip link set evpn-vrf up ip link set br100 master evpn-vrf ip link set br10 master evpn-vrf
节点2 mp_bgp配置
Building configuration...
Current configuration:
!
frr version 7.3-MyOwnFRRVersion
frr defaults traditional
hostname evpn2.novalocal
!
vrf evpn-vrf
vni 100 exit-vrf ! router bgp 9999 bgp router-id 10.10.18.212 bgp bestpath as-path multipath-relax neighbor fabric peer-group neighbor fabric remote-as external neighbor 10.10.18.209 peer-group fabric neighbor 10.10.18.209 update-source 10.10.18.212 ! address-family l2vpn evpn neighbor fabric activate advertise-all-vni exit-address-family ! router bgp 9999 vrf evpn-vrf
!
address-family l2vpn evpn
advertise ipv4 unicast
exit-address-family
!
line vty
!
end
节点2 设备
#!/bin/bash
#enable forward
#add host2
ip netns add host2
ip link add veth2 type veth peer name eth0 netns host2
ip netns exec host2 ip link set lo up
ip netns exec host2 ip link set eth0 up
ip netns exec host2 ip addr add 9.9.9.1/24 dev eth0
ip netns exec host2 ip route add default via 9.9.9.254 dev eth0
#add br20
ip link add br20 type bridge
ip link set br20 up ip link set veth2 up ip link set veth2 master br20 ip addr add 9.9.9.254/24 dev br20 #add host3 ip netns add host3 ip link add veth3 type veth peer name eth0 netns host3 ip netns exec host3 ip link set lo up ip netns exec host3 ip link set eth0 up ip netns exec host3 ip addr add 2.2.2.3/24 dev eth0 ip netns exec host3 ip route add default via 2.2.2.254 dev eth0 ip link add br30 type bridge ip link add vxlan10 type vxlan id 10 local 10.10.18.212 dstport 4789 nolearning ip link set vxlan10 up ip link set vxlan10 master br30 ip link set br30 up ip link set veth3 up ip link set veth3 master br30 ip addr add 2.2.2.254/24 dev br30 ip link set dev br30 address 00:00:01:02:03:10 #add l3vni ip link add br100 type bridge ip link add vxlan100 type vxlan id 100 local 10.10.18.212 dstport 4789 nolearning ip link set br100 up ip link set vxlan100 up ip link set vxlan100 master br100 ip link set dev br100 address 00:00:01:02:03:05 #add vrf ip link add evpn-vrf type vrf table 100 ip link set evpn-vrf up ip link set br100 master evpn-vrf ip link set br20 master evpn-vrf //加入vrf ip link set br30 master evpn-vrf

evpn2.novalocal# show ip bgp neighbors
BGP neighbor is 10.10.18.212, remote AS 9999, local AS 8888, external link
Hostname: evpn2.novalocal
Member of peer-group fabric for session parameters
BGP version 4, remote router ID 10.10.18.212, local router ID 10.10.18.209
BGP state = Established, up for 00:00:28
Last read 00:00:27, Last write 00:00:27 Hold time is 180, keepalive interval is 60 seconds Neighbor capabilities: 4 Byte AS: advertised and received AddPath: IPv4 Unicast: RX advertised IPv4 Unicast and received L2VPN EVPN: RX advertised L2VPN EVPN and received Route refresh: advertised and received(old & new) Address Family IPv4 Unicast: advertised and received Address Family L2VPN EVPN: advertised and received Hostname Capability: advertised (name: evpn2.novalocal,domain name: n/a) received (name: evpn2.novalocal,domain name: n/a) Graceful Restart Capabilty: advertised and received Remote Restart timer is 120 seconds Address families by peer: none Graceful restart information: End-of-RIB send: IPv4 Unicast, L2VPN EVPN End-of-RIB received: IPv4 Unicast, L2VPN EVPN Message statistics: Inq depth is 0 Outq depth is 0 Sent Rcvd Opens: 1 1 Notifications: 0 0 Updates: 5 5 Keepalives: 1 1 Route Refresh: 0 0 Capability: 0 0 Total: 7 7 Minimum time between advertisement runs is 0 seconds Update source is 10.10.18.209 For address family: IPv4 Unicast fabric peer-group member Update group 1, subgroup 1 Packet Queue length 0 Community attribute sent to this neighbor(all) 0 accepted prefixes For address family: L2VPN EVPN fabric peer-group member Update group 2, subgroup 2 Packet Queue length 0 NEXT_HOP is propagated unchanged to this neighbor Community attribute sent to this neighbor(all) advertise-all-vni 3 accepted prefixes Connections established 1; dropped 0 Last reset 00:39:31, Waiting for NHT Local host: 10.10.18.209, Local port: 33021 Foreign host: 10.10.18.212, Foreign port: 179 Nexthop: 10.10.18.209 Nexthop global: fe80::f816:3eff:fe11:8c48 Nexthop local: fe80::f816:3eff:fe11:8c48 BGP connection: shared network BGP Connect Retry Timer in Seconds: 120 Read thread: on Write thread: on FD used: 24 evpn2.novalocal# show bgp evpn route BGP table version is 7, local router ID is 10.10.18.209 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal Origin codes: i - IGP, e - EGP, ? - incomplete EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP] EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP] EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP] EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP] Network Next Hop Metric LocPrf Weight Path Extended Community Route Distinguisher: 10.10.18.209:2 *> [3]:[0]:[32]:[10.10.18.209] 10.10.18.209 32768 i ET:8 RT:8888:10 Route Distinguisher: 10.10.18.212:2 *> [2]:[0]:[48]:[3a:d4:04:8c:3b:ff] 10.10.18.212 0 9999 i RT:9999:10 RT:9999:100 ET:8 Rmac:00:00:01:02:03:05 *> [2]:[0]:[48]:[3a:d4:04:8c:3b:ff]:[32]:[2.2.2.3] 10.10.18.212 0 9999 i RT:9999:10 RT:9999:100 ET:8 Rmac:00:00:01:02:03:05 *> [3]:[0]:[32]:[10.10.18.212] 10.10.18.212 0 9999 i RT:9999:10 ET:8 Displayed 4 prefixes (4 paths) evpn2.novalocal# show evpn vni VNI Type VxLAN IF # MACs # ARPs # Remote VTEPs Tenant VRF 10 L2 vxlan10 2 3 1 evpn-vrf 100 L3 vxlan100 1 1 n/a evpn-vrf
evpn2.novalocal# show ip bgp l2vpn evpn
BGP table version is 7, local router ID is 10.10.18.209
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP]
EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP]
EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP]
EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP]
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 10.10.18.209:2
*> [3]:[0]:[32]:[10.10.18.209]
10.10.18.209 32768 i
ET:8 RT:8888:10
Route Distinguisher: 10.10.18.212:2
*> [3]:[0]:[32]:[10.10.18.212]
10.10.18.212 0 9999 i
RT:9999:10 ET:8
Displayed 2 out of 2 total prefixes
evpn2.novalocal# show ip route vrf evpn-vrf
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
VRF evpn-vrf:
C>* 2.2.2.0/24 is directly connected, br10, 01:03:03
B>* 2.2.2.3/32 [20/0] via 10.10.18.212, br100 onlink, 00:05:50
节点2
evpn2.novalocal# show ip route vrf evpn-vrf
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route VRF evpn-vrf: C>* 9.9.9.0/24 is directly connected, br20, 00:49:41 C>* 2.2.2.0/24 is directly connected, br30, 00:49:41 B>* 2.2.2.2/32 [20/0] via 10.10.18.209, br100 onlink, 00:02:06
节点2 ip netns exec host2 ping 2.2.2.2
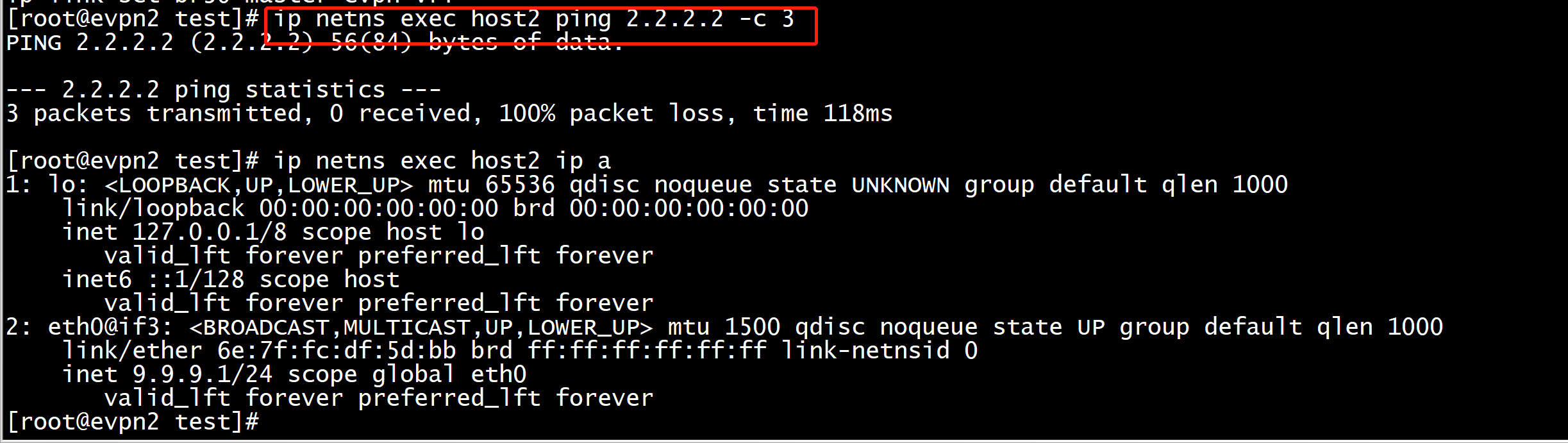
添加 network 9.9.9.0/24 路由通告
evpn2.novalocal# conf t
evpn2.novalocal(config)# address-family ipv4 unicast
% Unknown command: address-family ipv4 unicast
evpn2.novalocal(config)# router bgp 9999 vrf evpn-vrf
evpn2.novalocal(config-router)# address-family ipv4 unicast
evpn2.novalocal(config-router-af)# network 9.9.9.0/24 evpn2.novalocal(config-router-af)# exit-address-family evpn2.novalocal(config-router)# exit evpn2.novalocal(config)# exit evpn2.novalocal# wr mem Note: this version of vtysh never writes vtysh.conf Building Configuration... Configuration saved to /etc/frr/zebra.conf Configuration saved to /etc/frr/ospfd.conf Configuration saved to /etc/frr/bgpd.conf Configuration saved to /etc/frr/pimd.conf Configuration saved to /etc/frr/fabricd.conf Configuration saved to /etc/frr/staticd.conf
再次执行ping
show evpn mac vni

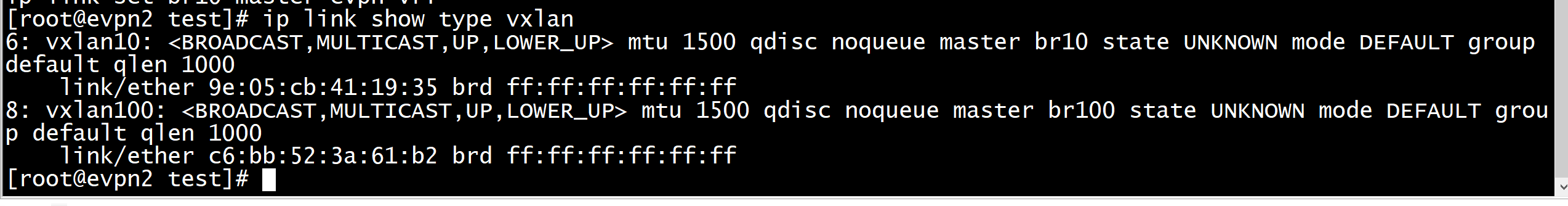
evpn2.novalocal# show evpn vni
VNI Type VxLAN IF # MACs # ARPs # Remote VTEPs Tenant VRF
10 L2 vxlan10 1 4 1 evpn-vrf
100 L3 vxlan100 1 1 n/a evpn-vrf
evpn2.novalocal# show evpn mac vni 100
% VNI 100 does not exist
evpn2.novalocal# show evpn mac vni 10
Number of MACs (local and remote) known for this VNI: 3
MAC Type Intf/Remote VTEP VLAN Seq #'s
3a:d4:04:8c:3b:ff remote 10.10.18.212 0/0
ea:e1:8d:a6:39:96 local veth1 0/0
00:00:01:02:03:10 local br10 1 0/0
show evpn vni 10
evpn2.novalocal# show evpn vni 10
VNI: 10
Type: L2
Tenant VRF: evpn-vrf
VxLAN interface: vxlan10
VxLAN ifIndex: 6
Local VTEP IP: 10.10.18.209 Mcast group: 0.0.0.0 Remote VTEPs for this VNI: 10.10.18.212 flood: HER Number of MACs (local and remote) known for this VNI: 3 Number of ARPs (IPv4 and IPv6, local and remote) known for this VNI: 6 Advertise-gw-macip: No
show evpn vni 100
evpn2.novalocal# show evpn vni 100
VNI: 100
Type: L3
Tenant VRF: evpn-vrf
Local Vtep Ip: 10.10.18.209
Vxlan-Intf: vxlan100
SVI-If: br100 State: Up VNI Filter: none System MAC: 00:00:01:02:03:04 Router MAC: 00:00:01:02:03:04 L2 VNIs: 10
show bgp neighbor 10.10.18.212
evpn2.novalocal# show bgp neighbor 10.10.18.212
BGP neighbor is 10.10.18.212, remote AS 9999, local AS 8888, external link
Hostname: evpn2.novalocal
Member of peer-group fabric for session parameters
BGP version 4, remote router ID 10.10.18.212, local router ID 10.10.18.209
BGP state = Established, up for 19:58:02
Last read 00:00:02, Last write 00:00:02 Hold time is 180, keepalive interval is 60 seconds Neighbor capabilities: 4 Byte AS: advertised and received AddPath: IPv4 Unicast: RX advertised IPv4 Unicast and received L2VPN EVPN: RX advertised L2VPN EVPN and received Route refresh: advertised and received(old & new) Address Family IPv4 Unicast: advertised and received Address Family L2VPN EVPN: advertised and received Hostname Capability: advertised (name: evpn2.novalocal,domain name: n/a) received (name: evpn2.novalocal,domain name: n/a) Graceful Restart Capabilty: advertised and received Remote Restart timer is 120 seconds Address families by peer: none Graceful restart information: End-of-RIB send: IPv4 Unicast, L2VPN EVPN End-of-RIB received: IPv4 Unicast, L2VPN EVPN Message statistics: Inq depth is 0 Outq depth is 0 Sent Rcvd Opens: 1 1 Notifications: 0 0 Updates: 145 145 Keepalives: 1199 1199 Route Refresh: 0 0 Capability: 0 0 Total: 1345 1345 Minimum time between advertisement runs is 0 seconds Update source is 10.10.18.209 For address family: IPv4 Unicast fabric peer-group member Update group 1, subgroup 1 Packet Queue length 0 Community attribute sent to this neighbor(all) 0 accepted prefixes For address family: L2VPN EVPN fabric peer-group member Update group 2, subgroup 2 Packet Queue length 0 NEXT_HOP is propagated unchanged to this neighbor Community attribute sent to this neighbor(all) advertise-all-vni 2 accepted prefixes Connections established 1; dropped 0 Last reset 20:37:05, Waiting for NHT Local host: 10.10.18.209, Local port: 33021 Foreign host: 10.10.18.212, Foreign port: 179 Nexthop: 10.10.18.209 Nexthop global: fe80::f816:3eff:fe11:8c48 Nexthop local: fe80::f816:3eff:fe11:8c48 BGP connection: shared network BGP Connect Retry Timer in Seconds: 120 Read thread: on Write thread: on FD used: 24
show bgp evpn route
evpn2.novalocal# show bgp evpn route
BGP table version is 3, local router ID is 10.10.18.209
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP]
EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP] EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP] EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP] Network Next Hop Metric LocPrf Weight Path Extended Community Route Distinguisher: 9.9.9.254:3 *> [5]:[0]:[24]:[9.9.9.0] 10.10.18.212 0 0 9999 i RT:9999:100 ET:8 Rmac:00:00:01:02:03:05 Route Distinguisher: 10.10.18.209:2 *> [3]:[0]:[32]:[10.10.18.209] 10.10.18.209 32768 i ET:8 RT:8888:10 Route Distinguisher: 10.10.18.212:2 *> [3]:[0]:[32]:[10.10.18.212] 10.10.18.212 0 9999 i RT:9999:10 ET:8 Displayed 3 prefixes (3 paths)
Rmac:00:00:01:02:03:05 是节点2 br100 address 00:00:01:02:03:05
bridge fdb show dev
[root@evpn2 test]# bridge fdb show dev vxlan100 00:00:01:02:03:05 vlan 1 extern_learn master br100 00:00:01:02:03:05 extern_learn master br100 c6:bb:52:3a:61:b2 vlan 1 master br100 permanent c6:bb:52:3a:61:b2 master br100 permanent 00:00:01:02:03:05 dst 10.10.18.212 self extern_learn [root@evpn2 test]# bridge fdb show dev vxlan10 3a:d4:04:8c:3b:ff vlan 1 extern_learn master br10 3a:d4:04:8c:3b:ff extern_learn master br10 9e:05:cb:41:19:35 vlan 1 master br10 permanent 9e:05:cb:41:19:35 master br10 permanent 00:00:00:00:00:00 dst 10.10.18.212 self permanent 3a:d4:04:8c:3b:ff dst 10.10.18.212 self extern_learn
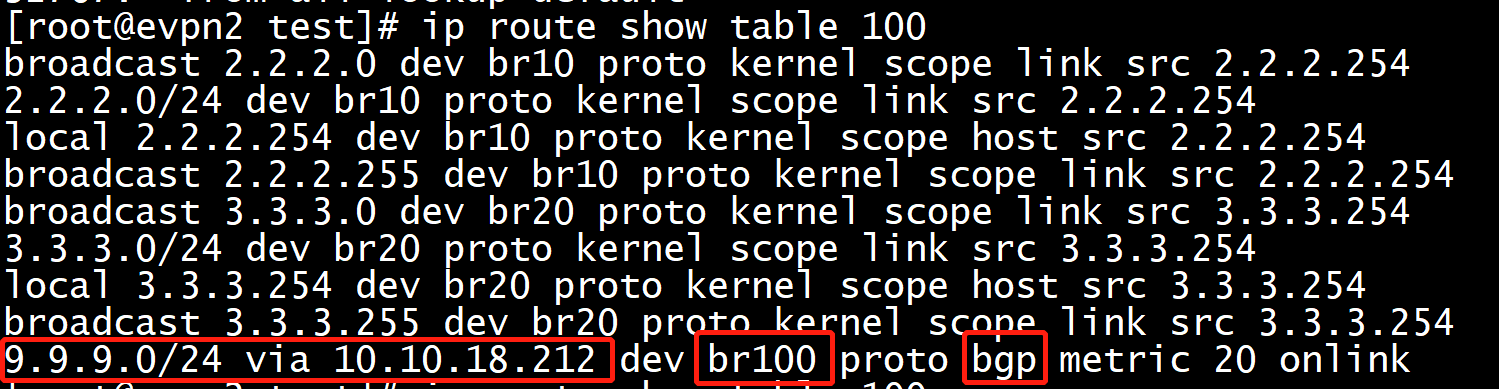
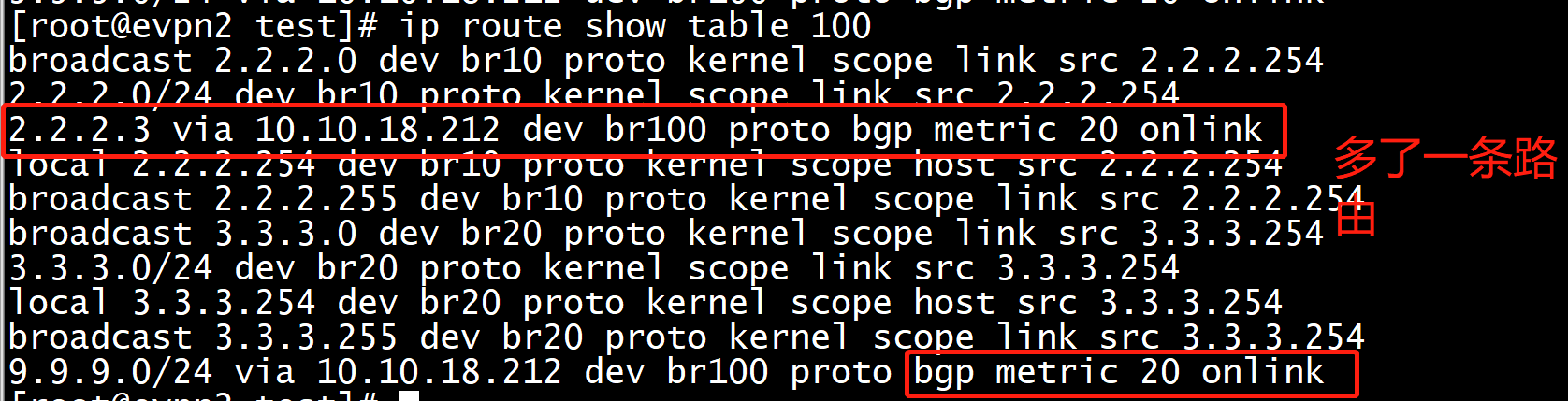
ip route show vrf evpn-vrf
[root@evpn2 test]# ip route show vrf evpn-vrf
2.2.2.0/24 dev br10 proto kernel scope link src 2.2.2.254
9.9.9.0/24 via 10.10.18.212 dev br100 proto bgp metric 20 onlink
节点2
[root@evpn2 test]# ip route show vrf evpn-vrf
2.2.2.0/24 dev br30 proto kernel scope link src 2.2.2.254
9.9.9.0/24 dev br20 proto kernel scope link src 9.9.9.254
[root@evpn2 test]# ip netns exec host2 ip route get 2.2.2.2
2.2.2.2 via 9.9.9.254 dev eth0 src 9.9.9.1 uid 0
cache
show ip route vrf evpn-vrf
evpn2.novalocal# show ip route vrf evpn-vrf
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route VRF evpn-vrf: C>* 2.2.2.0/24 is directly connected, br10, 21:14:15 B>* 9.9.9.0/24 [20/0] via 10.10.18.212, br100 onlink, 00:30:37 节点2 evpn2.novalocal# show ip route vrf evpn-vrf Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP, T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP, F - PBR, f - OpenFabric, > - selected route, * - FIB route, q - queued route, r - rejected route VRF evpn-vrf: C>* 2.2.2.0/24 is directly connected, br30, 20:56:30 C>* 9.9.9.0/24 is directly connected, br20, 19:45:25
show ip bgp l2vpn evpn
evpn2.novalocal# show ip bgp l2vpn evpn
BGP table version is 3, local router ID is 10.10.18.209
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP]
EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP] EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP] EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP] Network Next Hop Metric LocPrf Weight Path Route Distinguisher: 9.9.9.254:3 *> [5]:[0]:[24]:[9.9.9.0] 10.10.18.212 0 0 9999 i RT:9999:100 ET:8 Rmac:00:00:01:02:03:05 Route Distinguisher: 10.10.18.209:2 *> [3]:[0]:[32]:[10.10.18.209] 10.10.18.209 32768 i ET:8 RT:8888:10 Route Distinguisher: 10.10.18.212:2 *> [3]:[0]:[32]:[10.10.18.212] 10.10.18.212 0 9999 i RT:9999:10 ET:8 Displayed 3 out of 3 total prefixes
tcpdump
[root@evpn2 test]# tcpdump -i br10 -eennvv
tcpdump: listening on br10, link-type EN10MB (Ethernet), capture size 262144 bytes
11:30:17.200999 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 62, id 36214, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 1, length 64
11:30:17.201038 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25151, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 1, length 64
11:30:18.218978 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 62, id 36235, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 2, length 64
11:30:18.219012 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25194, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 2, length 64 11:30:19.259006 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 62, id 36266, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 3, length 64 11:30:19.259037 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25211, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 3, length 64 11:30:20.298958 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 62, id 36351, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 4, length 64 11:30:20.298994 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25259, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 4, length 64 11:30:21.338964 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 62, id 36372, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 5, length 64 11:30:21.339001 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25299, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 5, length 64 11:30:22.279971 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 2.2.2.254 tell 2.2.2.2, length 28 11:30:22.279995 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 2.2.2.254 is-at 00:00:01:02:03:10, length 28 11:30:22.378912 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 62, id 36433, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 6, length 64 11:30:22.378944 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25364, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 6, length 64 11:30:23.418964 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 62, id 36484, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 7, length 64 11:30:23.418998 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25395, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 7, length 64 11:30:24.458931 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 62, id 36564, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 8, length 64 11:30:24.458965 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25453, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 8, length 64 11:30:25.499062 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 62, id 36590, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 9, length 64 11:30:25.499097 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25491, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 9, length 64 c11:30:26.539010 00:00:01:02:03:10 > ea:e1:8d:a6:39:96, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 62, id 36603, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 10, length 64 11:30:26.539049 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25532, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 10, length 64 ^C 22 packets captured 22 packets received by filter 0 packets dropped by kernel [root@evpn2 test]# tcpdump -i evpn-vrf -eennvv tcpdump: listening on evpn-vrf, link-type EN10MB (Ethernet), capture size 262144 bytes 11:30:30.698994 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 36708, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 14, length 64 11:30:30.699044 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25754, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 14, length 64 11:30:31.738973 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 36749, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 15, length 64 11:30:31.739022 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25810, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 15, length 64 11:30:32.778979 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 36852, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 16, length 64 11:30:32.779027 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25888, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 16, length 64 11:30:33.818950 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 36868, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 17, length 64 11:30:33.818996 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25971, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 17, length 64 11:30:34.858933 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 36961, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 18, length 64 11:30:34.858981 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 25986, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 18, length 64 11:30:35.898938 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 36998, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 19, length 64 11:30:35.898986 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 26081, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 19, length 64 11:30:36.938957 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 37061, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 20, length 64 11:30:36.939006 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 26179, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 20, length 64 c11:30:37.978971 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 37141, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 21, length 64 11:30:37.979018 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 26261, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 21, length 64 11:30:39.018947 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 37145, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 22, length 64 11:30:39.018991 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 26293, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 22, length 64 11:30:40.058941 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 37160, offset 0, flags [DF], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 23, length 64 11:30:40.059014 ea:e1:8d:a6:39:96 > 00:00:01:02:03:10, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 26390, offset 0, flags [none], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 23, length 64 ^C 20 packets captured 20 packets received by filter 0 packets dropped by kernel
[root@evpn2 test]# tcpdump -i br100 -eennvv
tcpdump: listening on br100, link-type EN10MB (Ethernet), capture size 262144 bytes
11:32:43.818994 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44163, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 142, length 64
11:32:43.819043 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 32603, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 142, length 64
11:32:44.858956 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44248, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 143, length 64
11:32:44.859005 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 32629, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 143, length 64
11:32:45.898953 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44255, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 144, length 64
11:32:45.899004 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 32635, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 144, length 64
11:32:46.938978 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44353, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 145, length 64
11:32:46.939027 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 32710, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 145, length 64
11:32:47.978976 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44361, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7169, seq 146, length 64
11:32:47.979029 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 32784, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7169, seq 146, length 64
^C
10 packets captured
10 packets received by filter
0 packets dropped by kernel
[root@evpn2 test]# tcpdump -i vlan100 -eennvv
tcpdump: vlan100: No such device exists
(SIOCGIFHWADDR: No such device)
[root@evpn2 test]# tcpdump -i vxlan100 -eennvv
tcpdump: listening on vxlan100, link-type EN10MB (Ethernet), capture size 262144 bytes
11:33:23.290832 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44655, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7170, seq 1, length 64
11:33:23.290888 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34488, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7170, seq 1, length 64
11:33:24.298924 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44693, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7170, seq 2, length 64
11:33:24.298986 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34496, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7170, seq 2, length 64
11:33:25.338932 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44724, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7170, seq 3, length 64
11:33:25.338998 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34499, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7170, seq 3, length 64
11:33:26.378908 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44788, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7170, seq 4, length 64
11:33:26.378970 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34602, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7170, seq 4, length 64
11:33:27.418903 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44881, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7170, seq 5, length 64
11:33:27.418966 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34637, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7170, seq 5, length 64
11:33:28.458875 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44951, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7170, seq 6, length 64
11:33:28.458932 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34639, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7170, seq 6, length 64
11:33:29.498916 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 44966, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7170, seq 7, length 64
11:33:29.498977 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 34686, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7170, seq 7, length 64
^C
14 packets captured
14 packets received by filter
0 packets dropped by kernel
[root@evpn2 test]# tcpdump -i enp1s0 -eennvv udp
tcpdump: listening on enp1s0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:57:07.551235 fa:16:3e:43:10:25 > fa:16:3e:11:8c:48, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 17431, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.212.56060 > 10.10.18.209.4789: [bad udp cksum 0x3a3c -> 0x5b92!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 62754, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7186, seq 1, length 64
11:57:07.551327 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 16331, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.209.59282 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x4efc!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 10192, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7186, seq 1, length 64
11:57:08.618917 fa:16:3e:43:10:25 > fa:16:3e:11:8c:48, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 17449, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.212.56060 > 10.10.18.209.4789: [bad udp cksum 0x3a3c -> 0x5b92!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 62834, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7186, seq 2, length 64
11:57:08.619004 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 16417, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.209.59282 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x4efc!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 10246, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7186, seq 2, length 64
11:57:09.658904 fa:16:3e:43:10:25 > fa:16:3e:11:8c:48, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 17547, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.212.56060 > 10.10.18.209.4789: [bad udp cksum 0x3a3c -> 0x5b92!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 62871, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7186, seq 3, length 64
11:57:09.658975 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 16485, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.209.59282 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x4efc!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 10285, offset 0, flags [none], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo reply, id 7186, seq 3, length 64
11:57:10.698939 fa:16:3e:43:10:25 > fa:16:3e:11:8c:48, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 17593, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.212.56060 > 10.10.18.209.4789: [bad udp cksum 0x3a3c -> 0x5b92!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 62933, offset 0, flags [DF], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo request, id 7186, seq 4, length 64
11:57:10.699023 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 16543, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.209.59282 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x4efc!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 10367, offset 0, flags [none], proto ICMP (1), length 84)
[root@evpn2 test]# tcpdump -i vxlan10 -eennvv
tcpdump: listening on vxlan10, link-type EN10MB (Ethernet), capture size 262144 bytes
无无
00:00:01:02:03:05

00:00:01:02:03:04
[root@evpn2 test]# ip a | grep 00:00:01:02:03:04 -B 3
inet6 fe80::9c05:cbff:fe41:1935/64 scope link
valid_lft forever preferred_lft forever
7: br100: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master evpn-vrf state UP group default qlen 1000
link/ether 00:00:01:02:03:04 brd ff:ff:ff:ff:ff:ff
00:00:01:02:03:10
[root@evpn2 test]# ip a | grep '00:00:01:02:03:10' -B 5
4: veth1@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br10 state UP group default qlen 1000
link/ether 3a:31:5e:c0:cc:79 brd ff:ff:ff:ff:ff:ff link-netns host1
inet6 fe80::3831:5eff:fec0:cc79/64 scope link
valid_lft forever preferred_lft forever
5: br10: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master evpn-vrf state UP group default qlen 1000
link/ether 00:00:01:02:03:10 brd ff:ff:ff:ff:ff:ff
节点1 ip netns exec host1 ping 9.9.9.1
[root@evpn2 test]# tcpdump -i vxlan100 -eennvv
tcpdump: listening on vxlan100, link-type EN10MB (Ethernet), capture size 262144 bytes
11:53:45.567149 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 1418, offset 0, flags [DF], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo request, id 16024, seq 1, length 64
11:53:45.567212 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 57044, offset 0, flags [none], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo reply, id 16024, seq 1, length 64
11:53:46.635278 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 1457, offset 0, flags [DF], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo request, id 16024, seq 2, length 64
11:53:46.635344 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 57086, offset 0, flags [none], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo reply, id 16024, seq 2, length 64 11:53:47.675200 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 1561, offset 0, flags [DF], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo request, id 16024, seq 3, length 64 11:53:47.675262 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 57130, offset 0, flags [none], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo reply, id 16024, seq 3, length 64 11:53:48.715193 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 1662, offset 0, flags [DF], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo request, id 16024, seq 4, length 64 11:53:48.715258 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 57203, offset 0, flags [none], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo reply, id 16024, seq 4, length 64 11:53:49.715707 00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 1755, offset 0, flags [DF], proto ICMP (1), length 84) 2.2.2.2 > 9.9.9.1: ICMP echo request, id 16024, seq 5, length 64 11:53:49.715776 00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 57273, offset 0, flags [none], proto ICMP (1), length 84) 9.9.9.1 > 2.2.2.2: ICMP echo reply, id 16024, seq 5, length 64
物理接口
[root@evpn2 test]# tcpdump -i enp1s0 -eennvv udp
tcpdump: listening on enp1s0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:55:07.177095 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 15131, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.209.59282 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x4efc!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 9422, offset 0, flags [DF], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo request, id 16025, seq 1, length 64
11:55:07.177201 fa:16:3e:43:10:25 > fa:16:3e:11:8c:48, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 11711, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.212.56060 > 10.10.18.209.4789: [bad udp cksum 0x3a3c -> 0x5b92!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 61542, offset 0, flags [none], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo reply, id 16025, seq 1, length 64
11:55:08.235207 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 15213, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.209.59282 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x4efc!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 9509, offset 0, flags [DF], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo request, id 16025, seq 2, length 64
11:55:08.235302 fa:16:3e:43:10:25 > fa:16:3e:11:8c:48, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 11724, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.212.56060 > 10.10.18.209.4789: [bad udp cksum 0x3a3c -> 0x5b92!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 61600, offset 0, flags [none], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo reply, id 16025, seq 2, length 64
11:55:09.275221 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 15231, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.209.59282 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x4efc!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 9522, offset 0, flags [DF], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo request, id 16025, seq 3, length 64
11:55:09.275344 fa:16:3e:43:10:25 > fa:16:3e:11:8c:48, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 11787, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.212.56060 > 10.10.18.209.4789: [bad udp cksum 0x3a3c -> 0x5b92!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 61611, offset 0, flags [none], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo reply, id 16025, seq 3, length 64
11:55:10.315163 fa:16:3e:11:8c:48 > fa:16:3e:43:10:25, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 15283, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.209.59282 > 10.10.18.212.4789: [bad udp cksum 0x3a3c -> 0x4efc!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:04 > 00:00:01:02:03:05, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 9623, offset 0, flags [DF], proto ICMP (1), length 84)
2.2.2.2 > 9.9.9.1: ICMP echo request, id 16025, seq 4, length 64
11:55:10.315265 fa:16:3e:43:10:25 > fa:16:3e:11:8c:48, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 11867, offset 0, flags [none], proto UDP (17), length 134)
10.10.18.212.56060 > 10.10.18.209.4789: [bad udp cksum 0x3a3c -> 0x5b92!] VXLAN, flags [I] (0x08), vni 100
00:00:01:02:03:05 > 00:00:01:02:03:04, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 61628, offset 0, flags [none], proto ICMP (1), length 84)
9.9.9.1 > 2.2.2.2: ICMP echo reply, id 16025, seq 4, length 64
11:55:11.330730 fa:16:3e:7d:53:30 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 212: (tos 0x0, ttl 255, id 54371, offset 0, flags [DF], proto UDP (17), length 198)
10.10.18.220.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 3/0/0 host-13-0-0-506960.local. (Cache flush) HINFO, _workstation._tcp.local. PTR host-13-0-0-506960 [fa:16:3e:7d:53:30]._workstation._tcp.local., _services._dns-sd._udp.local. PTR _workstation._tcp.local. (170)
11:55:11.331051 fa:16:3e:97:cb:f7 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 114: (tos 0x0, ttl 255, id 35979, offset 0, flags [DF], proto UDP (17), length 100)
10.10.18.195.5353 > 224.0.0.251.5353: [bad udp cksum 0xfe29 -> 0xe652!] 0*- [0q] 1/0/0 _services._dns-sd._udp.local. PTR _workstation._tcp.local. (72)
11:55:11.331217 fa:16:3e:d9:a5:82 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 255, id 23407, offset 0, flags [DF], proto UDP (17), length 84)
10.10.18.222.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 linux-495458.local. (Cache flush) HINFO (56)
11:55:11.331298 fa:16:3e:b2:24:23 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 114: (tos 0x0, ttl 255, id 42750, offset 0, flags [DF], proto UDP (17), length 100)
10.10.18.116.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 _services._dns-sd._udp.local. PTR _workstation._tcp.local. (72)
11:55:11.331360 fa:16:3e:9b:5c:21 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 114: (tos 0x0, ttl 255, id 19130, offset 0, flags [DF], proto UDP (17), length 100)
10.10.18.155.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 _services._dns-sd._udp.local. PTR _workstation._tcp.local. (72)
11:55:11.331399 fa:16:3e:9c:47:ff > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 200: (tos 0x0, ttl 255, id 52587, offset 0, flags [DF], proto UDP (17), length 186)
10.10.18.221.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 3/0/0 linux-307754.local. (Cache flush) HINFO, _workstation._tcp.local. PTR linux-307754 [fa:16:3e:9c:47:ff]._workstation._tcp.local., _services._dns-sd._udp.local. PTR _workstation._tcp.local. (158)
11:55:11.331443 fa:16:3e:47:25:57 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 114: (tos 0x0, ttl 255, id 337, offset 0, flags [DF], proto UDP (17), length 100)
10.10.18.171.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 _services._dns-sd._udp.local. PTR _workstation._tcp.local. (72)
11:55:11.331488 fa:16:3e:47:25:57 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 114: (tos 0x0, ttl 255, id 337, offset 0, flags [DF], proto UDP (17), length 100)
10.10.18.171.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 _services._dns-sd._udp.local. PTR _workstation._tcp.local. (72)
11:55:11.331531 fa:16:3e:47:25:57 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 114: (tos 0x0, ttl 255, id 337, offset 0, flags [DF], proto UDP (17), length 100)
10.10.18.171.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 _services._dns-sd._udp.local. PTR _workstation._tcp.local. (72)
11:55:11.331576 fa:16:3e:47:25:57 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 114: (tos 0x0, ttl 255, id 337, offset 0, flags [DF], proto UDP (17), length 100)
10.10.18.171.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 _services._dns-sd._udp.local. PTR _workstation._tcp.local. (72)
11:55:11.331622 fa:16:3e:23:7e:86 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 200: (tos 0x0, ttl 255, id 36271, offset 0, flags [DF], proto UDP (17), length 186)
10.10.18.218.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 3/0/0 linux-455865.local. (Cache flush) HINFO, _workstation._tcp.local. PTR linux-455865 [fa:16:3e:23:7e:86]._workstation._tcp.local., _services._dns-sd._udp.local. PTR _workstation._tcp.local. (158)
11:55:11.381189 fa:16:3e:7d:53:30 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 110: (tos 0x0, ttl 255, id 54373, offset 0, flags [DF], proto UDP (17), length 96)
10.10.18.220.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? host-13-0-0-506961.local. ns: host-13-0-0-506961.local. HINFO (68)
11:55:11.443963 fa:16:3e:d9:a5:82 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 23410, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.222.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-495459.local. ns: linux-495459.local. HINFO (62)
11:55:11.499941 fa:16:3e:23:7e:86 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 36285, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.218.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-455866.local. ns: linux-455866.local. HINFO (62)
11:55:11.520404 fa:16:3e:eb:39:71 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 163: (tos 0x0, ttl 255, id 58333, offset 0, flags [DF], proto UDP (17), length 149)
10.10.18.223.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 2/0/0 linux-487018.local. (Cache flush) HINFO, _workstation._tcp.local. PTR linux-487018 [fa:16:3e:eb:39:71]._workstation._tcp.local. (121)
11:55:11.596472 fa:16:3e:9c:47:ff > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 52596, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.221.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-307755.local. ns: linux-307755.local. HINFO (62)
11:55:11.632030 fa:16:3e:7d:53:30 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 110: (tos 0x0, ttl 255, id 54390, offset 0, flags [DF], proto UDP (17), length 96)
10.10.18.220.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? host-13-0-0-506961.local. ns: host-13-0-0-506961.local. HINFO (68)
11:55:11.694732 fa:16:3e:d9:a5:82 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 23418, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.222.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-495459.local. ns: linux-495459.local. HINFO (62)
11:55:11.750910 fa:16:3e:23:7e:86 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 36308, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.218.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-455866.local. ns: linux-455866.local. HINFO (62)
11:55:11.800832 fa:16:3e:eb:39:71 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 58357, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.223.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-487019.local. ns: linux-487019.local. HINFO (62)
11:55:11.846924 fa:16:3e:9c:47:ff > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 52621, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.221.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-307755.local. ns: linux-307755.local. HINFO (62)
11:55:11.882516 fa:16:3e:7d:53:30 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 110: (tos 0x0, ttl 255, id 54405, offset 0, flags [DF], proto UDP (17), length 96)
10.10.18.220.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? host-13-0-0-506961.local. ns: host-13-0-0-506961.local. HINFO (68)
11:55:11.945287 fa:16:3e:d9:a5:82 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 23426, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.222.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-495459.local. ns: linux-495459.local. HINFO (62)
11:55:12.001349 fa:16:3e:23:7e:86 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 36331, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.218.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-455866.local. ns: linux-455866.local. HINFO (62)
11:55:12.051352 fa:16:3e:eb:39:71 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 58373, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.223.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-487019.local. ns: linux-487019.local. HINFO (62)
11:55:12.081901 fa:16:3e:7d:53:30 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 54406, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.220.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 host-13-0-0-506961.local. (Cache flush) HINFO (62)
11:55:12.097783 fa:16:3e:9c:47:ff > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 52639, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.221.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-307755.local. ns: linux-307755.local. HINFO (62)
11:55:12.145306 fa:16:3e:d9:a5:82 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 255, id 23437, offset 0, flags [DF], proto UDP (17), length 84)
10.10.18.222.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 linux-495459.local. (Cache flush) HINFO (56)
11:55:12.202265 fa:16:3e:23:7e:86 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 255, id 36341, offset 0, flags [DF], proto UDP (17), length 84)
10.10.18.218.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 linux-455866.local. (Cache flush) HINFO (56)
11:55:12.298137 fa:16:3e:9c:47:ff > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 255, id 52649, offset 0, flags [DF], proto UDP (17), length 84)
10.10.18.221.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 linux-307755.local. (Cache flush) HINFO (56)
11:55:12.302649 fa:16:3e:eb:39:71 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 255, id 58396, offset 0, flags [DF], proto UDP (17), length 90)
10.10.18.223.5353 > 224.0.0.251.5353: [udp sum ok] 0 [1n] ANY (QM)? linux-487019.local. ns: linux-487019.local. HINFO (62)
11:55:12.502480 fa:16:3e:eb:39:71 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 255, id 58415, offset 0, flags [DF], proto UDP (17), length 84)
10.10.18.223.5353 > 224.0.0.251.5353: [udp sum ok] 0*- [0q] 1/0/0 linux-487019.local. (Cache flush) HINFO (56)
^C
vrf 路由
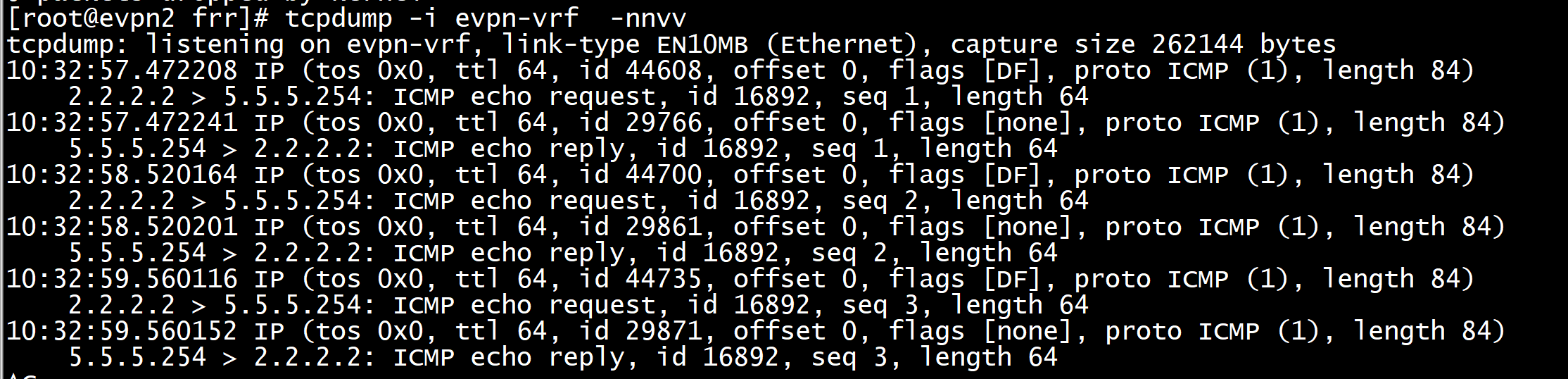
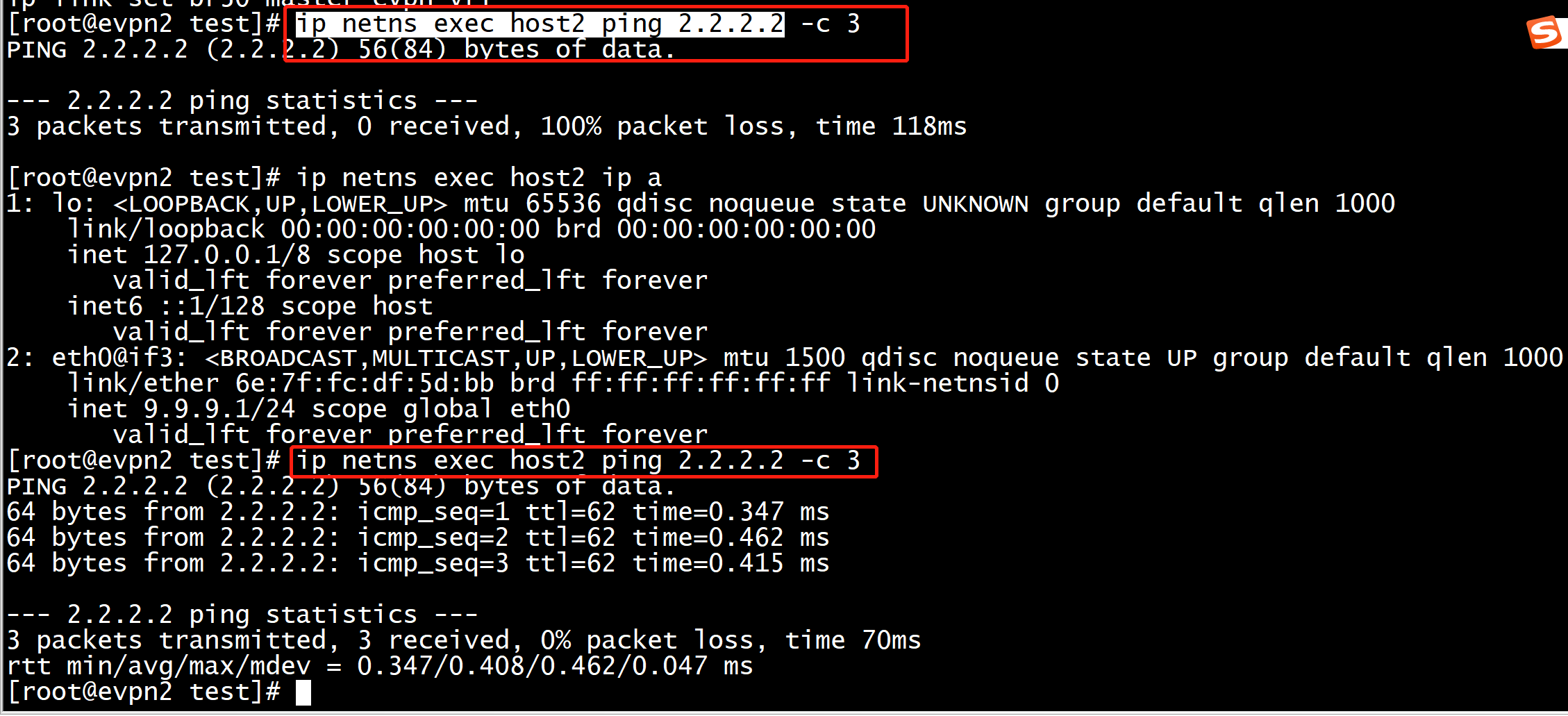
执行ip netns exec host2 ping 2.2.2.3
给evpn-vrf 添加默认路由
ip link add default_g1 type veth peer name default_g
ip link set default_g1 up
ip link set default_g up
#其中default_g1在evpn-vrf,default_g在default
ip link set default_g1 master evpn-vrf
ip addr add 5.5.5.253/24 dev default_g1 ip addr add 5.5.5.254/24 dev default_g
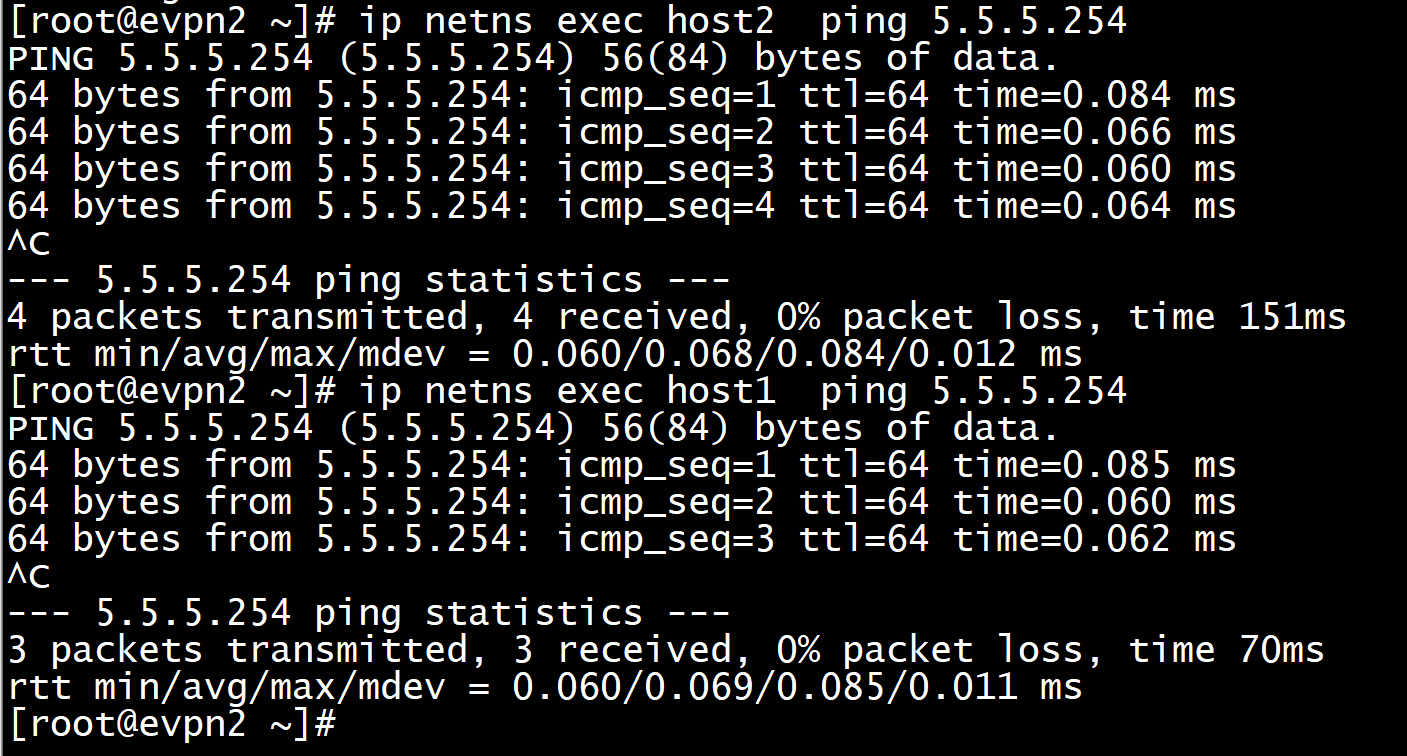
在evpn-vrf 内的子设备上tcpdump抓不到数据