To help more children's shoes of rhythm learning, this paper is divided into Demo actual articles and papers to make narrative.
Briefly explain Xposed frame (hereinafter abbreviated: Xposed)
About Xposed
Brief introduction
Xposed hook is a very powerful tool on the android platform, it can affect the framework services that run without modification APK file, and in the case of simultaneous operation of functions that do not conflict. Xposed based developers can create a lot of powerful module for reverse android crack, landscaping and other aspects of the application, is now available in the market to grab a lot of red envelopes, the message anti-withdrawal application to crack the billing module is also based on this application.
principle
When the brush is written into the system and replace Xposed key file system, the following is the installation package file structure:
META-INF/ 里面有flash-script.sh脚本文件,用于配置各个文件安装位置
system/bin/ 主要为替换系统的Zygote进程执行文件对应的xposed版文件,如app_process
system/framework/XposedBridge.jar jar包位置
system/lib so文件所在位置
system/lib64 so(适用于64架构)文件所在位置
system/xposed.prop xposed版本说明文件
- We all know Zygote process is the core of Android, all applications and system services processes are made Zygote process fork out.
- The system will open when you start this process, the corresponding executable file is / system / bin / app_process, due app_process file is replaced, it launched a version of Xposed Zygote process.
- The process will be loaded Xposed libraries and related functions, including XposedBridge.jar library.
- XposedBridge.jar in XposedBridge.main complete the initialization of the function key and the function of the system will be Xposed hook module.
- Xposed hook java when carrying out the method, using the modified method of virtual machine will be registered as native methods, the JVM call java function, if the function is native, just call it nativeFunc, when you call this method, it will call to the native method.
- In this method, native, java Xposed directly call a method, the method java inside the original method invocation, and inserted hooks across calls , so they hook live this method.
Briefly process is as follows:
You may not fully understand, it does not matter, is not the focus of this article, a simple understanding of the case helps to understand the following.

Hijack Log Demo
Write Xposed module
- Android Studio (hereinafter referred to as: AS) new Android project, the paper called "XposedDemo", and create a new module (module), the paper called "HookLoginModule".
- Add dependent (in build.gradle under HookLoginModule in more versions depend Click here to visit ):
compileOnly 'de.robv.android.xposed:api:82'
Note: Be sure to "compileOnly", please use the old version of AS "provided", not to "implementation" or "compile"
- Add the following in the application of labels on the modules in AndroidManifest.xml:
<!--模块申明,true表示申明为xposed模块-->
<meta-data
android:name="xposedmodule"
android:value="true" />
<!--模块说明,一般为模块的功能描述-->
<meta-data
android:name="xposeddescription"
android:value="这个模块是用来劫持登录的" />
<!--模块兼容版本-->
<meta-data
android:name="xposedminversion"
android:value="54" />
- Hook inlet implement new class HookLogin IXposedHookLoadPackage xposed interface and override method handleLoadPackage:
public class HookLogin implements IXposedHookLoadPackage {
public void handleLoadPackage(XC_LoadPackage.LoadPackageParam lpparam) {
}
}
- In the src / main / assets module (if no assets directory, please create a new one) under the new file xposed_init full class name and class written into HookLogin to complete the registration Hook entrance class:
cn.icheny.xposed.HookLogin
Well, Xposed module has completed basic writing, then write Demo Project
Write Demo Project
- To simplify the article directly under XposedDemo "app" module, renamed "LoginDemo"
- New Login Activity is "LoginActivity" and write the following code:
public class LoginActivity extends AppCompatActivity {
EditText mTvUsername, mTvPassword;
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_login);
mTvUsername = findViewById(R.id.tv_username);
mTvPassword = findViewById(R.id.tv_password);
}
/**
* 登录
*/
public void login(View view) {
String username = mTvUsername.getText().toString();
String password = mTvPassword.getText().toString();
if (TextUtils.isEmpty(username)) {
Toast.makeText(this, "请输入用户名", Toast.LENGTH_SHORT).show();
return;
} else if (TextUtils.isEmpty(password)) {
Toast.makeText(this, "请输入密码", Toast.LENGTH_SHORT).show();
return;
}
if (checkLogin(username, password)) {
startActivity(new Intent(this, LoginSuccessActivity.class));
}
}
/**
* 模拟后台服务器校验登录
*
* @param username 用户名
* @param password 密码
*/
public boolean checkLogin(String username, String password) {
if ("admin".equals(username) && "admin123".equals(password)) {
return true;
}
Toast.makeText(this, "用户名或密码不正确!", Toast.LENGTH_SHORT).show();
return false;
}
}
- In the corresponding login screen layout editing code is as follows:
<?xml version="1.0" encoding="utf-8"?>
<LinearLayout xmlns:android="http://schemas.android.com/apk/res/android"
android:layout_width="match_parent"
android:layout_height="match_parent"
android:orientation="vertical"
android:padding="30dp">
<EditText
android:id="@+id/tv_username"
android:layout_width="match_parent"
android:layout_height="wrap_content"
android:layout_marginTop="30dp"
android:hint="请输入用户名..."
android:imeOptions="actionNext"
android:textSize="18dp" />
<EditText
android:id="@+id/tv_password"
android:layout_width="match_parent"
android:layout_height="wrap_content"
android:layout_marginTop="30dp"
android:hint="请输入密码..."
android:imeOptions="actionDone"
android:inputType="textPassword"
android:textSize="18dp" />
<Button
android:layout_width="match_parent"
android:layout_height="wrap_content"
android:layout_marginTop="30dp"
android:onClick="login"
android:text="登录"
android:textSize="18dp" />
</LinearLayout>
By LoginActivity code can understand the user name must be "admin" password is "admin123" to complete the login. Then we run LoginDemo verify follows:
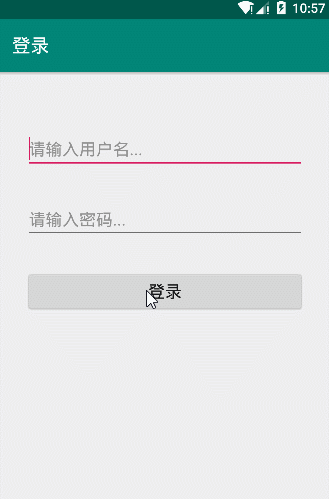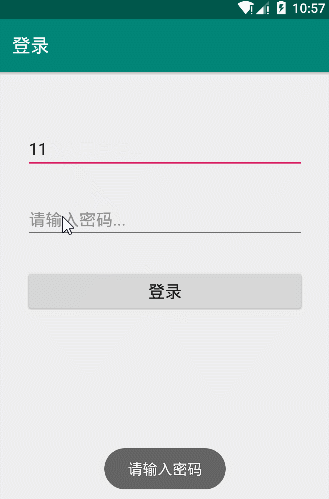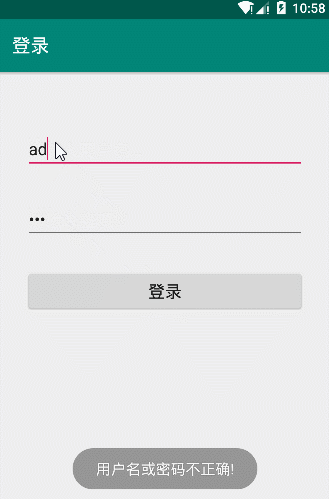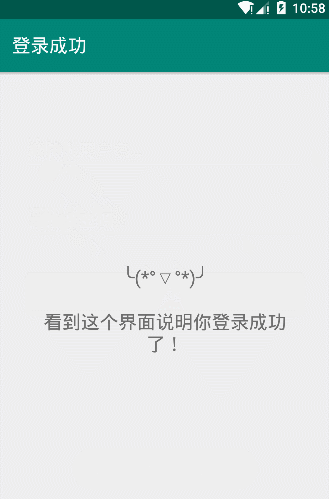
Presentation charts successfully verified code logic.
Hook hijacking
- handleLoadPackage method in edit HookLogin:
......
public void handleLoadPackage(XC_LoadPackage.LoadPackageParam lpparam) {
if (lpparam == null) {
return;
}
Log.e(TAG, "Load app packageName:" + lpparam.packageName);
/**
* 过滤非目标应用,本文目标应用即LoginDemo,包名为:cn.icheny.logindemo
*/
if (!"cn.icheny.logindemo".equals(lpparam.packageName)) {
return;
}
//固定格式
XposedHelpers.findAndHookMethod(
"cn.icheny.logindemo.LoginActivity", // 需要hook的方法所在类的完整类名
lpparam.classLoader, // 类加载器,固定这么写就行了
"checkLogin", // 需要hook的方法名,checkLogin(username,password)
String.class, // 第一个参数,用户名
String.class, // 第二个参数,密码
// Hook回调
new XC_MethodHook() {
@Override
/**
* checkLogin被hook前执行下面的方法
*/
protected void beforeHookedMethod(MethodHookParam param) {
Log.e(TAG, "劫持开始了↓↓↓↓↓↓");
}
/**
* checkLogin被hook后执行下面的方法
*/
protected void afterHookedMethod(MethodHookParam param) {
// hook 用户名和密码
String username = (String) param.args[0];
String password = (String) param.args[1];
Log.e(TAG, "用户名:" + username + " 密码:" + password);
// 被hook后返回自己指定的值(true,表示方法checkLogin调用返回值为true)
param.setResult(true);
Log.e(TAG, "劫持结束了↑↑↑↑↑↑");
}
}
);
}
......
The code we hook of "checkLogin (String username, String password)" under LoginActivity method, obtain a user name and password and do the log printing, and finally allowed to return to true, that is, enter your user name and password for any character can be successful login . beforeHookedMethod and afterHookedMethod i.e. previously described methods "before and after the insertion hook," the.
- Notes code has been very clear, if you have not read, I can help optimize the comments below the article, Xposed module HookLoginModule took us to compile written apk installed to the phone, check the use of the module in Xposed Installer, and then restart cellphone.
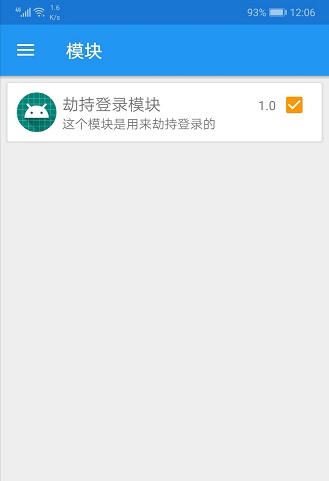
3. Next, open the application again to verify LoginDemo Hook Code:

FIG successfully verified Hook presentation code logic, where the posted log log:
2019-05-08 22:08:06.614 24617-24617/? E/HookLogin: 劫持开始了↓↓↓↓↓↓
2019-05-08 22:08:06.621 24617-24617/? E/HookLogin: 用户名:11 密码:111
2019-05-08 22:08:06.621 24617-24617/? E/HookLogin: 劫持结束了↑↑↑↑↑↑
---------------------------------------------------------------------------
2019-05-08 22:08:14.855 24617-24617/? E/HookLogin: 劫持开始了↓↓↓↓↓↓
2019-05-08 22:08:14.863 24617-24617/? E/HookLogin: 用户名:114554 密码:1114545
2019-05-08 22:08:14.863 24617-24617/? E/HookLogin: 劫持结束了↑↑↑↑↑↑
To successfully obtain a user name and password, so that our work on the big Xposed module caused, Demo articles This is the end!
XposedDemo Download: https://github.com/ausboyue/XposedDemo