SharpUserIP
Function introduction
-
Server login log (requires administrator rights)
-
Extract login logs from the domain controller or remotely to quickly obtain the IP address corresponding to the domain user.
-
Project address: https://github.com/lele8/SharpUserIP
Instructions for use
`___ _ _ _ ___ ___` `/ __| |_ __ _ _ _ _ __| | | |___ ___ _ |_ _| _ \` ``\__ \ ' \/ _` | '_| '_ \ |_| (_-</ -_) '_| || _/`` `|___/_||_\__,_|_| | .__/\___//__/\___|_||___|_|` `|_|`` `` ``Get the log of successful login or the specified user``By @lele`` ` `-H Specify the machine IP or machine name` `-U Administrator account name` `-P Administrator account password` `-D Specify the time range (days) for enumeration` `-F Enumerate specified users` `-O Path to save the result, by default save to the log.txt of the current path` `-All Get logs from all domain controllers`` ` `Usage:` `SharpUserIP.exe -d 7` `SharpUserIP.exe -h ip -d 7` `SharpUserIP.exe -h ip -d 7 -f user1,user2` `SharpUserIP.exe -h ip -u username -p password -d 7` `SharpUserIP.exe -h ip -u username -p password -d 7 -all` `SharpUserIP.exe -h ip -u username -p password -d 7 -f user -o C:\path\result.txt`
Server acquisition log:
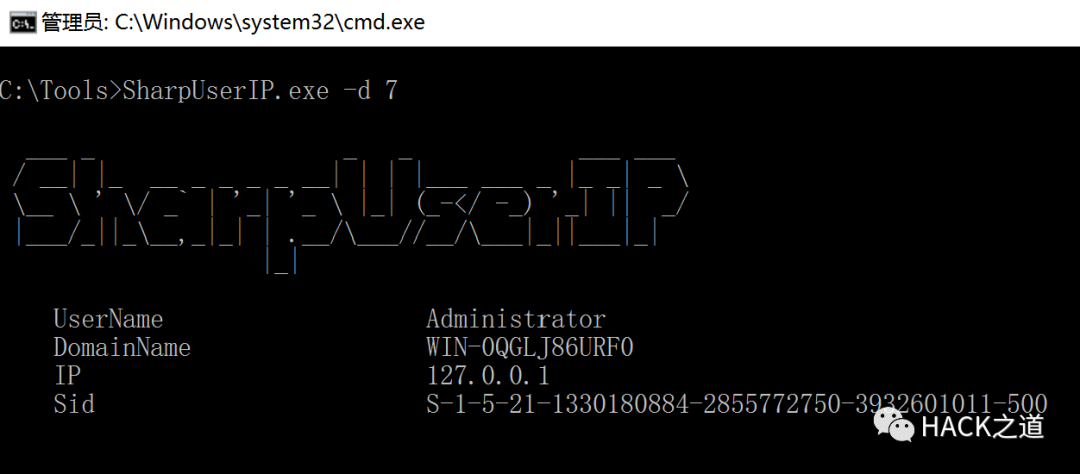
Get logs remotely within the domain:

Disclaimer
This tool is only for legally authorized enterprise security construction activities. If you need to test the usability of this tool, please build a target drone environment yourself. When using this tool, you should ensure that your behavior complies with local laws and regulations and that you have obtained sufficient authorization. Do not scan unauthorized targets. If you commit any illegal behavior while using this tool, you will be responsible for the consequences. The author and this official account will not bear any legal and joint liability.
`How to learn hacking & network security
As long as you like my article today, my private network security learning materials will be shared with you for free. Come and see what is available.
1. Learning roadmap
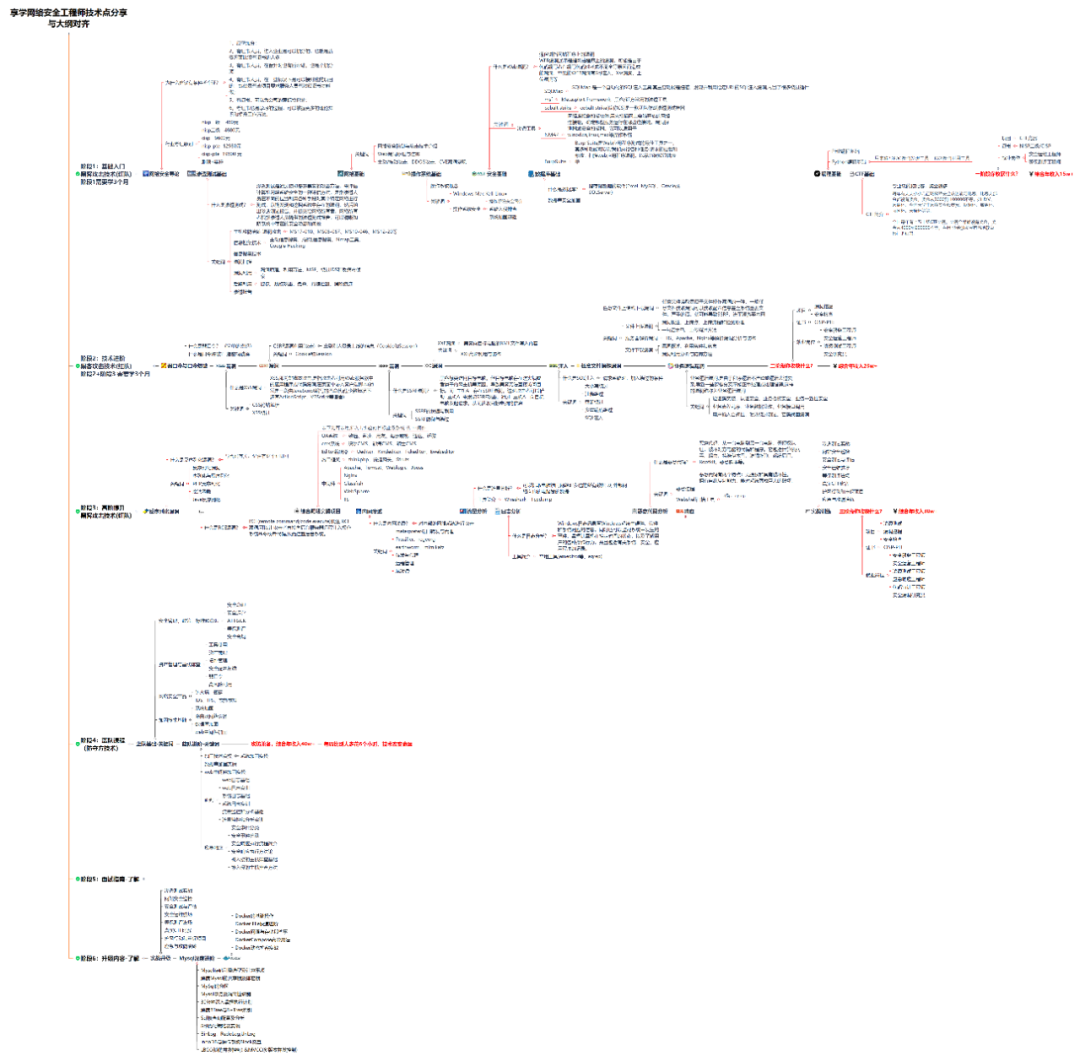
There are a lot of things to learn about attack and defense. I have written down the specific things you need to learn in the road map above. If you can complete them, you will have no problem getting a job or taking on a private job.
2. Video tutorial
Although there are many learning resources on the Internet, they are basically incomplete. This is an Internet security video tutorial I recorded myself. I have accompanying video explanations for every knowledge point in the roadmap above.
The content covers the study of network security laws, network security operations and other security assessments, penetration testing basics, detailed explanations of vulnerabilities, basic computer knowledge, etc. They are all must-know learning contents for getting started with network security.
(They are all packaged into one piece and cannot be expanded one by one. There are more than 300 episodes in total)
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
3. Technical documents and e-books
I also compiled the technical documents myself, including my experience and technical points in participating in large-scale network security operations, CTF, and digging SRC vulnerabilities. There are more than 200 e-books. Due to the sensitivity of the content, I will not display them one by one.
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
4. Toolkit, interview questions and source code
"If you want to do your job well, you must first sharpen your tools." I have summarized dozens of the most popular hacking tools for everyone. The scope of coverage mainly focuses on information collection, Android hacking tools, automation tools, phishing, etc. Interested students should not miss it.
There is also the case source code and corresponding toolkit mentioned in my video, which you can take away if needed.
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
Finally, here are the interview questions about network security that I have compiled over the past few years. If you are looking for a job in network security, they will definitely help you a lot.
These questions are often encountered when interviewing Sangfor, Qi Anxin, Tencent or other major companies. If you have good questions or good insights, please share them.
Reference analysis: Sangfor official website, Qi’anxin official website, Freebuf, csdn, etc.
Content features: Clear organization and graphical representation to make it easier to understand.
Summary of content: Including intranet, operating system, protocol, penetration testing, security service, vulnerability, injection, XSS, CSRF, SSRF, file upload, file download, file inclusion, XXE, logical vulnerability, tools, SQLmap, NMAP, BP, MSF…
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.