Configure and deploy squid traditional agency services reference Bowen: https://blog.51cto.com/14154700/2406060
configuration squid transparent proxy reference Bowen: https://blog.51cto.com/14154700/2406121
ACL access control service squid:
squid proxy provides a powerful control mechanism, can filter for a variety of conditions, source address, destination address, URL path access, access time by setting ACL and reasonable restrictions.
In the configuration file squid.conf, ACL the access control implemented in two steps: 1, using the conditions defined ACL configuration item needs to be controlled; 2, CI http_access by the defined list do "allow" or "deny" Access control.
1, each line ACL configuration may define an access control list, the following format:
acl content type list List name List
Wherein, the list is the name of the custom , it is equivalent to the ACL a name; "List Type" squid must use a predefined value, the control conditions corresponding to different categories; "content list" is a specific object to be controlled, different types of the list corresponding to the content are not the same, can have multiple values (separated by a space, the relationship of "or").
Common access control list types are as follows:
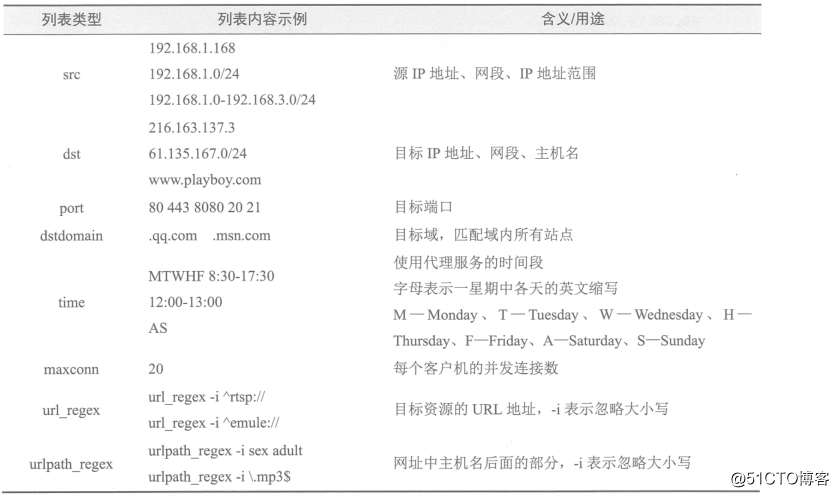
ACL Definition Example:
[root@localhost /]# vim /etc/squid.conf
..........................
acl localnet src 10.0.0.0/8 # RFC1918 possible internal network #squid默认的一些ACL
acl localnet src 172.16.0.0/12 # RFC1918 possible internal network #默认存在
acl localnet src 192.168.0.0/16 # RFC1918 possible internal network #默认存在
acl localhost src 127.0.0.1/255.255.255.255 #源地址为127.0.0.1
acl mylan src 192.168.1.0/24 192.168.4.0/24 #客户机网段
acl to_localhost dst 127.0.0.0/8 #目标地址为127.0.0.0/8网段
acl mc20 maxconn 20 #最大并发连接量为20
acl blackurl url_regex -i ^rtsp:// ^emule:// #以rtsp://等开头的URL
acl mediafile urlpath_regex -i \.mp3$ \.mp4$ \.rmvb$ #以.mp3等结尾的URL路径
acl worktime time MTWHF 9:00-18:00 #时间为周一至周五的 9:00-18:00
........................When there are many restrictions in a subject in need of the same class, a separate file may be used to store a file location corresponding to the row disposed at the content acl. as follows:
[root@localhost /]# mkdir /etc/squid
[root@localhost /]# cd /etc/squid
[root@localhost squid]# vim ipblock.list #建立目标IP地址名单
61.135.167.36
125.39.127.25
60.28.14.0
[root@localhost squid]# vim dmblock.list #建立目标域地址名单
.qq.com
.msn.com
.live.com
.verycd.com
[root@localhost squid]# vim /etc/squid.conf
acl ipblock dst "/etc/squid/ipblock.list" #调用指定文件中的列表内容
acl dmblock dstdomain "/etc/squid/dmblock.list"
When the ACL is set up, you need to be controlled by http_access configuration items. It must be noted that, http_access configuration line must be placed after the corresponding row acl configuration. Each row arranged http_access determining an access rule, the following format:
http_access allow or deny list name
The acl just defined rules applied to, the following:
[root@localhost squid]# vim /etc/squid.conf
......................
http_access deny !Safe_ports #squid默认存在的访问权限
http_access deny mediafile #禁止客户机下载mp3等文件
http_access deny ipblock #禁止客户机访问黑名单中的IP地址
http_access deny dmblock #禁止客户机访问黑名单中网站域
http_access deny mc20 #客户机的并发连接量超过20时将被阻止
http_access allow worktime #允许客户机在工作时间内上网
reply_body_max_size 10 MB #允许下载的最大文件大小(10M)
.......................
http_access deny all #默认禁止所有客户机使用代理,squid默认存在的访问权限When configuring access, you need to pay attention to the following points:
- Each http_access rules, you can include multiple simultaneous access control list names, separated by spaces between each list, it is "AND", expressed must meet all the conditions will limit the access control list corresponding.
- Need to use the inverted condition, you can add "!" Sign in front of the access control list.
- When performing access control, squid will be checked in accordance with the order of the rules in turn, if a match is found the rule is no longer search backward (this rule and iptables match similar). Therefore, the order of the rules is important.
- When not set any rules, squid service denies client's request. This is why the default configuration file ACL rule, there are three network segment, if you want to reject three segments in a default exists, the need to comment it out, and then to limit, in order to avoid conflict, resulting in access rules do not take effect.
- There are rules but can not find items that match: squid will use the last rule opposite action, that is, if a rule is best to allow, reject the client's request, otherwise the request is allowed, the final rule exists by default is " http_access deny all "
- Typically, the most commonly used control rules on the front, to reduce the load of squid. On the overall policy access control, we recommend the use of "first refusal to allow" or "first refused to allow" approach.
If you want to configure more precise control can refer Bowen: https://blog.51cto.com/jafy00/682590
Two, squid log analysis:
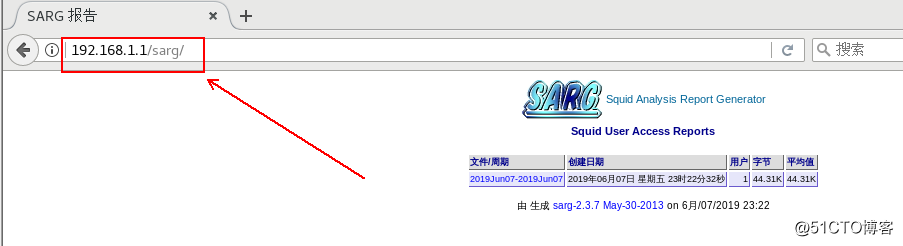
In order for us to view the log more intuitive, you could use SARG, it is a squid log analysis tool, HTML format, detailing each user to access information on the Internet site, time occupancy information, rank, number of connections, traffic Wait.
SARG deployment process is as follows:
1, the installation of the GD library system tray:
[root@localhost yum.repos.d]# yum -y install gd gd-devel2, install SARG:
[root@localhost src]# tar zxf sarg-2.3.7.tar.gz
[root@localhost src]# cd sarg-2.3.7/
[root@localhost sarg-2.3.7]# ./configure --prefix=/usr/local/sarg --sysconfdir=/etc/sarg --enable-extraprotection && make && make installCI following meanings:
--prefix = / usr / local / SARG: specify the installation directory;
--sysconfdir = / etc / SARG: configuration file directory, if not specified, the default is / usr / local / etc;
--enable- extraprotection: Add extra security protection
3, Configuration:
[root@localhost sarg-2.3.7]# cd /etc/sarg/
[root@localhost sarg]# vim sarg.conf
......................
#若只实现基本的功能,则配置以下三项即可:
access_log /usr/local/squid/var/logs/access.log #指定squid的访问日志文件
output_dir /var/www/html/sarg #sarg报告的输出目录,指向网站的根目录下
www_document_root /var/www/html #网页根目录
#其余一些优化的配置项如下,根据需求来改即可:
title "Squid User Access Reports" #网页标题
user_ip no #使用用户名显示
exclude_hosts /usr/local/sarg/noreport #指定不计入排序的站点列表文件
topuser_sort_field connect BYTES reverse
#在top排名中,指定连接次数、访问字节数,采用降序排列,升序将reverse换成normal即可。
user_sort_field connect reverse #对于用户访问记录,连接次数按降序排列
overwrite_report no #当那个日期报告已经存在,是否覆盖报告
mail_utility mailq.postfix #发送邮件报告的命令
charset utf-8 #使用字符集
weekdays 0-6 #指定top排序时的星期周期,0为周日。
hours 7-12,14,16,18-20 #指定top排序时的时间周期。
4, run:
[root@localhost sarg]# touch /usr/local/sarg/noreport
#上面的配置项中添加了不计入排序的站点,需要存在这个文件中。
#这个文件中添加的域名将不被显示在排序中。
[root@localhost sarg]# ln -s /usr/local/sarg/bin/sarg /usr/local/bin #设置符号链接
[root@localhost sarg]# sarg #执行sarg启动一次记录。
SARG: 纪录在文件: 546, reading: 100.00%
SARG: 成功的生成报告在 /var/www/html/sarg/2019Jun07-2019Jun07
[root@localhost sarg]# systemctl start httpd #启动httpd服务,若没有该服务,须自行安装。5. Verification: