Excerpt from: Information System project 32 hours clearance (only for learning exchanges, tort deleted!)
Connected articles soft test - Project Management Professional (information technology and information systems a)
Application Integration Technology
Basic knowledge points
- Database and data warehouse technology
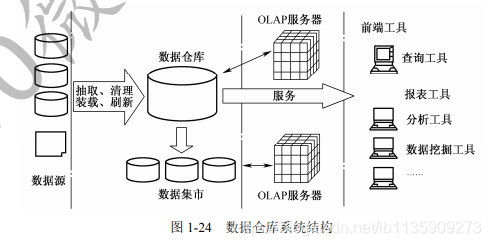
(1) The data warehouse is a subject-oriented, integrated, relatively stable data collection that reflects historical changes and is used to support management decision-making.
(2) The structure of the data warehouse system is shown in the figure below
2. Web Service Technology
(1) The typical technology of Web services is
used to transfer information, the Simple Object Access Protocol (SOAP), the Web Services Description Language (WSDL) used to describe services, and the unified description of Web service registration. Discovery and Integration Specification UDDI (Universal Description, Discovery and Integration), XML for data exchange.
(2) Applicable to the situation of Web Service: across firewalls, application integration, B2B integration, software reuse.
(3) The situation that does not apply to Web Service: stand-alone applications, homogeneous applications on the local area network.
- JavaEE structure
(1) JavaEE applications divide the development work into two categories: business logic development and presentation logic development, and the rest of the system resources are handled by the application server, and there is no need to code the middle-tier resources and operation management.
(2) The JavaEE application server operating environment mainly includes three parts: components, containers, and services. The component is the code, the container is the environment, and the service is the interface.
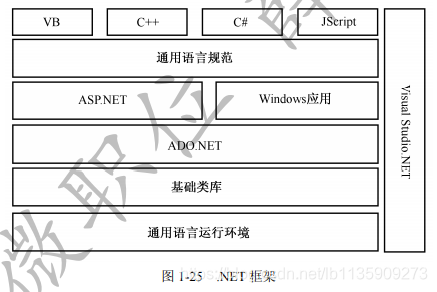
- .NET architecture
The general language runtime environment is at the bottom of the .NET development framework, and the penultimate layer is the basic class library, as shown in the following figure
5. Software middleware
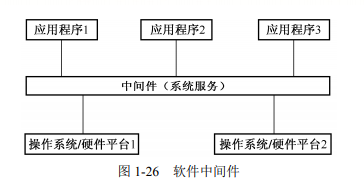
(1) Middleware solves the heterogeneous problems of distributed systems and has standard program interfaces and protocols.
(2) Middleware is usually divided into:
- Database access middleware, typical technologies such as ODBC on Windows platform and JDBC on Java platform.
- Remote procedure call middleware (RPC), in terms of effect, is the same as executing local calls.
- Message-oriented middleware (MOM) for platform-independent data transfer, such as IBM's MQSeries.
- Distributed object middleware, such as CORBA of OMG, RMI/EJB of Java, DCOM of Microsoft, etc.
- Transaction middleware, complete transaction management and coordination, load balancing, failure recovery and other tasks, such as IBM/BEA's Tuxedo, EJB-supported JavaEE application server, etc.
computer network Technology
Basic knowledge points
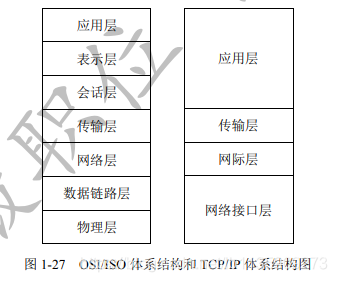
- OSI seven-layer protocol
(1) The left side of the figure below is the OSI/ISO system structure, and the right side is the TCP/IP system structure diagram
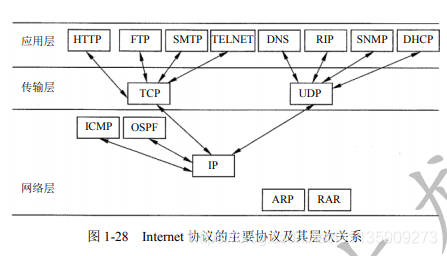
(2) The main protocols of the Internet protocol and their hierarchical relationships are shown in the figure below
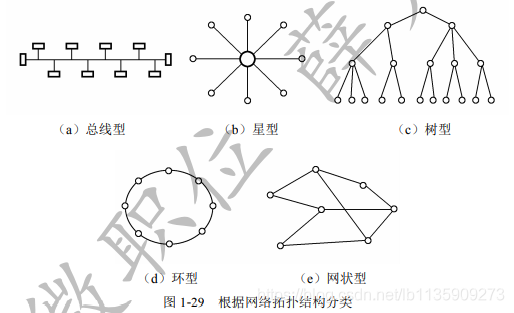
(3) According to the network topology classification, it is divided into Bus type, star type, tree type, ring type, mesh, as shown in the following figure
(4) The data exchange in the network can be divided into: circuit switching, packet switching, ATM switching, all-optical switching and label switching.
(5) The network access technology is divided into optical fiber interface, coaxial cable access, copper wire access, and wireless access.
(6) Wireless network refers to the use of radio waves as the transmission medium of information, which can be divided into: wireless personal area network, wireless local area network, wireless metropolitan area network, and cellular mobile communication network according to the application field.
- Network server and network storage technology
(1) The biggest difference between a network server and a personal computer is its reliability in a multi-user and multi-task environment.
(2) Network storage technologies include DAS, NAS, and SAN.
- Integrated wiring and computer room engineering
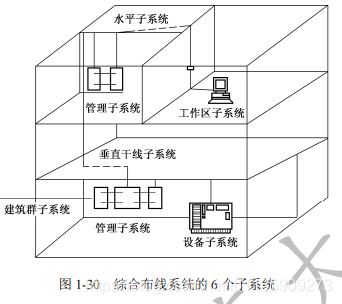
(1) The integrated wiring system includes 6 subsystems, as shown in the following figure.
(2) The computer equipment in the computer room should be arranged in zones, mainly including: host area, memory area, data input area, data output area, communication area, monitoring and dispatching area, etc. .
(3) The distance between communication and equipment in the host room should meet the following requirements:
- The distance between the two opposite cabinet fronts should not be less than 1.5m;
- The side (or unused side) of the cabinet should not be less than 0.5m from the wall. When maintenance and testing are required, the distance between the cabinet and the wall should not be less than 1.2m;
- The clear width of the walkway should not be less than 1.2m
(4) The lighting of the computer room generally adopts non-glare multi-grid lights; the illuminance of the host room is not less than 300LUX, the auxiliary room is not less than 200LUX, and the fault lighting is not less than 600LUX. The lighting of the computer room should be controlled separately, in accordance with the relevant electrical design and construction specifications.
(5) The power supply system of the computer room should adopt double loop power supply, and choose three-phase five-wire power supply.
(6) Four grounding methods should be adopted in the machine room:
- AC working grounding, the grounding resistance should not be greater than 4 Ω;
- Safe working grounding, the grounding resistance should not be greater than 4 Ω;
- DC working grounding, the grounding resistance should be determined according to the specific requirements of the computer system;
- Lightning protection grounding should be implemented in accordance with "Code for Design of Building Lightning Protection" GB 50057-95.
(7) The temperature and humidity of the computer room when starting up are shown in the table below
| Level item | Class A | Class B | |
|---|---|---|---|
| summer | winter | annual | |
| temperature | 23℃ ± 2℃ | 20℃ ± 2℃ | 18℃ ~ 28℃ |
| Relative humidity | 45% ~ 65% | 40% ~ 70% | |
| Temperature change rate | <5℃/h and no condensation | <10℃/h and no condensation | |
(8) The temperature and humidity requirements of the computer room during shutdown are shown in the table below
| project | Class A | Class B |
|---|---|---|
| temperature | 5℃ ~ 35℃ | 5℃ ~ 35℃ |
| Relative humidity | 40% ~ 70% | 20% ~ 80% |
| Temperature change rate | <5℃/h and no condensation | <10℃/h and no condensation |
(9) Calculation formula of RJ45 joint demand:
RJ45 demand: m = n * 4 + n * 4 * 15%
- m is the total demand of RJ45
- n is the total amount of information points
- n * 4 * 15% is the margin left
(10) The calculation formula of the demand for
information modules: the demand for information modules: m = n + n * 3%
- m is the total demand for information modules
- n is the total amount of information points
- n * 3% is the margin
(11) Requirements for related bending radius
- The bending radius of the optical cable cannot be less than 30cm
- The bending radius of the thick coaxial cable cannot be less than 30cm
- The bending radius of the coaxial thin cable should not be less than 20cm
(12) Requirements for concealed pipelines
-
The laying route of the concealed pipeline should be straight line, do not choose the curved route, if it is necessary to play, the radius of curvature should not be less than 6 times the outer diameter of the pipe
-
If the outer diameter of the concealed tube is greater than 50mm, the radius of curvature should not be less than 10 times the outer diameter of the tube
-
The angle of turning should not be less than 90°, and there should be no more than two bends
-
If there are two bends, try to set the bend at both ends of the elbow section, and the length of the section shall not exceed 15m. At the same time, there shall be no S-shaped bends or U-shaped bends in this section.
-
If the length of the bending pipe exceeds 20m, a joint box (joint box or transition box) should be installed in this section
-
Network planning, design and implementation
(1) Today's LAN technology is mainly switched Ethernet technology
(2) When choosing a topological structure, the main factors that should be considered are: geographic environment, transmission medium, transmission distance, and reliability.
(3) The existence of the convergence layer depends on the size of the network
(4) Network communication equipment selection includes: core switch selection, aggregation layer/access layer switch selection, remote access and access equipment selection
- Network security and its prevention technology
(1) The basic elements of information security are: confidentiality, integrity, availability, controllability, and auditability. In order to achieve the above goals, the tasks that need to be done include: formulating security policies, user authentication, encryption, access control, auditing and management
(2) The typical network attack steps are generally: information collection, probing to find breakthroughs, implementation of attacks, fire records, and retention of access rights
(3) The five levels of information security are: user independent protection level, system audit protection level, security mark protection level, structured protection, and access verification protection level.
(4) The firewall cannot prevent and detect hacker attacks and virus intrusions based on data content, and at the same time cannot control violations between internal networks. Scanners cannot detect ongoing intrusions, and it may become a tool for attackers. Anti-virus software is powerless against network-based attacks (such as profiling, attacks against vulnerabilities). At present, there are few mature security audit systems in the market. Even if there are products in the name of audit, they are more engaged in intrusion detection.
- Network management
Network management includes the use, synthesis, and coordination of hardware, software, and human resources to monitor, test, configure, allocate, evaluate, and control network resources, so that some network requirements can be met at a reasonable price, such as actual operating performance, Service quality, etc. When the network fails, it can report and deal with it in time. At the same time, an important job in network management is backup.
Information Security Management
Basic knowledge points
-
Information Security Management System (ISMS): It is part of the overall management system. It is a method based on business risks to establish, implement, operate, monitor, review, maintain and improve the structure, policies, planning activities, responsibilities, practices, procedures, processes and resources of information security.
-
The basic attributes of information security are shown in the following table
| Completeness | Refers to the characteristics of information that is not modified, damaged, inserted, delayed, out of order, and not lost during storage or transmission |
|---|---|
| Availability | Refers to the feature that information can be accessed by legitimate users and can be used in the required order. That is, you can access the required information when you need it |
| Confidentiality | Refers to the characteristic that information is not disclosed to or used by unauthorized individuals and entities |
| Controllability | Refers to the authority that can control the confidentiality of information at any time |
| reliability | Refers to the characteristic that information continuously serves users with a quality recognized by users |
-
Information security management activities mainly include: defining information security strategies, defining the scope of the information security management system, conducting information security risk assessment, determining management objectives and selecting management measures, and preparing information security practicability statements.
-
Information security grade protection is the basic system, method and strategy for the security protection of information systems implemented in the process of informationization in our country.
-
The main links of grade protection: grading, filing, safety construction rectification, grade evaluation and safety inspection.
-
Symmetric encryption technology
Encryption and decryption use the same key. Therefore, the symmetric encryption key is short and simple and quick to use. Commonly used symmetric encryption algorithms are: DES (Data Encryption Standard), 3DES, IDEA (International Data Encryption Algorithm), AES, etc.
- Asymmetric encryption technology
Encryption and decryption use different keys. Asymmetric encryption algorithms require two keys: public key and private key. The public key and the private key are a pair. If you use A’s public key for encryption, you must use A’s private key for decryption. The asymmetric encryption algorithm has slow encryption speed and is not suitable for encrypting large amounts of data. Commonly used asymmetric encryption algorithms are: RSA, Elgamal, ECC, etc. Among them, RSA can realize digital signature and data encryption at the same time.
- Hash function
Use the Hash function to perform a Hash operation on a part of the message to get the Hash code, that is, the message summary. The sender sends the message summary together with the original message to the receiver, and the receiver performs the Hash operation again and compares it with the received Hash code to verify whether the message has been tampered with. This process takes advantage of the characteristics of the Hash function: if even one letter is changed in a piece of plain text, the subsequent Hash codes will all produce different values.
- digital signature
The sender A uses its private key for digital signature, and the receiver B uses the sender A's public key for verification. This is because A's private key is only owned by A, and the sender cannot deny his signature.
Features of digital signature:
- Signers cannot deny their signatures
- No one else can forge the signature
- Certification
The difference between authentication and encryption: encryption is used to ensure the confidentiality of data and prevent passive total; authentication is used to ensure the authenticity of the sender/receiver and the integrity of the data, prevent active attacks, and authentication is the first defense of security protection .
The difference between authentication and digital signature: digital signature allows a third party to verify and is non-repudiation, while authentication does not.
Supplementary knowledge points
| grade | security function | Guarantee/effectiveness | State management level | Object |
|---|---|---|---|---|
| First level | User self-protection | Basic guarantee | Autonomy | SMEs |
| Level 2 | System audit protection | Plan tracking | guide | General systems used by government agencies, and information systems for internal production management and control of enterprises and institutions |
| Level 3 | Security mark protection | Well-defined | Supervise | Basic information network, government, key projects, large state-owned enterprises |
| Level 4 | Structured protection | keep improve | Mandatory | Important subsystems of information systems in important departments of national government agencies |
| Level 5 | Verification protection | Strictly monitor | Exclusive control | Dedicated information system for important core departments of the country |
Next-generation information technology
Basic knowledge points
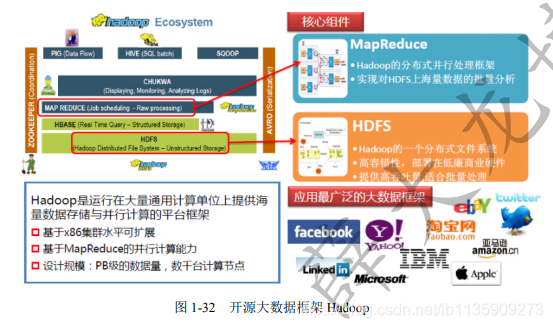
- Big Data
(1) Big data 5V features: Volume (large volume), Velocity (high speed), Variety (diversity), Value (value), Veracity (authenticity)
(2) Big data processing system needs to go through 5 links: data preparation; storage management; calculation processing; data analysis; knowledge display
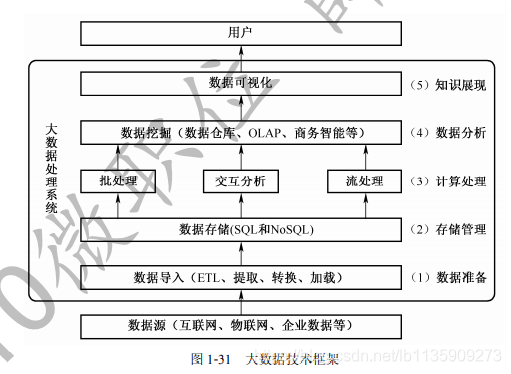
(3) Key technologies of big data
- HDFS: It can provide high-throughput data access, which is very suitable for applications on large-scale data sets.
- HBase: Different from the general relational database, it is a database for unstructured data storage.
- MapReduce: A programming model, the main idea: the concepts "Map (mapping)" and "Reduce (reduce)".
- Chukwa: A data collection system for monitoring large-scale distributed systems.
2. Cloud Computing
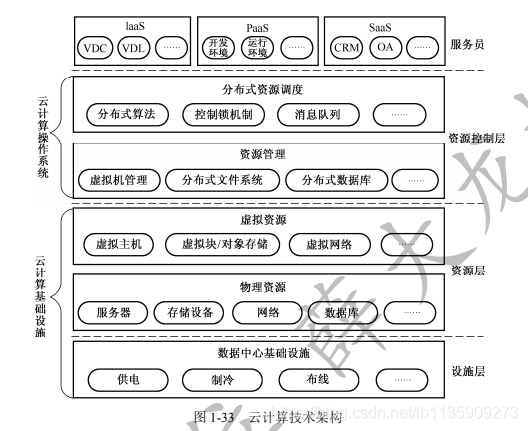
(1) Cloud computing service types
- IaaS (Infrastructure as a Service)
- PaaS (Platform as a Service)
- SaaS (Software as a Service)
(2) 4 layers of cloud computing technology architecture: facility layer, resource layer, resource control layer, service layer
3. Internet of Things
(1) Internet of things architecture
- Perception layer: responsible for information collection and information transmission between objects
- Network layer: Among the three layers of the Internet of Things, the most standardized, industrialized, and mature part
- Application layer: implement the application
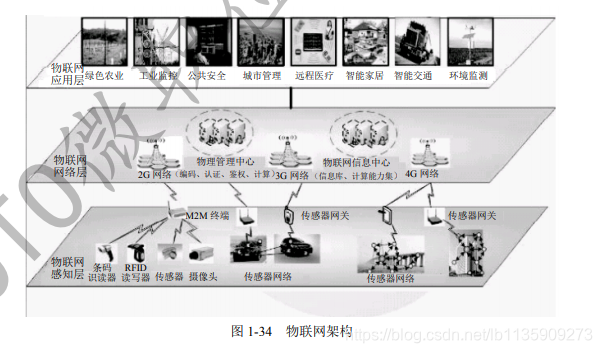
(2) Key technologies of the Internet of Things
The perception layer is the basic layer of the Internet of Things architecture. The main technologies include: automatic identification technology of products and sensors (barcodes, RFID, sensors, etc.), wireless transmission technology (WLAN, Bluetooth, ZigBee, UWB), self-organizing networking technology, middleware technology
- Mobile Internet
(1) Mobile Internet = mobile communication network + Internet content and applications, it is not only an extension of the Internet, but also the development direction of the Internet
(2) Mobile Internet not only has simple copying and transplantation of traditional Internet applications, but also has the following new features:
- Access mobility
- Time fragmentation
- Life relevance
- Terminal diversity
(3) Key technologies of mobile Internet
- Architecture technology SOA: Service Oriented Architect, a service-oriented architecture, does not involve the underlying programming interface and communication model, Web Service is currently the main technology to achieve SOA.
- Page display technology Web 2.0: Strictly speaking, it is not a technology, but an Internet mindset.
The following table shows the difference between Web 1.0 and Web 2.0
| project | Web 1.0 | Web 2.0 |
|---|---|---|
| Page style | Complex structure and cumbersome pages | Simple page, smooth style |
| Degree of personalization | Vertical and popular | Personalization, highlighting self-brand |
| User experience level | Low participation, passive acceptance | High participation, interactive acceptance |
| Communication degree | Information is blocked, and the level of knowledge is low | Well-informed and highly knowledgeable |
| Sensibility | Pursue material value | Pursue spiritual value |
| Feature | Pursuit of functional benefits | Experience the pursuit of emotional benefits |
- Page display technology HTML5: The API is extended on the basis of the original HTML. The biggest advantage is that it can be debugged and modified directly on the web page.
- Mainstream development platform Android: It is characterized by easy entry, because Android's middle layer is mostly implemented in Java, with relatively fewer instructions, relatively simple development, and an active development community with abundant development resources.
- Mainstream development platform iOS: A non-open source operating system. Developers must join the Apple Developer Program and need to pay to obtain Apple’s approval. The development languages are Objective-C, C and C++, which is more difficult to develop than Android.
- Mainstream development platform Windows Phone: A mobile operating system of Microsoft, with development technologies such as C and C#.
Corporate Chief Information Officer and his responsibilities
Basic knowledge points
- Related concepts
CFO: Chief Financial Officer
CTO: Chief Technology Officer
COO: Chief Operating Officer
CIO: Chief Information Officer
- CIO's main responsibilities
From the perspective of CIO's responsibilities, CIO needs to be three types of experts, its enterprise business experts, IT experts and management experts. The system analyst is the best candidate for the CIO. The following briefly introduces the main responsibilities of the CIO:
- Provide information to help companies make decisions
- Help companies formulate medium and long-term development strategies
- Effectively manage the IT department
- Designated information system development plan
- Build a positive IT culture