题目给出加密代码如下:
<?php
$miwen="a1zLbgQsCESEIqRLwuQAyMwLyq2L5VwBxqGA3RQAyumZ0tmMvSGM2ZwB4tws";
function encode($str){
$_o=strrev($str);
// echo $_o;
for($_0=0;$_0<strlen($_o);$_0++){
$_c=substr($_o,$_0,1);
$__=ord($_c)+1;
$_c=chr($__);
$_=$_.$_c;
}
return str_rot13(strrev(base64_encode($_)));
}
highlight_file(__FILE__);
/*
逆向加密算法,解密$miwen就是flag
*/
?> 看其代码加密逻辑如下:
1、反转字符串
2、逐位提取各位上的字符转换为ascii后-1
3、进行base64编码
4、反转字符串
5、rot13加密
6、输出密文
根据以上逻辑,用python3给出解密代码如下:
import base64
# ROT13字符变换,要变回去再调用一次即可。
def rot13(s, OffSet=13):
def encodeCh(ch):
f = lambda x: chr((ord(ch) - x + OffSet) % 26 + x)
return f(97) if ch.islower() else (f(65) if ch.isupper() else ch)
return ''.join(encodeCh(c) for c in s)
def main():
miwen = 'a1zLbgQsCESEIqRLwuQAyMwLyq2L5VwBxqGA3RQAyumZ0tmMvSGM2ZwB4tws'
miwen = rot13(miwen)
miwen = miwen[::-1]
miwen = base64.b64decode(miwen)
miwen = str(miwen,'utf-8')
print(miwen)
mingwen = ""
for _0 in range(0, len(miwen)):
_c = ord(miwen[_0])
fuck = (_c)-1
mingwen+=(chr(fuck))
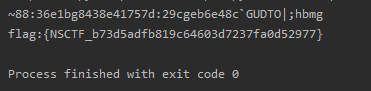
print(mingwen[::-1])
if __name__ == '__main__':
main()运行得到flag: