1.外围信息搜集
1.1whois域名注册信息查询
示例代码如下
msf > whois testfire.net

1.2网站的目录结构
示例代码如下
msf > use auxiliary/scanner/http/dir_scanner
msf auxiliary(scanner/http/dir_scanner) > set THEREADS 50
THEREADS => 50
msf auxiliary(scanner/http/dir_scanner) > set RHOSTS www.testfire.netRHOSTS => www.testfire.net
msf auxiliary(scanner/http/dir_scanner) > exploit

1.3搜索网站中的E-mail地址
示例代码如下
msf auxiliary(scanner/http/dir_scanner) > use auxiliary/gather/search_email_collector
msf auxiliary(gather/search_email_collector) > set DOMAIN altoromutual.com
DOMAIN => altoromutual.com
msf auxiliary(gather/search_email_collector) > run
2.主机探测与端口扫描
2.1Metasploit的主机发现模块

示例代码如下
msf auxiliary(gather/search_email_collector) > use auxiliary/scanner/discovery/arp_sweep
msf auxiliary(scanner/discovery/arp_sweep) > show options
Module options (auxiliary/scanner/discovery/arp_sweep):
Name Current Setting Required Description
---- --------------- -------- -----------
INTERFACE no The name of the interface
RHOSTS yes The target address range or CIDR identifier
SHOST no Source IP Address
SMAC no Source MAC Address
THREADS 1 yes The number of concurrent threads
TIMEOUT 5 yes The number of seconds to wait for new data
msf auxiliary(scanner/discovery/arp_sweep) > set RHOSTS 10.10.10.0/24RHOSTS => 10.10.10.0/24
msf auxiliary(scanner/discovery/arp_sweep) > set THREADS 50
THREADS => 50
msf auxiliary(scanner/discovery/arp_sweep) > run
2.2使用Nmap进行主机探测
示例代码如下
msf > nmap -PU -sn 10.10.10.0/24


2.3操作系统辨识
示例代码如下
nmap -O -sV 10.10.10.254
-O对目标操作系统识别
-sV 对其服务的版本进行辨识
2.4Metasploit中的端口扫描器
search portscan命令列出metasploit中的端口扫描器

示例代码如下
msf auxiliary(scanner/discovery/arp_sweep) > use auxiliary/scanner/portscan/syn
msf auxiliary(scanner/portscan/syn) > set RHOSTS 10.10.10.254
RHOSTS => 10.10.10.254
msf auxiliary(scanner/portscan/syn) > set THREADS 20
THREADS => 20
msf auxiliary(scanner/portscan/syn) > run
2.5Nmap的端口扫描功能
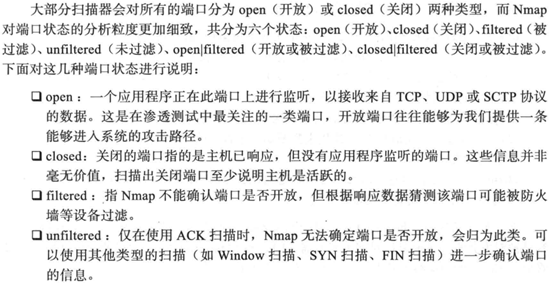


3.服务扫描与查点

在MSF终端,输入search name:_version命令查看所有可用的服务查点模块
3.1Telnet服务扫描

示例代码如下
msf auxiliary(scanner/portscan/syn) > use auxiliary/scanner/telnet/telnet_version
msf auxiliary(scanner/telnet/telnet_version) > set RHOSTS 10.10.10.0/24
RHOSTS => 10.10.10.0/24
msf auxiliary(scanner/telnet/telnet_version) > set THREADS 100
THREADS => 100
msf auxiliary(scanner/telnet/telnet_version) > run
3.2SSH服务扫描
示例代码如下
msf auxiliary(scanner/telnet/telnet_version) > use auxiliary/scanner/ssh/ssh_version
msf auxiliary(scanner/ssh/ssh_version) > set RHOSTS 10.10.10.0/24
RHOSTS => 10.10.10.0/24
msf auxiliary(scanner/ssh/ssh_version) > set THREADS 100
THREADS => 100
msf auxiliary(scanner/ssh/ssh_version) > run
3.3Oracle数据库服务查点
使用tnslsnr_version模块在网络中发现后台服务器上开放的Oracle数据库,并获取其版本号,示例代码如下
msf auxiliary(scanner/ssh/ssh_version) > use auxiliary/scanner/oracle/tnslsnr_version
msf auxiliary(scanner/oracle/tnslsnr_version) > set RHOSTS 10.10.10.0/24
RHOSTS => 10.10.10.0/24
msf auxiliary(scanner/oracle/tnslsnr_version) > set THREADS 50
THREADS => 50
msf auxiliary(scanner/oracle/tnslsnr_version) > run
3.4开放代理探测与利用

示例代码如下
msf auxiliary(scanner/oracle/tnslsnr_version) > use auxiliary/scanner/http/open_proxy
msf auxiliary(scanner/http/open_proxy) > set SITE www.google.com
SITE => www.google.com
msf auxiliary(scanner/http/open_proxy) > set RHOSTS 24.25.24.1-24.25.26.254
RHOSTS => 24.25.24.1-24.25.26.254
msf auxiliary(scanner/http/open_proxy) > set MULTIPORTS true
MULTIPORTS => true
msf auxiliary(scanner/http/open_proxy) > set VERIFY_CONNECT true
VERIFY_CONNECT => true
msf auxiliary(scanner/http/open_proxy) > set THREADS 100
THREADS => 100
msf auxiliary(scanner/http/open_proxy) > run
3.5SSH服务口令猜测
示例代码如下
msf auxiliary(scanner/http/open_proxy) > use auxiliary/scanner/ssh/ssh_login
msf auxiliary(scanner/ssh/ssh_login) > set RHOSTS 10.10.10.254
RHOSTS => 10.10.10.254
msf auxiliary(scanner/ssh/ssh_login) > set USERNAME root
USERNAME => root
msf auxiliary(scanner/ssh/ssh_login) > set PASS_FILE /root/words.txt
PASS_FILE => /root/words.txt
msf auxiliary(scanner/ssh/ssh_login) > set THREADS 50
THREADS => 50
msf auxiliary(scanner/ssh/ssh_login) > run
6.psnuffle口令嗅探
psnuffle是metasploit用于口令嗅探的工具,可以使用它截获常见协议的身份认证过程,并将用户名和口令信息记录下来。
示例代码如下
msf auxiliary(scanner/ssh/ssh_login) > use auxiliary/sniffer/psnuffle
msf auxiliary(sniffer/psnuffle) > run
