总结一下学习springboot权限管理的经验
1、创建数据库
5张表
user表:用户表
role表:角色表
permission表:功能表
role_permission:角色功能表(外键关联)
user_role:角色用户表(外键关联)
/*
Navicat MySQL Data Transfer
Source Server : 10.2.10.201111
Source Server Version : 50540
Source Host : 10.2.10.201:3306
Source Database : shiro
Target Server Type : MYSQL
Target Server Version : 50540
File Encoding : 65001
Date: 2019-12-13 16:08:36
*/
SET FOREIGN_KEY_CHECKS=0;
-- ----------------------------
-- Table structure for permission
-- ----------------------------
DROP TABLE IF EXISTS `permission`;
CREATE TABLE `permission` (
`permission_id` int(11) NOT NULL,
`permission` varchar(255) DEFAULT NULL,
`permission_name` varchar(255) DEFAULT NULL,
PRIMARY KEY (`permission_id`)
) ENGINE=InnoDB DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of permission
-- ----------------------------
INSERT INTO `permission` VALUES ('1', 'select', '查看');
INSERT INTO `permission` VALUES ('2', 'update', '更新');
INSERT INTO `permission` VALUES ('3', 'delete', '删除');
INSERT INTO `permission` VALUES ('4', 'save', '新增');
-- ----------------------------
-- Table structure for role
-- ----------------------------
DROP TABLE IF EXISTS `role`;
CREATE TABLE `role` (
`role_id` int(11) NOT NULL,
`role_name` varchar(255) DEFAULT NULL,
PRIMARY KEY (`role_id`)
) ENGINE=InnoDB DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of role
-- ----------------------------
INSERT INTO `role` VALUES ('1', 'svip');
INSERT INTO `role` VALUES ('2', 'vip');
INSERT INTO `role` VALUES ('3', 'p');
-- ----------------------------
-- Table structure for role_permission
-- ----------------------------
DROP TABLE IF EXISTS `role_permission`;
CREATE TABLE `role_permission` (
`role_id` int(11) NOT NULL,
`permission_id` int(11) NOT NULL,
PRIMARY KEY (`role_id`,`permission_id`),
KEY `FKf8yllw1ecvwqy3ehyxawqa1qp` (`permission_id`),
CONSTRAINT `FKa6jx8n8xkesmjmv6jqug6bg68` FOREIGN KEY (`role_id`) REFERENCES `role` (`role_id`),
CONSTRAINT `FKf8yllw1ecvwqy3ehyxawqa1qp` FOREIGN KEY (`permission_id`) REFERENCES `permission` (`permission_id`)
) ENGINE=InnoDB DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of role_permission
-- ----------------------------
INSERT INTO `role_permission` VALUES ('1', '1');
INSERT INTO `role_permission` VALUES ('2', '1');
INSERT INTO `role_permission` VALUES ('3', '1');
INSERT INTO `role_permission` VALUES ('1', '2');
INSERT INTO `role_permission` VALUES ('2', '2');
INSERT INTO `role_permission` VALUES ('1', '3');
INSERT INTO `role_permission` VALUES ('1', '4');
INSERT INTO `role_permission` VALUES ('2', '4');
-- ----------------------------
-- Table structure for user
-- ----------------------------
DROP TABLE IF EXISTS `user`;
CREATE TABLE `user` (
`user_id` int(11) NOT NULL,
`password` varchar(255) DEFAULT NULL,
`username` varchar(255) DEFAULT NULL,
PRIMARY KEY (`user_id`)
) ENGINE=InnoDB DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of user
-- ----------------------------
INSERT INTO `user` VALUES ('1', '123', 'Jack');
INSERT INTO `user` VALUES ('2', '123', 'Rose');
INSERT INTO `user` VALUES ('3', '123', 'Paul');
-- ----------------------------
-- Table structure for user_role
-- ----------------------------
DROP TABLE IF EXISTS `user_role`;
CREATE TABLE `user_role` (
`user_id` int(11) NOT NULL,
`role_id` int(11) NOT NULL,
PRIMARY KEY (`user_id`,`role_id`),
KEY `FKa68196081fvovjhkek5m97n3y` (`role_id`),
CONSTRAINT `FK859n2jvi8ivhui0rl0esws6o` FOREIGN KEY (`user_id`) REFERENCES `user` (`user_id`),
CONSTRAINT `FKa68196081fvovjhkek5m97n3y` FOREIGN KEY (`role_id`) REFERENCES `role` (`role_id`)
) ENGINE=InnoDB DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of user_role
-- ----------------------------
INSERT INTO `user_role` VALUES ('1', '1');
INSERT INTO `user_role` VALUES ('2', '2');
INSERT INTO `user_role` VALUES ('3', '3');
具体项目的目录结构长这个亚子
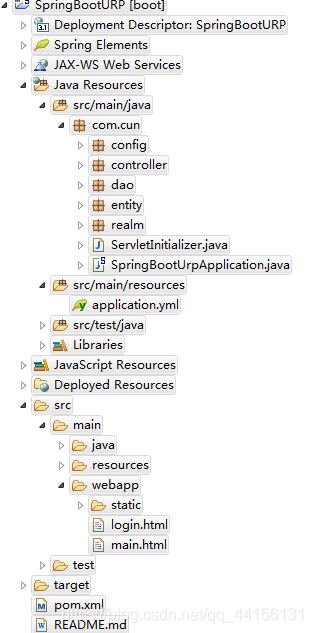 大致的目录结构就是
大致的目录结构就是
config:配置包
controller:控制层
dao:稻城(dao层)
entity:实体类
realm:权限控制层
webapp:简单的页面(layui)
config
CorsConfig(实现跨域访问的配置文件)
package com.cun.config;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.web.cors.CorsConfiguration;
import org.springframework.web.cors.UrlBasedCorsConfigurationSource;
import org.springframework.web.filter.CorsFilter;
/**
* 实现基本的跨域请求
* @author linhongcun
*
*/
@Configuration
public class CorsConfig {
private CorsConfiguration buildConfig() {
CorsConfiguration corsConfiguration = new CorsConfiguration();
corsConfiguration.addAllowedOrigin("*"); // 允许任何域名使用
corsConfiguration.addAllowedHeader("*"); // 允许任何头
corsConfiguration.addAllowedMethod("*"); // 允许任何方法(post、get等)
return corsConfiguration;
}
@Bean
public CorsFilter corsFilter() {
UrlBasedCorsConfigurationSource source = new UrlBasedCorsConfigurationSource();
source.registerCorsConfiguration("/**", buildConfig()); // 对接口配置跨域设置
return new CorsFilter(source);
}
}
ShiroConfig
package com.cun.config;
import java.util.LinkedHashMap;
import java.util.Map;
import org.apache.shiro.spring.LifecycleBeanPostProcessor;
import org.apache.shiro.spring.security.interceptor.AuthorizationAttributeSourceAdvisor;
import org.apache.shiro.spring.web.ShiroFilterFactoryBean;
import org.apache.shiro.web.mgt.DefaultWebSecurityManager;
import org.springframework.aop.framework.autoproxy.DefaultAdvisorAutoProxyCreator;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.context.annotation.DependsOn;
import org.apache.shiro.mgt.SecurityManager;
import com.cun.realm.MyRealm;
/**
* Shiro配置类
* @author linhongcun
*
*/
@Configuration
public class ShiroConfig {
/**
* ShiroFilterFactoryBean 处理拦截资源文件问题。
* 注意:单独一个ShiroFilterFactoryBean配置是或报错的,以为在
* 初始化ShiroFilterFactoryBean的时候需要注入:SecurityManager
*
* Filter Chain定义说明 1、一个URL可以配置多个Filter,使用逗号分隔 2、当设置多个过滤器时,全部验证通过,才视为通过
* 3、部分过滤器可指定参数,如perms,roles
*
*/
@Bean
public ShiroFilterFactoryBean shirFilter(SecurityManager securityManager) {
ShiroFilterFactoryBean shiroFilterFactoryBean = new ShiroFilterFactoryBean();
// 必须设置 SecurityManager
shiroFilterFactoryBean.setSecurityManager(securityManager);
// 如果不设置默认会自动寻找Web工程根目录下的"/login.jsp"页面
shiroFilterFactoryBean.setLoginUrl("/login.html");
// 拦截器.
Map<String, String> filterChainDefinitionMap = new LinkedHashMap<String, String>();
// 配置不会被拦截的链接 顺序判断
filterChainDefinitionMap.put("/static/**", "anon");
filterChainDefinitionMap.put("/user/login", "anon");
//测试权限用
filterChainDefinitionMap.put("/swagger-ui.html", "anon");
// 配置退出过滤器,其中的具体的退出代码Shiro已经替我们实现了
filterChainDefinitionMap.put("/logout", "logout");
// 过滤链定义,从上向下顺序执行,一般将 /**放在最为下边 :这是一个坑呢,一不小心代码就不好使了;
// ① authc:所有url都必须认证通过才可以访问; ② anon:所有url都都可以匿名访问
filterChainDefinitionMap.put("/**", "authc");
shiroFilterFactoryBean.setFilterChainDefinitionMap(filterChainDefinitionMap);
return shiroFilterFactoryBean;
}
@Bean
public SecurityManager securityManager() {
DefaultWebSecurityManager securityManager = new DefaultWebSecurityManager();
// 设置realm.
securityManager.setRealm(myRealm());
return securityManager;
}
/**
* 身份认证realm; (这个需要自己写,账号密码校验;权限等)
*
* @return
*/
@Bean
public MyRealm myRealm() {
MyRealm myRealm = new MyRealm();
return myRealm;
}
/**
* Shiro生命周期处理器
* @return
*/
@Bean
public LifecycleBeanPostProcessor lifecycleBeanPostProcessor() {
return new LifecycleBeanPostProcessor();
}
/**
* 开启Shiro的注解(如@RequiresRoles,@RequiresPermissions),需借助SpringAOP扫描使用Shiro注解的类,并在必要时进行安全逻辑验证
* 配置以下两个bean(DefaultAdvisorAutoProxyCreator(可选)和AuthorizationAttributeSourceAdvisor)即可实现此功能
* @return
*/
@Bean
@DependsOn({ "lifecycleBeanPostProcessor" })
public DefaultAdvisorAutoProxyCreator advisorAutoProxyCreator() {
DefaultAdvisorAutoProxyCreator advisorAutoProxyCreator = new DefaultAdvisorAutoProxyCreator();
advisorAutoProxyCreator.setProxyTargetClass(true);
return advisorAutoProxyCreator;
}
@Bean
public AuthorizationAttributeSourceAdvisor authorizationAttributeSourceAdvisor() {
AuthorizationAttributeSourceAdvisor authorizationAttributeSourceAdvisor = new AuthorizationAttributeSourceAdvisor();
authorizationAttributeSourceAdvisor.setSecurityManager(securityManager());
return authorizationAttributeSourceAdvisor;
}
}
说实话,这里的配置具体过程,为啥要这么配置,配置原理这些我是没有整明白
entity
Permission
package com.cun.entity;
import javax.persistence.Column;
import javax.persistence.Entity;
import javax.persistence.GeneratedValue;
import javax.persistence.Id;
import javax.persistence.Table;
@Entity
@Table(name = "t_permission")
public class Permission {
@Id
@GeneratedValue
private Integer id; // 编号
@Column(length = 50)
private String permissionName; // 菜单名称
@Column(length = 1000)
private String remarks; // 备注
public String getRemarks() {
return remarks;
}
public void setRemarks(String remarks) {
this.remarks = remarks;
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public String getPermissionName() {
return permissionName;
}
public void setPermissionName(String permissionName) {
this.permissionName = permissionName;
}
public Permission() {
super();
}
@Override
public String toString() {
return "Permission [id=" + id + ", permissionName=" + permissionName + ", remarks=" + remarks + "]";
}
}
Role
package com.cun.entity;
import javax.persistence.Column;
import javax.persistence.Entity;
import javax.persistence.GeneratedValue;
import javax.persistence.Id;
import javax.persistence.Table;
@Entity
@Table(name = "t_role")
public class Role {
@Id
@GeneratedValue
private Integer id; // 编号
@Column(length = 100)
private String roleName; // 角色名称
@Column(length = 1000)
private String remarks; // 备注
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public String getRoleName() {
return roleName;
}
public void setRoleName(String roleName) {
this.roleName = roleName;
}
public String getRemarks() {
return remarks;
}
public void setRemarks(String remarks) {
this.remarks = remarks;
}
public Role() {
super();
}
@Override
public String toString() {
return "Role [id=" + id + ", roleName=" + roleName + ", remarks=" + remarks + "]";
}
}
RolePermission
package com.cun.entity;
import javax.persistence.Column;
import javax.persistence.Entity;
import javax.persistence.GeneratedValue;
import javax.persistence.Id;
import javax.persistence.JoinColumn;
import javax.persistence.ManyToOne;
import javax.persistence.Table;
@Entity
@Table(name = "t_role_permission")
public class RolePermission {
@Id
@GeneratedValue
private Integer id; // 编号
@ManyToOne
@JoinColumn(name = "role_id")
private Role role; // 角色
@ManyToOne
@JoinColumn(name = "permission_id")
private Permission menu; // 菜单
@Column(length = 1000)
private String remarks; // 备注
public String getRemarks() {
return remarks;
}
public void setRemarks(String remarks) {
this.remarks = remarks;
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public Role getRole() {
return role;
}
public void setRole(Role role) {
this.role = role;
}
public Permission getMenu() {
return menu;
}
public void setMenu(Permission menu) {
this.menu = menu;
}
public RolePermission() {
super();
}
@Override
public String toString() {
return "RolePermission [id=" + id + ", role=" + role + ", menu=" + menu + ", remarks=" + remarks + "]";
}
}
User
package com.cun.entity;
import javax.persistence.Column;
import javax.persistence.Entity;
import javax.persistence.GeneratedValue;
import javax.persistence.Id;
import javax.persistence.Table;
import org.hibernate.validator.constraints.NotEmpty;
@Entity
@Table(name = "t_user")
public class User {
@Id
@GeneratedValue
private Integer id;
@Column(length = 100)
@NotEmpty(message = "用户名不能为空")
private String userName; //用户名
@Column(length = 100)
@NotEmpty(message = "密码不能为空")
private String password; //密码
@Column(length = 1000)
private String remarks; // 备注
public String getRemarks() {
return remarks;
}
public void setRemarks(String remarks) {
this.remarks = remarks;
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public String getUserName() {
return userName;
}
public void setUserName(String userName) {
this.userName = userName;
}
public String getPassword() {
return password;
}
public void setPassword(String password) {
this.password = password;
}
public User() {
super();
}
@Override
public String toString() {
return "User [id=" + id + ", userName=" + userName + ", password=" + password + ", remarks=" + remarks + "]";
}
}
UserRole
package com.cun.entity;
import javax.persistence.Column;
import javax.persistence.Entity;
import javax.persistence.GeneratedValue;
import javax.persistence.Id;
import javax.persistence.JoinColumn;
import javax.persistence.ManyToOne;
import javax.persistence.Table;
@Entity
@Table(name = "t_user_role")
public class UserRole {
@Id
@GeneratedValue
private Integer id; // 编号
@ManyToOne
@JoinColumn(name = "user_id")
private User user; // 用户
@ManyToOne
@JoinColumn(name = "role_id")
private Role role; // 角色
@Column(length = 1000)
private String remarks; // 备注
public String getRemarks() {
return remarks;
}
public void setRemarks(String remarks) {
this.remarks = remarks;
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public User getUser() {
return user;
}
public void setUser(User user) {
this.user = user;
}
public Role getRole() {
return role;
}
public void setRole(Role role) {
this.role = role;
}
public UserRole() {
super();
}
@Override
public String toString() {
return "UserRole [id=" + id + ", user=" + user + ", role=" + role + ", remarks=" + remarks + "]";
}
}
这个俺是整的明明白白
 dao层
dao层
PermissionDao

package com.cun.dao;
import java.util.List;
import org.springframework.data.jpa.repository.JpaRepository;
import org.springframework.data.jpa.repository.Query;
import com.cun.entity.Permission;
public interface PermissionDao extends JpaRepository<Permission, Integer>{
/**
* 通过用户名来获取到权限功能名称
* @param userName
* @return
*/
@Query(nativeQuery=true,value="select p.* from t_user u,t_user_role ur,t_role_permission rp,t_permission p where u.id=ur.user_id and ur.role_id=rp.role_id and rp.permission_id=p.id and u.user_name=?1")
List<Permission> getPermissionsByUserName(String userName);
}
RoleDao
package com.cun.dao;
import java.util.List;
import org.springframework.data.jpa.repository.JpaRepository;
import org.springframework.data.jpa.repository.Query;
import com.cun.entity.Role;
public interface RoleDao extends JpaRepository<Role, Integer>{
/**
* 通过用户名来获取到角色名
* @param userName
* @return
*/
@Query(value="select r.* from t_user u,t_user_role ur,t_role r where u.id=ur.role_id and ur.role_id=r.id and u.user_name=?1",nativeQuery=true)
List<Role> getRolesByUserName(String userName);
}
RolePermissionDao
package com.cun.dao;
import org.springframework.data.jpa.repository.JpaRepository;
import com.cun.entity.RolePermission;
public interface RolePermissionDao extends JpaRepository<RolePermission, Integer>{
}
UserDao
package com.cun.dao;
import org.springframework.data.jpa.repository.JpaRepository;
import org.springframework.data.jpa.repository.Query;
import com.cun.entity.User;
public interface UserDao extends JpaRepository<User, Integer>{
/**
* 登录的时候,根据用户名获取用户实体
* @param userName
* @return
*/
@Query(value="select * from t_user where user_name=?1",nativeQuery=true)
public User getUserByUserName(String userName);
}
UserRoleDao
package com.cun.dao;
import org.springframework.data.jpa.repository.JpaRepository;
import com.cun.entity.UserRole;
public interface UserRoleDao extends JpaRepository<UserRole, Integer>{
}
这里发现这5个dao层都继承了JpaRepository
JpaRepository是实现Spring Data JPA技术访问数据库的关键接口
(啥玩意????黑人问号)
应该是hibernate框架里边的东西,本菜鸟还未接触
还有注解@Query
实现自定义查询
我们在dao层接口按照规则来定义方法就可以不用写方法的实现也能操作数据库。但是如果一个条件查询有多个条件时,写出来的方法名字就太长了,所以我们就想着不按规则来定义方法名。我们可以使用@Query这个注解来实现这个功能,在定义的方法上加上@Query这个注解,将查询语句声明在注解中,也可以查询到数据库的数据。
(语法我是没整明白)
个人感觉还是mybtis好用,大佬用的这个方法真的是没有看明白,数据到底是怎么来的?

realm
package com.cun.realm;
import java.util.HashSet;
import java.util.List;
import java.util.Set;
import org.apache.shiro.SecurityUtils;
import org.apache.shiro.authc.AuthenticationException;
import org.apache.shiro.authc.AuthenticationInfo;
import org.apache.shiro.authc.AuthenticationToken;
import org.apache.shiro.authc.SimpleAuthenticationInfo;
import org.apache.shiro.authz.AuthorizationInfo;
import org.apache.shiro.authz.SimpleAuthorizationInfo;
import org.apache.shiro.realm.AuthorizingRealm;
import org.apache.shiro.subject.PrincipalCollection;
import org.springframework.beans.factory.annotation.Autowired;
import com.cun.dao.PermissionDao;
import com.cun.dao.RoleDao;
import com.cun.dao.UserDao;
import com.cun.entity.Permission;
import com.cun.entity.Role;
import com.cun.entity.User;
public class MyRealm extends AuthorizingRealm {
@Autowired
private UserDao userDao;
@Autowired
private RoleDao roleDao;
@Autowired
private PermissionDao permissionDao;
/**
* 授权
*/
@Override
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) {
String userName=(String) SecurityUtils.getSubject().getPrincipal();
System.out.println("获取到的用户名"+userName);
SimpleAuthorizationInfo info=new SimpleAuthorizationInfo();
System.out.println("获取到的信息"+info.toString());
//新建一个角色
Set<String> roles=new HashSet<String>();
//获取到所有角色
List<Role> rolesByUserName = roleDao.getRolesByUserName(userName);
for(Role role:rolesByUserName) {
roles.add(role.getRoleName());
System.out.println("获取到的角色"+role.getRoleName());
}
//通过用户名查询到权限功能
List<Permission> permissionsByUserName = permissionDao.getPermissionsByUserName(userName);
for(Permission permission:permissionsByUserName) {
info.addStringPermission(permission.getPermissionName());
System.out.println("权限功能有"+permission.getPermissionName());
}
info.setRoles(roles);
System.out.println("看一下返回的是什么信息"+info.toString());
return info;
}
/**
* 认证
*/
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException {
System.out.println("token.getPrincipal:" + token.getPrincipal());
System.out.println("token.getCredentials:" + token.getCredentials());
String userName = token.getPrincipal().toString();
User user = userDao.getUserByUserName(userName);
if (user != null) {
// Object principal, Object credentials, String realmName
AuthenticationInfo authcInfo = new SimpleAuthenticationInfo(user.getUserName(), user.getPassword(), getName());
return authcInfo;
} else {
return null;
}
}
}
这个是核心功能,返回的是一个AuthorizationInfo
AuthorizationInfo 用于聚合授权信息的:
当我们使用AuthorizingRealm 时,如果身份验证成功,在进行授权时就通过doGetAuthorizationInfo方法获取角色/权限信息用于授权验证。
会用就完事了嗷(原理是啥我很懵逼)
认证的话时采用的token
User user = userDao.getUserByUserName(userName);
这段代码获取到该用户的账号,密码,姓名
然后一股脑儿添加到这个AuthenticationInfo里边
AuthenticationInfo authcInfo = new SimpleAuthenticationInfo(user.getUserName(), user.getPassword(), getName());
然后将信息返回(这就是token?)

ServletInitializer(容器bean)
package com.cun;
import org.springframework.boot.builder.SpringApplicationBuilder;
import org.springframework.boot.web.support.SpringBootServletInitializer;
public class ServletInitializer extends SpringBootServletInitializer {
@Override
protected SpringApplicationBuilder configure(SpringApplicationBuilder application) {
return application.sources(SpringBootUrpApplication.class);
}
}
SpringBootUrpApplication(开关)
package com.cun;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
@SpringBootApplication
public class SpringBootUrpApplication {
public static void main(String[] args) {
SpringApplication.run(SpringBootUrpApplication.class, args);
}
}
前端静态页面使用layui做的(。。。。。当初就不该学jsp o(╥﹏╥)o)
login.html
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<title>登录页面</title>
<link rel="stylesheet" href="static/layui/css/layui.css" />
<script type="text/javascript" src="static/js/jquery-1.7.2.js"></script>
<style type="text/css">
</style>
</head>
<body>
<br />
<div class="layui-form-item">
<label class="layui-form-label">用户名:</label>
<div class="layui-input-block">
<!-- 1、参数必须被命名为 userName,不能为 username,保持和实体中的属性一致 -->
<input type="text" id="userName" name="userName" placeholder="userName" class="layui-input" autocomplete="off"><br/>
</div>
<label class="layui-form-label">密码:</label>
<div class="layui-input-block">
<!-- 2、同理密码参数必须被命名为 password -->
<input type="password" id="password" name="password" placeholder="password" class="layui-input"><br/>
</div>
</div>
<div class="layui-form-item">
<div class="layui-input-block">
<input type="submit" id="loginBtn" value="登录" class="layui-btn"></input>
</div>
</div>
</body>
<script type="text/javascript">
$("#loginBtn").click(function() {
$.post("http://localhost/user/login", {
userName: $("#userName").val(),
password: $("#password").val(),
}, function(result) {
if(result.success) {
window.location.href = "main.html";
//必须加上,否则跳转不了
return false;
} else {
alert(result.errorInfo);
}
});
});
</script>
</html>
mian.html
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<title>主页</title>
<link rel="stylesheet" href="static/layui/css/layui.css" />
<script type="text/javascript" src="static/js/jquery-1.7.2.js"></script>
<style type="text/css">
body {
margin: 50px;
}
</style>
</head>
<body>
<button id="selectBtn" class="layui-btn layui-btn-sm layui-btn-radius layui-bg-cyan">
<i class="layui-icon"></i>select
</button>
<button id="insertBtn" class="layui-btn layui-btn-normal layui-btn-sm layui-btn-radius">
<i class="layui-icon"></i>insert
</button>
<button id="updateBtn" class="layui-btn layui-btn-warm layui-btn-sm layui-btn-radius">
<i class="layui-icon"></i>update
</button>
<button id="deleteBtn" class="layui-btn layui-btn-danger layui-btn-sm layui-btn-radius">
<i class="layui-icon"></i>delete
</button>
<hr />
<button id="vipBtn" class="layui-btn layui-btn-lg">
vip
</button>
<button id="ipBtn" class="layui-btn layui-btn-lg">
ip
</button>
<button id="pBtn" class="layui-btn layui-btn-lg">
p
</button>
<hr/>
<a class="layui-btn layui-btn-sm layui-btn-primary" href="logout">注销</a>
</body>
<script type="text/javascript">
$("#selectBtn").click(function() {
$.post("http://localhost/user/select", {}, function(result) {
if(result.success) {
alert(result.msg);
return false;
} else {
alert(result.errorInfo);
return false;
}
});
});
$("#insertBtn").click(function() {
$.post("http://localhost/user/insert", {}, function(result) {
if(result.success) {
alert(result.msg);
return false;
} else {
alert(result.errorInfo);
return false;
}
});
});
$("#updateBtn").click(function() {
$.post("http://localhost/user/update", {}, function(result) {
if(result.success) {
alert(result.msg);
return false;
} else {
alert(result.errorInfo);
return false;
}
});
});
$("#deleteBtn").click(function() {
$.post("http://localhost/user/delete", {}, function(result) {
if(result.success) {
alert(result.msg);
return false;
} else {
alert(result.errorInfo);
return false;
}
});
});
$("#vipBtn").click(function() {
$.post("http://localhost/user/vip", {}, function(result) {
if(result.success) {
alert(result.msg);
return false;
} else {
alert('无权访问');
return false;
}
});
});
$("#ipBtn").click(function() {
$.post("http://localhost/user/ip", {}, function(result) {
if(result.success) {
alert(result.msg);
return false;
} else {
alert('无权访问');
return false;
}
});
});
$("#pBtn").click(function() {
$.post("http://localhost/user/p", {}, function(result) {
if(result.success) {
alert(result.msg);
return false;
} else {
alert('无权访问');
return false;
}
});
});
</script>
</html>
配置文件:
server:
port: 80 #为了以后访问项目不用写端口号
context-path: / #为了以后访问项目不用写项目名
spring:
datasource:
driver-class-name: com.mysql.jdbc.Driver
url: jdbc:mysql://localhost:3306/urp?useUnicode=true&characterEncoding=utf-8 #解决中文乱码的问题
username: root
password: 123456
jpa:
hibernate:
ddl-auto: update #数据库同步代码
show-sql: true #dao操作时,显示sql语句
pom.xml
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<groupId>com.cun</groupId>
<artifactId>SpringBootURP</artifactId>
<version>0.0.1-SNAPSHOT</version>
<packaging>war</packaging>
<name>SpringBootURP</name>
<description>Demo project for Spring Boot</description>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>1.5.11.RELEASE</version>
<relativePath /> <!-- lookup parent from repository -->
</parent>
<properties>
<project.build.sourceEncoding>UTF-8</project.build.sourceEncoding>
<project.reporting.outputEncoding>UTF-8</project.reporting.outputEncoding>
<java.version>1.8</java.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-data-jpa</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<scope>runtime</scope>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-tomcat</artifactId>
<scope>provided</scope>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
<!-- SpringBoot中使用 Shiro 做用户、角色、权限管理 -->
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-core</artifactId>
<version>1.4.0</version>
</dependency>
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-spring</artifactId>
<version>1.4.0</version>
</dependency>
<!-- swagger生成接口API -->
<dependency>
<groupId>io.springfox</groupId>
<artifactId>springfox-swagger2</artifactId>
<version>2.7.0</version>
</dependency>
<!-- 接口API生成html文档 -->
<dependency>
<groupId>io.springfox</groupId>
<artifactId>springfox-swagger-ui</artifactId>
<version>2.6.1</version>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>
搭建完毕!!!!

效果
访问地址:http://localhost/login.html
 登录之后
登录之后
 这是一个vip用户,所有的权限他都有
这是一个vip用户,所有的权限他都有

如果是非vip用户只会有部分权限
后台:
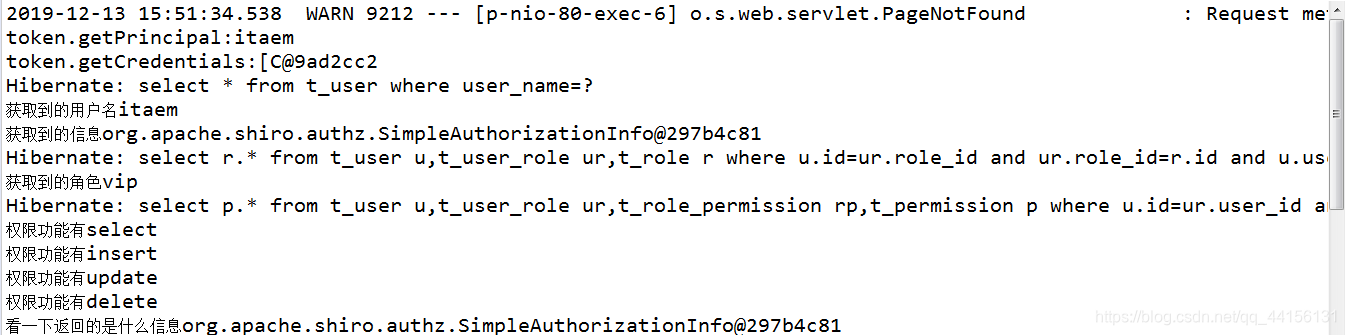 因为不懂数据是怎么来的,总感觉心里没底,需要学的还有好多
因为不懂数据是怎么来的,总感觉心里没底,需要学的还有好多
明天双休,周末愉快

大佬原博客(有源码)原文地址
