link設定 OpenvSwitch by roan,内容相对比较全面,但是给出的网页链接废了好多
流表中数字越大,优先级越高
各个组件的命令有什么子命令和功能,直接--help
e.g. ovs-ofctl --help
关于显示
ovs-vsctl list bridge br0

关于port
更改 ofport (openflow port number)为100:
ovs-vsctl set Interface eth0 ofport_request=100
设置 port 为 internal
ovs-vsctl set Interface eth0 type=internal
关于controller
设置 Controller
ovs-vsctl set-controller br0 tcp:1.2.3.4:6633
设置 multi controller
ovs-vsctl set-controller br0 tcp:1.2.3.4:6633 tcp:5.6.7.8:6633
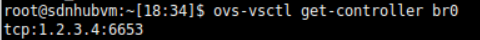
查询 Controller
ovs-vsctl get-controller br0
关于OpenFlow version
支持OpenFlow 协议1.3 1.2
root@sdnhubvm:~[18:35]$ ovs-vsctl set bridge br0 protocols=OpenFlow12,OpenFlow13
root@sdnhubvm:~[18:46]$ ovs-vsctl clear bridge br0 protocols
没有什么明确的东西出来
关于VLAN
一到ofctl的复杂指令我就看不懂
关于Dump flows
怎么我又没有关terminal为什么今天我的流表又没了???
Dumps OpenFlow flows 不含 hidden flows (常用
root@sdnhubvm:~[18:52]$ ovs-ofctl dump-flows br0
NXST_FLOW reply (xid=0x4):
Dumps OpenFlow flows 包含 hidden flows
这些出来的都是hidden flows,但是我昨天那些table 0, 1, 2, 3, 4, 10的设置咋都没了orz
root@sdnhubvm:~[18:53]$ ovs-appctl bridge/dump-flows br0
table_id=254, duration=53967s, n_packets=0, n_bytes=0, priority=2,recirc_id=0,actions=drop
table_id=254, duration=53967s, n_packets=0, n_bytes=0, priority=1,actions=resubmit(,0)
table_id=254, duration=53967s, n_packets=0, n_bytes=0, priority=0,reg0=0x1,actions=controller(reason=no_match)
table_id=254, duration=53967s, n_packets=0, n_bytes=0, priority=0,reg0=0x2,actions=drop
table_id=254, duration=53967s, n_packets=0, n_bytes=0, priority=0,reg0=0x3,actions=drop
Dump 特定 bridge 的 datapath flows 不論任何 type
???什么反应都没有
root@sdnhubvm:~[18:54]$ ovs-appctl dpif/dump-flows br0
Dump 在 Linux kernel 裡的 datapath flow table (常用)
root@sdnhubvm:~[18:57]$ ovs-dpctl dump-flows
flow-dump from pmd on cpu core: 32767
recirc_id(0),in_port(8),eth(src=52:54:00:12:35:02,dst=08:00:27:30:49:74),eth_type(0x0806), packets:2, bytes:120, used:6.165s, actions:9
Top like behavior for ovs-dpctl dump-flows
ovs-dpctl-top
???

关于feedback
Controller connection: false 的時候, 會自動調成 legacy switch mode
ovs-vsctl set-fail-mode ovs-br standalone
無論 Controller connection status 為何, 都必須通過 OpenFlow 來進行網路行為 (default)
ovs-vsctl set-fail-mode ovs-br secure
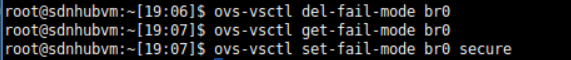
移除
ovs-vsctl del-fail-mode ovs-br
查询
root@sdnhubvm:~[19:05]$ ovs-vsctl get-fail-mode br0
secure
被删了之后就什么都不反馈
关于sFlow
sFlow,名称来自流量采样(英语:sampled flow)的缩写,是一种工业规格,用来测量OSI模型第二层封包。这个规格提供了一个方法,以取样的方式,获得网络封包的资讯,让网络管理人员可以了解网络的运作状况,了解网络壅塞的原因。
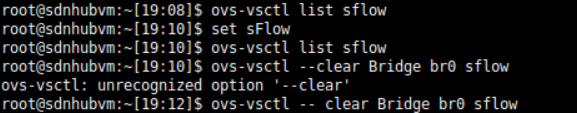
查詢
ovs-vsctl list sflow
新增
Set sFlow
刪除
ovs-vsctl -- clear Bridge ovs-br sflow
真实毫无反应,到底是干啥的
NetFlow是一种网络监测功能,可以收集进入及离开网络界面的IP封包的数量及资讯,最早由思科公司研发,应用在路由器及交换器等产品上。经由分析Netflow收集到的资讯,网络管理人员可以知道封包的来源及目的地,网络服务的种类,以及造成网络壅塞的原因
sampled flow aka(also known as) sFlow
hough sFlow stands for Sampled Flow, actual packets are being sampled here instead of flows. Sampling involves either copying headers of packets, or extracting features from packet. The goal of packet sampling and filtering is to forward only certain packets. Based on a defined sampling rate, an average of 1 out of n packets is randomly sampled. sFlow agent running within a router or a switch, packages interface counters and flow samples into sFlow datagrams. The datagrams are continuously sent using UDP to the sFlow Collector where they are further analyzed.
NetFlow versus sFlow
SFlow has an ability to monitor L2-L7 headers, the ability to monitor L2 headers (MAC, VLAN ID) has been added to NetFlow v9.
Packet sampling is hardware based and is performed by switching ASICs, achieving wire speed performance. It makes sFlow a scalable technology which is able to monitor the links with the speed of up to 10 GBps.
BGP in Large Networks eBook
sFlow datagrams are continuously sent across the network in real-time, while the export of NetFlow records depends on active/inactive timers. It may take up to 30 minutes to export flow when NetFlow is used. Obviously, sFlow is better in traffic visibility than NetFlow. It makes sFlow good at massive DoS attacks detection, as the sampled network patterns are sent on the fly to the sFlow collector.
Nevertheless, measurements provided by sFlow are only an approximation of the real traffic because sampled packets do not reflect all network traffic. As a result, sFlow lacks accuracy provided by NetFlow as it cannot track every network communication. The accuracy, however is highly required in digital forensics so sFlow cannot fully qualify for forensic investigation.
In-band and out-band
所谓connection mode
linkin-band和out-band的区别
在计算机网络领域,常常会遇见in-band和out-band两种不同的网络架构,它们的概念和区别是什么?
In-band:频内,指那些数据控制已经被固定的网络协议,In-band 控制的控制数据通常和主要的传输数据公用用同样的连接链路(以太网通道),属于应用层管理。被管理设备只有处于开机状态并进入作业系统的情况下,才能进行管理。像SNMP(Simple Network Management Protocol)都是属于In-band协议。SNMP使用方便,但是存在一个固有的缺陷:SNMP 管理信息总是和网络数据使用同样的网络路径。它使用相同的WAN和LAN路由、中继器和连接链路。当网络中断或是严重受损的时候,SNMP流量就不能在向量的管理设备或是工作站中流通。当网络组件中断时,In-band失去网络连接,不能使用。
Out-band:频外,又被称为熄灯(Lights out Mangement,LOM)管理,弥补了In-band的缺点,是指那些数据传输信道独立于正常的网络传输,被管理设备即使在关机状态甚至故障的状态下,都可以进行修复重开机或是日志监控等管理作业。这对于分离两种不同类型的数据是十分有用的。Out of band 管理指那些通过拨号电话线允许技术人员连接到网络组件(防火墙、路由器、网桥、交换机、服务器等)。在电话系统中,当用于建立语音通信的设备分离时,就使用Out of band通信建立语音通信。
In-band管理相对于Out-band管理更廉价,但是在计算机网络中它不能够接触固件(BIOS和URFI),也不能够远程重新安装操作系统,不能修复系统booting的问题。在网络中,不允许独立于当前网络组件的网络组件进行远程管理。
查詢
ovs-vsctl get controller ovs-br connection-mode
Out-of-band
ovs-vsctl set controller ovs-br connection-mode=out-of-band
In-band (default)
ovs-vsctl set controller ovs-br connection-mode=in-band
移除 hidden flow 不知所云,用appctl查看后也没有移除掉啊
ovs-vsctl set bridge br0 other-config:disable-in-band=true
root@sdnhubvm:~[19:32]$ ovs-vsctl set-controller br0 tcp:1.2.3.4:6633
root@sdnhubvm:~[19:32]$ ovs-vsctl get controller br0 connection-mode
[]
root@sdnhubvm:~[19:32]$ ovs-vsctl set controller br0 connection-mode=out-of-band
root@sdnhubvm:~[19:33]$ ovs-vsctl get controller br0 connection-mode
out-of-band
事实证明in-band不是默认的,默认是么得
其他
查询OpenvSwitch版本
root@sdnhubvm:~[19:35]$ ovs-ofctl -V
ovs-ofctl (Open vSwitch) 2.3.90
Compiled Jan 8 2015 11:52:49
OpenFlow versions 0x1:0x4
查詢下過的指令歷史記錄
ovsdb-tool show-log [-mmm]
以下部分参考link 作为知识补充
- ovs-vswtiched:openvswitch的守护进程.
- ovsdb-server:openvswitch的数据库服务,保存相关配置信息,非常轻量级
- kernel Datapath:Datapath是流的一个缓存,会把流的match结果cache起来,避免下一次流继续到用户空间进行flow match
- controller:这个不是ovs自身的部件,而是一个抽象的概念,指的是ovs的控制者
这个缓存应该和流表没啥关系叭。。
基本概念

Port
端口是收发数据包的单元。OpenvSwitch中,每个端口都属于一个特定的网桥。端口收到的数据包会经过流规则的处理,发往其他端口;也会把其他端口来的数据包发送出去.主要有
| 类型 | 说明 |
|---|---|
| Normal | 用户可以把操作系统中的网卡绑定到ovs上,ovs会生成一个普通端口处理这块网卡进出的数据包。 |
| Internal | 端口类型为internal时,ovs会创建一块虚拟网卡,端口收到的所有数据包都会交给该网卡,发出的包会通过该端口交给ovs。当ovs创建一个新网桥时,默认会创建一个与网桥同名的Internal Port |
| Patch | 当机器中有多个ovs网桥时,可以使用Patch Port把两个网桥连起来。Patch Port总是成对出现,分别连接在两个网桥上,在两个网桥之间交换数据。 |
| Tunnel | 隧道端口是一种虚拟端口,支持使用gre或vxlan等隧道技术与位于网络上其他位置的远程端口通讯。 |
Interface
接口是ovs与外部交换数据包的组件。一个接口就是操作系统的一块网卡,这块网卡可能是ovs生成的虚拟网卡,也可能是物理网卡挂载在ovs上,也可能是操作系统的虚拟网卡(TUN/TAP)挂载在ovs上。
FlowTable
流定义了端口之间数据包的交换规则.
相关命令快速指南
ovs命令行挺复杂的,提供多个命令,每个命令又有多个不同的子命令,刚刚接触会觉得一团糟,但仔细理解ovs架构和基本概念后会发现命令使用起来非常简单.
- ovs对每个组件都会单独提供一个命令行,所以命令行的功能都非常的专一,理解了组件的用途,也就记住了命令行的用途和大概的子命令.
- 命令行的子命令其实就是对数据库的CURD,而数据库表其实就是OVS的核心概念,如Bridge,Ports,FlowTables等.
常用子命令说明
- ovs-dpctl
show -s - ovs-ofctl
show, dump-ports, dump-flows, add-flow, mod-flows, del-flows - ovsdb-tools
show-log -m - ovs-vsctl
show显示数据库内容- 关于桥的操作
add-br, list-br, del-br, br-exists.
- 关于port的操作
list-ports, add-port, del-port, add-bond, port-to-br. - 关于interface的操作
list-ifaces, iface-to-br ovs-vsctl list/set/get/add/remove/clear/destroy table record column [value], 常见的表有bridge,controller,interface,mirror,netflow,open_vswitch,port,qos,queue,ssl,sflow.
- ovs-appctl
list-commands, fdb/show, qos/show
日常操作
查看有哪些桥,桥中有哪些ports,哪些interfaces
root@sdnhubvm:~[19:37]$ ovs-vsctl list-br
br0
mybridge
ovs-switch
root@sdnhubvm:~[20:14]$ ovs-vsctl list-ports br0
p
p1
p2
p3
p4
root@sdnhubvm:~[20:14]$ ovs-vsctl list-ifaces br0
p
p1
p2
p3
p4
查看port,interface属于哪个bridge,xxx-to-br即可.
root@sdnhubvm:~[20:14]$ ovs-vsctl port-to-br p0
ovs-switch
root@sdnhubvm:~[20:16]$ ovs-vsctl iface-to-br o3
ovs-vsctl: no interface named o3
root@sdnhubvm:~[20:16]$ ovs-vsctl iface-to-br p3
br0
查看bridge中的流表
ovs-ofctl dump-flows br-ex
流表规则中往往使用portid来指定相关的port,可以使用show命令来对应port name与port id.
root@sdnhubvm:~[20:17]$ ovs-ofctl show br0
OFPT_FEATURES_REPLY (xid=0x2): dpid:0000267742430b49
n_tables:254, n_buffers:256
capabilities: FLOW_STATS TABLE_STATS PORT_STATS QUEUE_STATS ARP_MATCH_IP
actions: output enqueue set_vlan_vid set_vlan_pcp strip_vlan mod_dl_src mod_dl_dst mod_nw_src mod_nw_dst mod_nw_tos mod_tp_src mod_tp_dst
1(p1): addr:0e:0c:85:5b:92:88
config: PORT_DOWN
state: LINK_DOWN
speed: 0 Mbps now, 0 Mbps max
2(p2): addr:2a:75:16:8c:d4:a1
config: PORT_DOWN
state: LINK_DOWN
speed: 0 Mbps now, 0 Mbps max
3(p3): addr:2e:02:cc:06:46:89
config: PORT_DOWN
state: LINK_DOWN
speed: 0 Mbps now, 0 Mbps max
4(p4): addr:72:e9:09:fd:1f:7f
config: PORT_DOWN
state: LINK_DOWN
speed: 0 Mbps now, 0 Mbps max
LOCAL(br0): addr:26:77:42:43:0b:49
config: PORT_DOWN
state: LINK_DOWN
speed: 0 Mbps now, 0 Mbps max
OFPT_GET_CONFIG_REPLY (xid=0x4): frags=normal miss_send_len=0
查看隐藏的流表规则,很少使用
ovs-appctl bridge/dump-flows br0
查看一些有用的统计信息
查看datapath统计信息.主要关注lost数值.hit表示datapath命中数,missed未命中,lost表示没有传递到用户空间就丢弃了. 主要关注lost值是否上升,如果上升说明存在问题了.该命令可以使用-s选项,会将每个port的统计信息也显示出来.
root@sdnhubvm:~[20:19]$ ovs-dpctl show
system@ovs-system:
lookups: hit:5000 missed:603 lost:0
flows: 1
masks: hit:5012 total:1 hit/pkt:0.89
port 0: ovs-system (internal)
port 1: p2 (internal)
port 2: p3 (internal)
port 3: p4 (internal)
port 4: p1 (internal)
port 5: br0 (internal)
port 6: p0 (internal)
port 7: ovs-switch (internal)
port 8: eth0
port 9: mybridge (internal)
root@sdnhubvm:~[20:29]$ ovs-dpctl show -s
system@ovs-system:
lookups: hit:5012 missed:603 lost:0
flows: 1
masks: hit:5024 total:1 hit/pkt:0.89
port 0: ovs-system (internal)
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 aborted:0 carrier:0
collisions:0
RX bytes:0 TX bytes:0
port 1: p2 (internal)
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 aborted:0 carrier:0
collisions:0
RX bytes:0 TX bytes:0
port 2: p3 (internal)
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 aborted:0 carrier:0
collisions:0
RX bytes:0 TX bytes:0
port 3: p4 (internal)
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 aborted:0 carrier:0
collisions:0
RX bytes:0 TX bytes:0
port 4: p1 (internal)
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 aborted:0 carrier:0
collisions:0
RX bytes:0 TX bytes:0
port 5: br0 (internal)
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 aborted:0 carrier:0
collisions:0
RX bytes:0 TX bytes:0
port 6: p0 (internal)
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 aborted:0 carrier:0
collisions:0
RX bytes:0 TX bytes:0
port 7: ovs-switch (internal)
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 aborted:0 carrier:0
collisions:0
RX bytes:0 TX bytes:0
port 8: eth0
RX packets:5623 errors:0 dropped:0 overruns:0 frame:0
TX packets:5637 errors:0 dropped:0 aborted:0 carrier:0
collisions:0
RX bytes:344945 (336.9 KiB) TX bytes:340214 (332.2 KiB)
port 9: mybridge (internal)
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:5615 aborted:0 carrier:0
collisions:0
RX bytes:0 TX bytes:0
ovs-ofctl dump-ports br [port]也可以查看port的统计信息.这个命令优势是可以指定port.
查看bridge的转发表
root@sdnhubvm:~[20:33]$ ovs-appctl fdb/show br0
port VLAN MAC Age
设置qos
ovs-vsctl set Interface tap0 ingress_policing_rate=100000
ovs-vsctl set Intervace tap ingress_policing_burst=10000
ovs-appctl qos/show <iface>
调试技巧
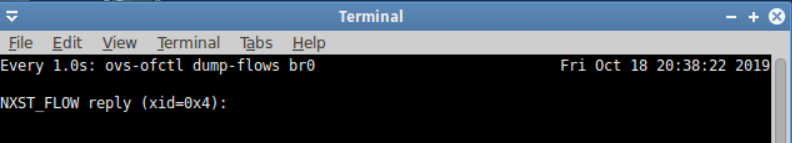
查看流规则的匹配
watch -d -n 1 "ovs-ofctl dump-flows br0"
查看统计信息
ovs-dpctl show -s
ovs-dpctl show
ovs-ofctl dump-ports <br> [port]
使用tcpdump抓包,需要设置端口镜像
以后再试
ip link add name snooper0 type dummy
ip link set dev snooper0 up
ovs-vsctl add-port br-int snooper0
# ovs-vsctl -- set Bridge br-int mirrors=@m -- --id=@snooper0 \
get Port snooper0 -- --id=@patch-tun get Port patch-tun \
-- --id=@m create Mirror name=mymirror select-dst-port=@patch-tun \
select-src-port=@patch-tun output-port=@snooper0 select_all=1
tcpdump -i snooper0
ovs-vsctl clear Bridge br-int mirrors
ovs-vsctl del-port br-int snooper0
ip link delete dev snooper0
查看日志
ovsdb-tool show-log -m
使用ovs-appctl ofproto/trace <bridge> k1=v1,k2=v2测试流匹配
FAQ
Q: Why would I use Open vSwitch instead of the Linux bridge?
A: Open vSwitch is specially designed to make it easier to manage VM network configuration and monitor state spread across many physical hosts in dynamic virtualized environments. Please see WHY-OVS.md for a more detailed description of how Open vSwitch relates to the Linux Bridge.
Q: Why can I no longer connect to my OpenFlow controller or OVSDB manager?
A: Starting in OVS 2.4, we switched the default ports to the IANA-specified port numbers for OpenFlow (6633->6653) and OVSDB (6632->6640). We recommend using these port numbers, but if you cannot, all the programs allow overriding the default port. See the appropriate man page.
Q: I hear OVS has a couple of kinds of flows. Can you tell me about them?
A: Open vSwitch uses different kinds of flows for different purposes:
OpenFlow flows are the most important kind of flow. OpenFlow controllers use these flows to define a switch’s policy. OpenFlow flows support wildcards, priorities, and multiple tables.
When in-band control is in use, Open vSwitch sets up a few “hidden” flows, with priority higher than a controller or the user can configure, that are not visible via OpenFlow. (See the “Controller” section of the FAQ for more information about hidden flows.)
The Open vSwitch software switch implementation uses a second kind of flow internally. These flows, called “datapath” or “kernel” flows, do not support priorities and comprise only a single table, which makes them suitable for caching. (Like OpenFlow flows, datapath flows do support wildcarding, in Open vSwitch 1.11 and later.) OpenFlow flows and datapath flows also support different actions and number ports differently.
Datapath flows are an implementation detail that is subject to change in future versions of Open vSwitch. Even with the current version of Open vSwitch, hardware switch implementations do not necessarily use this architecture.
Users and controllers directly control only the OpenFlow flow table. Open vSwitch manages the datapath flow table itself, so users should not normally be concerned with it.
Q: Why are there so many different ways to dump flows?
A: Open vSwitch has two kinds of flows (see the previous question), so it has commands with different purposes for dumping each kind of flow:
ovs-ofctl dump-flows
dumps OpenFlow flows, excluding hidden flows. This is the most commonly useful form of flow dump. (Unlike the other commands, this should work with any OpenFlow switch, not just Open vSwitch.)
ovs-appctl bridge/dump-flows
dumps OpenFlow flows, including hidden flows. This is occasionally useful for troubleshooting suspected issues with in-band control.
ovs-dpctl dump-flows [dp] dumps the datapath flow table entries for a Linux kernel-based datapath. In Open vSwitch 1.10 and later, ovs-vswitchd merges multiple switches into a single datapath, so it will show all the flows on all your kernel-based switches. This command can occasionally be useful for debugging.
ovs-appctl dpif/dump-flows
, new in Open vSwitch 1.10, dumps datapath flows for only the specified bridge, regardless of the type.