在做之前需要将nginx建好,保证端口打开
一、检查openssl是否安装
[root@localhost ~]# rpm -qa openssl openssl-1.0.2k-16.el7_6.1.x86_64
二、创建根证书CA
1、生成CA私钥
[root@localhost openssl]# openssl genrsa -out local.key 2048 Generating RSA private key, 2048 bit long modulus .............................+++ ..............................................................................+++ e is 65537 (0x10001)
[root@localhost openssl]# ls local.key
2、生成CA证书请求
[root@localhost openssl]# openssl req -new -key local.key -out local.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:China string is too long, it needs to be less than 2 bytes long Country Name (2 letter code) [XX]:CN //国家 State or Province Name (full name) []:beijing //省 Locality Name (eg, city) [Default City]:beijing //城市 Organization Name (eg, company) [Default Company Ltd]: Organizational Unit Name (eg, section) []:test //部门 Common Name (eg, your name or your server's hostname) []:test //主机名 Email Address []:[email protected] //邮箱 Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:tanxiao //密码 An optional company name []:tanxiao //公司名
[root@localhost openssl]# ls local.csr local.key
3、生成CA根证书
这个生成CA证书的命令不容易搞懂 1.通过秘钥 生成证书请求文件 2.通过证书请求文件 生成最终的证书 -in 使用证书请求文件生成证书,-signkey 指定私钥
req:提供生成证书的请求文件,验证证书和创建根CA -new:表示新生成一个证书请求 -x509:直接输出证书 -key:生成证书请求时用到的私钥文件 -out:输出文件
[root@localhost openssl]# openssl x509 -req -in local.csr -extensions v3_ca -signkey local.key -out local.crt Signature ok subject=/C=CN/ST=beijing/L=beijing/O=Default Company Ltd/OU=test/CN=test/[email protected] Getting Private key
三、根据CA根证书创建server根证书
1、生成server私钥
[root@localhost openssl]# openssl genrsa -out my_server.key 2048 Generating RSA private key, 2048 bit long modulus ..+++ ....................................................+++ e is 65537 (0x10001)
2、生成server证书请求
[root@localhost openssl]# openssl req -new -key my_server.key -out my_server.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:beijing Locality Name (eg, city) [Default City]:beijing Organization Name (eg, company) [Default Company Ltd]: Organizational Unit Name (eg, section) []:test Common Name (eg, your name or your server's hostname) []:test Email Address []:[email protected] Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:tanxiao An optional company name []:tanxiao
[root@localhost openssl]# ls local.crt local.csr local.key my_server.csr my_server.key
3、生成server证书
[root@localhost openssl]# openssl x509 -days 365 -req -in my_server.csr -extensions v3_req -CAkey local.key -CA local.crt -CAcreateserial -out my_server.crt Signature ok subject=/C=CN/ST=beijing/L=beijing/O=Default Company Ltd/OU=test/CN=test/[email protected] Getting CA Private Key
四、配置nginx支持SSL(在配置nginx时必须安装ssl模块)
[root@localhost ~]# vim /usr/local/nginx/conf/nginx.conf
server { listen 80; listen 443 default ssl; keepalive_timeout 100; ssl_certificate /root/local.crt; ssl_certificate_key /root/local.key; ssl_session_cache shared:SSL:10m; ssl_session_timeout 10m; ssl_ciphers HIGH:!aNULL:!MD5; ssl_prefer_server_ciphers on; server_name localhost; charset utf-8; }
五、测试
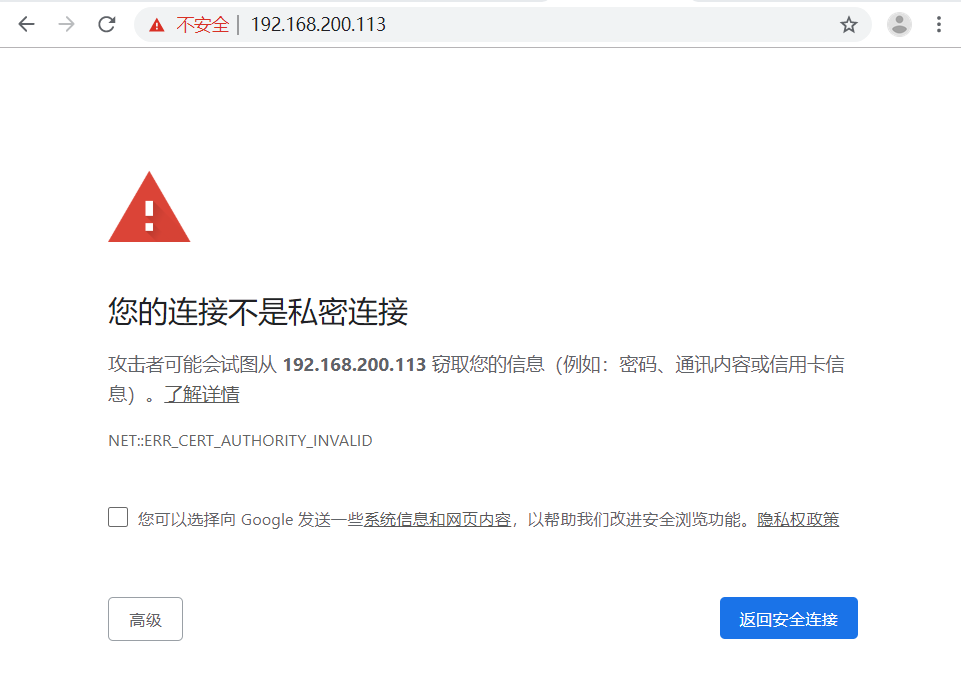
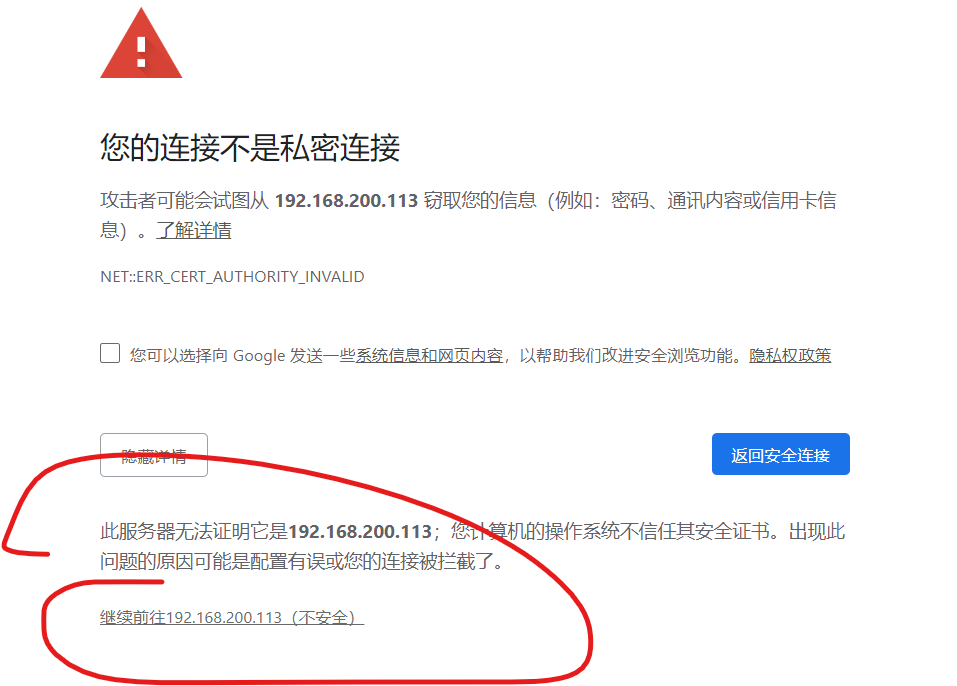
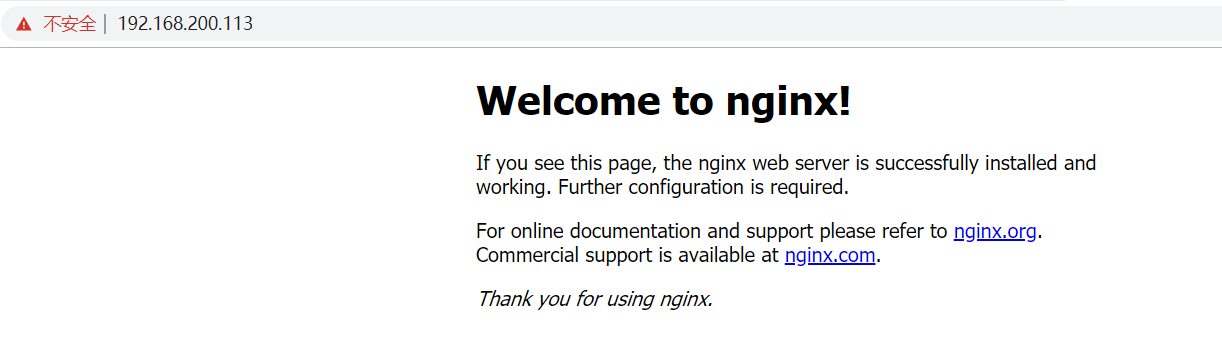
https://www.cnblogs.com/tanxiaojuncom/
