一、链路备份IPSec ××× HA解决方案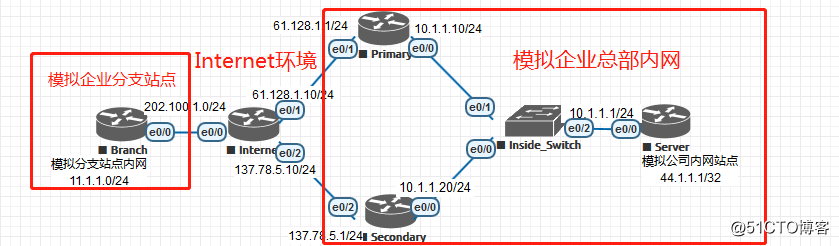
1.相关节点关键配置
Branch节点
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 61.128.1.1
crypto isakmp key cisco address 137.78.5.1
crypto isakmp keepalive 10 periodic
!
crypto ipsec transform-set cisco esp-3des esp-md5-hmac
mode tunnel
!
crypto map cisco 10 ipsec-isakmp
set peer 61.128.1.1
set peer 137.78.5.1
set transform-set cisco
match address
!
interface Ethernet0/0
ip address 202.100.1.1 255.255.255.0
crypto map cisco
!
ip route 0.0.0.0 0.0.0.0 202.100.1.10
!
ip access-list extended
permit ip 11.1.1.0 0.0.0.255 44.1.1.0 0.0.0.255
Primary节点:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 202.100.1.1
crypto isakmp keepalive 10 periodic
!
crypto ipsec transform-set cisco esp-3des esp-md5-hmac
mode tunnel
!
crypto map cisco 10 ipsec-isakmp
set peer 202.100.1.1
set transform-set cisco
set reverse-route tag 100
match address
reverse-route
!
router ospf 110
router-id 33.1.1.1
redistribute static subnets tag 100
network 10.1.1.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 61.128.1.10
!
ip access-list extended
permit ip 44.1.1.0 0.0.0.255 11.1.1.0 0.0.0.255
Secondary节点:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 202.100.1.1
crypto isakmp keepalive 10 periodic
!
crypto ipsec transform-set cisco esp-3des esp-md5-hmac
mode tunnel
!
crypto map cisco 10 ipsec-isakmp
set peer 202.100.1.1
set transform-set cisco
set reverse-route tag 100
match address
reverse-route
!
interface Ethernet0/2
ip address 137.78.5.1 255.255.255.0
crypto map cisco
!
router ospf 110
router-id 55.1.1.1
redistribute static subnets tag 100
network 10.1.1.0 0.0.0.255 area 0
!ip route 0.0.0.0 0.0.0.0 137.78.5.10
!
ip access-list extended
permit ip 44.1.1.0 0.0.0.255 11.1.1.0 0.0.0.255
Inside节点:
router ospf 110
router-id 44.1.1.1
network 10.1.1.0 0.0.0.255 area 0
network 44.1.1.1 0.0.0.0 area 0
二、验证:
1.分支节点ping远端内部服务器44.1.1.1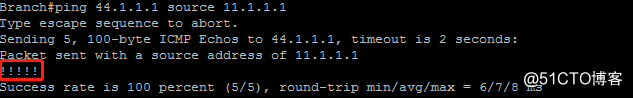
2.查看分支加密节点上ipsec sa,说明此时ipsec 连接是和远端网关Primary加密节点建立通信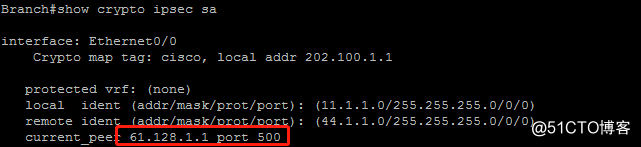
3.远端网关Primary加密节点静态路由,看到了该节点上RRI动态注入的静态路由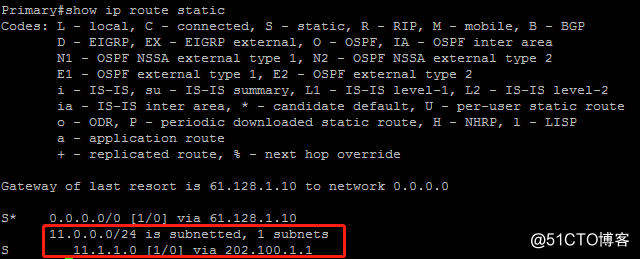
secondary节点由于未与branch节点建立连接,所以RRI没有动态注入静态路由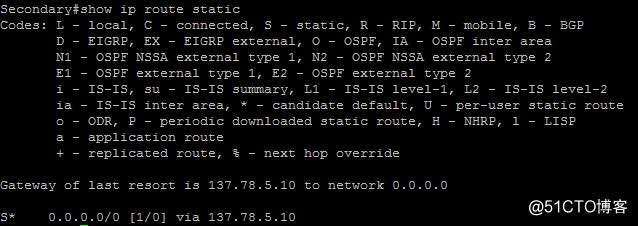
4.由于primary节点对RRI注入的静态路由做了重分布,在server节点上可以看到通过OSPF学习到的OE2类型的域外路由,路由条目去往11.1.1.0/24,下一跳为当前活动网关内部接口的IP地址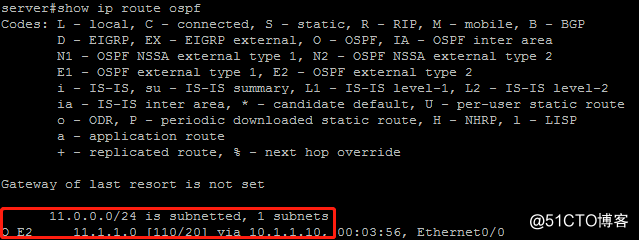
三、测试:
1.down掉R3的互联网口eth0/1,从44.1.1.0/24到11.1.1.0/24的通信中断一段时间后又重新建立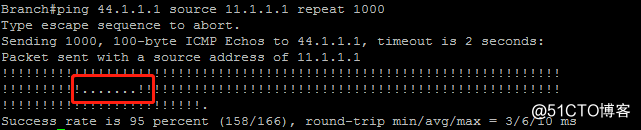
2.此时在分支节点上看ipsec sa发现分支节点与远端网络的secondary网关建立了ipsec ***连接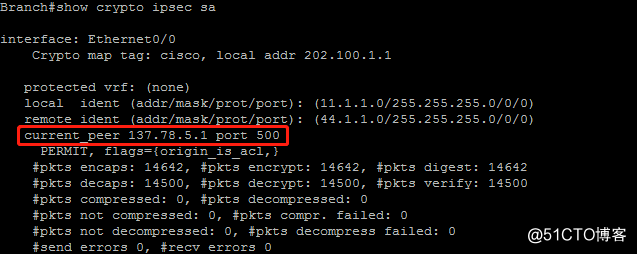
3.由于primary节点不属于活动网关,因此RRI未动态注入指向其的静态路由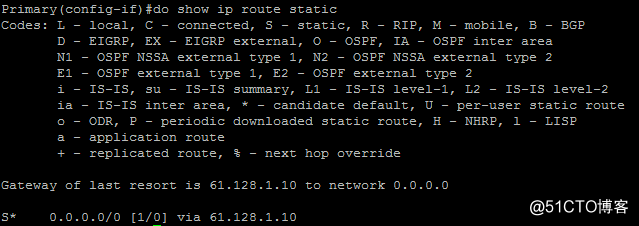
secondary网关在primary网关down掉后,成为活动主网关,可以在路由表中看到RRI注入的指向其的静态路由,并重发布进OSPF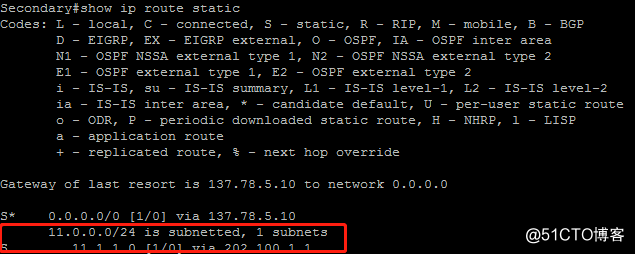
4.在server端,可以看到重发布进OSPF的域外路由下一跳变成secondary的内网接口地址。
四、其他
1.链路备份高可用性IPSec ×××使用DPD和RRI技术;
2.链路备份高可用性IPSec ×××不支持抢占特性。
二、设备备份IPSec ××× HA解决方案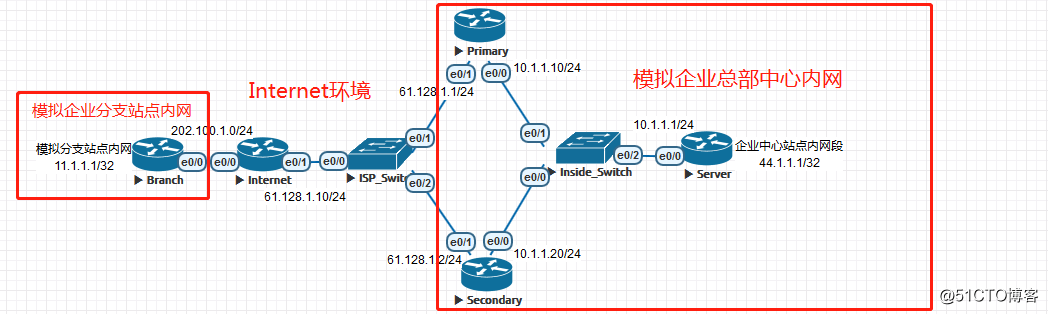
1.相关节点关键配置:
Branch节点:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 61.128.1.100
!
crypto ipsec transform-set cisco esp-3des esp-md5-hmac
mode tunnel
!
crypto map cisco 10 ipsec-isakmp
set peer 61.128.1.100
set transform-set cisco
match address
!
ip route 0.0.0.0 0.0.0.0 202.100.1.10
!
ip access-list extended
permit ip 11.1.1.0 0.0.0.255 44.1.1.0 0.0.0.255
Primary节点:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 202.100.1.1
!
crypto ipsec transform-set cisco esp-3des esp-md5-hmac
mode tunnel
!
crypto map cisco 10 ipsec-isakmp
set peer 202.100.1.1
set transform-set cisco
set reverse-route tag 100
match address
reverse-route static
!
interface Ethernet0/1
ip address 61.128.1.1 255.255.255.0
standby 1 ip 61.128.1.100
standby 1 priority 105
standby 1 preempt
standby 1 name Redun.
crypto map cisco redundancy Redun.
!
router ospf 110
router-id 33.1.1.1
redistribute static subnets tag 100
network 10.1.1.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 61.128.1.10
!
ip access-list extended
permit ip 44.1.1.0 0.0.0.255 11.1.1.0 0.0.0.255
Secondary节点:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 202.100.1.1
!
crypto ipsec transform-set cisco esp-3des esp-md5-hmac
mode tunnel
!
crypto map cisco 10 ipsec-isakmp
set peer 202.100.1.1
set transform-set cisco
set reverse-route tag 100
match address
reverse-route static
!
interface Ethernet0/1
ip address 61.128.1.2 255.255.255.0
standby 1 ip 61.128.1.100
standby 1 preempt
standby 1 name Redun.
crypto map cisco redundancy Redun.
!
router ospf 110
router-id 55.1.1.1
redistribute static subnets tag 100
network 10.1.1.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 61.128.1.10
!
ip access-list extended
permit ip 44.1.1.0 0.0.0.255 11.1.1.0 0.0.0.255
公司内部Server节点:
router ospf 110
router-id 44.1.1.1
network 0.0.0.0 255.255.255.255 area 0
2.验证
测试Branch节点内部网络11.1.1.1到企业中心站点内网44.1.1.1的连通性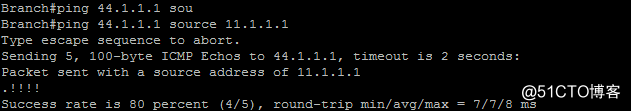
查看Primary的HSRP状态,该设备为active状态,而Secondary节点HSRP状态为standby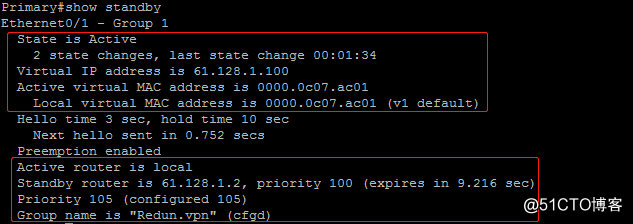
由于Primary节点为HSRP的active路由器,由配置中“reverse-route static”的特性,产生RRI的静态路由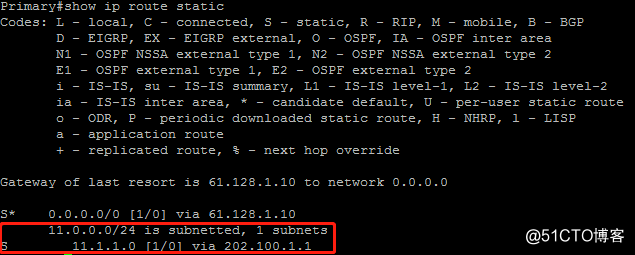
由于Secondry节点为HSRP的standby路由器,所以没有产生RRI静态路由,这样也保证了企业内部站点不会学习到两条去往远程通信点的路由。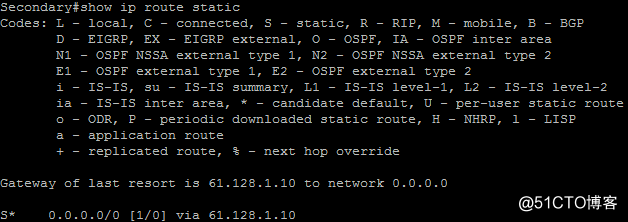
由于Primary节点和Secondary节点设备OSPF配置中将RRI产生的静态路由(tag=100)重分布进OSPF,所以在内部server节点上能收到一条去往11.1.1.0/24、下一跳为Primary内部接口的OE2域外路由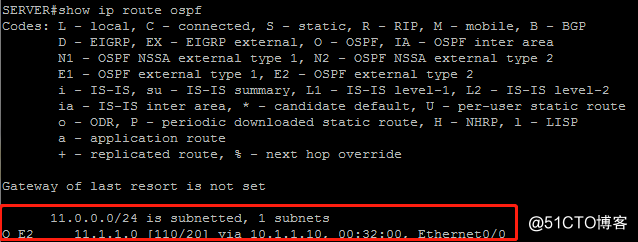
3.测试及发现的问题。
为了观察实验现象,在Branch节点上持续Ping 44.1.1.1,并将Primary节点reload,此时可看到Secondary状态由standby切换为active,ping中断十几个包之后会恢复通信,此时在Secondary节点上show ip route static会发现RRI静态路由,在总部中心内网Server节点show ip route ospf会看到去往11.1.1.0/24同时下一跳指向Secondary节点内部接口eth0/0-IP地址的OE2路由。
我的实验环境应该是有BUG,做不了这个切换。因为Primary节点起来之后,Secondary的HSRP状态由于配置了preempt的原因由active-->standby,但是Branch持续ping的时候,Primary节点报错*May 20 12:12:06.758: %CRYPTO-4-RECVD_PKT_INV_SPI: decaps: rec'd IPSEC packet has invalid spi for destaddr=61.128.1.100, prot=50, spi=0xD304069F(3540256415), srcaddr=202.100.1.1, input interface=Ethernet0/1
我将Branch、Primary、Secondary节点相关接口重新调用下crypto map,然后在Branch上ping 44.1.1.1,OK了。
我排除了中间交换机IGMP Snooping的可能性,我估计应该是模拟器bug的原因,若有高手路过,可帮忙分析下,不胜感激,我模拟器保留配置。