网络拓扑:

在中小企业的办公网络的设计中,通常为了安全考虑,需要将不同部门之间的互访的流量经过防火墙中转,同时结合vpn stance将业务进行隔离,在本例中,使用两台USG防火墙做HA作为整个办公网的接入防火墙,企业的互联网接入有电信和联通的两条专线进行接入。
设计要点:
1.两台USG防火墙互联的业务口使用子接口的方式进行互联
通常使用子接口的方式一方面可以节省设备的物理接口。另一方面下联交换机通过trunk的方式接入,使用子接口可以很容易的创建大量的安全域实现隔离。
2.通常建议USG防火墙使用主备模式的HA,不建议使用负载分担模式的HA
由于防火墙的HA是基于会话和状态的,因此在高可用要求高的场合不建议使用负载分担的方式。
3.对不同的业务访问使用策略路由进行控制
在本例中,开发和测试访问internet默认走联通的链路,财务和OA默认走电信的链路。
4.对不同的业务创建不同的安全域
5.对不同的业务间的访问通过防火墙的安全策略进行精细化的控制
配置如下:
HRP_M[BJ-ZHX-FW]
===================================================================
#
sysname BJ-ZHX-FW
#
l2tp domain suffix-separator @
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
hrp enable
hrp standby-device
hrp interface Eth-Trunk0 remote 172.16.1.3 heartbeat-only
hrp auto-sync config static-route
#
update schedule location-sdb weekly Sun 22:24
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
undo web-manager config-guide enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 23:01
update schedule av-sdb daily 23:01
update schedule sa-sdb daily 23:01
update schedule cnc daily 23:01
update schedule file-reputation daily 23:01
#
ip vpn-instance default
ipv4-family
#
ip address-set kaifa type object
description kaifa
address 0 10.158.0.0 mask 16
#
ip address-set ceshi type object
description ceshi
address 0 10.133.0.0 mask 16
#
ip address-set caiwu type object
description caiwu
address 0 10.125.0.0 mask 16
#
ip address-set oa type object
description oa
address 0 10.178.0.0 mask 16
#
ip address-set bj-lan type group
address 0 address-set kaifa
address 1 address-set ceshi
address 2 address-set caiwu
address 3 address-set oa
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%Dm)zP@/@B4'q&:QY1cq&e>f>Sf6j8)KBs/hcLwX"yogE>fAe@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%}:)A*y$fjAi$*h91`2*Be3@Y6SreDuX7`>7`tY1kII^V3@\e@%@%
level 15
manager-user admin
password cipher @%@%x;X'+k=QR+t,#'*3\ME;a9Z=UFJ(U}+g{S:qBn3g'woV9Z@a@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
interface Eth-Trunk0
ip address 172.16.1.2 255.255.255.240
vrrp vrid 10 virtual-ip 172.16.1.1 active
alias hearbeat
gateway 172.16.1.3
undo service-manage enable
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/0
undo shutdown
eth-trunk 0
#
interface GigabitEthernet1/0/1
undo shutdown
eth-trunk 0
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/2.1
vlan-type dot1q 10
ip address 61.135.142.2 255.255.255.224
vrrp vrid 20 virtual-ip 61.135.142.3 active
alias untrust-cu
gateway 61.135.142.1
undo service-manage enable
#
interface GigabitEthernet1/0/2.2
vlan-type dot1q 20
ip address 222.128.90.2 255.255.255.224
vrrp vrid 30 virtual-ip 222.128.90.3 active
alias untrust-ct
gateway 222.128.90.1
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/3.1
vlan-type dot1q 40
ip address 10.158.1.251 255.255.255.0
vrrp vrid 40 virtual-ip 10.158.1.253 active
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/3.2
vlan-type dot1q 50
ip address 10.133.1.251 255.255.255.0
vrrp vrid 50 virtual-ip 10.133.1.253 active
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/3.3
vlan-type dot1q 60
ip address 10.125.1.251 255.255.255.0
vrrp vrid 60 virtual-ip 10.125.1.253 active
alias GE1/0/3.3
gateway 10.125.1.254
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/3.4
vlan-type dot1q 70
ip address 10.178.1.251 255.255.255.0
vrrp vrid 70 virtual-ip 10.178.1.253 active
alias GE1/0/3.4
gateway 10.178.1.254
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2.1
add interface GigabitEthernet1/0/2.2
#
firewall zone dmz
set priority 50
add interface Eth-Trunk0
#
firewall zone name kaifa id 4
description kaifa
set priority 80
add interface GigabitEthernet1/0/3.1
#
firewall zone name ceshi id 5
description ceshi
set priority 75
add interface GigabitEthernet1/0/3.2
#
firewall zone name caiwu id 6
description caiwu
set priority 70
add interface GigabitEthernet1/0/3.3
#
firewall zone name oa id 7
description oa
set priority 65
add interface GigabitEthernet1/0/3.4
#
ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet1/0/2.1 61.135.142.1
ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet1/0/2.2 222.128.90.1
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
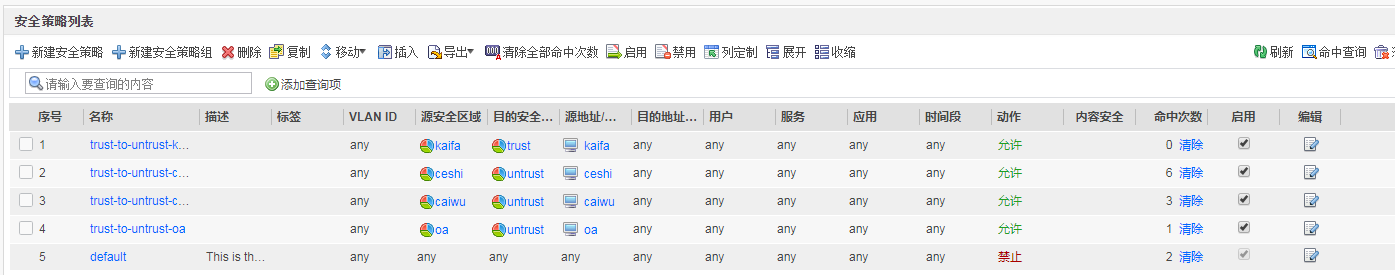
security-policy
rule name trust-to-untrust-kaifa
source-zone kaifa
destination-zone trust
source-address address-set kaifa
action permit
rule name trust-to-untrust-ceshi
source-zone ceshi
destination-zone untrust
source-address address-set ceshi
action permit
rule name trust-to-untrust-caiwu
source-zone caiwu
destination-zone untrust
source-address address-set caiwu
action permit
rule name trust-to-untrust-oa
source-zone oa
destination-zone untrust
source-address address-set oa
action permit
#
auth-policy
#
traffic-policy
#
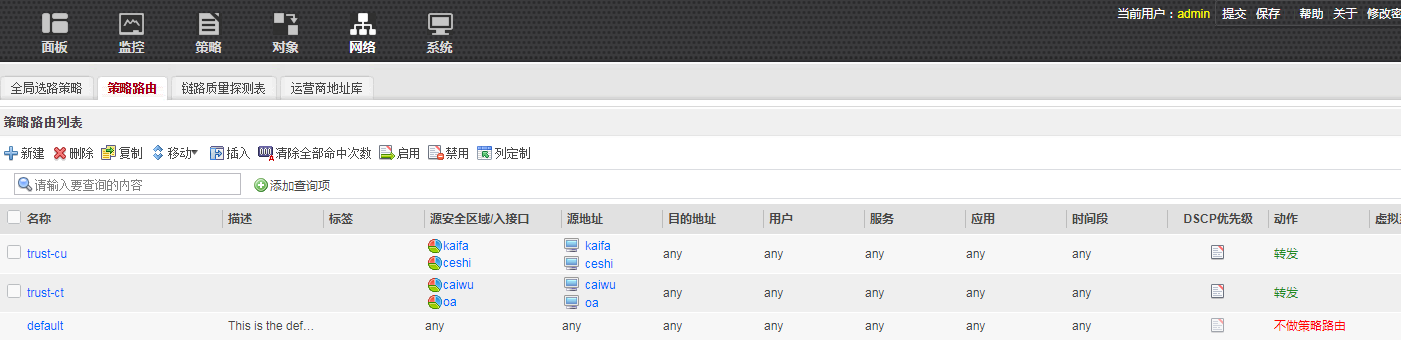
policy-based-route
rule name trust-cu 1
source-zone ceshi
source-zone kaifa
source-address address-set ceshi
source-address address-set kaifa
action pbr egress-interface GigabitEthernet1/0/2.1 next-hop 61.135.142.1
rule name trust-ct 2
source-zone caiwu
source-zone oa
source-address address-set caiwu
source-address address-set oa
action pbr egress-interface GigabitEthernet1/0/2.2 next-hop 222.128.90.1
#
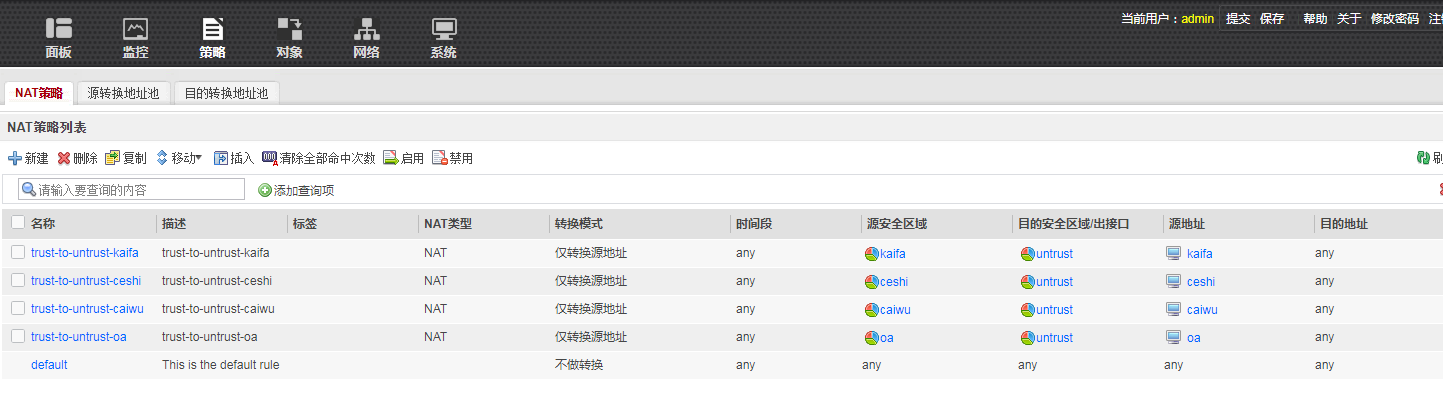
nat-policy
rule name trust-to-untrust-kaifa
description trust-to-untrust-kaifa
source-zone kaifa
destination-zone untrust
source-address address-set kaifa
action source-nat easy-ip
rule name trust-to-untrust-ceshi
description trust-to-untrust-ceshi
source-zone ceshi
destination-zone untrust
source-address address-set ceshi
action source-nat easy-ip
rule name trust-to-untrust-caiwu
description trust-to-untrust-caiwu
source-zone caiwu
destination-zone untrust
source-address address-set caiwu
action source-nat easy-ip
rule name trust-to-untrust-oa
description trust-to-untrust-oa
source-zone oa
destination-zone untrust
source-address address-set oa
action source-nat easy-ip
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return
ZHX-SW
===================================================================
#
sysname ZHX-SW
#
vlan batch 2 to 5 40 50 60 70 80
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
ip vpn-instance caiwu
ipv4-family
route-distinguisher 65001:300
vpn-target 65001:300 export-extcommunity
vpn-target 65002:300 import-extcommunity
#
ip vpn-instance ceshi
ipv4-family
route-distinguisher 65001:200
vpn-target 65001:200 export-extcommunity
vpn-target 65002:200 import-extcommunity
#
ip vpn-instance kaifa
ipv4-family
route-distinguisher 65001:100
vpn-target 65001:100 export-extcommunity
vpn-target 65002:100 import-extcommunity
#
ip vpn-instance oa
ipv4-family
route-distinguisher 65001:400
vpn-target 65001:400 export-extcommunity
vpn-target 65002:400 import-extcommunity
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
shutdown
#
interface Vlanif40
ip binding vpn-instance kaifa
ip address 10.158.1.254 255.255.255.0
#
interface Vlanif50
ip binding vpn-instance ceshi
ip address 10.133.1.254 255.255.255.0
#
interface Vlanif60
ip binding vpn-instance caiwu
ip address 10.125.1.254 255.255.255.0
#
interface Vlanif70
ip binding vpn-instance oa
ip address 10.178.1.254 255.255.255.0
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 40 50 60 70 80
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 40 50 60 70 80
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 2 to 4094
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
#
interface GigabitEthernet0/0/24
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 vpn-instance kaifa 10.158.1.253
ip route-static vpn-instance ceshi 0.0.0.0 0.0.0.0 Vlanif50 10.133.1.253
ip route-static vpn-instance caiwu 0.0.0.0 0.0.0.0 Vlanif60 10.125.1.253
ip route-static vpn-instance oa 0.0.0.0 0.0.0.0 Vlanif70 10.178.1.253
#
user-interface con 0
user-interface vty 0 4
#
return
NAT策略如下
===================================================================
安全策略如下
===================================================================
策略路由配置
===================================================================
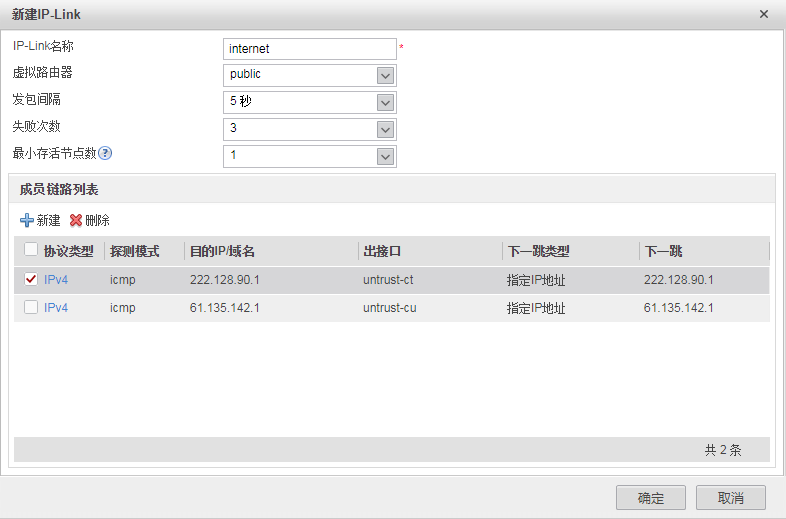
IP-LINK的配置
===================================================================