一、dashboard搭建
1、在master创建一个文件夹存放相关yaml文件
mkdir UI
cd UI
#用到的yaml文件有下面三个
[root@k8s-master-101 UI]# ls
dashboard-controller.yaml dashboard-rabc.yaml dashboard-service.yaml
2、创建rbac角色的文件,让应用服务具有权限访问集群,关于角色部分现在还不是很清楚,以后了解了再补充
vim dashboard-rabc.yaml
[root@k8s-master-101 UI]# cat dashboard-rabc.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard
namespace: kube-system
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
3、创建rabc
kubectl create -f dashboard-rabc.yaml
4、创建dashboard的deployment的文件,这里的镜像用了阿里的一个镜像,因为国外的拉不到。
registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.0
vim dashboard-controller.yaml
[root@k8s-master-101 UI]# cat dashboard-controller.yaml
apiVersion: apps/v1beta1
kind: Deployment
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ''
spec:
serviceAccountName: kubernetes-dashboard
containers:
- name: kubernetes-dashboard
image: registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.0
resources:
limits:
cpu: 100m
memory: 300Mi
requests:
cpu: 100m
memory: 100Mi
ports:
- containerPort: 9090
protocol: TCP
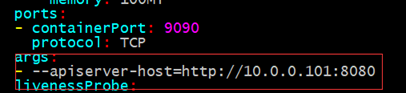
#args:
#- --apiserver-host=http://10.0.0.101:8080
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 9090
initialDelaySeconds: 30
timeoutSeconds: 30
tolerations:
- key: "CriticalAddonsOnly"
operator: "Exists"
5、创建deployment
kubectl create -f dashboard-controller.yaml
6、创建dashboard的service文件,匹配上面的deployment文件创建的pod标签
这里指定映射到宿主机的nodePort为43210,这样比较好记。nodePort的范围为30000-50000之间,前面某个配置文件里好像有。
vim dashboard-service.yaml
[root@k8s-master-101 UI]# cat dashboard-service.yaml
apiVersion: v1
kind: Service
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
type: NodePort
selector:
k8s-app: kubernetes-dashboard
ports:
- port: 80
targetPort: 9090
nodePort: 43210
7、创建service
kubectl create -f dashboard-service.yaml
二、查看
1、查询服务
[root@k8s-master-101 UI]# kubectl cluster-info
Kubernetes master is running at http://localhost:8080
kubernetes-dashboard is running at http://localhost:8080/api/v1/namespaces/kube-system/services/kubernetes-dashboard/proxy
2、查询pod地址
[root@k8s-master-101 UI]# kubectl get pod -o wide -n kube-system
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE
kubernetes-dashboard-6f79dd6f9f-hk5xc 1/1 Running 26 19d 172.17.71.2 10.0.0.103 <none>
3、查询svc

[root@k8s-master-101 UI]# kubectl get svc -o wide -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
kubernetes-dashboard NodePort 10.10.10.117 <none> 80:43210/TCP 19d k8s-app=kubernetes-dashboard
4、访问10.0.0.103的43210端口

5、补充一下之前遇到的问题:
一开始在做证书的时候没有加上10.10.10.1这个service的ip段,导致这个地址无法认证,连接不到apiserver
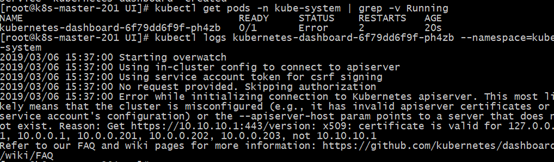
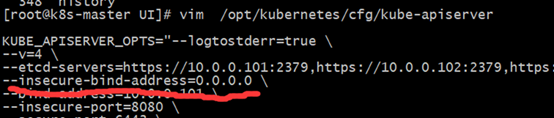
然后当时的方法是在yaml文件里指定apiserver-host,然后把apiserver的配置文件里insecure-bind-address的地址从127.0.0.1改成0.0.0.0,这样修改后才可以访问。
后面我把证书都重新做了一遍,加上了service的地址后就没有这个问题了。这里就记录一下,所以证书得做好啊啊啊啊~~