目录
项目说明
nginx设置https
生成证书
nginx配置文件
tomcat设置https
生成证书
tomcat配置(所有模块都可用共用一个证书配置)
复制jdk认证证书
修改应用里通过nginx调用的url
重启应用
对应漏洞
User credentials are sent in clear text
Severity Medium
Reported by module /Crawler/12-Crawler_User_Credentials_Plain_Text.jsDescription
User credentials are transmitted over an unencrypted channel. This information should always be transferred via an encrypted
channel (HTTPS) to avoid being intercepted by malicious users.Impact
A third party may be able to read the user credentials by intercepting an unencrypted HTTP connection.Recommendation
Because user credentials are considered sensitive information, should always be transferred to the server over an encrypted
connection (HTTPS)
项目说明
webapp分为多个模块,模块间通过nginx和sso模块相互调用
nginx设置https
生成证书
- 创建ssl目录
cd $nginx_home
mkdir ssl
cd ssl - 建立服务器私钥(过程需要输入密码,请记住这个changeit)生成RSA密钥
openssl genrsa -des3 -out server.key 2048
openssl req -new -key server.key -out server.csr
cp server.key server.key.org
openssl rsa -in server.key.org -out server.key - 使用上面的密钥和CSR对证书进行签名,以下命令生成v1版证书
openssl x509 -req -days 3650 -sha256 -in server.csr -signkey server.key -out servernew.crt - 把生成的证书导入java安全认证文件(关键步骤)
keytool -import -v -trustcacerts -alias nginx -file servernew.crt -keystore "$JAVA_HOME/jre/lib/security/cacerts"
输入密码:changeit
nginx配置文件
- server配置打开https
server {
listen 8026 ssl;
server_name localhost;
ssl_certificate /usr/local/nginx/ssl/servernew.crt;
ssl_certificate_key /usr/local/nginx/ssl/server.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on; - 转发改为https
location /bp-sso {
proxy_connect_timeout 300;
proxy_send_timeout 300;
proxy_read_timeout 300;
proxy_pass https://bp-sso;
proxy_set_header Host remote_addr;
}
tomcat设置https
生成证书
- 创建key目录
cd $tomcat_home/conf
mkdir key
cd key - keytool -genkey -v -alias tomcat -keyalg RSA -keystore tomcat.keystore
changeit - keytool -export -alias tomcat -keystore tomcat.keystore -file server.crt
输入密码: changeit - 把生成的证书导入java安全认证文件(关键步骤)
keytool -import -v -trustcacerts -alias tomcat -file server.crt -keystore "$JAVA_HOME/jre/lib/security/cacerts"
changeit
tomcat配置(所有模块都可用共用一个证书配置)
- 注释掉原来的端口号
<!--
<Connector port="8285" protocol="HTTP/1.1"
connectionTimeout="20000"
redirectPort="8443" />
-->- 把8443端口号改为原来要用的端口号,并添加https配置
<Connector port="8285" protocol="org.apache.coyote.http11.Http11NioProtocol"
maxThreads="150" SSLEnabled="true" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS"
keystoreFile="/opthb/bin/apache-tomcat-8.0.44_sso/conf/key/tomcat.keystore"
keystorePass="changeit"
/>
复制jdk认证证书
cd $JAVA_HOME/jre/lib/security
cp cacerts jssecacerts
修改应用里通过nginx调用的url
应用内部用过nginx调用的url都要改成https方式,例如:
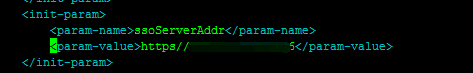
重启应用
nginx和tomcat都改好以后,重启所有应用