1、 an SQLi vulnerability will allow you to do the following
- query the database using select statement forezample users table. you might get the password or usersname
- Bypass the login page executing successfuly query results
- Execute system commands in the database in oreder compromise the web server
- Execute inserts.delete commands to manipulate the records in the database
2、Command Injection
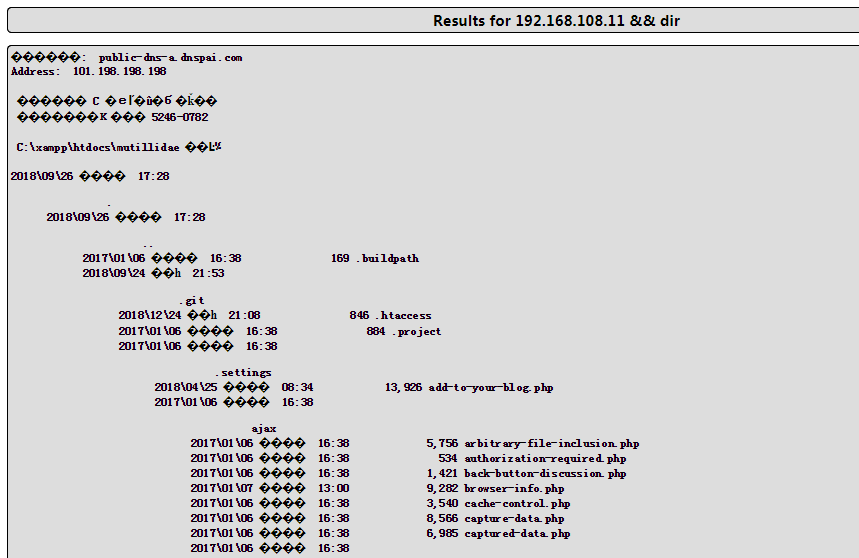
we can append other commands after the variable and the application will be to execute it for us , my goal is to make the backend execute someting like this [nslookup [domain name variable ] && [other command ]
3、OWASP top 10
Injection-----> when a attacker can inject and execute a custom command in the backend because of missing sanitization,besides it ,command Injection are more like LDAP、XPath、NoSQLo XML Parsers、STMTP Header
Broken Authentication ------> a hacker finds the user's idntity, credentials bouth name and password or web session
Sesitive Data 、 XML External Entities \ Broken Access Control \ Security Misconfig \Cross-site Scripting \ Insecure Deserialization \ Using Components with know vulnerability\ Insufficient logging
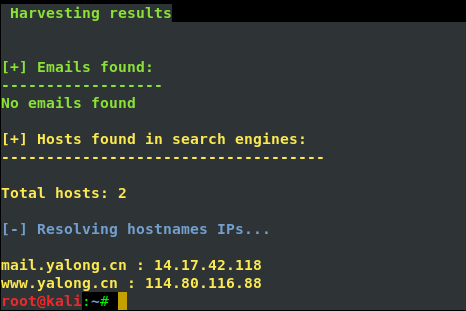
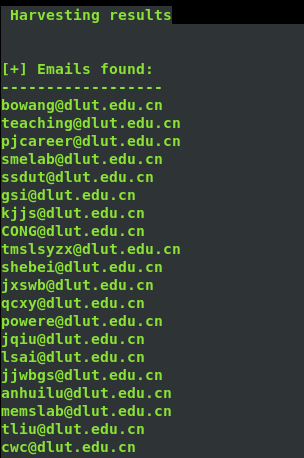
4、邮件信息收集
theharverster -d [目标网络域名地址] -l [邮件地址数量] -b [使用的搜索的公共知识库] eg : theharvester -d yalong.cn -l 20 -b baidu

5、 use Whois search DNS and ip register name and phone number and email
step one we can use the Whois.net the url: http:www.whois.net or another website is NetCraft the url :https://www.netcraft.com/
step two: use the command whois ,the screenshout as follow

another wegit tools is host it can translate ip to hostname
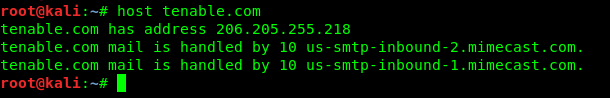
nslookup id find DNS