版权声明:欢迎转载,转载请注明出处:土豆洋芋山药蛋 https://blog.csdn.net/qq_33414271/article/details/80682205
一、实验目的:
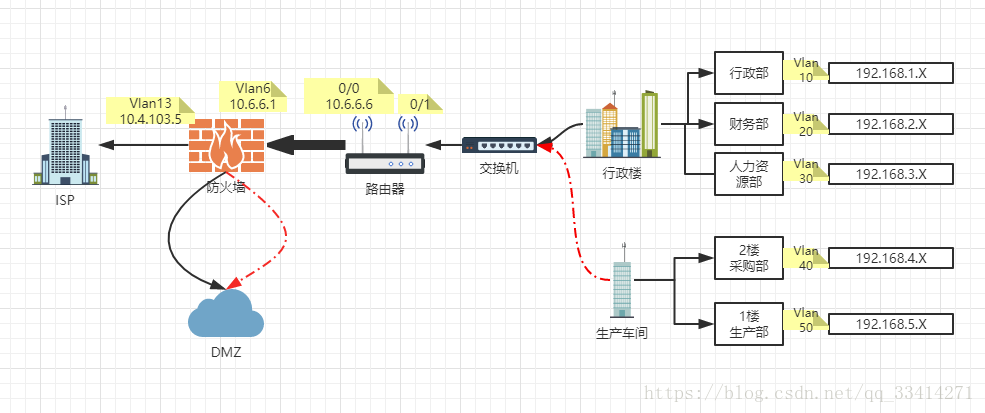
- 搭建企业网站,根据实际进行网络拓扑与IP段规划:
行政楼:人力资源部【1楼】
财务部【2楼】
行政部【3楼】
生产车间:生产部【1楼】
采购部【2楼】 - 只有行政楼各部门通过NAT访问公网,生产楼各部门只能访问内网
- 使用DHCP自动获取IP
二、实验设备:
交换机(二层)、路由器、防火墙
网线若干
电脑5台
三、实验步骤:
- 连接交换机、路由器、防火墙
- 配置DHCP池,排除默认网关
- 配置防火墙名称,启用防火墙结口VLAN
- 配置NAT转换:内网到外网
- 配置ACL:外网到内网
四、实验拓扑:
五、配置命令:
**交换机**
vlan database
vlan 10
vlan 20
vlan 30
vlan 40
vlan 50
int fa0/1
sw acc vlan 10
exit
int fa0/2
sw acc vlan 20
exit
int fa0/3
sw acc vlan 30
exit
int fa0/4
sw acc vlan 40
exit
int fa0/5
sw acc vlan 50
exit
配置交换机上联端口
config terminal
interface fa0/24
switchport mode trunk
end
**路由器**
interface GigabitEthernet0/1.1
encapsulation dot1Q 10
ip address 192.168.1.1 255.255.255.0
exit
interface GigabitEthernet0/1.2
encapsulation dot1Q 20
ip address 192.168.2.1 255.255.255.0
exit
interface GigabitEthernet0/1.3
encapsulation dot1Q 30
ip address 192.168.3.1 255.255.255.0
exit
interface GigabitEthernet0/1.4
encapsulation dot1Q 40
ip address 192.168.4.1 255.255.255.0
exit
interface GigabitEthernet0/1.5
encapsulation dot1Q 50
ip address 192.168.5.1 255.255.255.0
exit
配置DHCP
排除默认网关
ip dhcp excluded-address 192.168.2.1
ip dhcp excluded-address 192.168.1.1
ip dhcp excluded-address 192.168.1.254
ip dhcp excluded-address 192.168.2.254
ip dhcp excluded-address 192.168.3.1
ip dhcp excluded-address 192.168.4.1
ip dhcp excluded-address 192.168.5.1
ip dhcp excluded-address 192.168.3.254
ip dhcp excluded-address 192.168.4.254
ip dhcp excluded-address 192.168.5.254
配置池
ip dhcp pool pool10
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
ip dhcp pool pool20
network 192.168.2.0 255.255.255.0
default-router 192.168.2.1
ip dhcp pool pool30
network 192.168.3.0 255.255.255.0
default-router 192.168.3.1
ip dhcp pool pool40
network 192.168.4.0 255.255.255.0
default-router 192.168.4.1
ip dhcp pool pool50
network 192.168.5.0 255.255.255.0
default-router 192.168.5.1
#三层交换机使用
ip helper-address *路由器可达的端口*
**防火墙**
1、防火墙配置名称
config terminal
hostname g408-firewall
2、启用防火墙结口VLAN
#全部端口默认为vlan1,所以划分的时候不选vlan1
config terminal
interface vlan 6
no shutdown
nameif inside
security-level 100
ip address 10.6.6.1 255.255.255.0
interface vlan 13
no shutdown
nameif outside
security-level 0
ip address 10.4.103.5 255.255.255.0
end
write memory
#因为此防火墙不适用于在配置一个DMZ,所以讲DMZ配置在内网的一个主机中
###############
interface vlan 70
no shutdown
nameif DMZ
security-level 50
ip address DMZ的ip 255.255.255.0
end
###################
3、配置防火墙端口
config terminal
interface Ethernet0/0
no shutdown
switchport access vlan 6
interface Ethernet0/1
no shutdown
switchport access vlan 13
end
write memory
4、配置NAT转换:内网到外网
config terminal
nat (inside) 1 0.0.0.0 0.0.0.0
global (outside) 1 210.38.93.0-210.38.93.255 netmask 255.255.255.0
end
write memory
5、配置ACL:外网到内网
#出允许
config terminal
access-list 102 extended permit ip any any #允许
access-group 102 in interface outside #入站:由缺省的拒绝变为允许
end
write memory
#103为进入拒绝
access-list 103 extended deny ip 192.168.4.0 255.255.255.0 host 192.168.10.10
access-list 103 extended deny ip 192.168.5.0 255.255.255.0 host 192.168.10.10
access-list 103 extended permit ip any any
access-group 103 in interface inside
6、配置路由
config terminal
route outside 0.0.0.0 0.0.0.0 10.4.103.1 1
route inside 192.168.1.0 255.255.255.0 10.6.6.6 1
route inside 192.168.2.0 255.255.255.0 10.6.6.6 1
route inside 192.168.3.0 255.255.255.0 10.6.6.6 1
route inside 192.168.4.0 255.255.255.0 10.6.6.6 1
route inside 192.168.5.0 255.255.255.0 10.6.6.6 1
end
write memory
7、测试
防火墙:
show route
show conn
show xlate
show local-host
show arp
路由器:
show ip route
show arp
show interface ethernet 0/0
write memory
show running-config
show interfaces ethernet 0/1
ping 10.4.103.1
备注:
sh xlat查看转换表
sh route (防火墙)
sh ip route (路由器)
sh arp arp表
sh conn 查看连接信息
sh access-list 102 查看ACL信息
六、实验结果:
可以使用DHCP自动获取IP,只有行政楼各部门通过NAT访问公网,生产楼各部门只能访问内网。