[root@localhost ~]# yum install vsftpd -y
[root@localhost ~]# yum info vsftpd
已加载插件:fastestmirror
Loading mirror speeds from cached hostfile
* base: mirrors.tuna.tsinghua.edu.cn
* extras: mirrors.huaweicloud.com
* updates: mirrors.tuna.tsinghua.edu.cn
已安装的软件包
名称 :vsftpd
架构 :x86_64
版本 :3.0.2
发布 :22.el7
大小 :348 k
源 :installed
来自源:base
简介 : Very Secure Ftp Daemon
网址 :https://security.appspot.com/vsftpd.html
协议 : GPLv2 with exceptions
描述 : vsftpd is a Very Secure FTP daemon. It was written completely from
: scratch.
[root@localhost ~]# yum info openssl
已加载插件:fastestmirror
Loading mirror speeds from cached hostfile
* base: mirrors.tuna.tsinghua.edu.cn
* extras: mirrors.huaweicloud.com
* updates: mirrors.tuna.tsinghua.edu.cn
已安装的软件包
名称 :openssl
架构 :x86_64
时期 :1
版本 :1.0.2k
发布 :12.el7
大小 :814 k
源 :installed
来自源:base
简介 : Utilities from the general purpose cryptography library with TLS implementation
网址 :http://www.openssl.org/
协议 : OpenSSL
描述 : The OpenSSL toolkit provides support for secure communications between
: machines. OpenSSL includes a certificate management tool and shared
: libraries which provide various cryptographic algorithms and
: protocols.
[root@localhost ~]# cd /etc/vsftpd/
[root@localhost vsftpd]# ls
ftpusers user_list vsftpd.conf vsftpd_conf_migrate.sh
[root@localhost vsftpd]# mv vsftpd.conf vsftpd.conf.bak
[root@localhost vsftpd]# mkdir certs
[root@localhost vsftpd]# vim vsftpd.conf
listen_port=21
listen=YES
background=YES
#禁止匿名用户访问
anonymous_enable=NO
#允许本机用户访问 比如 root
local_enable=YES
#允许写权限
write_enable=YES
local_umask=022
anon_upload_enable=NO
anon_mkdir_write_enable=NO
dirmessage_enable=YES
xferlog_enable=YES
#connect_from_port_20=NO
#主动模式下数据传输使用的端口 默认是20
#如果要改变端口需要将connect_from_port_20=YES设置为NO
#connect_from_port_20=NO
#ftp_data_port=2000
#listen_data_port=2000
chown_uploads=NO
xferlog_enable=YES
xferlog_file=/var/log/vsftpd.log
xferlog_std_format=YES
async_abor_enable=YES
ascii_upload_enable=YES
ascii_download_enable=YES
pam_service_name=vsftpd
#设定被动模式的通信端口 29100 - 29200之间
pasv_min_port=29100
pasv_max_port=29200
#不对ip地址进行域名解析ip 这样会效率更高
#pasv_addr_resolve=NO
#连接超时 默认是60秒
connect_timeout=30
#数据传输连接超时 默认是300秒
data_connection_timeout=50
#开启本地用户chroot 限制 ,本地用户不能访问除自身宿主目录以外的目录
chroot_local_user=YES
# 开启chroot 列表 在这个列表里面的用户 可以不受chroot 的限制,访问除自身宿主目录以外的目录
chroot_list_enable=YES
#不受chroot限制的用户列表所在的文件路径
chroot_list_file=/etc/vsftpd/chroot_list
#启用用户列表 也就是允许系统用户使用vsftp
userlist_enable=NO
#接受用户列表
userlist_deny=NO
#用户列表路径 这里的用户都是linux系统的用户
userlist_file=/etc/vsftpd/user_list
#开启被动模式,建议使用被动模式较为安全
pasv_enable=YES
chroot_list:不受chroot约束的用户列表
ftpusers:被禁止使用ftp的用户列表
user_list:可以使用ftp的用户列表
[root@localhost vsftpd]# vim chroot_list
stuart
[root@localhost vsftpd]# systemctl start vsftpd
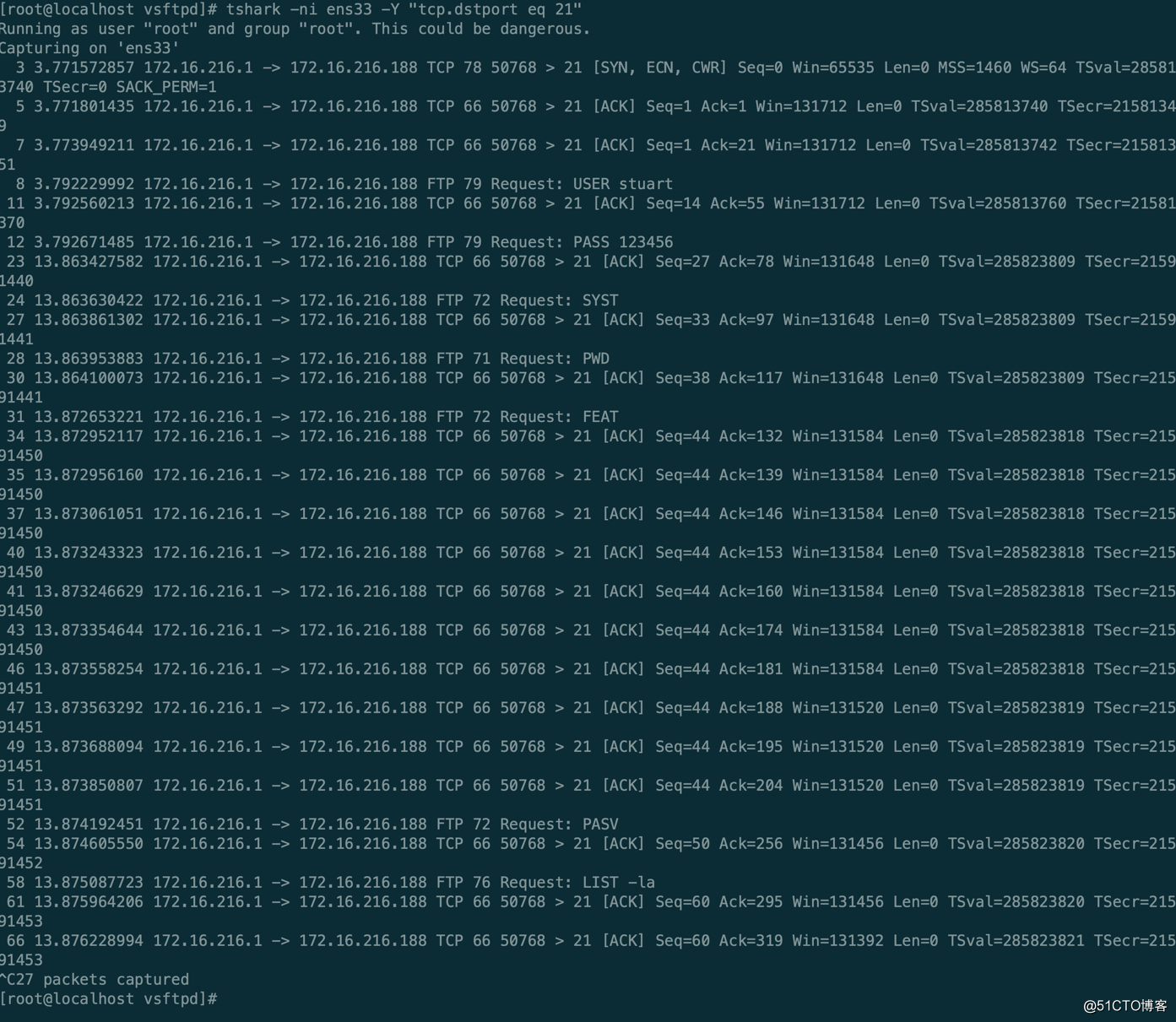
[root@localhost vsftpd]# tshark -ni ens33 -Y "tcp.dstport eq 21"
Running as user "root" and group "root". This could be dangerous.
Capturing on 'ens33'
3 3.771572857 172.16.216.1 -> 172.16.216.188 TCP 78 50768 > 21 [SYN, ECN, CWR] Seq=0 Win=65535 Len=0 MSS=1460 WS=64 TSval=285813740 TSecr=0 SACK_PERM=1
5 3.771801435 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=1 Ack=1 Win=131712 Len=0 TSval=285813740 TSecr=21581349
7 3.773949211 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=1 Ack=21 Win=131712 Len=0 TSval=285813742 TSecr=21581351
8 3.79222××× 172.16.216.1 -> 172.16.216.188 FTP 79 Request: USER stuart
11 3.792560213 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=14 Ack=55 Win=131712 Len=0 TSval=285813760 TSecr=21581370
12 3.792671485 172.16.216.1 -> 172.16.216.188 FTP 79 Request: PASS 123456
23 13.863427582 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=27 Ack=78 Win=131648 Len=0 TSval=285823809 TSecr=21591440
24 13.863630422 172.16.216.1 -> 172.16.216.188 FTP 72 Request: SYST
27 13.863861302 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=33 Ack=97 Win=131648 Len=0 TSval=285823809 TSecr=21591441
28 13.863953883 172.16.216.1 -> 172.16.216.188 FTP 71 Request: PWD
30 13.864100073 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=38 Ack=117 Win=131648 Len=0 TSval=285823809 TSecr=21591441
31 13.872653221 172.16.216.1 -> 172.16.216.188 FTP 72 Request: FEAT
34 13.872952117 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=44 Ack=132 Win=131584 Len=0 TSval=285823818 TSecr=21591450
35 13.872956160 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=44 Ack=139 Win=131584 Len=0 TSval=285823818 TSecr=21591450
37 13.873061051 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=44 Ack=146 Win=131584 Len=0 TSval=285823818 TSecr=21591450
40 13.873243323 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=44 Ack=153 Win=131584 Len=0 TSval=285823818 TSecr=21591450
41 13.873246629 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=44 Ack=160 Win=131584 Len=0 TSval=285823818 TSecr=21591450
43 13.873354644 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=44 Ack=174 Win=131584 Len=0 TSval=285823818 TSecr=21591450
46 13.873558254 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=44 Ack=181 Win=131584 Len=0 TSval=285823818 TSecr=21591451
47 13.873563292 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=44 Ack=188 Win=131520 Len=0 TSval=285823819 TSecr=21591451
49 13.873688094 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=44 Ack=195 Win=131520 Len=0 TSval=285823819 TSecr=21591451
51 13.873850807 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=44 Ack=204 Win=131520 Len=0 TSval=285823819 TSecr=21591451
52 13.874192451 172.16.216.1 -> 172.16.216.188 FTP 72 Request: PASV
54 13.874605550 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=50 Ack=256 Win=131456 Len=0 TSval=285823820 TSecr=21591452
58 13.875087723 172.16.216.1 -> 172.16.216.188 FTP 76 Request: LIST -la
61 13.875964206 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=60 Ack=295 Win=131456 Len=0 TSval=285823820 TSecr=21591453
66 13.876228994 172.16.216.1 -> 172.16.216.188 TCP 66 50768 > 21 [ACK] Seq=60 Ack=319 Win=131392 Len=0 TSval=285823821 TSecr=21591453
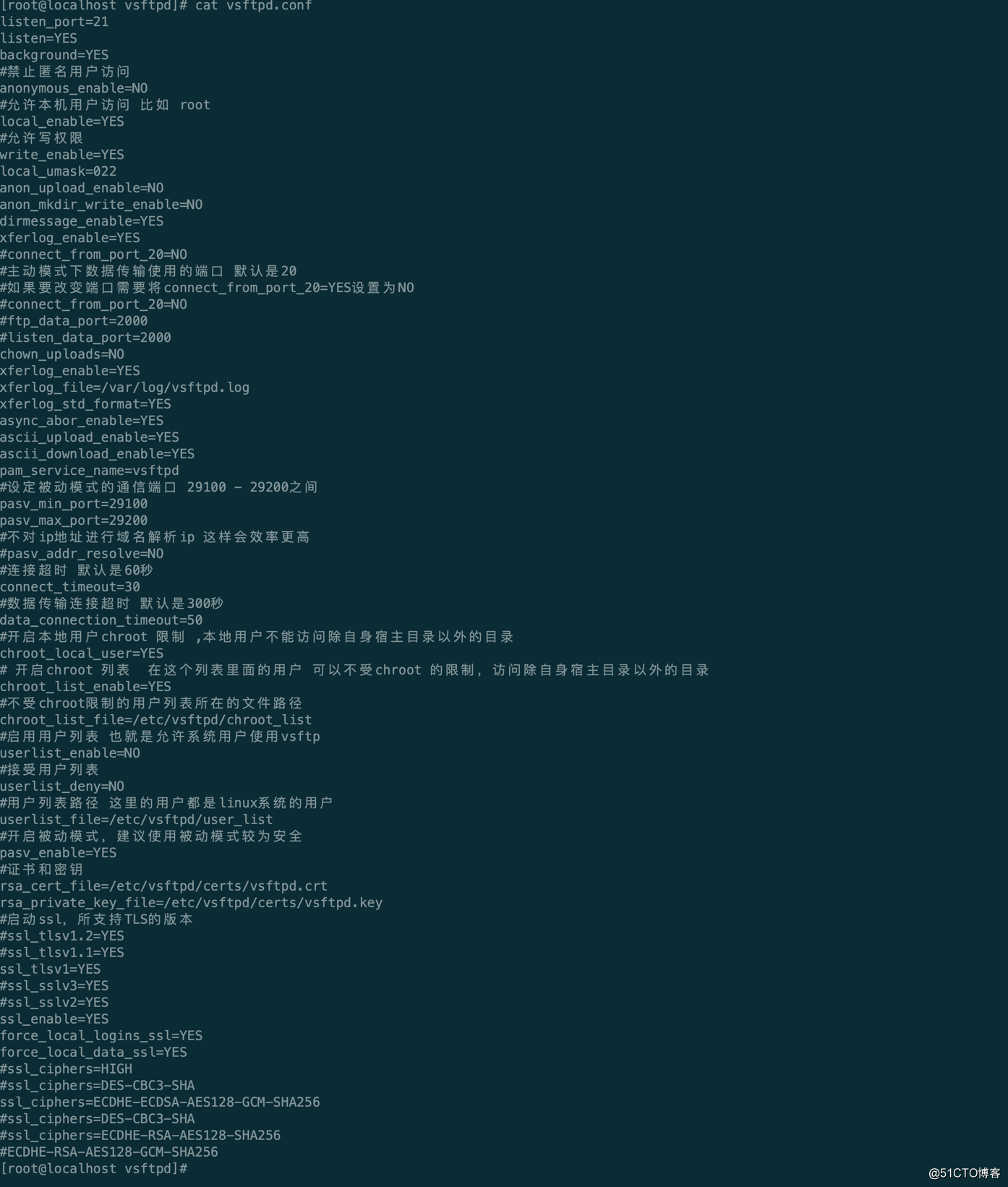
[root@localhost vsftpd]# vim vsftpd.conf
listen_port=21
listen=YES
background=YES
#禁止匿名用户访问
anonymous_enable=NO
#允许本机用户访问 比如 root
local_enable=YES
#允许写权限
write_enable=YES
local_umask=022
anon_upload_enable=NO
anon_mkdir_write_enable=NO
dirmessage_enable=YES
xferlog_enable=YES
#connect_from_port_20=NO
#主动模式下数据传输使用的端口 默认是20
#如果要改变端口需要将connect_from_port_20=YES设置为NO
#connect_from_port_20=NO
#ftp_data_port=2000
#listen_data_port=2000
chown_uploads=NO
xferlog_enable=YES
xferlog_file=/var/log/vsftpd.log
xferlog_std_format=YES
async_abor_enable=YES
ascii_upload_enable=YES
ascii_download_enable=YES
pam_service_name=vsftpd
#设定被动模式的通信端口 29100 - 29200之间
pasv_min_port=29100
pasv_max_port=29200
#不对ip地址进行域名解析ip 这样会效率更高
#pasv_addr_resolve=NO
#连接超时 默认是60秒
connect_timeout=30
#数据传输连接超时 默认是300秒
data_connection_timeout=50
#开启本地用户chroot 限制 ,本地用户不能访问除自身宿主目录以外的目录
chroot_local_user=YES
# 开启chroot 列表 在这个列表里面的用户 可以不受chroot 的限制,访问除自身宿主目录以外的目录
chroot_list_enable=YES
#不受chroot限制的用户列表所在的文件路径
chroot_list_file=/etc/vsftpd/chroot_list
#启用用户列表 也就是允许系统用户使用vsftp
userlist_enable=NO
#接受用户列表
userlist_deny=NO
#用户列表路径 这里的用户都是linux系统的用户
userlist_file=/etc/vsftpd/user_list
#开启被动模式,建议使用被动模式较为安全
pasv_enable=YES
#证书和密钥
rsa_cert_file=/etc/vsftpd/certs/vsftpd.crt
rsa_private_key_file=/etc/vsftpd/certs/vsftpd.key
#启动ssl,所支持TLS的版本
#ssl_tlsv1.2=YES
#ssl_tlsv1.1=YES
ssl_tlsv1=YES
#ssl_sslv3=YES
#ssl_sslv2=YES
ssl_enable=YES
force_local_logins_ssl=YES
force_local_data_ssl=YES
#ssl_ciphers=HIGH
#ssl_ciphers=DES-CBC3-SHA
ssl_ciphers=ECDHE-ECDSA-AES128-GCM-SHA256
#ssl_ciphers=DES-CBC3-SHA
#ssl_ciphers=ECDHE-RSA-AES128-SHA256
#ECDHE-RSA-AES128-GCM-SHA256
[root@www ~]# cd /usr/local/openssl/sub-CA/
[root@www sub-CA]# mkdir vsftp
[root@www sub-CA]# cd vsftp
[root@www vsftp]# openssl ecparam -genkey -name prime256v1 -out vsftpd.key
[root@www vsftp]# openssl req -new -key vsftpd.key -out vsftpd.csr -subj /C=CN/ST=BeiJing/L=BeiJing/O=A_company/OU=ftp/CN=vsftp01/[email protected]
[root@www vsftp]# ll
总用量 8
-rw-r--r--. 1 root root 509 12月 14 22:53 vsftpd.csr
-rw-------. 1 root root 302 12月 14 22:50 vsftpd.key
[root@www vsftp]# openssl ca -config ../sub-ca.cnf -extensions server_ext -in vsftpd.csr -out vsftpd.crt -md sha384 -days 120 -batch -notext
Using configuration from ../sub-ca.cnf
Enter pass phrase for /usr/local/openssl/sub-CA/private/second_cakey_ecdsa.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
88:40:ac:09:86:09:b6:19:9d:fa:33:71:f2:cb:f7:b1
Issuer:
countryName = CN
stateOrProvinceName = BeiJing
localityName = BeiJing
organizationName = A_company
organizationalUnitName = subca
commonName = sub01_CA
emailAddress = [email protected]
Validity
Not Before: Dec 14 14:58:20 2018 GMT
Not After : Apr 13 14:58:20 2019 GMT
Subject:
countryName = CN
stateOrProvinceName = BeiJing
localityName = BeiJing
organizationName = A_company
organizationalUnitName = ftp
commonName = vsftp01
emailAddress = [email protected]
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:27:f4:48:d2:79:5b:c5:f4:68:cb:00:47:d7:75:
0b:5a:f3:6b:42:89:a6:0e:f4:ac:c2:ca:06:34:58:
4d:d7:2e:97:f7:b6:c0:a8:71:2d:cd:65:26:11:cf:
a2:12:5a:f9:98:f5:45:32:5a:48:13:89:e2:55:67:
5a:c0:0c:be:09
ASN1 OID: prime256v1
NIST CURVE: P-256
X509v3 extensions:
Authority Information Access:
CA Issuers - URI:http://sub-ca.a-company.com/sub-ca.crt
OCSP - URI:http://ocsp.sub-ca.a-company.com:9081
X509v3 Authority Key Identifier:
keyid:9B:EC:B4:AF:12:B8:23:58:BC:12:86:8A:10:E2:5A:3C:B9:CA:2D:94
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 CRL Distribution Points:
Full Name:
URI:http://sub-ca.a-company.com/sub-ca.crl
X509v3 Extended Key Usage:
TLS Web Client Authentication, TLS Web Server Authentication
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Subject Key Identifier:
B8:5F:D2:09:EE:1F:76:64:A3:85:7F:67:95:3C:E0:4A:6C:A2:7B:97
Certificate is to be certified until Apr 13 14:58:20 2019 GMT (120 days)
Write out database with 1 new entries
Data Base Updated
[root@www vsftp]# ll
总用量 12
-rw-r--r--. 1 root root 1192 12月 14 22:58 vsftpd.crt
-rw-r--r--. 1 root root 509 12月 14 22:53 vsftpd.csr
-rw-------. 1 root root 302 12月 14 22:50 vsftpd.key
[root@www vsftp]# mv vsftpd.crt vsftpd.key /etc/vsftpd/cert/
[root@www vsftpd]# tshark -ni ens33 -Y "tcp.dstport eq 21"
67 15.046536662 172.16.216.1 -> 172.16.216.188 TCP 78 49635 > 21 [SYN, ECN, CWR] Seq=0 Win=65535 Len=0 MSS=1460 WS=64 TSval=282259949 TSecr=0 SACK_PERM=1
69 15.046669765 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=1 Ack=1 Win=131712 Len=0 TSval=282259949 TSecr=120440378
71 15.049437670 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=1 Ack=21 Win=131712 Len=0 TSval=282259952 TSecr=120440381
72 15.049866493 172.16.216.1 -> 172.16.216.188 FTP 76 Request: AUTH TLS
75 15.050351954 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=11 Ack=52 Win=131712 Len=0 TSval=282259952 TSecr=120440382
76 15.050362961 172.16.216.1 -> 172.16.216.188 FTP 583 Request: \026\003\001\002\000\001\000\001\374\003\003x4\224sB\257\262\376o
78 15.051263181 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=528 Ack=1180 Win=130560 Len=0 TSval=282259953 TSecr=120440383
79 15.051901324 172.16.216.1 -> 172.16.216.188 FTP 204 Request: \026\003\003\000\a\v\000\000\003\000\000\000\026\003\003\000F\020\000\000BA\004k\352%\273\367\271
81 15.052379356 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=666 Ack=1406 Win=130816 Len=0 TSval=282259954 TSecr=120440384
82 15.067241901 172.16.216.1 -> 172.16.216.188 FTP 103 Request: \027\003\003\000 \235~\b\315\327\340L\f\006\375\370\220\210\267A\252\365Y\245\254G\357"ja]nn\006\260\257\231
84 15.067498976 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=703 Ack=1455 Win=131008 Len=0 TSval=282259968 TSecr=120440399
85 15.067505380 172.16.216.1 -> 172.16.216.188 FTP 103 Request: \027\003\003\000 \235~\b\315\327\340L
87 15.067677376 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=740 Ack=1507 Win=131008 Len=0 TSval=282259968 TSecr=120440399
88 15.067813304 172.16.216.1 -> 172.16.216.188 FTP 108 Request: \027\003\003\000%\235~\b\315\327\340L\016\261l\225scz\361\200#\355\340a\330\v\tN\025)\005\266\272\354\255\331\242\207\240#a
90 15.067987300 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=782 Ack=1570 Win=131008 Len=0 TSval=282259968 TSecr=120440400
91 15.067992528 172.16.216.1 -> 172.16.216.188 FTP 108 Request: \027\003\003\000%\235~\b\315\327\340L\017oj\234\217\027>\376\311\321\312\241\261\215\270\2104\262_u\034v\3525\263\2767\372\315\274
96 15.142121329 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=824 Ack=1622 Win=131008 Len=0 TSval=282260042 TSecr=120440474
97 15.142339919 172.16.216.1 -> 172.16.216.188 FTP 101 Request: \027\003\003\000\036\235~\b\315\327\340L\020\376N1E\212\203\022\272\a]g<\320\002\203\305\223v\233\323\246@
100 15.142665222 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=859 Ack=1670 Win=131008 Len=0 TSval=282260042 TSecr=120440474
101 15.142770320 172.16.216.1 -> 172.16.216.188 FTP 100 Request: \027\003\003\000\035\235~\b\315\327\340L\021#\337\302\234\267\261\260\331\245#
103 15.142993988 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=893 Ack=1719 Win=131008 Len=0 TSval=282260042 TSecr=120440475
104 15.151674771 172.16.216.1 -> 172.16.216.188 FTP 101 Request: \027\003\003\000\036\235~\b\315\327\340L\0226(\324a:L\266w#p\032\017\337\351r\020n\347\341\356\251\313
110 15.153126677 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=1763 Win=131008 Len=0 TSval=282260052 TSecr=120440485
112 15.153307114 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=1803 Win=131008 Len=0 TSval=282260052 TSecr=120440485
114 15.153495253 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=1839 Win=131008 Len=0 TSval=282260052 TSecr=120440485
117 15.153714163 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=1875 Win=131008 Len=0 TSval=282260052 TSecr=120440485
118 15.153799916 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=1911 Win=131008 Len=0 TSval=282260053 TSecr=120440485
121 15.153971456 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=1947 Win=131008 Len=0 TSval=282260053 TSecr=120440486
123 15.154088504 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=1983 Win=131008 Len=0 TSval=282260053 TSecr=120440486
125 15.154205766 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=2019 Win=131008 Len=0 TSval=282260053 TSecr=120440486
127 15.154323155 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=2062 Win=131008 Len=0 TSval=282260053 TSecr=120440486
129 15.154439978 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=2098 Win=131008 Len=0 TSval=282260053 TSecr=120440486
131 15.154557241 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=2134 Win=131008 Len=0 TSval=282260053 TSecr=120440486
132 15.154623982 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=2170 Win=131008 Len=0 TSval=282260053 TSecr=120440486
134 15.154752307 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=928 Ack=2208 Win=131008 Len=0 TSval=282260054 TSecr=120440486
135 15.155433837 172.16.216.1 -> 172.16.216.188 FTP 101 Request: \027\003\003\000\036\235~\b\315\327\340L\023Vy\2512\272\266\257O9+>0R\205Y\031TJ\017\361\272\002
137 15.156175888 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=963 Ack=2290 Win=130944 Len=0 TSval=282260055 TSecr=120440488
141 15.156830014 172.16.216.1 -> 172.16.216.188 FTP 105 Request: \027\003\003\000"\235~\b\315\327\340L\024F\221\210\026Z\206\277\270\\334tJ\264\362`
143 15.157198433 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=1002 Ack=2358 Win=130944 Len=0 TSval=282260056 TSecr=120440489
158 15.160583796 172.16.216.1 -> 172.16.216.188 TCP 66 49635 > 21 [ACK] Seq=1002 Ack=2411 Win=131008 Len=0 TSval=282260058 TSecr=120440492
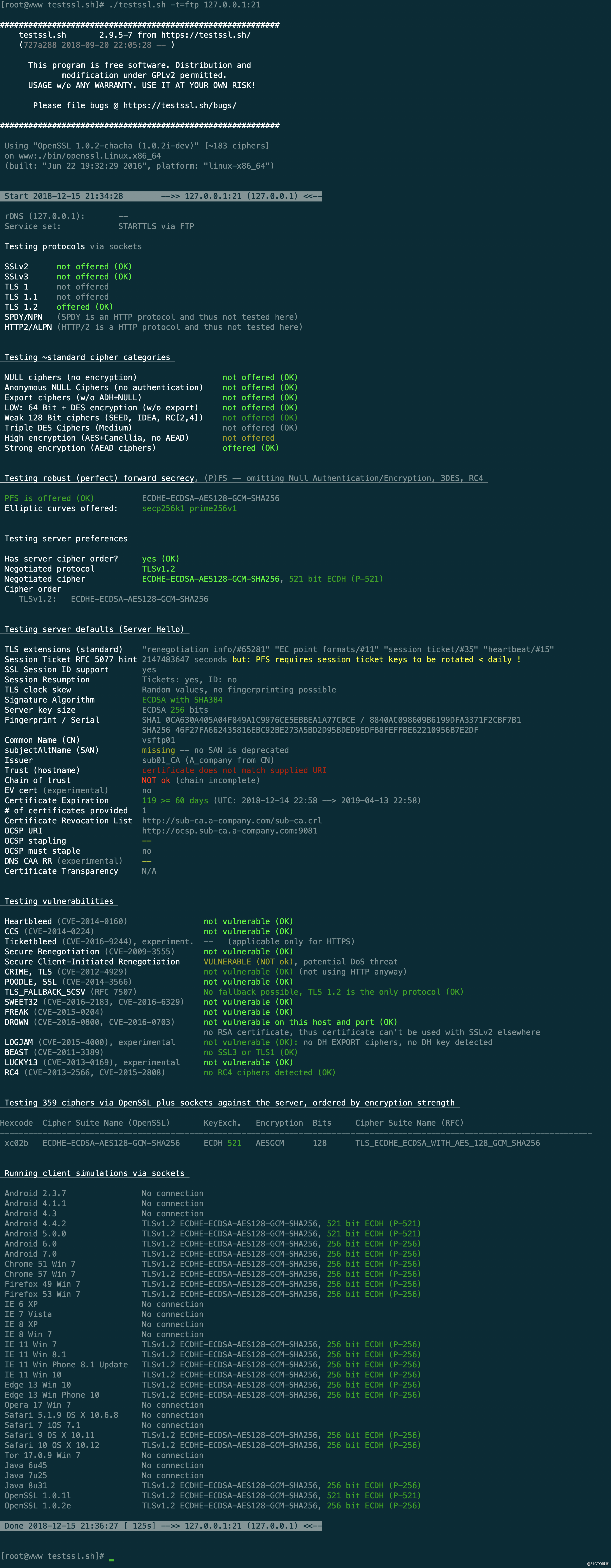
[root@www testssl.sh]# ./testssl.sh -t=ftp 127.0.0.1:21
###########################################################
testssl.sh 2.9.5-7 from https://testssl.sh/
(727a288 2018-09-20 22:05:28 -- )
This program is free software. Distribution and
modification under GPLv2 permitted.
USAGE w/o ANY WARRANTY. USE IT AT YOUR OWN RISK!
Please file bugs @ https://testssl.sh/bugs/
###########################################################
Using "OpenSSL 1.0.2-chacha (1.0.2i-dev)" [~183 ciphers]
on www:./bin/openssl.Linux.x86_64
(built: "Jun 22 19:32:29 2016", platform: "linux-x86_64")
Start 2018-12-15 21:34:28 -->> 127.0.0.1:21 (127.0.0.1) <<--
rDNS (127.0.0.1): --
Service set: STARTTLS via FTP
Testing protocols via sockets
SSLv2 not offered (OK)
SSLv3 not offered (OK)
TLS 1 not offered
TLS 1.1 not offered
TLS 1.2 offered (OK)
SPDY/NPN (SPDY is an HTTP protocol and thus not tested here)
HTTP2/ALPN (HTTP/2 is a HTTP protocol and thus not tested here)
Testing ~standard cipher categories
NULL ciphers (no encryption) not offered (OK)
Anonymous NULL Ciphers (no authentication) not offered (OK)
Export ciphers (w/o ADH+NULL) not offered (OK)
LOW: 64 Bit + DES encryption (w/o export) not offered (OK)
Weak 128 Bit ciphers (SEED, IDEA, RC[2,4]) not offered (OK)
Triple DES Ciphers (Medium) not offered (OK)
High encryption (AES+Camellia, no AEAD) not offered
Strong encryption (AEAD ciphers) offered (OK)
Testing robust (perfect) forward secrecy, (P)FS -- omitting Null Authentication/Encryption, 3DES, RC4
PFS is offered (OK) ECDHE-ECDSA-AES128-GCM-SHA256
Elliptic curves offered: secp256k1 prime256v1
Testing server preferences
Has server cipher order? yes (OK)
Negotiated protocol TLSv1.2
Negotiated cipher ECDHE-ECDSA-AES128-GCM-SHA256, 521 bit ECDH (P-521)
Cipher order
TLSv1.2: ECDHE-ECDSA-AES128-GCM-SHA256
Testing server defaults (Server Hello)
TLS extensions (standard) "renegotiation info/#65281" "EC point formats/#11" "session ticket/#35" "heartbeat/#15"
Session Ticket RFC 5077 hint 2147483647 seconds but: PFS requires session ticket keys to be rotated < daily !
SSL Session ID support yes
Session Resumption Tickets: yes, ID: no
TLS clock skew Random values, no fingerprinting possible
Signature Algorithm ECDSA with SHA384
Server key size ECDSA 256 bits
Fingerprint / Serial SHA1 0CA630A405A04F849A1C9976CE5EBBEA1A77CBCE / 8840AC098609B6199DFA3371F2CBF7B1
SHA256 46F27FA662435816EBC92BE273A5BD2D95BDED9EDFB8FEFFBE62210956B7E2DF
Common Name (CN) vsftp01
subjectAltName (SAN) missing -- no SAN is deprecated
Issuer sub01_CA (A_company from CN)
Trust (hostname) certificate does not match supplied URI
Chain of trust NOT ok (chain incomplete)
EV cert (experimental) no
Certificate Expiration 119 >= 60 days (UTC: 2018-12-14 22:58 --> 2019-04-13 22:58)
# of certificates provided 1
Certificate Revocation List http://sub-ca.a-company.com/sub-ca.crl
OCSP URI http://ocsp.sub-ca.a-company.com:9081
OCSP stapling --
OCSP must staple no
DNS CAA RR (experimental) --
Certificate Transparency N/A
Testing vulnerabilities
Heartbleed (CVE-2014-0160) not vulnerable (OK)
CCS (CVE-2014-0224) not vulnerable (OK)
Ticketbleed (CVE-2016-9244), experiment. -- (applicable only for HTTPS)
Secure Renegotiation (CVE-2009-3555) not vulnerable (OK)
Secure Client-Initiated Renegotiation VULNERABLE (NOT ok), potential DoS threat
CRIME, TLS (CVE-2012-4929) not vulnerable (OK) (not using HTTP anyway)
POODLE, SSL (CVE-2014-3566) not vulnerable (OK)
TLS_FALLBACK_SCSV (RFC 7507) No fallback possible, TLS 1.2 is the only protocol (OK)
SWEET32 (CVE-2016-2183, CVE-2016-6329) not vulnerable (OK)
FREAK (CVE-2015-0204) not vulnerable (OK)
DROWN (CVE-2016-0800, CVE-2016-0703) not vulnerable on this host and port (OK)
no RSA certificate, thus certificate can't be used with SSLv2 elsewhere
LOGJAM (CVE-2015-4000), experimental not vulnerable (OK): no DH EXPORT ciphers, no DH key detected
BEAST (CVE-2011-3389) no SSL3 or TLS1 (OK)
LUCKY13 (CVE-2013-0169), experimental not vulnerable (OK)
RC4 (CVE-2013-2566, CVE-2015-2808) no RC4 ciphers detected (OK)
Testing 359 ciphers via OpenSSL plus sockets against the server, ordered by encryption strength
Hexcode Cipher Suite Name (OpenSSL) KeyExch. Encryption Bits Cipher Suite Name (RFC)
-----------------------------------------------------------------------------------------------------------------------------
xc02b ECDHE-ECDSA-AES128-GCM-SHA256 ECDH 521 AESGCM 128 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
Running client simulations via sockets
Android 2.3.7 No connection
Android 4.1.1 No connection
Android 4.3 No connection
Android 4.4.2 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 521 bit ECDH (P-521)
Android 5.0.0 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 521 bit ECDH (P-521)
Android 6.0 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Android 7.0 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Chrome 51 Win 7 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Chrome 57 Win 7 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Firefox 49 Win 7 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Firefox 53 Win 7 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
IE 6 XP No connection
IE 7 Vista No connection
IE 8 XP No connection
IE 8 Win 7 No connection
IE 11 Win 7 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
IE 11 Win 8.1 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
IE 11 Win Phone 8.1 Update TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
IE 11 Win 10 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Edge 13 Win 10 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Edge 13 Win Phone 10 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Opera 17 Win 7 No connection
Safari 5.1.9 OS X 10.6.8 No connection
Safari 7 iOS 7.1 No connection
Safari 9 OS X 10.11 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Safari 10 OS X 10.12 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Tor 17.0.9 Win 7 No connection
Java 6u45 No connection
Java 7u25 No connection
Java 8u31 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
OpenSSL 1.0.1l TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 521 bit ECDH (P-521)
OpenSSL 1.0.2e TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Done 2018-12-15 21:36:27 [ 125s] -->> 127.0.0.1:21 (127.0.0.1) <<--