负载均衡配置
查看网站对应的ip地址工具dig
安装 yum install -y bind-utils
使用 dig www.163.com
设置163.com的两个地址为负债均衡
[root@test-a ~]# dig www.163.com
; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7_5.1 <<>> www.163.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 39731
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.163.com. IN A
;; ANSWER SECTION:
www.163.com. 535 IN CNAME www.163.com.lxdns.com.
www.163.com.lxdns.com. 46 IN A 116.242.0.145
www.163.com.lxdns.com. 46 IN A 60.207.246.98
;; Query time: 103 msec
;; SERVER: 119.29.29.29#53(119.29.29.29)
;; WHEN: Fri Nov 30 07:40:01 CST 2018
;; MSG SIZE rcvd: 104
# 配置
[root@test-a vhost]# vim load_balance.conf
[root@test-a vhost]# cat load_balance.conf
upstream 163
{
ip_hash;
server 116.242.0.145:80;
server 60.207.246.98:80;
}
server
{
listen 80;
server_name www.163.com;
location /
{
proxy_pass http://163;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forward-For $proxy_add_x_forwarded_for;
}
}
# 测试
[root@test-a vhost]# curl -x127.0.0.1:80 www.163.com
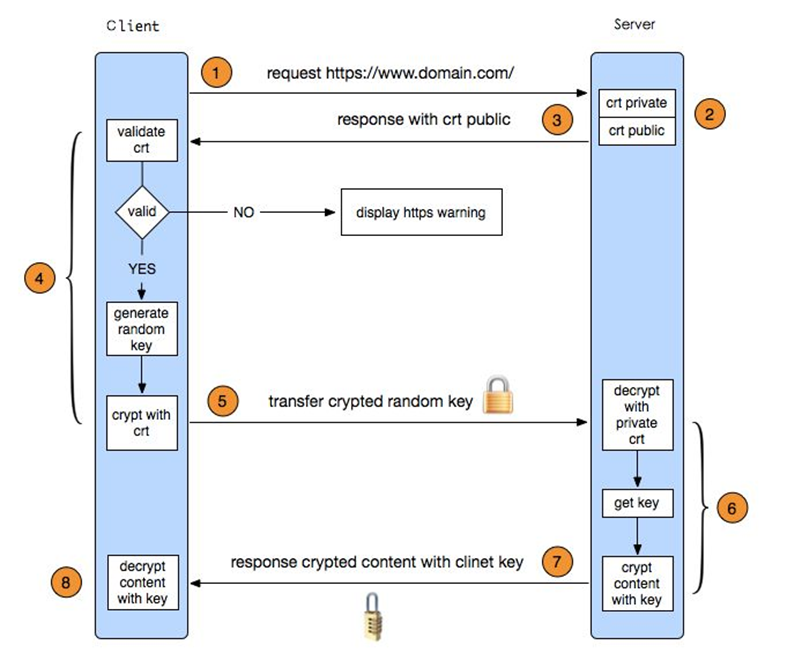
SSL工作流程
- 浏览器发送一个https的请求给服务器;
- 服务器要有一套数字证书,可以自己制作,也可以向组织申请,区别就是自己颁发的证书需要客户端验证通过,才可以继续访问,而使用受信任的公司申请的证书则不会弹出>提示页面,这套证书其实就是一对公钥和私钥;
- 服务器会把公钥传输给客户端;
- 客户端(浏览器)收到公钥后,会验证其是否合法有效,无效会有警告提醒,有效则会生成一串随机数,并用收到的公钥加密;
- 客户端把加密后的随机字符串传输给服务器;
- 服务器收到加密随机字符串后,先用私钥解密(公钥加密,私钥解密),获取到这一串随机数后,再用这串随机字符串加密传输的数据(该加密为对称加密,所谓对称加密,就是将数据和私钥也就是这个随机字符串>通过某种算法混合在一起,这样除非知道私钥,否则无法获取数据内容);
- 服务器把加密后的数据传输给客户端;
- 客户端收到数据后,再用自己的私钥也就是那个随机字符串解密;
利用openssl生成自己的证书
[root@test-a conf]# openssl genrsa -des3 -out tmp.key 2048 # 生成私钥文件tmp.key
Generating RSA private key, 2048 bit long modulus
.........................+++
.......................................+++
e is 65537 (0x10001)
Enter pass phrase for tmp.key:
Verifying - Enter pass phrase for tmp.key:
[root@test-a conf]# openssl rsa -in tmp.key -out mytest.key # 转换key,取消密码
Enter pass phrase for tmp.key:
writing RSA key
[root@test-a conf]# rm tmp.key
rm: remove regular file ‘tmp.key’? y
[root@test-a conf]# openssl req -new -key mytest.key -out mytest.csr # 生成证书请求文件,后面需要拿这个文件和私钥一起生产公钥文件
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:
Locality Name (eg, city) [Default City]:
Organization Name (eg, company) [Default Company Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@test-a conf]#
[root@test-a conf]# openssl x509 -req -days 365 -in mytest.csr -signkey mytest.key -out mytest.crt # 生成公钥
Signature ok
subject=/C=cn/L=Default City/O=Default Company Ltd
Getting Private key
[root@test-a conf]# ls mytest.*
mytest.crt mytest.csr mytest.key
[root@test-a vhost]# vim ssl.conf
[root@test-a vhost]# cat ssl.conf
server
{
listen 443;
server_name 12345.com;
index index.html index.php;
root /data/wwwroot/12345.com;
ssl on;
ssl_certificate mytest.crt;
ssl_certificate_key mytest.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
}
[root@test-a vhost]# /usr/local/nginx/sbin/nginx -t
nginx: [emerg] unknown directive "ssl" in /usr/local/nginx/conf/vhost/ssl.conf:7
nginx: configuration file /usr/local/nginx/conf/nginx.conf test failed
# 重新编译nginx,加上--with-http_ssl_module
[root@test-a vhost]# cd /usr/local/src/nginx-1.14.1/
[root@test-a nginx-1.14.1]# ./configure --prefix=/usr/local/nginx --with-http_ssl_module
[root@test-a nginx-1.14.1]# make
[root@test-a nginx-1.14.1]# make install
[root@test-a nginx-1.14.1]# /usr/local/nginx/sbin/nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful
[root@test-a nginx-1.14.1]# /usr/local/nginx/sbin/nginx -s reload
[root@test-a nginx-1.14.1]# /etc/init.d/nginx restart
Restarting nginx (via systemctl): [ OK ]
[root@test-a nginx-1.14.1]# netstat -nltp # 有443端口
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 2375/master
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 6105/nginx: master
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 6105/nginx: master
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1195/sshd
tcp6 0 0 ::1:25 :::* LISTEN 2375/master
tcp6 0 0 :::3306 :::* LISTEN 2402/mysqld
tcp6 0 0 :::22 :::* LISTEN 1195/sshd
[root@test-a nginx-1.14.1]# cd /data/wwwroot/ # 创建站点目录及文件
[root@test-a wwwroot]# mkdir 12345.com
[root@test-a wwwroot]# cd 12345.com/
[root@test-a 12345.com]# vim index.html
[root@test-a 12345.com]# cat index.html
SSL test.
[root@test-a 12345.com]# curl https://12345.com # 本地需要配置hosts
curl: (35) Encountered end of file
[root@test-a 12345.com]# cd /usr/local/nginx/conf/vhost/
[root@test-a vhost]# vim /etc/hosts
[root@test-a vhost]# curl https://12345.com # 访问提示证书不被信任,自己颁发的,肯定不被信任
curl: (60) Peer's certificate issuer has been marked as not trusted by the user.
More details here: http://curl.haxx.se/docs/sslcerts.html
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.
- 浏览器访问测试