检查openssl是否安装
![]()
openssl的相关目录:
/etc/pki/….
生成CA自签证书
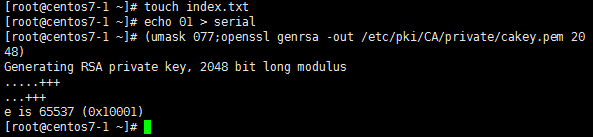
自签证书:
-new:生成新证书签署请求
-x509:专用CA生成自签证书
-key:生成请求时用到的私钥文件
-day n:证书的有效期限
-out /PATH/TO/SOMECERTFILE:证书的保存路径

Country Name (2 letter code) [XX]:CN------------国家
State or Province Name (full name)[]:HN---------省份
Locality Name (eg, city) [DefaultCity]:HB-------地区
Organization Name (eg, company)[Default Company Ltd]:MING------公司名称
Organizational Unit Name (eg,section) []:MING------公司的部门名称
Common Name (eg, your name or yourserver's hostname) []:CentOS7----CA服务器主机名
Email Address []:[email protected]管理员邮箱
初始化工作环境:
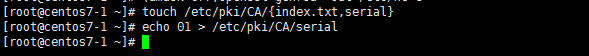
index.txt:索引文件,用于匹配证书编号;
serial:证书序列号文件,只在首次生成证书时赋值。
颁发证书过程:
a、用到证书的主机生成证书请求
#(umask 077; openssl genrsa -out /etc/httpd/ssl/httpd.key 2048)
#openssl req -new -x509 -key /etc/httpd/ssl/httpd.key -days 365 -out /etc/httpd/ssl/httpd.csr
b、把请求文件传输给CA
c、CA签署证书,并把证书发还给请求者
(https加密,在httpd创建ssl,生成申请,然后注册证书)
拷贝到CA服务器后:
签署:openssl ca -in /ca存放位置.csr -out /输出审核ca.crt -days 365 (签署天数)
xxx.crt的传输给客户端
证书的后缀是CRT
查看证书内的信息:
openssl x509 -in /PATH/FROM/CERT_FILE -noout -text [-subject]-serial
4、吊销证书:
a、获取吊销证书的serial
#openssl x509 -in /PATH/FROM/CERT_FILE -noout -serial -subject
b、CA服务器
先根据客户端提交的serial与 subject信息,对比检验是否index.txt文件中的信息是否一致
吊销证书:
openssl ca -revoke /etc/pki/CA/newcerts/SERIAL.pem
c、生成吊销证书编号(第一次吊销一个证书)
# echo 01 > /etc/pki/CA/crlnumber
d、更新证书吊销列表:
# openssl ca -gencrl -out thisca.crl
查看crl文件
# openssl crl -in /PATH/FROM/CRL_FILE.crl -noout –text
一次CA搭建到申请审批的完整过程:
cd /etc/pki/CA/
touch index.txt
echo 01 > serial
(umask 077; openssl genrsa -out private/cakey.pem 2048 )
openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 7300 -out /etc/pki/CA/cacert.pem
mkdir -p /etc/httpd/ssl/
cd /etc/httpd/ssl/
(umask 077; openssl genrsa -out /etc/httpd/ssl/httpd.key 2048)
openssl req -new -key httpd.key -days 365 -out httpd.csr
openssl ca -in httpd.csr -out httpd.crt -days 365