版权声明:知识就是为了传播! https://blog.csdn.net/weixin_36171533/article/details/82746418
基于canel的网络策略
canel工作的默认网段是192.168.0.0/16的网段
官网:https://docs.projectcalico.org/v3.2/introduction/
参考地址:
https://docs.projectcalico.org/v3.2/getting-started/kubernetes/installation/flannel
分别运行:
kubectl apply -f \
https://docs.projectcalico.org/v3.2/getting-started/kubernetes/installation/hosted/canal/rbac.yaml
kubectl apply -f \
https://docs.projectcalico.org/v3.2/getting-started/kubernetes/installation/hosted/canal/canal.yaml
监控:
kubectl get pods -n kube-system -w
[root@master ~]# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
canal-98mcn 3/3 Running 0 3m
canal-gnp5r 3/3 Running 0 3m
coredns-78fcdf6894-27npt 1/1 Running 1 12d
coredns-78fcdf6894-mbg8n 1/1 Running 1 12d
etcd-master 1/1 Running 1 12d
kube-apiserver-master 1/1 Running 1 12d
kube-controller-manager-master 1/1 Running 1 12d
kube-flannel-ds-amd64-6ws6q 1/1 Running 0 1h
kube-flannel-ds-amd64-mg9sm 1/1 Running 0 1h
kube-flannel-ds-amd64-sq9wj 1/1 Running 0 1h
kube-proxy-g9n4d 1/1 Running 1 12d
kube-proxy-wrqt8 1/1 Running 2 12d
kube-proxy-x7vc2 1/1 Running 0 12d
kube-scheduler-master 1/1 Running 1 12d
kubernetes-dashboard-767dc7d4d-7rmp8 1/1 Running 0 2d查看帮助:
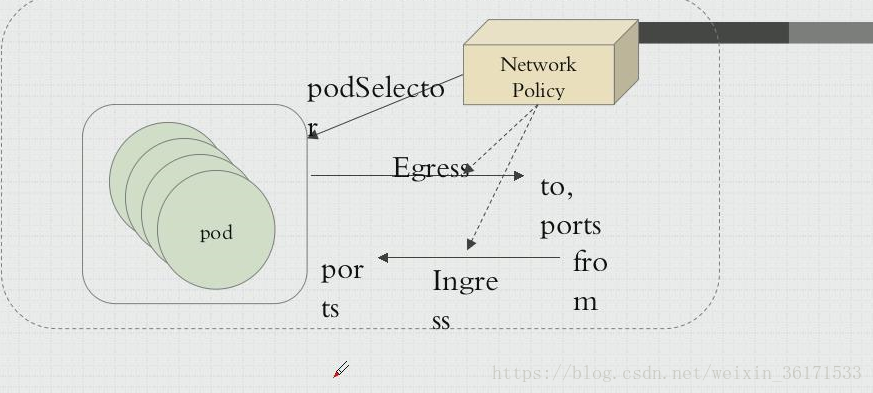
kubectl explain networkpolicy.spec
网络策略:
名称空间:
拒绝所有的出站,入站。
放行所有出站目标本名称空间内的所有Pod
开始试验:
[root@master networkpolicy]# kubectl create namespace dev
namespace/dev created
[root@master networkpolicy]# kubectl create namespace prod
namespace/prod created
创建yaml文件
[root@master networkpolicy]# cat ingres-def.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all-ingress
#namespace: dev
spec:
podSelector: {} #空选择器代表命苦空间所有的Pod
policyTypes:
- Ingress
#如果不写Ingress的话,默认都可以访问
#如果写上Ingress的话,默认都不能访问
[root@master networkpolicy]# kubectl apply -f ingres-def.yaml -n dev
networkpolicy.networking.k8s.io/deny-all-ingress created
-n 是指定的名称空间dev
[root@master networkpolicy]# kubectl get netpol -n dev
NAME POD-SELECTOR AGE
deny-all-ingress <none> 39s
创建一个web yaml
[root@master networkpolicy]# vim pod-a.yaml
[root@master networkpolicy]# kubectl apply -f pod-a.yaml -n dev
pod/pod1 created
[root@master networkpolicy]# cat pod-a.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod1
spec:
containers:
- name: myapp
image: ikubernetes/myapp:v1
[root@master networkpolicy]# kubectl get pods
No resources found.
[root@master networkpolicy]# kubectl get pods -n dev
NAME READY STATUS RESTARTS AGE
pod1 1/1 Running 0 50s
[root@master networkpolicy]# kubectl get pods -n dev -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE
pod1 1/1 Running 0 1m 10.244.2.2 node2 <none>
[root@master networkpolicy]# curl 10.244.2.2
发现是访问不了的
更换一下名称空间:
[root@master networkpolicy]# kubectl apply -f pod-a.yaml -n prod
pod/pod1 created
[root@master networkpolicy]# kubectl get pods -n prod
NAME READY STATUS RESTARTS AGE
pod1 1/1 Running 0 8s
[root@master networkpolicy]# kubectl get pods -n prod -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE
pod1 1/1 Running 0 13s 10.244.1.2 node1 <none>
[root@master networkpolicy]# curl 10.244.1.2
Hello MyApp | Version: v1 | <a href="hostname.html">Pod Name</a>
发现是可以访问的
因为在dev中Ingress中定义了不能访问
[root@master networkpolicy]# kubectl get pods -n prod -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE
pod1 1/1 Running 0 3m 10.244.1.2 node1 <none>
[root@master networkpolicy]# kubectl get pods -n dev -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE
pod1 1/1 Running 0 7m 10.244.2.2 node2 <none>
可以看出,prod和dev不同的命名空间都有一个pods
[root@master networkpolicy]# curl 10.244.1.2 #可以
Hello MyApp | Version: v1 | <a href="hostname.html">Pod Name</a>
[root@master networkpolicy]# curl 10.244.2.2 #NO
^C
现在放行2.2
dev是默认拒绝一切规则的,他可以请求别人
[root@master networkpolicy]# vim ingres-def.yaml
[root@master networkpolicy]# kubectl apply -f ingres-def.yaml -n dev
networkpolicy.networking.k8s.io/deny-all-ingress configured
[root@master networkpolicy]# cat ingres-def.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all-ingress
#namespace: dev
spec:
podSelector: {} #空选择器代表命苦空间所有的Pod
ingress:
- {} #允许所有的入栈规则
policyTypes:
- Ingress
#如果不写Ingress的话,默认都可以访问
#如果写上Ingress的话,默认都不能访问
再次访问:
[root@master networkpolicy]# curl 10.244.2.2
Hello MyApp | Version: v1 | <a href="hostname.html">Pod Name</a>
可以访问了
打一个标签,可以设置标签为myapp的特定访问
kubectl label pods pod1 app=myapp -n dev
[root@master networkpolicy]# kubectl label pods pod1 app=myapp -n dev
pod/pod1 labeled
[root@master networkpolicy]# cat allow-netpol-demo.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-myapp-ingress
spec:
podSelector:
matchLabels:
app: myapp
ingress:
- from:
- ipBlock: #ip 网段
cidr: 10.244.0.0/16 #排除的网段
except:
- 10.244.1.2/32 #允许的网段
ports:
- protocol: TCP
port: 80
[root@master networkpolicy]# kubectl apply -f allow-netpol-demo.yaml -n dev
networkpolicy.networking.k8s.io/allow-myapp-ingress created
[root@master networkpolicy]# kubectl get netpol -n dev
NAME POD-SELECTOR AGE
allow-myapp-ingress app=myapp 2m
deny-all-ingress <none> 36m
[root@master networkpolicy]# curl 10.244.2.2
Hello MyApp | Version: v1 | <a href="hostname.html">Pod Name</a>
生效了#允许出战
[root@master networkpolicy]# vim egress-def.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all-egress
spec:
podSelector: {}
egress:
- {}
policyTypes:
- Egress
#拒绝出站
[root@master networkpolicy]# vim egress-def.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all-egress
spec:
podSelector: {}
policyTypes:
- Egress