Telnet使用明文密码,在网络上传输是非常不安全的,尤其是远程穿越Internet访问。
为了远程控制的安全性,推荐使用SSH技术, SSH是英文Secure Shell的简写。通过使用SSH,可以对数据传输进行加密,这样“中间人”***方式就不能实现了,
捕获的数据包也是RSA加密后的数据包。
SSH 是基于TCP协议,端口号为22.
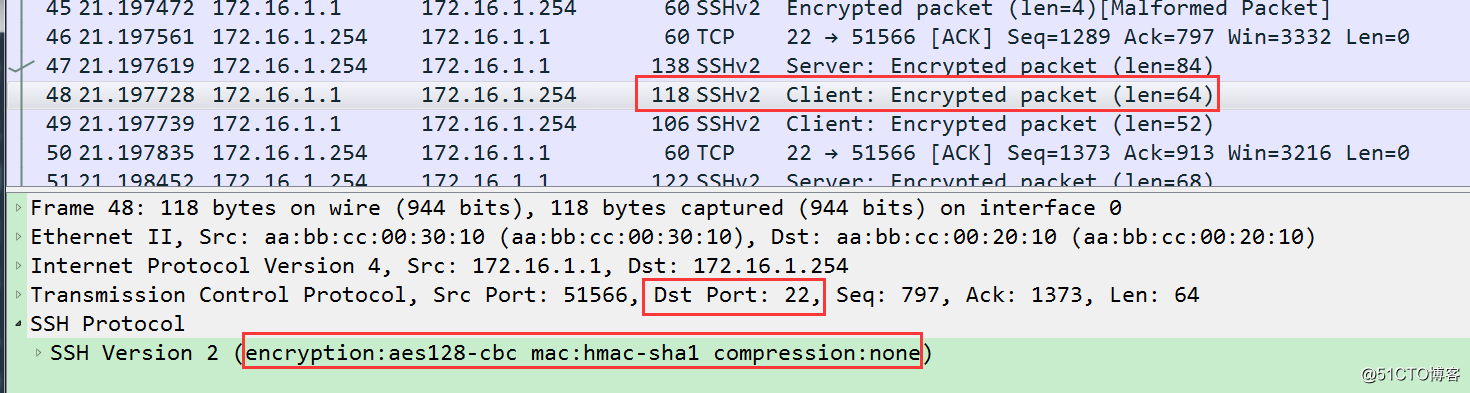
SSH配置:
拓扑:
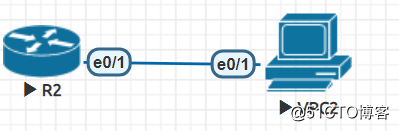
Router(config)#host R2
R2(config)#int e0/1
R2(config-if)#ip add 172.16.1.254 255.255.255.0
R2(config-if)#no shut
Router(config)#host VPC2 //路由器模拟器PC
VPC2(config)#no ip routing
VPC2(config)#ip default-gateway 172.16.1.254
VPC2(config)#int e0/1
VPC2(config-if)#ip add 172.16.1.1 255.255.255.0
VPC2(config-if)#no shuto shut
R2(config)#ip domain name qytang.com //先创建域名
R2(config)#crypto key generate rsa //创建RSA key
The name for the keys will be: R2.qytang.com
Choose the size of the key modulus in the range of 360 to 4096 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take
a few minutes.
How many bits in the modulus [512]: 1024 //输入1024
% Generating 1024 bit RSA keys, keys will be non-exportable...
[OK] (elapsed time was 0 seconds)
R2(config)#
*Oct 27 08:24:16.401: %SSH-5-ENABLED: SSH 1.99 has been enabled
R2(config)#ip ssh version 2 //设置版本为v2
R2(config)#ip ssh logging events //当有ssh有登录时,有日志事件
R2(config)#ip ssh maxstartups 5 //最大允许五个用户
R2(config)#access-list 10 permit host 172.16.1.1 //设置访问列表,只允许匹配到的地址访问
R2(config)#username qytang password cisco //创建本地用户数据库
R2(config)#line vty 0 4
R2(config-line)#transport input ssh //只允许SSH登录
R2(config-line)#login local //用本地用户名和数据库登录
R2(config-line)#access-class 10 in //调用ACL
R2(config-line)#exit
测试;
VPC2#ssh -l qytang 172.16.1.254 //客户端测试
Password:
R2>
R2#
*Oct 27 08:29:47.750: %SSH-5-SSH2_SESSION: SSH2 Session request from 172.16.1.1 (tty = 0) using crypto cipher 'aes128-cbc', hmac 'hmac-sha1' Succeeded
R2#
*Oct 27 08:30:01.428: %SSH-5-SSH2_USERAUTH: User 'qytang' authentication for SSH2 Session from 172.16.1.1 (tty = 0) using crypto cipher 'aes128-cbc', hmac 'hmac-sha1' Succeeded
R2#show users //查看在线用户
Line User Host(s) Idle Location
* 0 con 0 idle 00:00:00
2 vty 0 qytang idle 00:00:36 172.16.1.1
Interface User Mode Idle Peer Address
R2#show ssh
Connection Version Mode Encryption Hmac State Username
0 1.99 IN aes128-cbc hmac-sha1 Session started qytang
0 1.99 OUT aes128-cbc hmac-sha1 Session started qytang
%No SSHv1 server connections running.
R2#show ip access-lists
Standard IP access list 10
10 permit 172.16.1.1 (2 matches)
R2>show priv
Current privilege level is 1