介绍:对称加密和非对称加密,CA证书申请实验
目录
gpg工具
gpg工具对称加密命令
[root@centos7:app]# cp /etc/fstab .
[root@centos7:app]# ls
fstab
[root@centos7:app]# gpg -c fstab #对称加密文件
[root@centos7:app]# ls
fstab fstab.gpg
[root@centos7:app]# cat fstab.gpg #加密后的文字如下
(◔㊀a@ Ѭba↑
yۘ&>ձ¢¬µˮ㒄\®,¦Rб¤Ȗ£»І&6Wϰ.·ƝAU=TϋϟÔX,¯5<»ӗƦK$ʑuߩ~
떘Z¨˖D.긚´;QG룯Pҟ3¾2~ґ}i Wv3뒓ª$微2-=¦}ę±IbqG㻾糍槅ߨ¯Jjt²²¨Oar²ا|5姎ւn캛
[root@centos7:app]# scp fstab.gpg 172.18.119.213:/app
[root@centos6:app]# file fstab.gpg
fstab.gpg: data
[root@centos6 app ]#gpg -d fstab.gpg #输入密码,输出到终端
gpg: CAST5 encrypted data
***省略***
[root@centos6 app ]#gpg -o fstab -d fstab.gpg #输入密码,解开文件fstab.gpg为fstab,
[root@centos6 app ]#gpg -d fstab.gpg > fstab #同上gpg工具非对称加密命令
gpg --gen-key
[root@centos7 app ]#gpg --gen-key
gpg (GnuPG) 2.0.14; Copyright (C) 2009 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
[root@centos7:app]# gpg --list-keys
/root/.gnupg/pubring.gpg
------------------------
pub 1024R/32F67C1F 2018-07-10
uid zhaoliying (yingbaobao)
sub 1024R/E8F9B8C9 2018-07-10
[root@centos7:.gnupg]# gpg -a --export -o zhaoliying.pubkey #生成公钥
[root@centos7:.gnupg]# cat zhaoliying.pubkey
-----BEGIN PGP PUBLIC KEY BLOCK----
mI0EW0RpsQEEAKj+M9wEq/FYic64o5SaqDtTaqo+Hywg6dLklBKVIV1Hvg8nZRVd
***省略***
[root@centos7:.gnupg]# gpg --help
a, --armor create ascii armored output
***省略***
[root@centos7:.gnupg]# scp zhaoliying.pubkey 172.18.119.213:
[root@centos6 app ]#cp /root/zhaoliying.pubkey .
[root@centos6 app ]#ls
zhaoliying.pubkey
[root@centos6 app ]#gpg --gen-key # 如图1生成一个非对称密钥
gpg (GnuPG) 2.0.14; Copyright (C) 2009 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection?
图1
[root@centos6 app ]#gpg --list-keys
/root/.gnupg/pubring.gpg
------------------------
pub 1024R/C27FA3BD 2018-07-10
uid dhyhaha
sub 1024R/84AE51FE 2018-07-10
[root@centos6 app ]#gpg --import zhaoliying.pubkey #复制公钥到centos6,并导入centos7生成的非对称密钥的公钥
gpg: key 32F67C1F: public key "zhaoliying
(yingbaobao)" imported
gpg: Total number proce确定ssed: 1
gpg: imported: 1 (RSA: 1)
[root@centos6 app ]#gpg --list-keys #列出centos6上的两个公钥
/root/.gnupg/pubring.gpg
------------------------
pub 1024R/C27FA3BD 2018-07-10
uid dhyhaha
sub 1024R/84AE51FE 2018-07-10
pub 1024R/32F67C1F 2018-07-10
uid zhaoliying (yingbaobao)
sub 1024R/E8F9B8C9 2018-07-10
[root@centos6 app ]#gpg -e -r zhaoliying /etc/fstab #利用centos7上生成的zhaoliying公钥加密文件/et/fstab
gpg: E8F9B8C9: There is no assurance this key belongs to the named user
pub 1024R/E8F9B8C9 2018-07-10 zhaoliying (yingbaobao)
Primary key fingerprint: FBA4 2689 9797 0B65 B0D2 2C57 DD56 F4C7 32F6 7C1F
Subkey fingerprint: D165 9324 44CC 8811 453E F9CE 7F55 CD40 E8F9 B8C9
It is NOT certain that the key belongs to the person named
in the user ID. If you *really* know what you are doing,
you may answer the next question with yes.
Use this key anyway? (y/N)
[root@centos6 app ]#cp /etc/fstab.gpg . #利用centos7上的公钥加密后的fstab.gpg
[root@centos6 app ]#ls
fstab.gpg zhaoliying.pubkey
[root@centos6 app ]#scp fstab.gpg 172.18.119.212: #把centos6加密的文件fstab.gpg复制到centos7家目录下
[email protected]'s password:
fstab.gpg 100% 646 0.6KB/s 00:00
[root@centos
[root@centos7:~]# gpg -d fstab.gpg #利用centos7的私钥解密
[root@centos7:~]# ls
anaconda-ks.cfg Downloads fstab.gpg phone.sh Public Videos
Desktop findresults initial-setup-ks.cfg phone.txt secure
Documents fs
[root@centos6 app ]#gpg --delete-keys zhaoliying #centos6上删除centos7复制过来的公钥
gpg (GnuPG) 2.0.14; Copyright (C) 2009 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
pub 1024R/32F67C1F 2018-07-10 zhaoliying (yingbaobao)
Delete this key from the keyring? (y/N) y
[root@centos6 app ]#gpg --delete-keys dhyhaha #删除centos6上生成的公钥
gpg (GnuPG) 2.0.14; Copyright (C) 2009 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
gpg: there is a secret key for public key "dhyhaha"!
gpg: use option "--delete-secret-keys" to delete it first.
[root@centos6 app ]#gpg --delete-secret-keys dhyhaha
gpg (GnuPG) 2.0.14; Copyright (C) 2009 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
sec 1024R/C27FA3BD 2018-07-10 dhyhaha
Delete this key from the keyring? (y/N) y
This is a secret key! - really delete? (y/N) y
openssl:开源项目成果
openssl包
[root@centos7:~]# rpm -qi openssl
[root@centos7:~]# rpm -ql openssl
openssl --help
salt 盐 ,enc加密命令
对称加密算法enc命令
#对称加密算法des加密fstab,并且加入盐salt,输出文件起名为fstab.des3
[root@centos7:app]# openssl enc -e -des3 -a -salt -in fstab -out fstab.des3
enter des-ede3-cbc encryption password:
Verifying - enter des-ede3-cbc encryption password:
[root@centos7:app]# ls
fstab fstab.des3 fstab.gpg
#解密用对称加密算法des3加密的文件fstab.des3,解密后的文件名为fstab2
[root@centos7:app]# openssl enc -d -des3 -a -salt -in fstab.des3 -out fstab2
enter des-ede3-cbc decryption password:
[root@centos7:app]# ls
fstab fstab2 fstab.des3 fstab.gpg
#用Openssl 的命令dgst加密(算法有sha1,md5)
[root@centos7:app]# openssl dgst -sha1 fstab
SHA1(fstab)= cbdc030fee1ee7abdfc7b1793dcd7a35a9919722
[root@centos7:app]# sha1sum fstab
cbdc030fee1ee7abdfc7b1793dcd7a35a9919722 fstab生成密码passwd命令
[root@centos7:app]# openssl --help
[root@centos7:app]# man sslpasswd
#openssl中的命令passwd用户生成密码,1表示md5加密算法
[root@centos7:app]# openssl passwd -1
Password:
Verifying - Password:
$1$Kc/klHcV$x6RxdAOD6ULF5XRwELDr50
#$1 表示MD5
[root@centos6 ~ ]#grub-crypt #sha512加密算法,生成的密码中$6表示sha512算法
Password:
Retype password:
$6$lvBKG2qZI6zLU8wY$/62YiF2Uc3qNymNP9HCERE/7w8xFo8NsxR8UAWQo09rMRsO7K/POC3ONNeV6OT7ZyYvwEqYd8X.myemcCTYXX/
[root@centos7:app]# openssl rand -hex 2
ad16
随机生成口令,不太好
[root@centos7:app]# openssl rand -base64 6
QFK9Atiz
只要后面跟的是3的倍数,则不会有=号 base64转换对照表可以百度
[root@centos7:app]# openssl rand -base64 4
0JL8VA==
[root@centos7:app]# openssl rand -base64 20 | tr -d '+=/' | head -c8|xargs
vM9F7ue7随机数生成设备
[root@centos7:data]# ll /dev/random /dev/urandom
crw-rw-rw-. 1 root root 1, 8 Jul 10 09:05 /dev/random
crw-rw-rw-. 1 root root 1, 9 Jul 10 09:05 /dev/urandom
[root@centos7:data]# cat /dev/urandom | tr -dc '[:alnum:]'|head -c8
非对称加密算法genrsa命令
#rsa算法生成一个私钥test.key
[root@centos7:data]# openssl genrsa -out test.key 2048
Generating RSA private key, 2048 bit long modulus
.......................................................+++
............................................................................+++
e is 65537 (0x10001)
#rsa算法生成一个私钥test2.key,并用des加密私钥
[root@centos7:data]# openssl genrsa -out test2.key -des 1024
Generating RSA private key, 1024 bit long modulus
................++++++
...++++++
e is 65537 (0x10001)
Enter pass phrase for test2.key:
Verifying - Enter pass phrase for test2.key:
#生成私钥文件的权限为600,且是在子shell中运行,不影响当前shell的umask值
[root@centos7:data]# ( umask 066 ;openssl genrsa -out test3.key 1024)
Generating RSA private key, 1024 bit long modulus
..............++++++
...........++++++
e is 65537 (0x10001)
[root@centos7:data]# ll
total 12
-rw-r--r--. 1 root root 958 Jul 10 21:05 test2.key
-rw-------. 1 root root 891 Jul 10 21:06 test3.key
-rw-r--r--. 1 root root 1679 Jul 10 21:05 test.key
#私钥test2.key被加密了,此处解密私钥test2.key ,并起名为test22.ky
[root@centos7:data]# openssl rsa -in test2.key -out test22.ky
Enter pass phrase for test2.key:
writing RSA key
[root@centos7:data]# ll
total 16
-rw-r--r--. 1 root root 887 Jul 10 21:07 test22.ky #test22.ky与test2.key内容相同
-rw-r--r--. 1 root root 958 Jul 10 21:05 test2.key
-rw-------. 1 root root 891 Jul 10 21:06 test3.key
-rw-r--r--. 1 root root 1679 Jul 10 21:05 test.key
#导出公钥
[root@centos7:data]# openssl rsa -in test22.ky -pubout -out test22.pubkey
writing RSA key
[root@centos7:data]# openssl rsa -in test.key -pubout -out test.pubkey
writing RSA keyCA证书的搭建
实验:实现证书的申请
1 在CA主机:CA建立
cd /etc/pki/CA
(umask 066;openssl genrsa -out private/cakey.pem 2048)
openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650
touch index.txt
echo 01 > serial
2 在客户端主机上:申请
cd /app
(umask 066;openssl genrsa -out app.key 2048)
openssl req -new -key app.key -out app.csr
3 在CA主机上:颁发证书
cd /etc/pki/CA
openssl ca -in app.csr -out app.cer -days 300
1、服务器自签名证书
[root@centos7:tls]# pwd
/etc/pki/tls
[root@centos7:tls]# ls
cert.pem certs misc openssl.cnf private
#配置文件
[root@centos7:tls]# cat openssl.cnf
####################################################################
[ CA_default ]
dir = /etc/pki/CA # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file. 存放颁发证书的信息
#unique_subject = no # Set to 'no' to allow creation of
一个主题是否允许申请多个证书,默认不允许 # several ctificates with same subject.
new_certs_dir = $dir/newcerts # default place for new certs.
certificate = $dir/cacert.pem # The CA certificate
#CA的顶级证书
serial = $dir/serial # The current serial number ;颁发的证书编号,显示的是下一个申请的证书编号
crlnumber = $dir/crlnumber # the current crl number ;要被吊销证书编号,与颁发证书的编号没有关系
# must be commented out to leave a V1 CRL
crl = $dir/crl.pem # The current CRL
#吊销证书的路径
private_key = $dir/private/cakey.pem# The private key
RANDFILE = $dir/private/.rand # private random number file 随机文件
x509_extensions = usr_cert # The extentions to add to the cert 证书标准格式
***省略***
# For the CA policy
[ policy_match ] #匹配规则可改 policy =plicy_anything
countryName = match #国家
stateOrProvinceName = match #省,州 ,可改为optional不匹配也可以(客户申请信息和此处不同)
organizationName = match #组织
organizationalUnitName = optional
commonName = supplied #主机名称
emailAddress = optional #邮箱
------------------------------------------------------
#生成私钥,并对私钥用des3加密,生成的2048位私钥cakey.pem
[root@centos7:CA]# openssl genrsa -out private/cakey.pem -des3 2048
#x509表示自签名证书,用私钥cakey.pem签名证书生成cacert.pem
[root@centos7:CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365
Enter pass phrase for private/cakey.pem:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:dhydu
Organization Name (eg, company) [Default Company Ltd]:dhyduorg
Organizational Unit Name (eg, section) []:opt
Common Name (eg, your name or your server's hostname) []:www.baidu.com
Email Address []:
#查看生成的证书cacert.pem有专门的命令
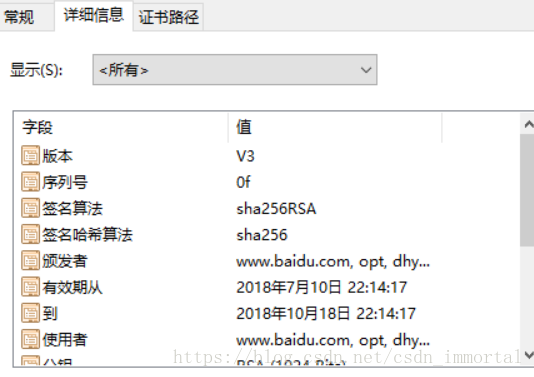
[root@centos7:CA]# openssl x509 -in cacert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
89:33:f9:89:39:b7:2f:df
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=beijing, L=dhydu, O=dhyduorg, OU=opt, CN=www.baidu.com
Validity
Not Before: Jul 10 14:08:12 2018 GMT
Not After : Jul 10 14:08:12 2019 GMT
*******省略
[root@centos7:CA]# sz cacert.pem
导出到windows10桌面,更改后缀为cer ,如图2
图2
2、客户端软件申请证书
#生成1024位私钥app.key
[root@centos6 app ]#(umask 066;openssl genrsa -out app.key 1024)
Generating RSA private key, 1024 bit long modulus
...............++++++
..........................................................++++++
e is 65537 (0x10001)
[root@centos6 app ]#ll
total 4
-rw-------. 1 root root 887 Jul 10 22:33 app.key
#生成向CA机构申请证书的文件app.csr
[root@centos6 app ]#openssl req -new -key app.key -out app.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:dhydu
Organization Name (eg, company) [Default Company Ltd]:dhyduorg
Organizational Unit Name (eg, section) []:opt
Common Name (eg, your name or your server's hostname) []:www.baidu.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:centos
An optional company name []:
[root@centos6 app ]#
[root@centos6 app ]#ll
total 8
-rw-r--r--. 1 root root 619 Jul 10 22:36 app.csr
-rw-------. 1 root root 887 Jul 10 22:33 app.key
#把申请证书文件传到centos7上
[root@centos6 app ]#scp app.csr 172.18.119.212:/etc/pki/CA
[email protected]'s password:
app.csr 100% 619 0.6KB/s 00:00
#centos7颁发证书,需要事先准备两个文件index,否则会报错,可根据报错解决
[root@centos7:CA]#touch index.txt
[root@centos7:CA]#echo 0F > serial
#颁发证书,有效期100天
[root@centos7:CA]# openssl ca -in app.csr -out app.cer -days 100
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for /etc/pki/CA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 15 (0xf)
Validity
Not Before: Jul 10 14:14:17 2018 GMT
Not After : Oct 18 14:14:17 2018 GMT
Subject:
countryName = CN
stateOrProvinceName = beijing
organizationName = dhyduorg
organizationalUnitName = opt
commonName = www.baidu.com
[root@centos7:CA]# tree
.
├── app.cer
├── app.csr
├── cacert.pem
├── certs确定
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old 旧证书的备份
├── newcerts
│ └── 0F.pem 新颁发的证书文件,和app.cer一样
├── private
│ └── cakey.pem
├── serial
└── serial.old 旧证书序列号的备份
4 directories, 10 files
[root@centos7:CA]# diff app.cer newcerts/0F.pem
[root@centos7:CA]# cat index.txt
V 181018141417Z 0F unknown /C=CN/ST=beijing/O=dhyduorg/OU=opt/CN=www.baidu.com
#下一个证书的编号
[root@centos7:CA]# cat serial
10
[root@centos7:CA]# cat serialold
0F
同一个申请文件app.csr是否可以申请多个证书
[root@centos7:CA]# cat index.txt.attr
unique_subject = yes 唯一证书,可以把配置文件改了vim index.txt.attr 改为no
但申请的多个证书是一样的,只是证书编号不一样,一般没此需求3、吊销证书:
[root@centos7:CA]# openssl ca -revoke newcerts/0F.pem
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for /etc/pki/CA/private/cakey.pem:
Revoking Certificate 0F.
Data Base Updated
[root@centos7:CA]# cat index.txt
R 181018141417Z 180718060447Z 0F unknown /C=CN/ST=beijing/O=dhyduorg/OU=opt/CN=www.baidu.com
[root@centos7:CA]# openssl ca -status 0F
Using configuration from /etc/pki/tls/openssl.cnf
0F=Revoked (R)
[root@centos7:CA]#
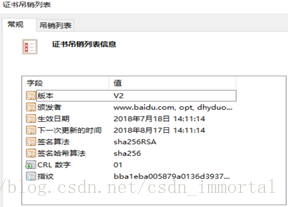
证书吊销后发到互联网上
[root@centos7:CA]# openssl ca -status 0F
Using configuration from /etc/pki/tls/openssl.cnf
0F=Revoked (R)
[root@centos7:CA]# pwd
/etc/pki/CA
#创建吊销序列号,此处从01开始编号
[root@centos7:CA]# echo 01 > crlnumber
[root@centos7:CA]# cat crlnumber
01
#生成吊销文件内容
[root@centos7:CA]# openssl ca -gencrl -out /etc/pki/CA/crl.pem
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for /etc/pki/CA/private/cakey.pem:
[root@centos7:CA]# cat crl.pem
-----BEGIN X509 CRL-----
MIIB1zCBwAIBATANBgkqhkiG9w0BAQsFADBoMQswCQYDVQQGEwJDTjEQMA4GA1UE
CAwHYmVpamluZzEOMAwGA1UEBwwFZGh5ZHUxETAPBgNVBAoMCGRoeWR1b3JnMQww
CgYDVQQLDANvcHQxFjAUBgNVBAMMDXd3dy5iYWlkdS5jb20XDTE4MDcxODA2MTEx
NFoXDTE4MDgxNzA2MTExNFowFDASAgEPFw0xODA3MTgwNjA0NDdaoA4wDDAKBgNV
HRQEAwIBATANBgkqhkiG9w0BAQsFAAOCAQEAaGsUOodT0WFT/ckcNCpsSgWXf7U+
25BcqOMigSuwmju00FdvNA3AXsozfJzt2UCWM8Eu7vUsnjZaN9jxmOqv8Fv4BSz/
y+31zknqHjryC9A+fFj1y50vyXObJtr0rjL2kmOE26ZQXtnUBguqQLVihxnXtbvG
MkODJRslVKJlAg+EcqXMWMWiZJPRkMOjhEyF97Yh3RJOcrB0TI/XH4Yusrq1ysyG
3CYaEge4TsysKOydncJw9zs9DIkTv9zhULwKrmZ8u0tYiaRETsKI9oFrM1mmhMxk
LkBLo2hNyFQ8ml/Vi4xzq8vz3Qw3aH9z7vB4g5MygaUdEEbSeZ0oOQDgSw==
-----END X509 CRL-----
[root@centos7:CA]# #传到windows上,更改后缀为.crl;如下图