VM Name:
BlackMarket
VM Description:
BlackMarket VM presented at Brisbane SecTalks BNE0x1B (28th Session) which is focused on students and other InfoSec Professional. This VM has total 6 flag and one r00t flag. Each Flag leads to another Flag and flag format is flag{blahblah}.
Shoutout to @RobertWinkel and @dooktwit for hosting at SecTalk Brisbane
If you get stuck in rabbit hole and need hints hit me up on twitter. Have fun!
VM Difficulty Level:
Beginner/Intermediate
What will you learn?
Learn about how to enumerate your target and join dots in order to pwn this VM.
VM Tested:
VMware Player VirtualBox
Networking:
DHCP Enabled
Author:
AcEb0mb3R Twitter: @Acebomber911
信息收集
-
ip发现
- 首先攻击机kali本机的IP为 192.168.0.104
启动BlackMarket虚拟机,虚机网络设置为dhcp,使用Nmap扫描,即可找到虚机IP,命令:
nmap -sP 192.168.0.0/24
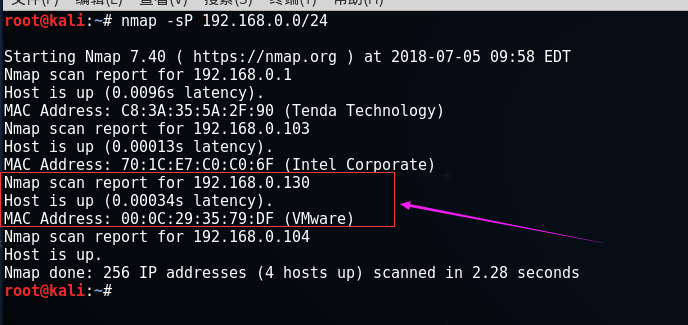
获得靶机ip 192.168.0.130
端口和服务识别
使用nmap扫描1-65535全端口,并做服务识别和深度扫描(加-A参数),命令:
nmap -T4 -A -v 192.168.0.130 -p 0-10000
端口开得有点多
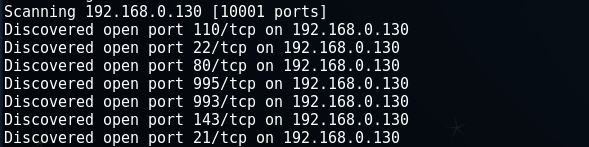
我们看具体信息

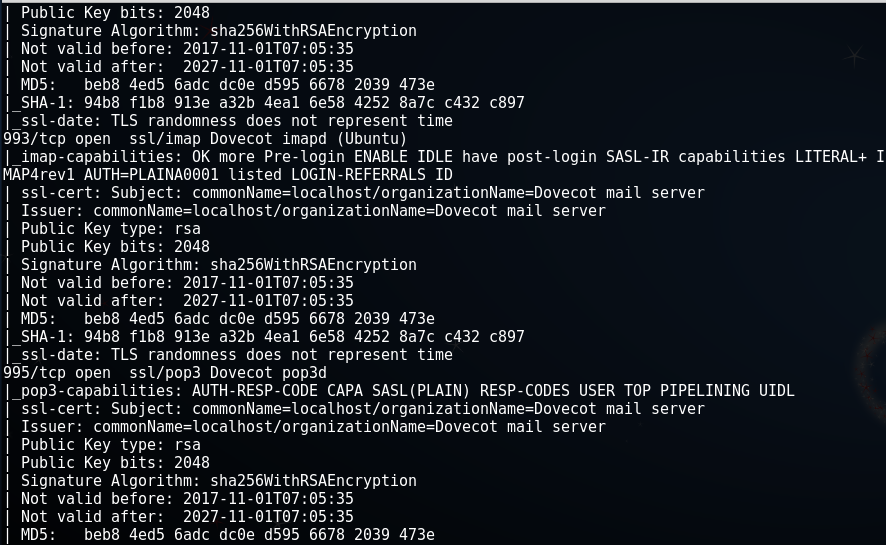
发现了几个敏感端口:
21端口 ---> ftp服务
22端口 ---> ssh服务
80端口 ---> Apache服务
我们访问靶机主页:
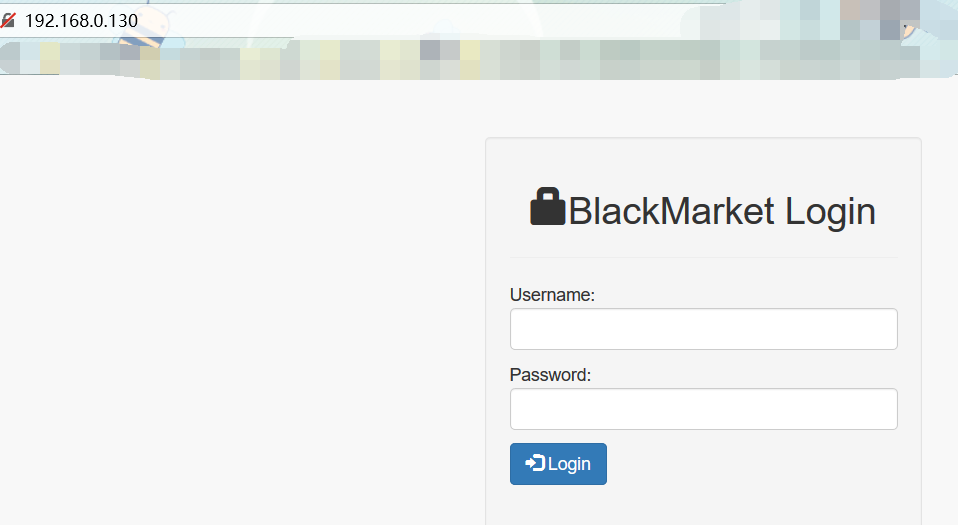
发现是个寻常登陆框,我们从web入手,也就是查看/robots.txt,查看源代码等
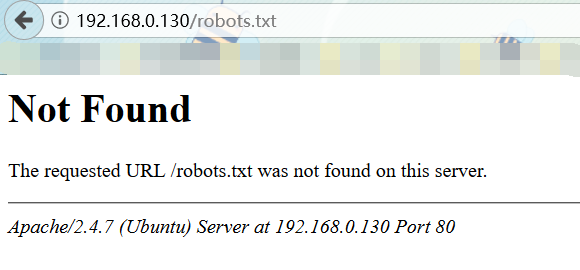
额...不慌,我们查看源代码

WTF??? surprise!!!! 我们得到了flag,不过这个flag的内容....有点像base64...,解码看看
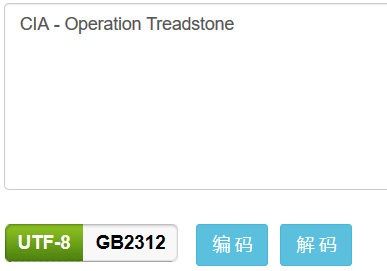 CIA - Operation Treadstone
CIA - Operation Treadstone
这个东西...完全没有一点思路好吧...Google一把

.....什么鬼
接下来,我们用kali自带的工具cewl来爬行网站获取关键信息创建一个密码字典,命令:
cewl -d 3 -m 3 -w /1.txt http://bourne.wikia.com/wiki/Operation_Treadstone
参数解释:-m:最小单词长度
-d:爬网深度
-c:每个单词出现的次数